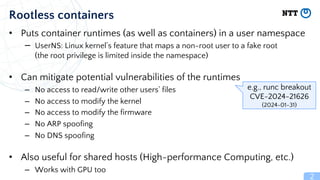
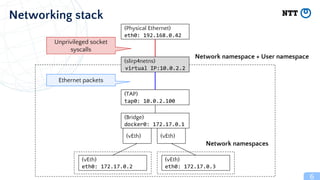
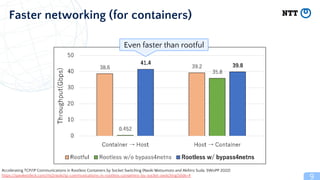
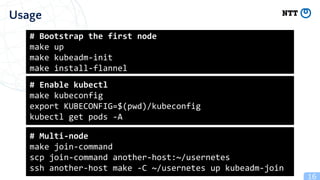
Rootless containers put the container runtime in a user namespace to limit privileges. This improves security by preventing access to other users' files, ability to modify the kernel or firmware. Rootless containers have been supported by container runtimes since 2014 and are useful for shared computing environments. Key aspects include user namespaces remap UIDs to limit privileges to inside namespaces, and networking solutions like slirp4netns or bypass4netns to provide networking without privileges. Rootless Kubernetes called Usernetes allows running Kubernetes without root privileges and supports multi-node clusters.