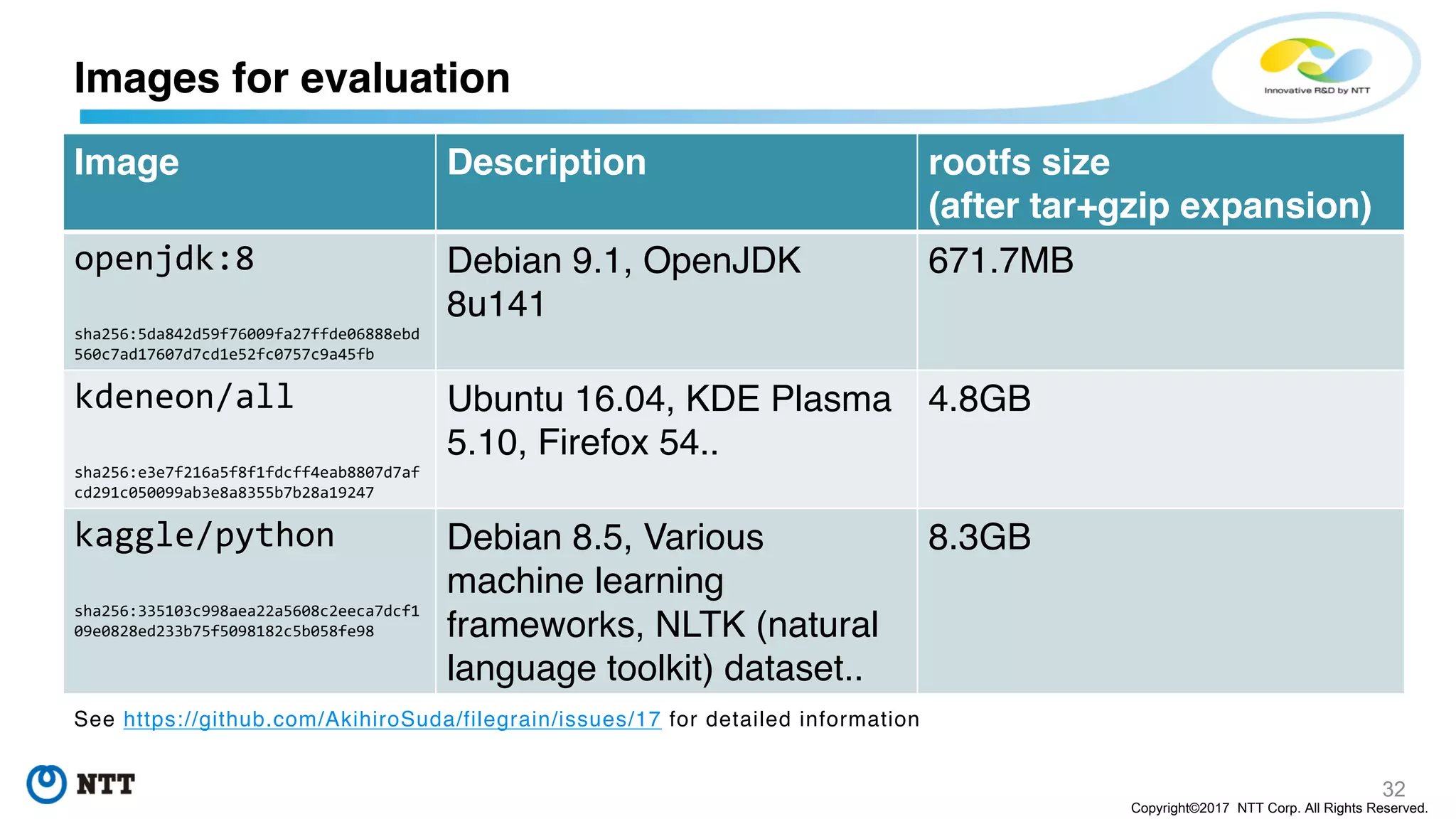
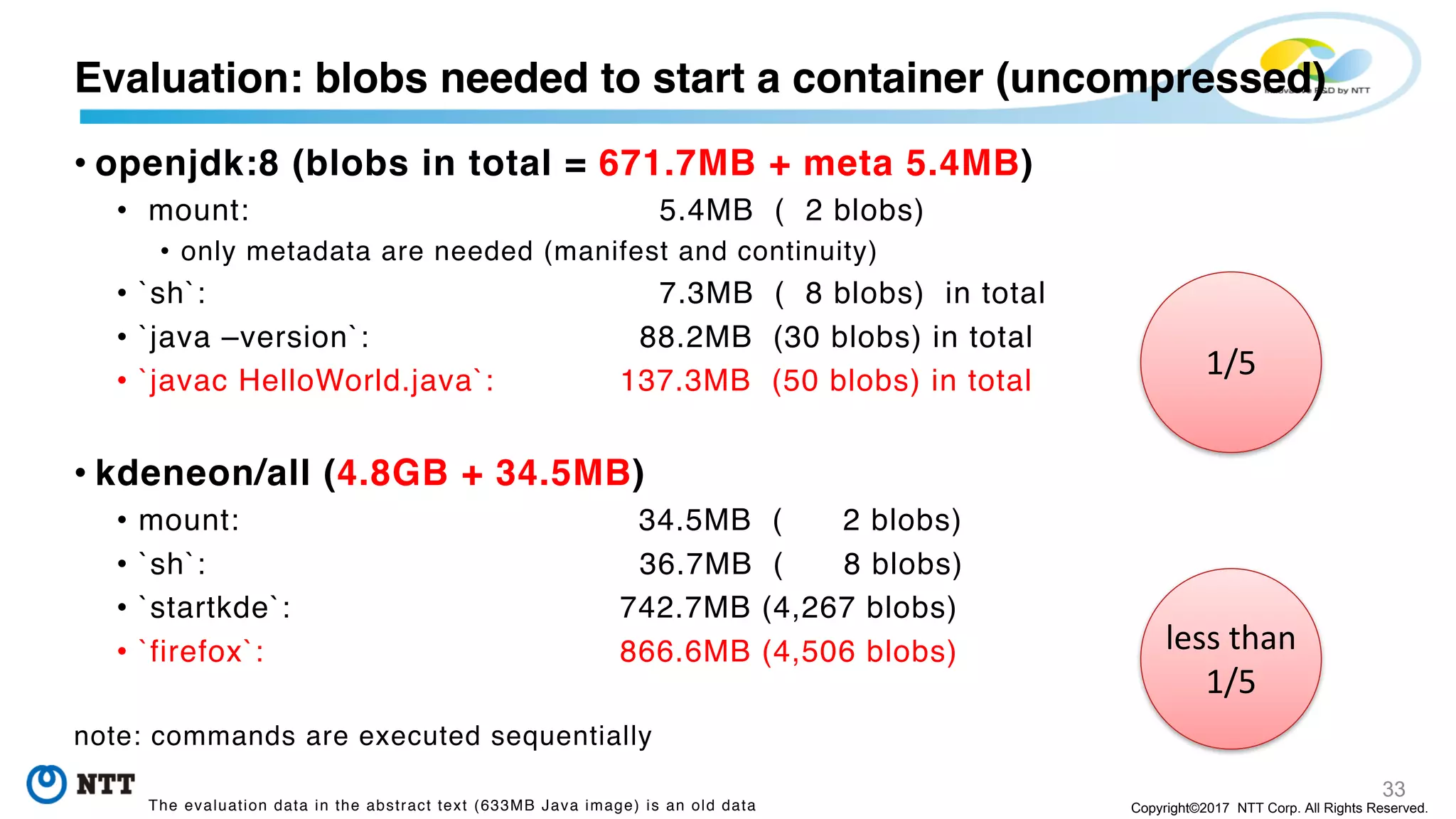
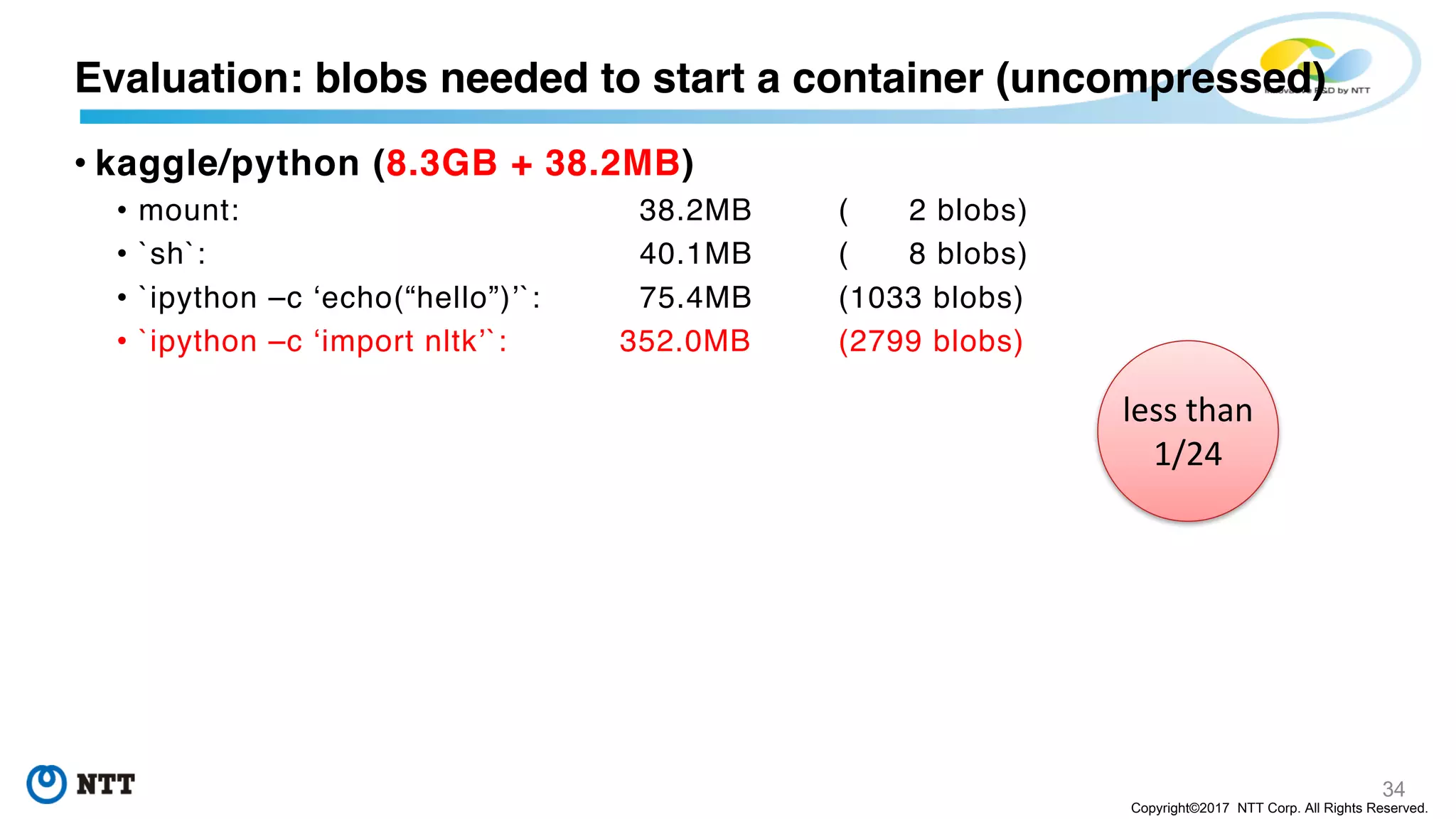
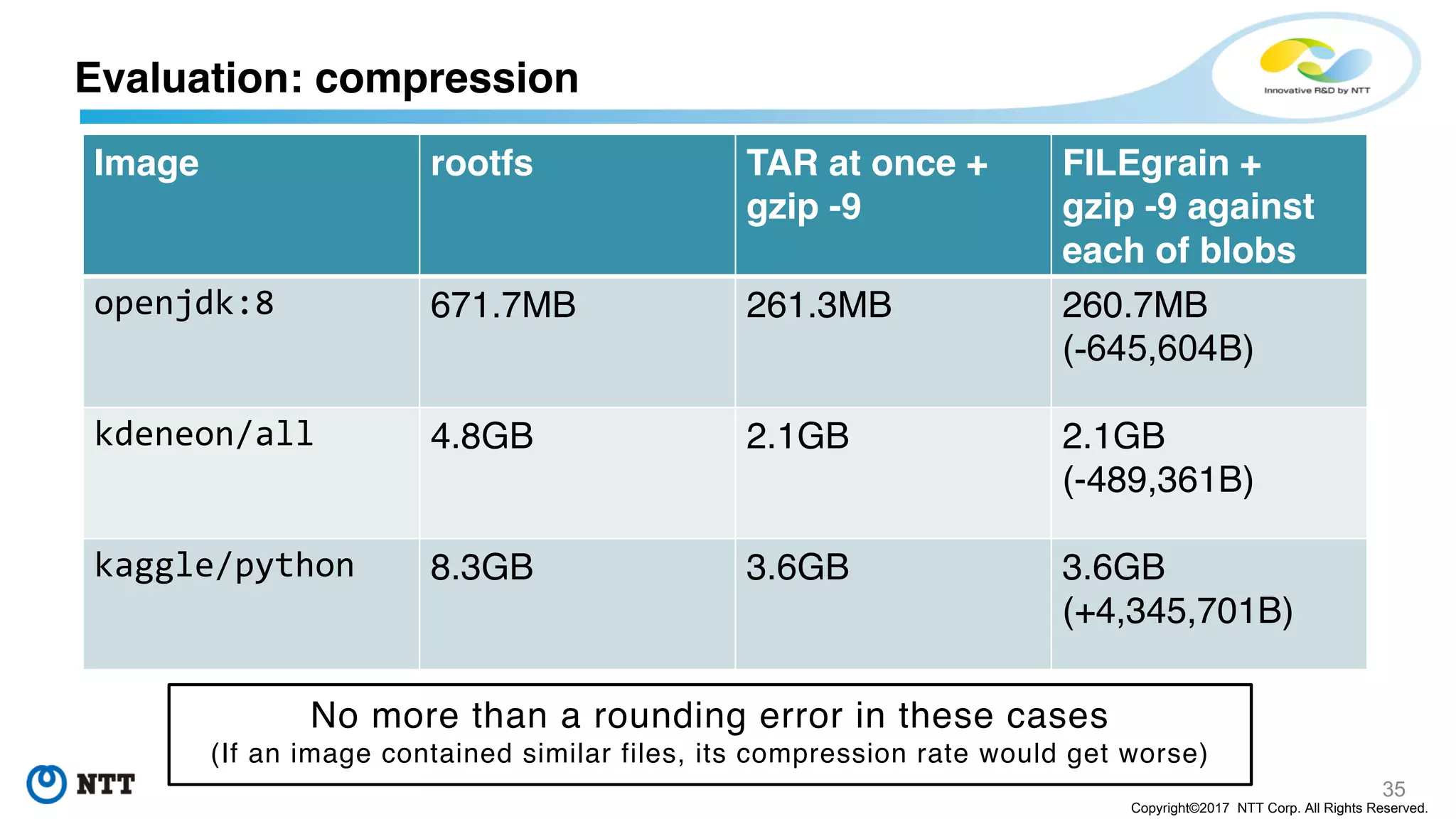
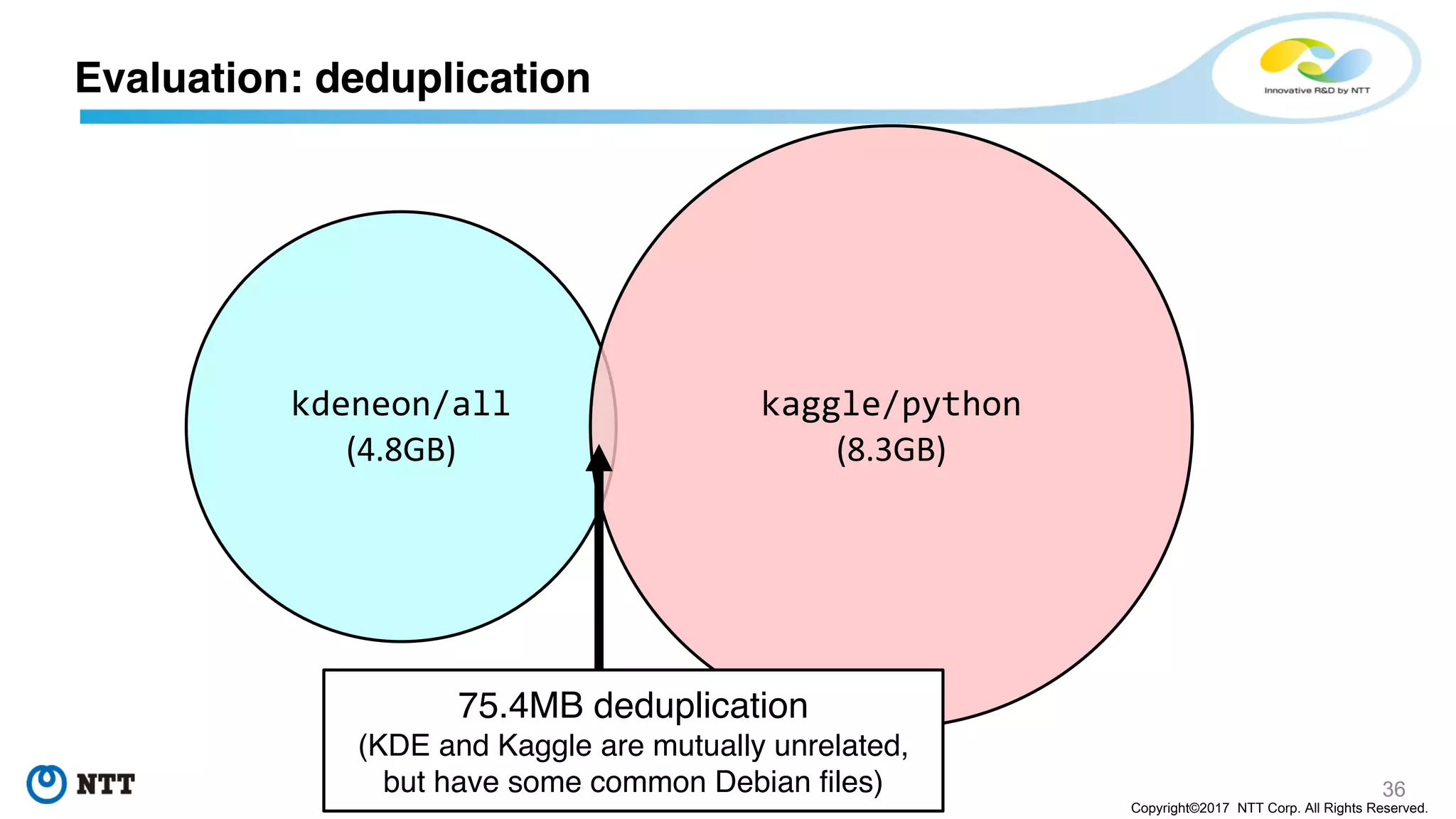
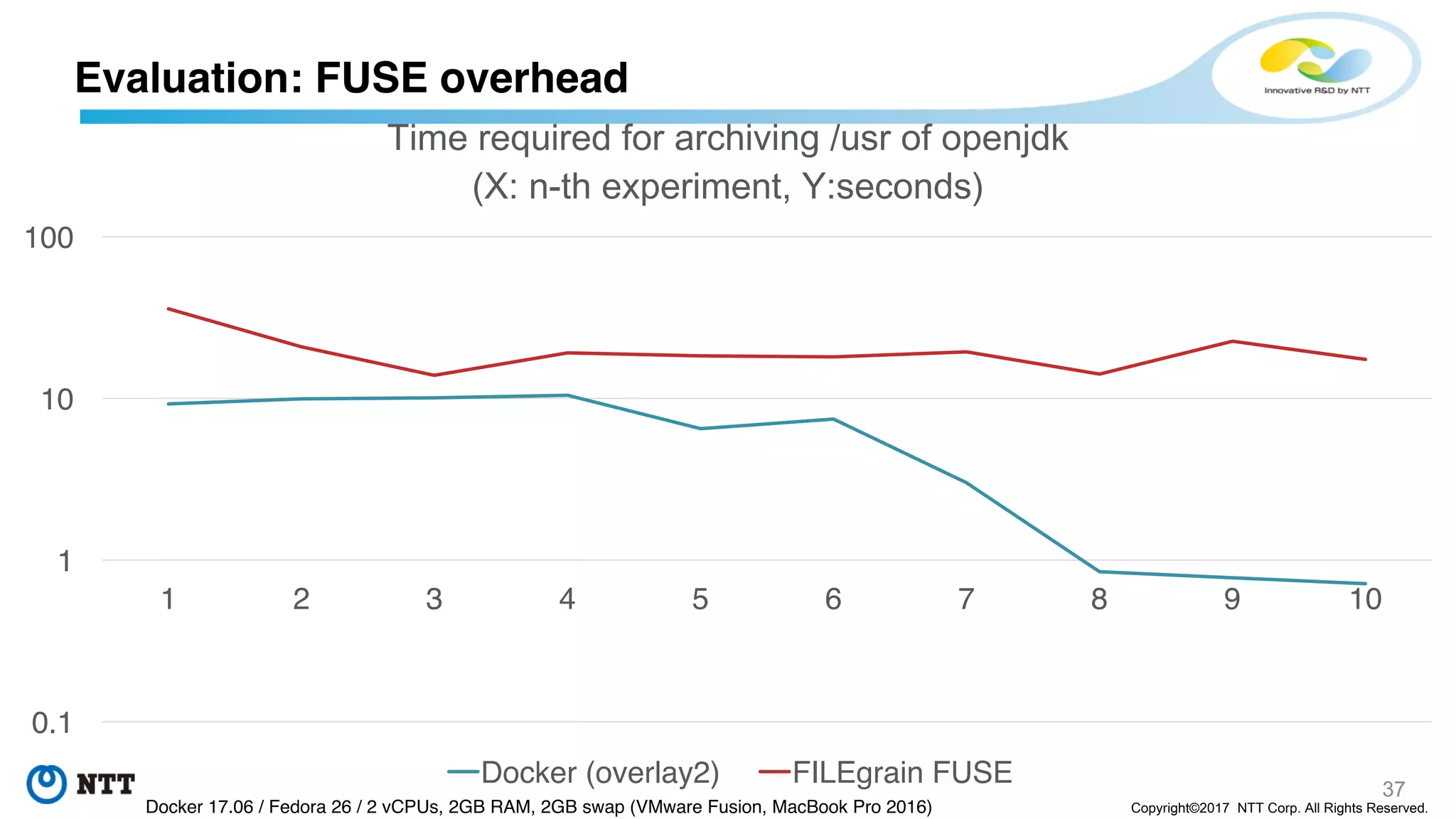
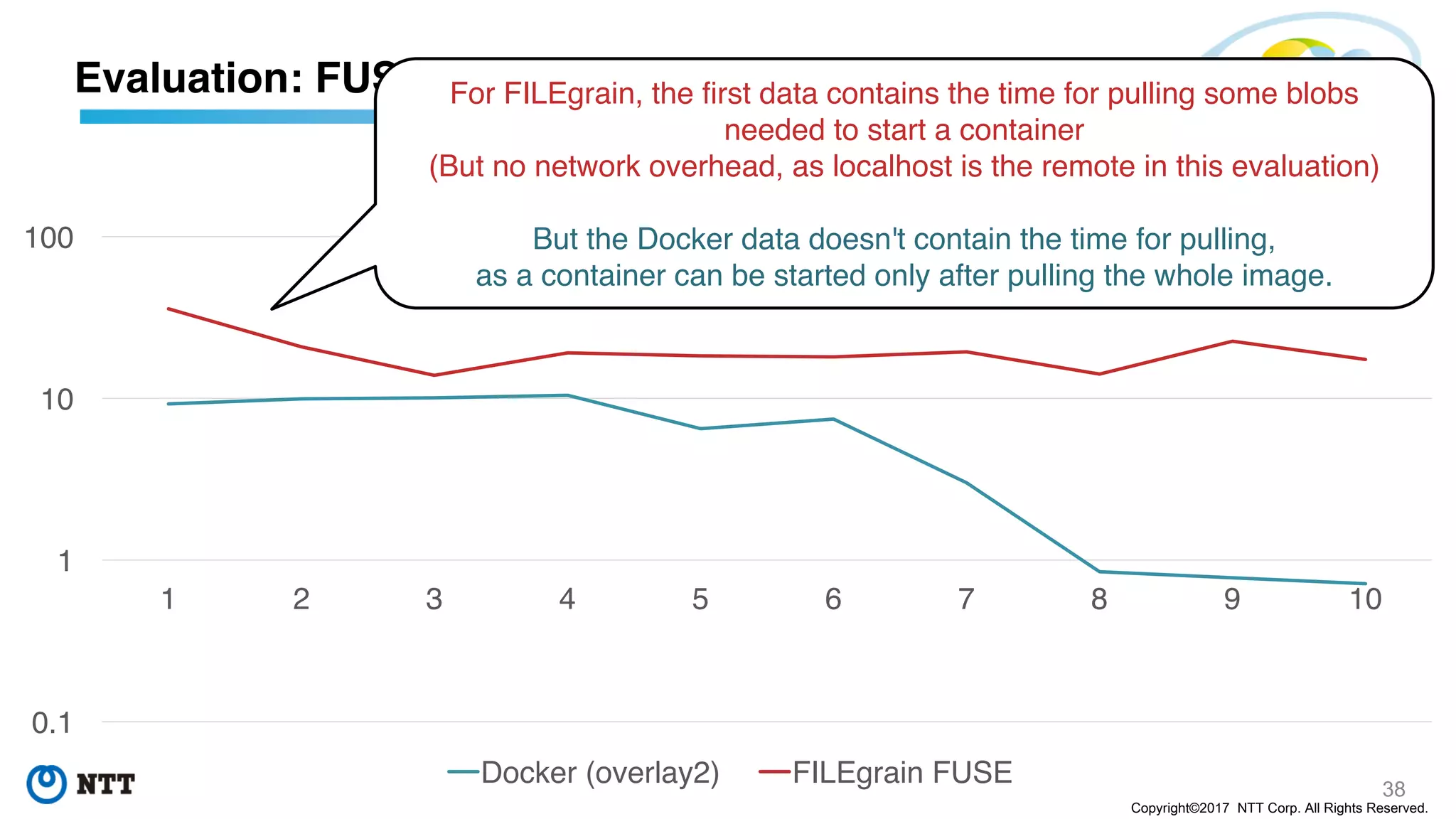
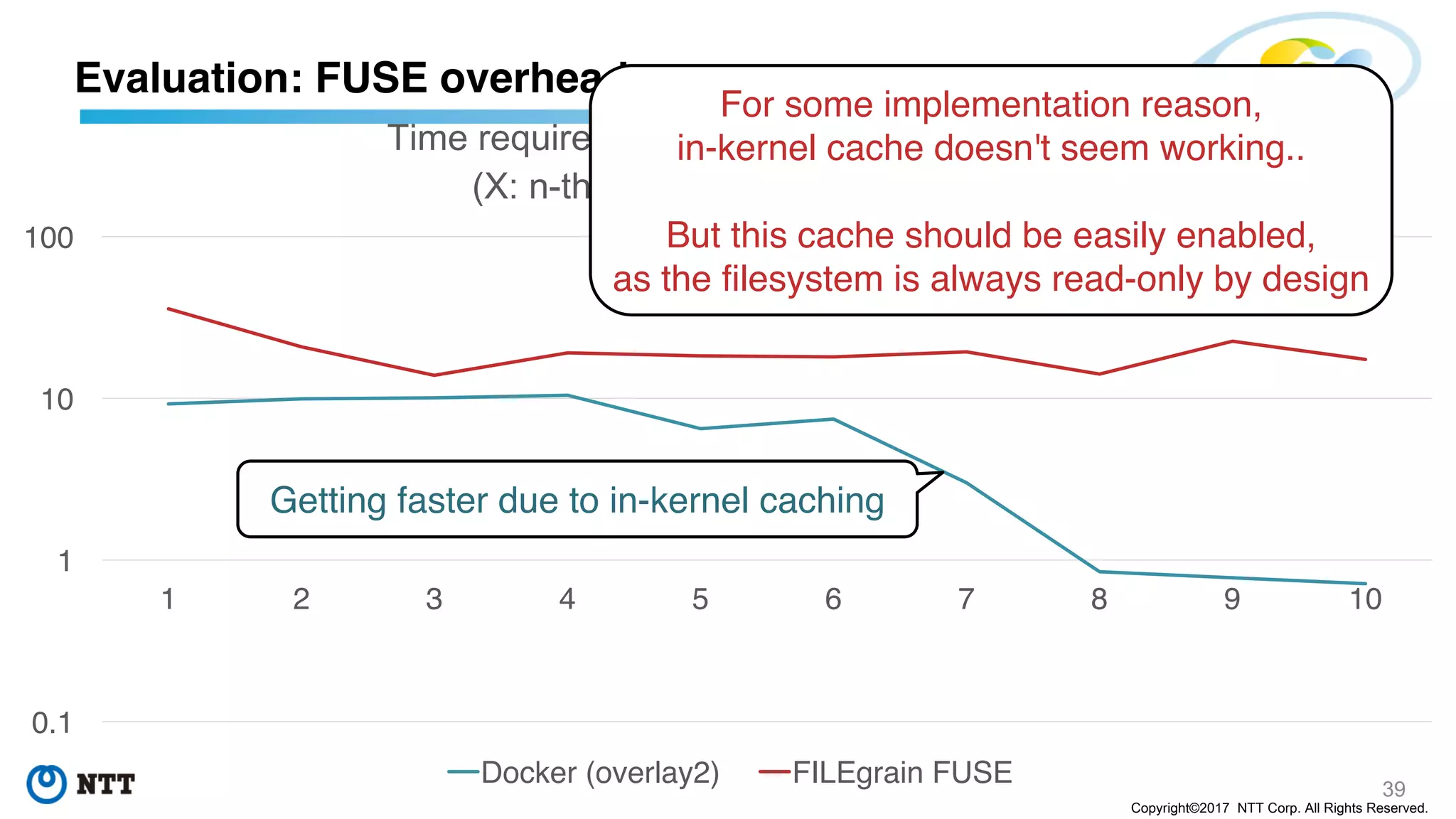
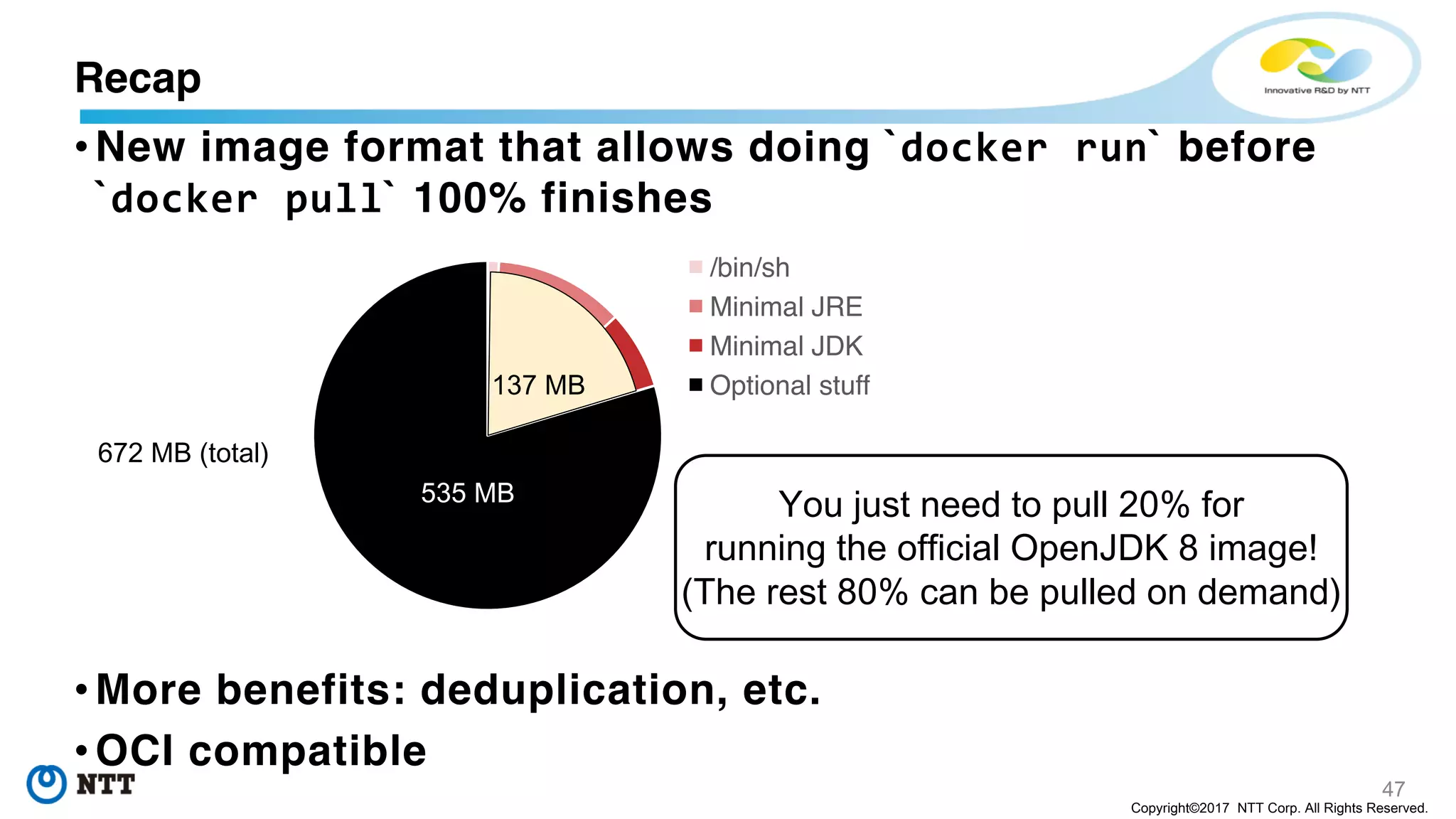
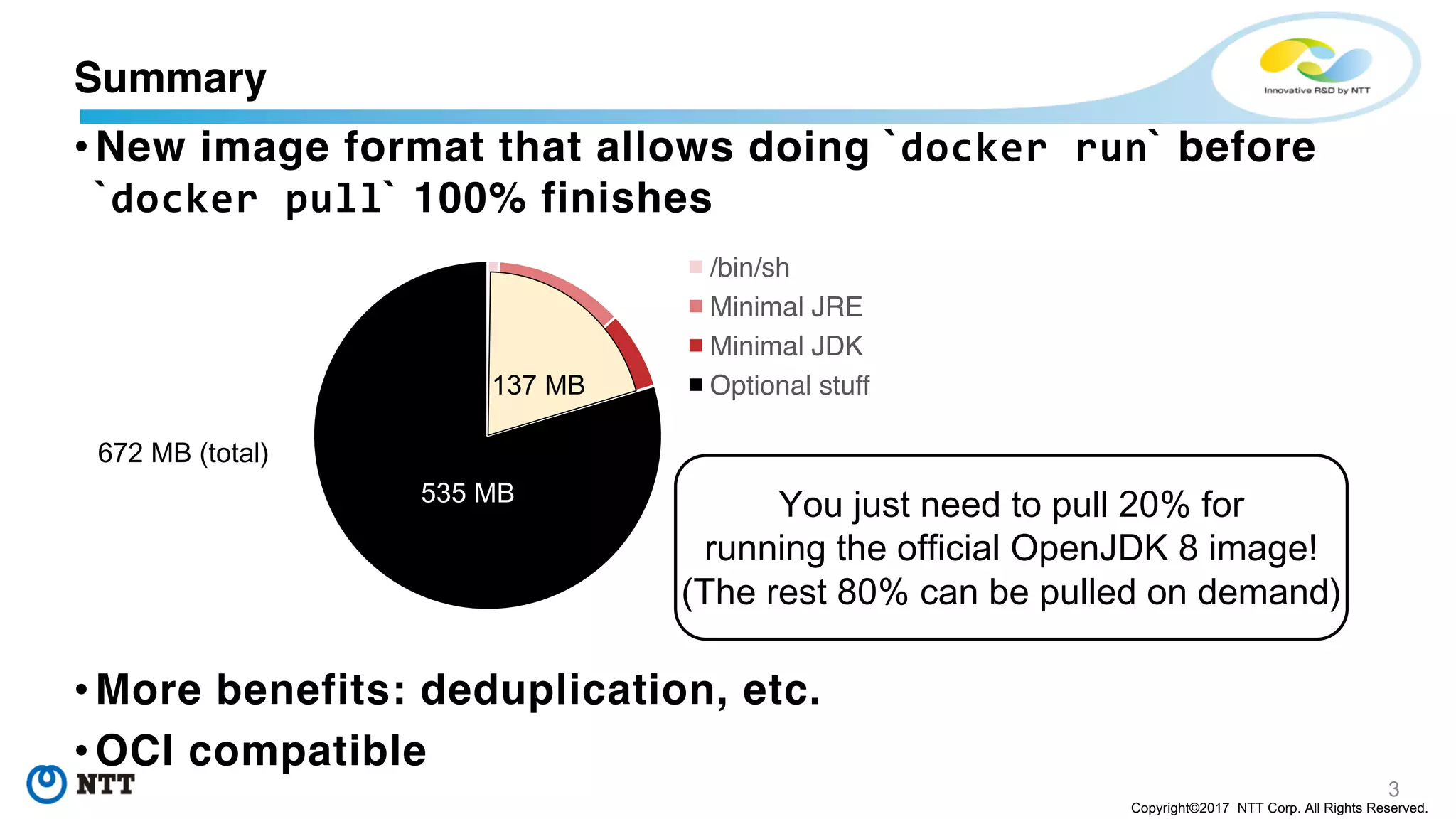
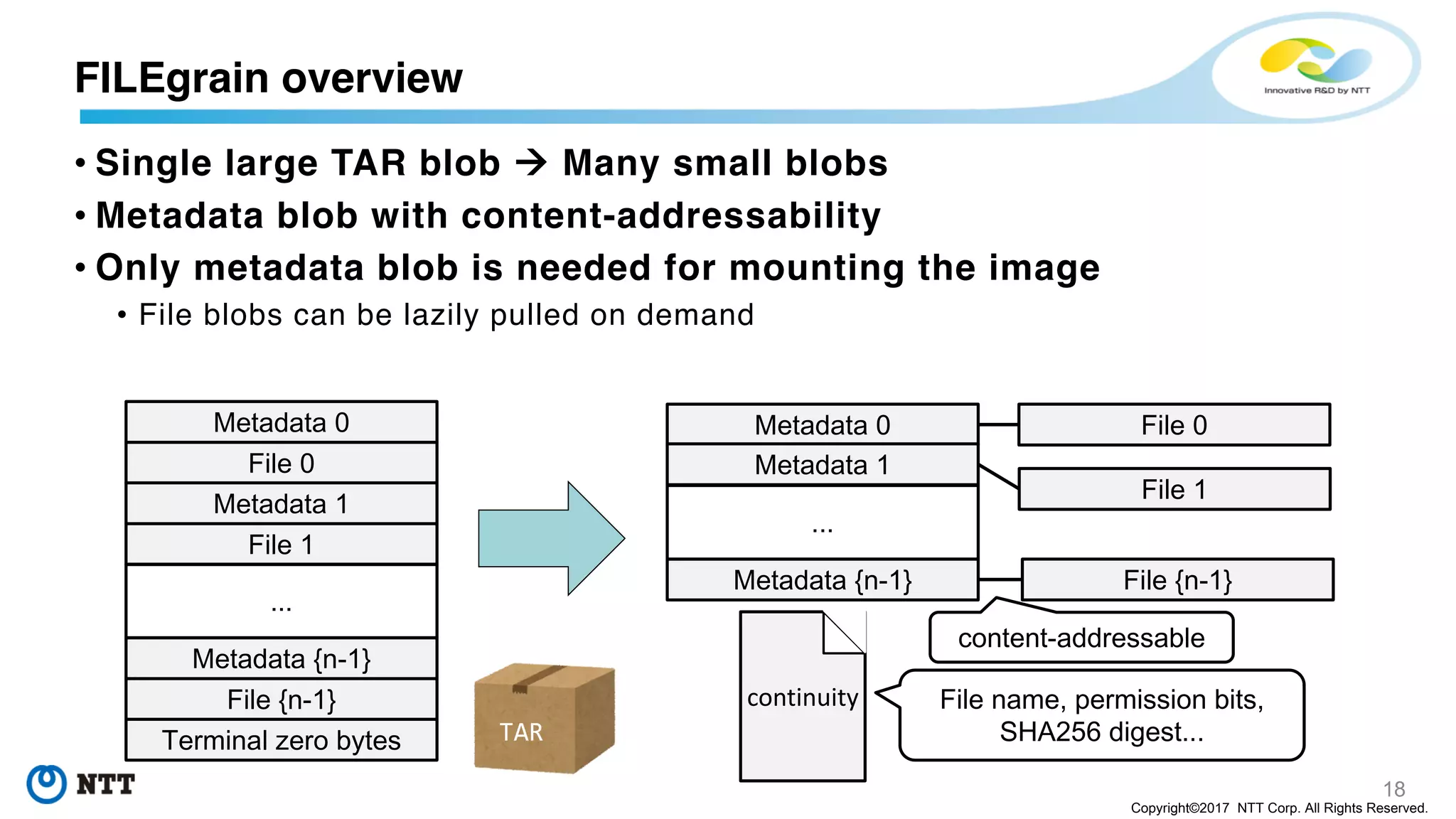
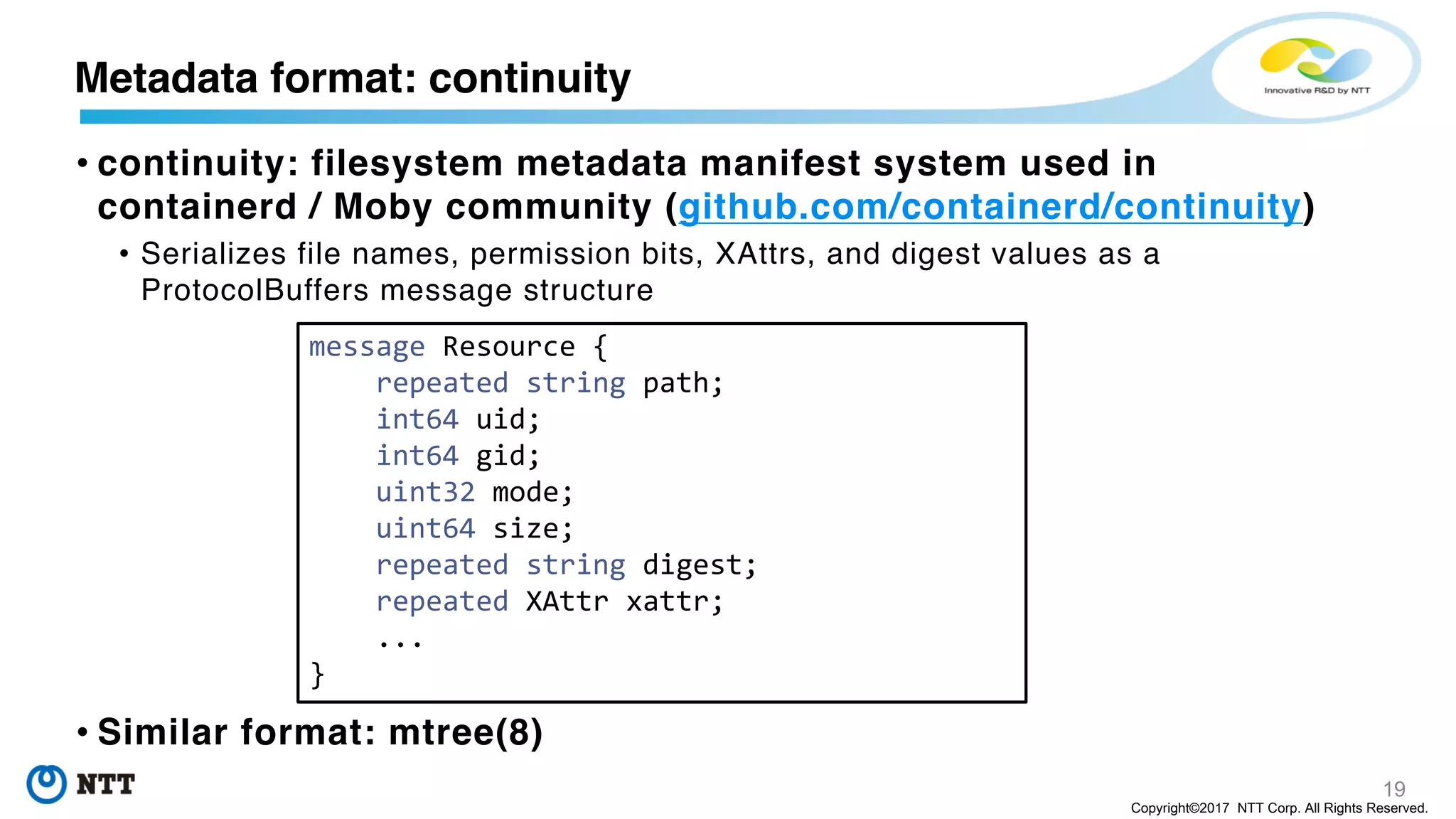
The document discusses the Filegrain project, an next-generation container image format designed to address limitations of the traditional Docker/OCI image format, such as the need for entire tar file scans, lack of deduplication, and poor concurrency. Filegrain allows for on-demand file pulling, faster container start-up times, and better resource utilization through content-addressable small blobs and a unified metadata format. The proposal includes compatibility with existing OCI specs while improving efficiency, particularly for large and complex applications.

![2
Copyright©2017 NTT Corp. All Rights Reserved.
• Software Engineer at NTT
• Largest telco in Japan
• Docker Moby Core maintainer
• BuildKit initial maintainer (github.com/moby/buildkit)
• Next-generation `docker build`
• Executes DAG vertexes of Dockerfile-equivalent concurrently
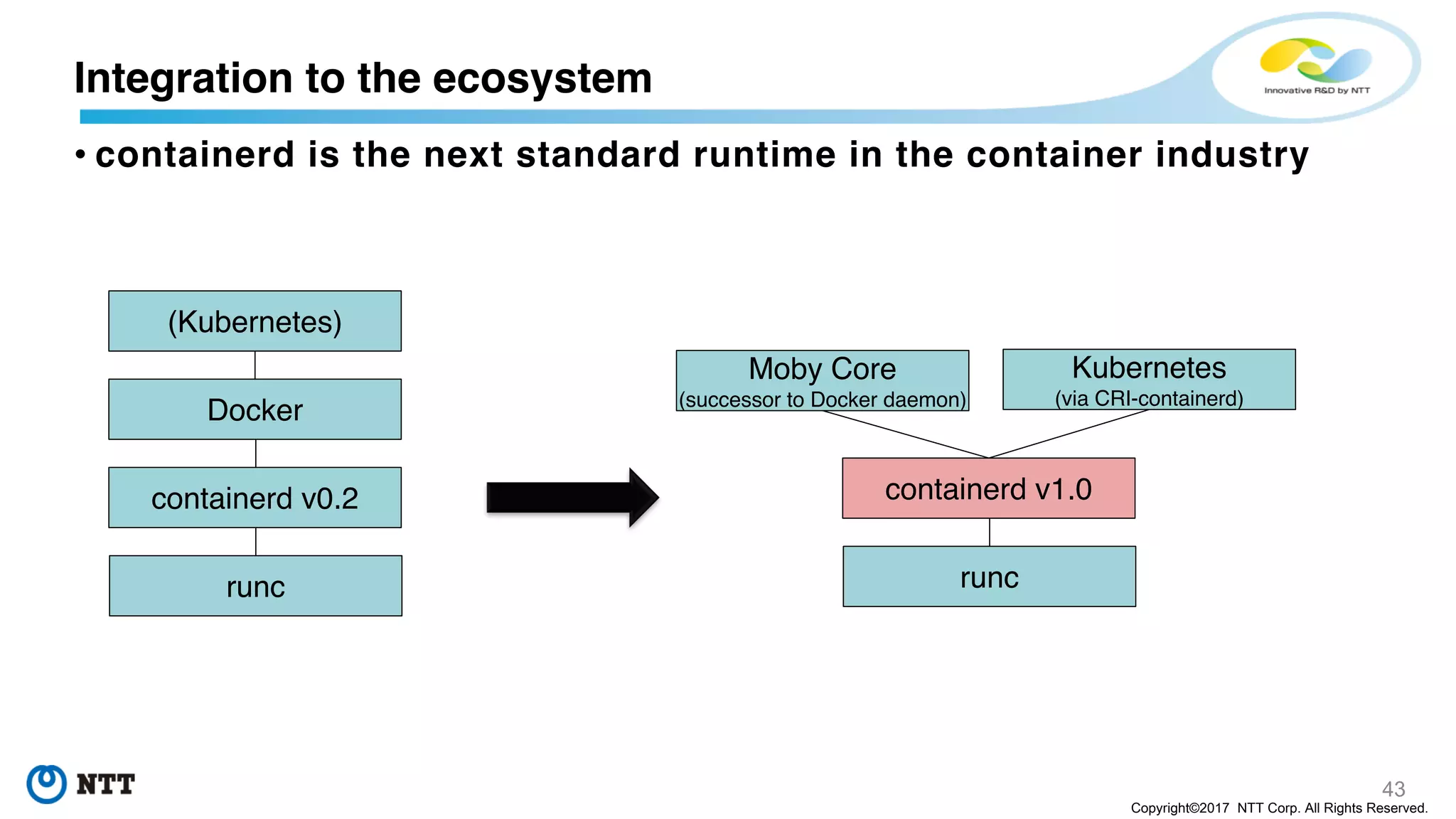
In April, Docker [ as a project ] transited into Moby.
Now Docker [ as a product ] has been developed as one of downstream of Moby.
: ≒ :
RHEL Fedora
Who am I](https://image.slidesharecdn.com/filegrain-20170817-170818052711/75/FILEgrain-Transport-Agnostic-Fine-Grained-Content-Addressable-Container-Image-Layout-2-2048.jpg)
![8
Copyright©2017 NTT Corp. All Rights Reserved.
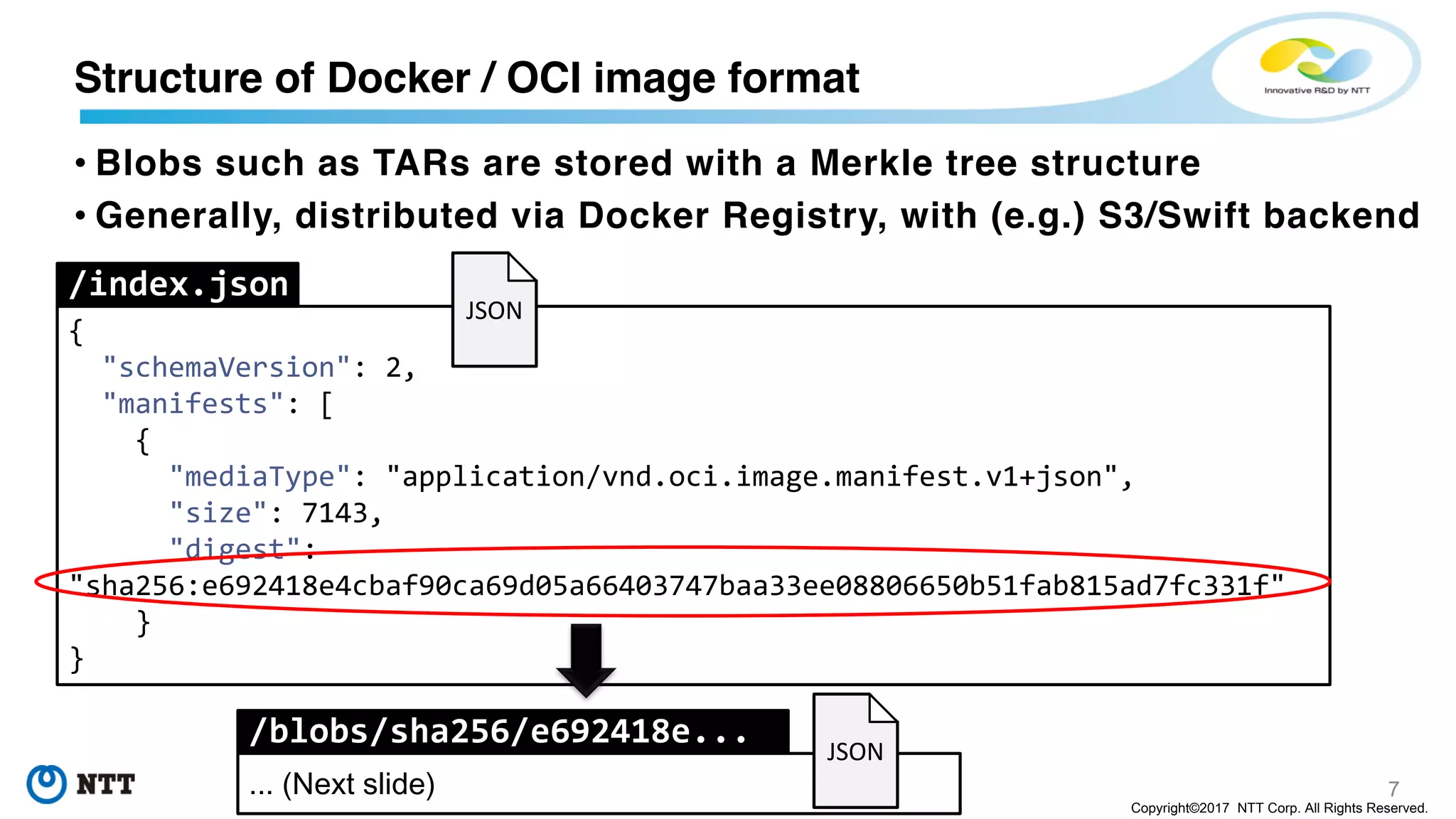
/blobs/sha256/e692418e...
{
"schemaVersion": 2,
"config": {
"mediaType": "application/vnd.oci.image.config.v1+json",
"size": 7023,
"digest": "sha256:b5b2b2c507a0944348e0303114d8d93aaaa081732b86451d9bce1f432a537bc7"
},
"layers": [
{
"mediaType": "application/vnd.oci.image.layer.v1.tar+gzip",
"size": 33554432,
"digest": "sha256:61be55a8e2f6b4e172338bddf184d6dbee29c98853e0a0485ecee7f27b9af0b4"
},
{
"mediaType": "application/vnd.oci.image.layer.v1.tar+gzip",
"size": 1073741824,
"digest": "sha256:3c3a4604a545cdc127456d94e421cd355bca5b528f4a9c1905b15da2eb4a4c6b"
},
{
"mediaType": "application/vnd.oci.image.layer.v1.tar+gzip",
"size": 73109,
"digest": "sha256:ec4b8955958665577945c89419d1af06b5f7636b4ac3da7f12184802ad867736"
}
]
}
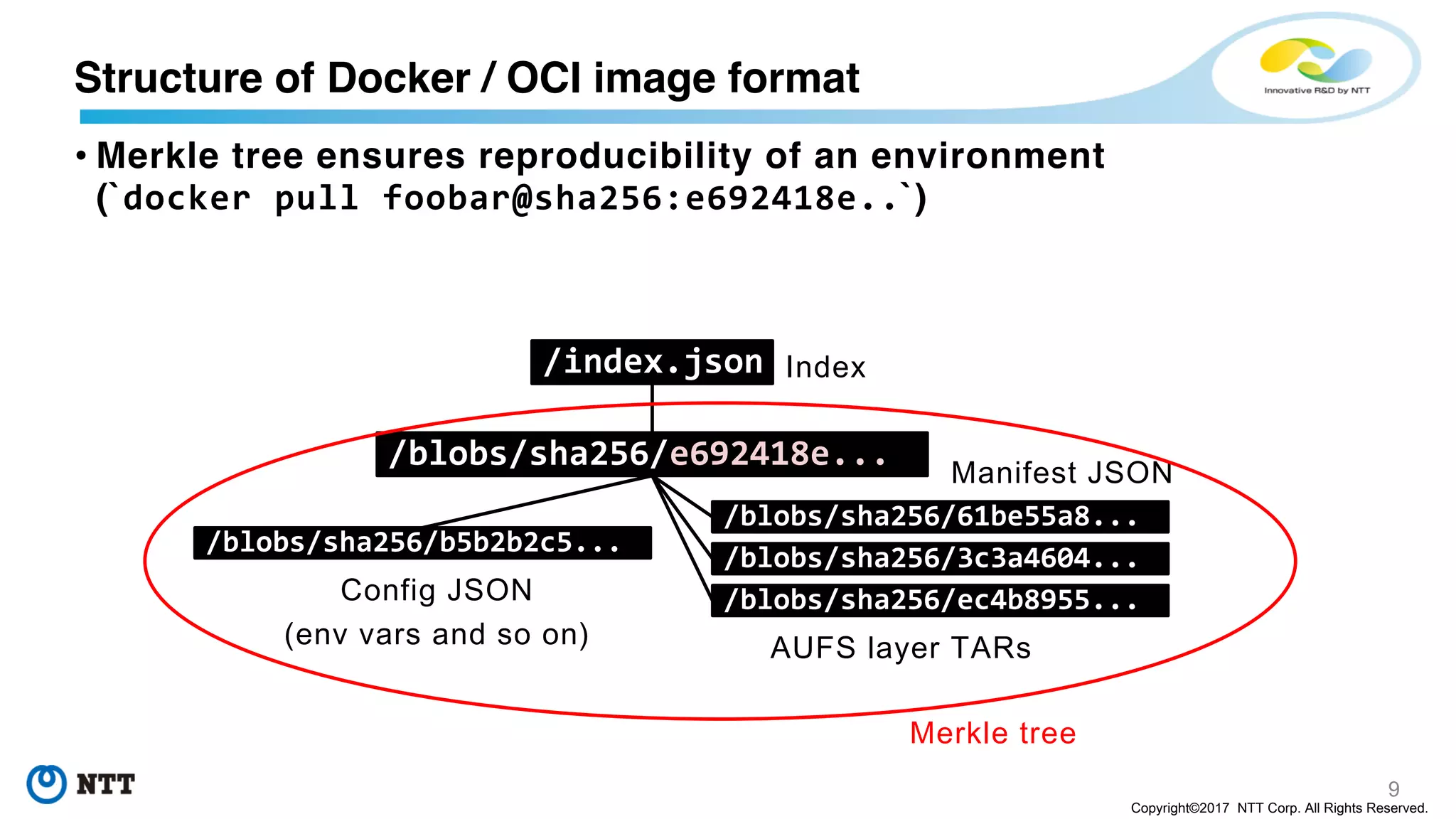
/blobs/sha256/b5b2b2c5...
Environment variables and so on
/blobs/sha256/61be55a8...
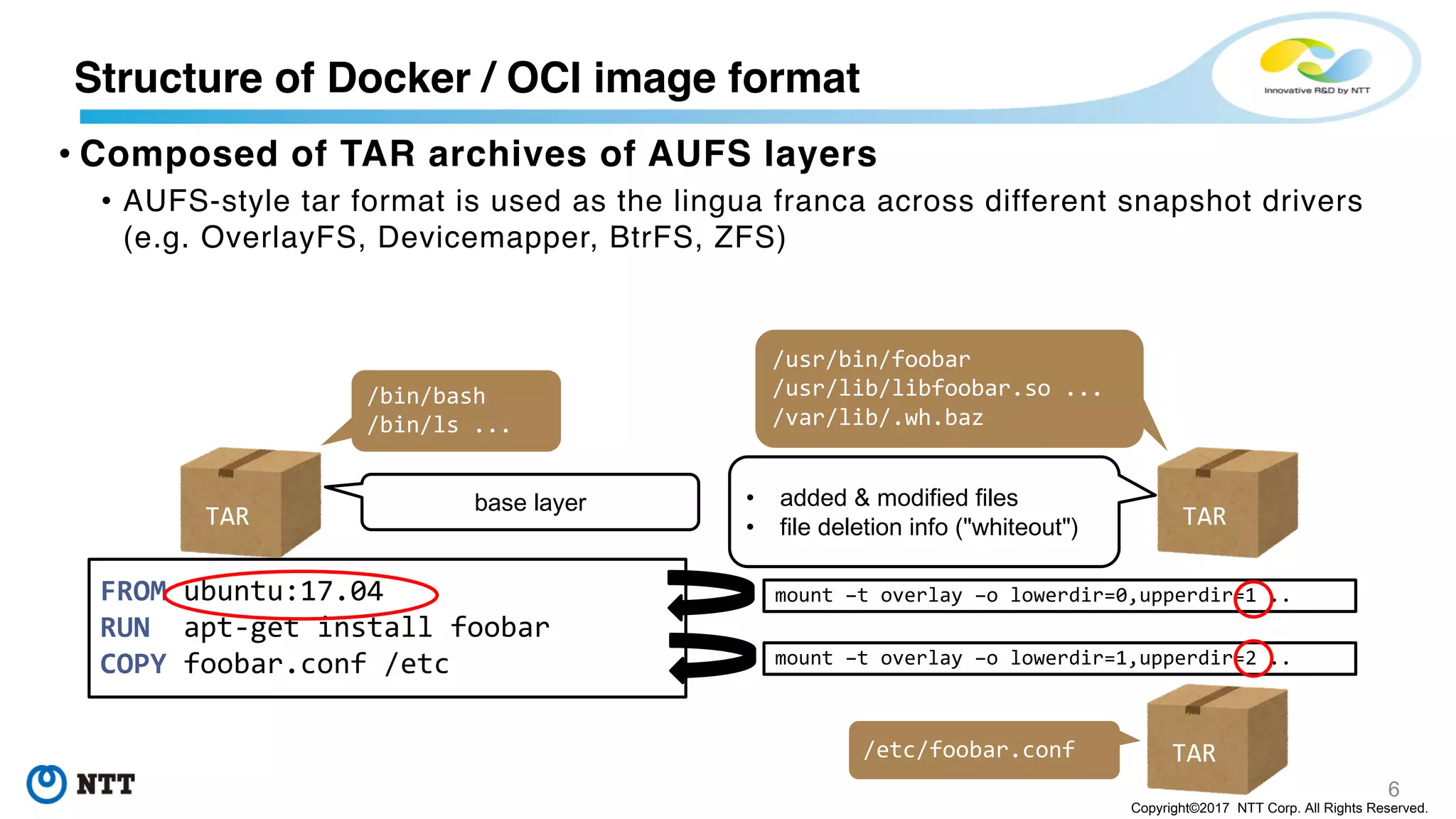
Base layer
/blobs/sha256/3c3a4604...
Diff layer
/blobs/sha256/ec4b8955...
Diff layer
TAR
TAR
TAR
JSON
JSON](https://image.slidesharecdn.com/filegrain-20170817-170818052711/75/FILEgrain-Transport-Agnostic-Fine-Grained-Content-Addressable-Container-Image-Layout-8-2048.jpg)
![21
Copyright©2017 NTT Corp. All Rights Reserved.
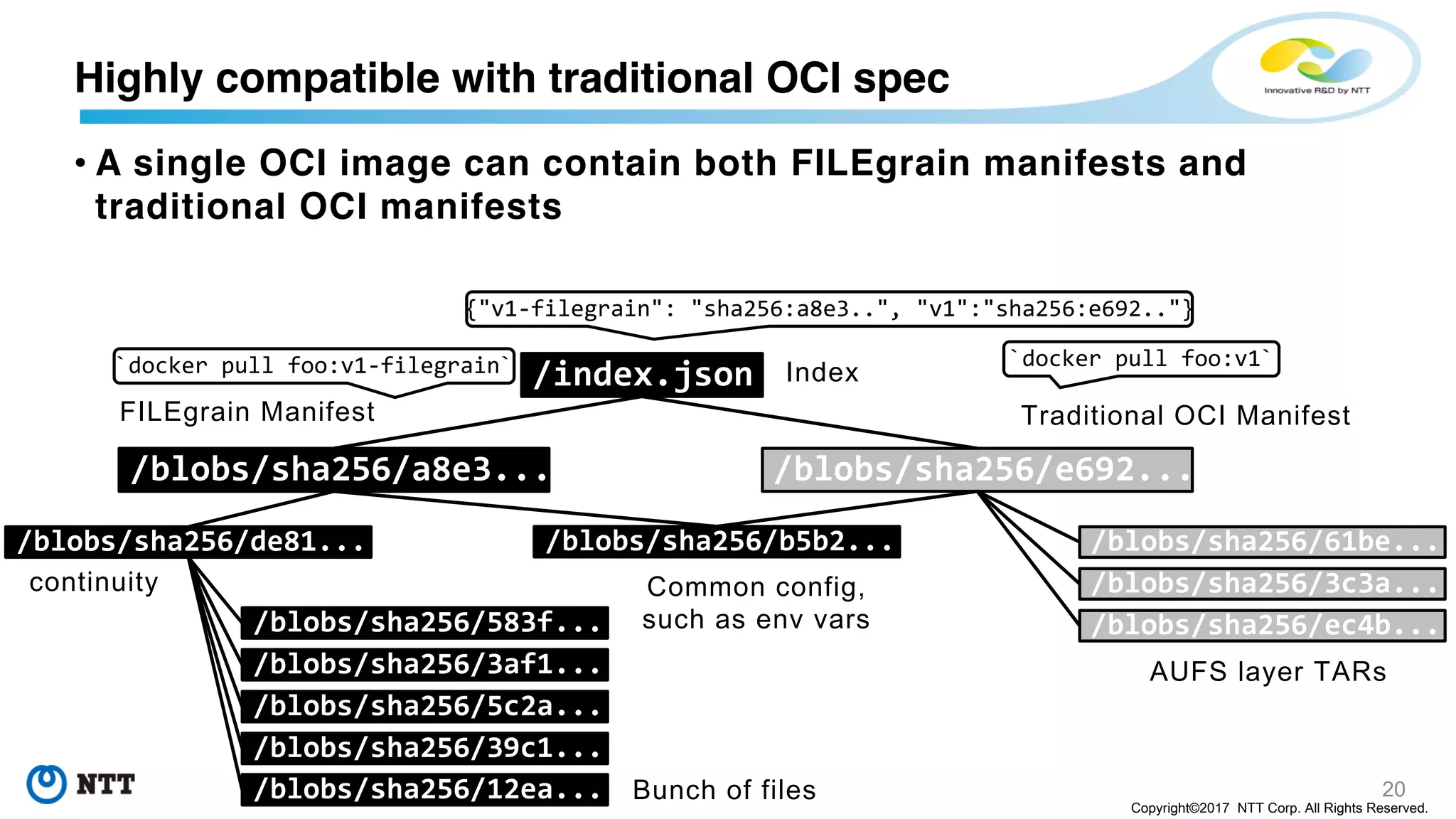
• FILEgrain layers can be put on top of traditional OCI layers
• Traditional OCI layers might be still suitable for frequently used files or large
number of small files
Highly compatible with traditional OCI spec
{
...
"layers": [
{
"mediaType": "application/vnd.oci.image.layer.v1.tar+gzip",
"size": 33554432,
"digest": "sha256:e692..."
},
{
"mediaType": "application/vnd.continuity.layer.v0+pb",
"size": 16724,
"digest": "sha256:a18b..."
}
]
}
TAR
continuity
Traditional OCI layer
(Needs to be completely
pulled before starting a container)
FILEgrain layer
(Can be lazy-pulled on demand)](https://image.slidesharecdn.com/filegrain-20170817-170818052711/75/FILEgrain-Transport-Agnostic-Fine-Grained-Content-Addressable-Container-Image-Layout-21-2048.jpg)