When using container image vulnerability scanners like Trivy, a large number of vulnerabilities may be detected. However, not all of them necessarily require an action. This is because not all libraries or command-line tools included in the container image are actually utilized.
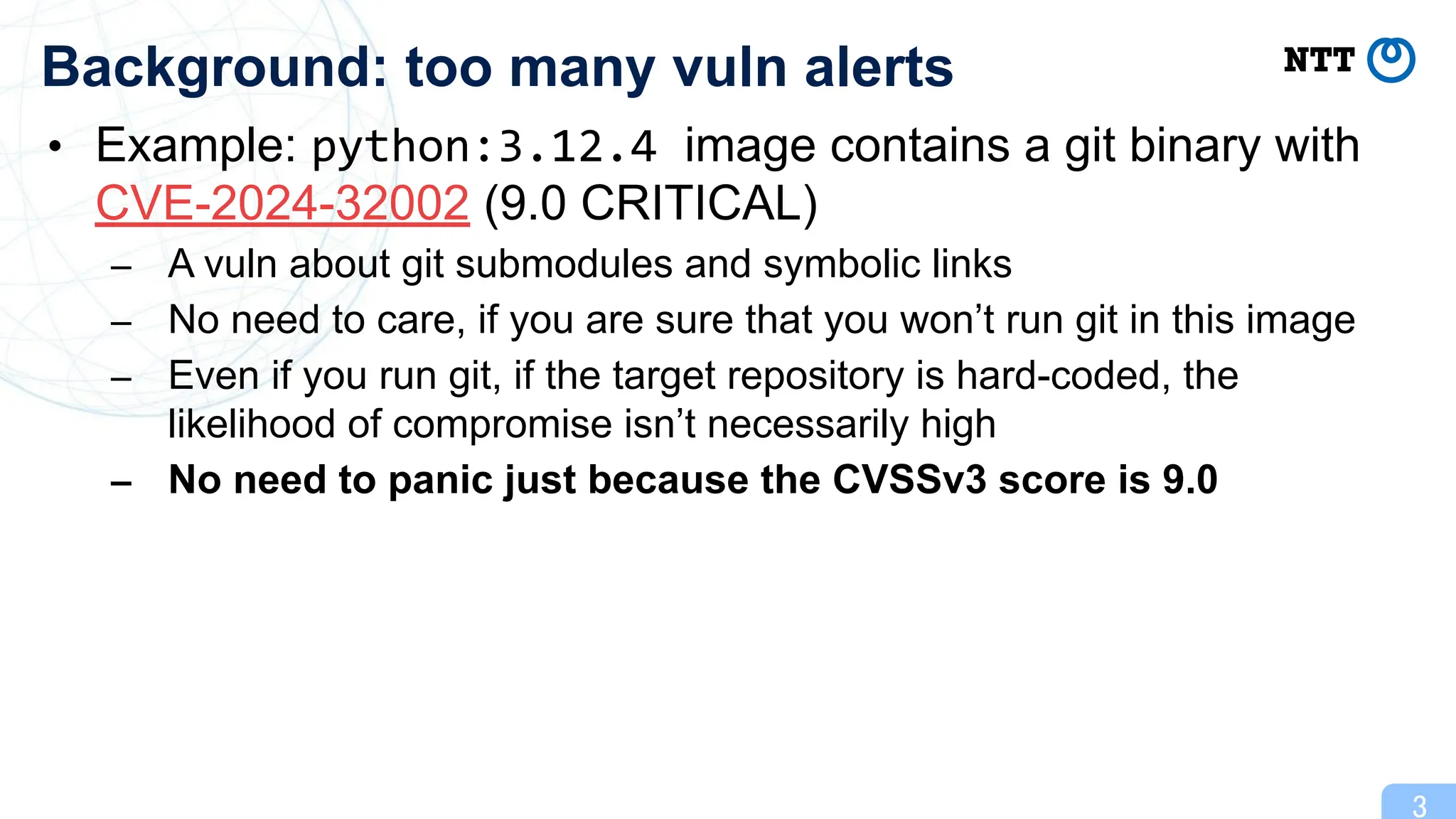
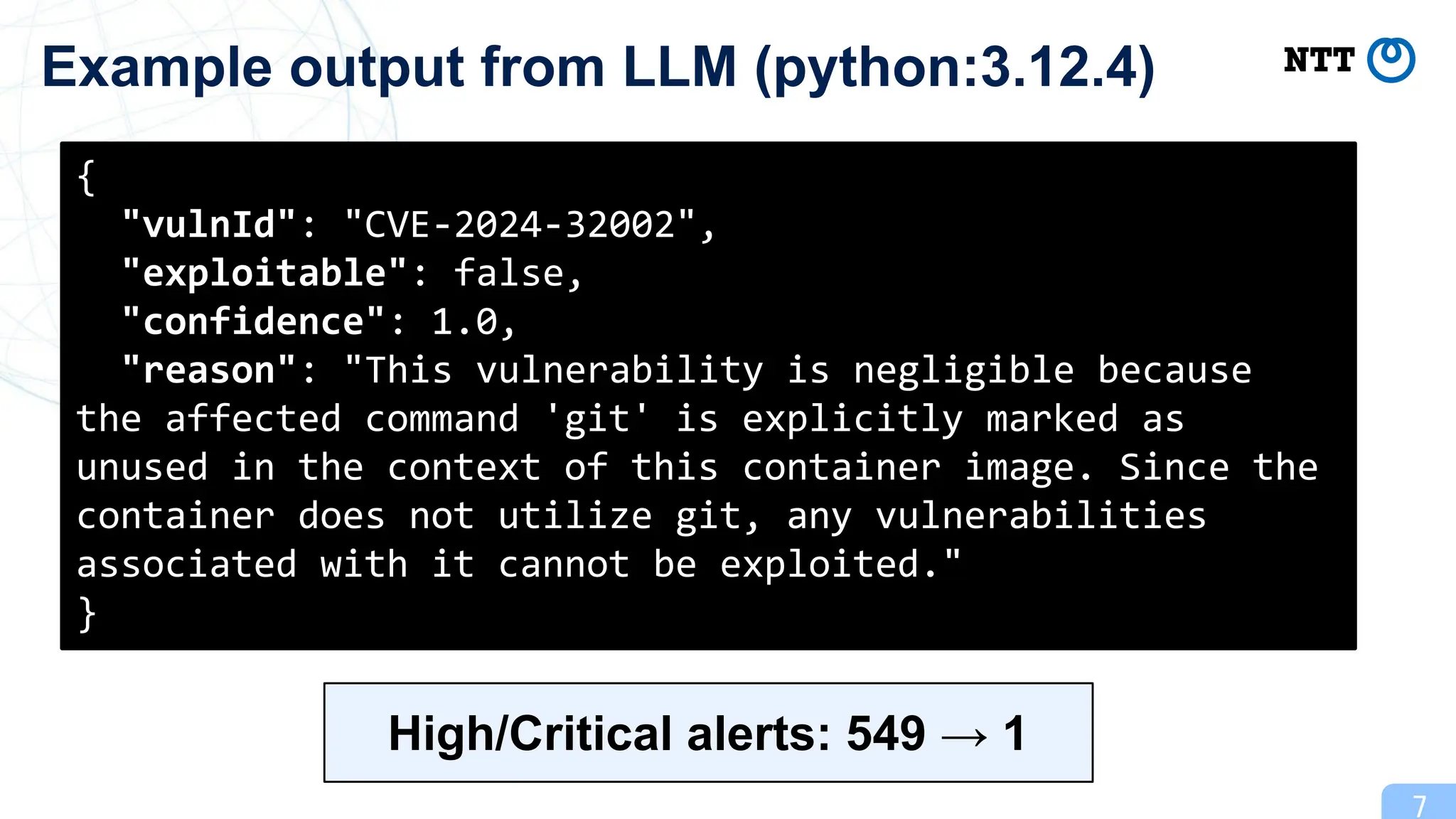
For example, the `python:3.12.4` image includes a `git` binary with the vulnerability CVE-2024-32002. This vulnerability does not need an immediate action if it is known that the Python application being run does not execute `git` commands.
VEX (Vulnerability-Exploitability eXchange) formats such as OpenVEX can be used to suppress such false alarms.
However, VEX is still not widely adopted due to the difficulty of manual analysis and classification of vulnerabilities.
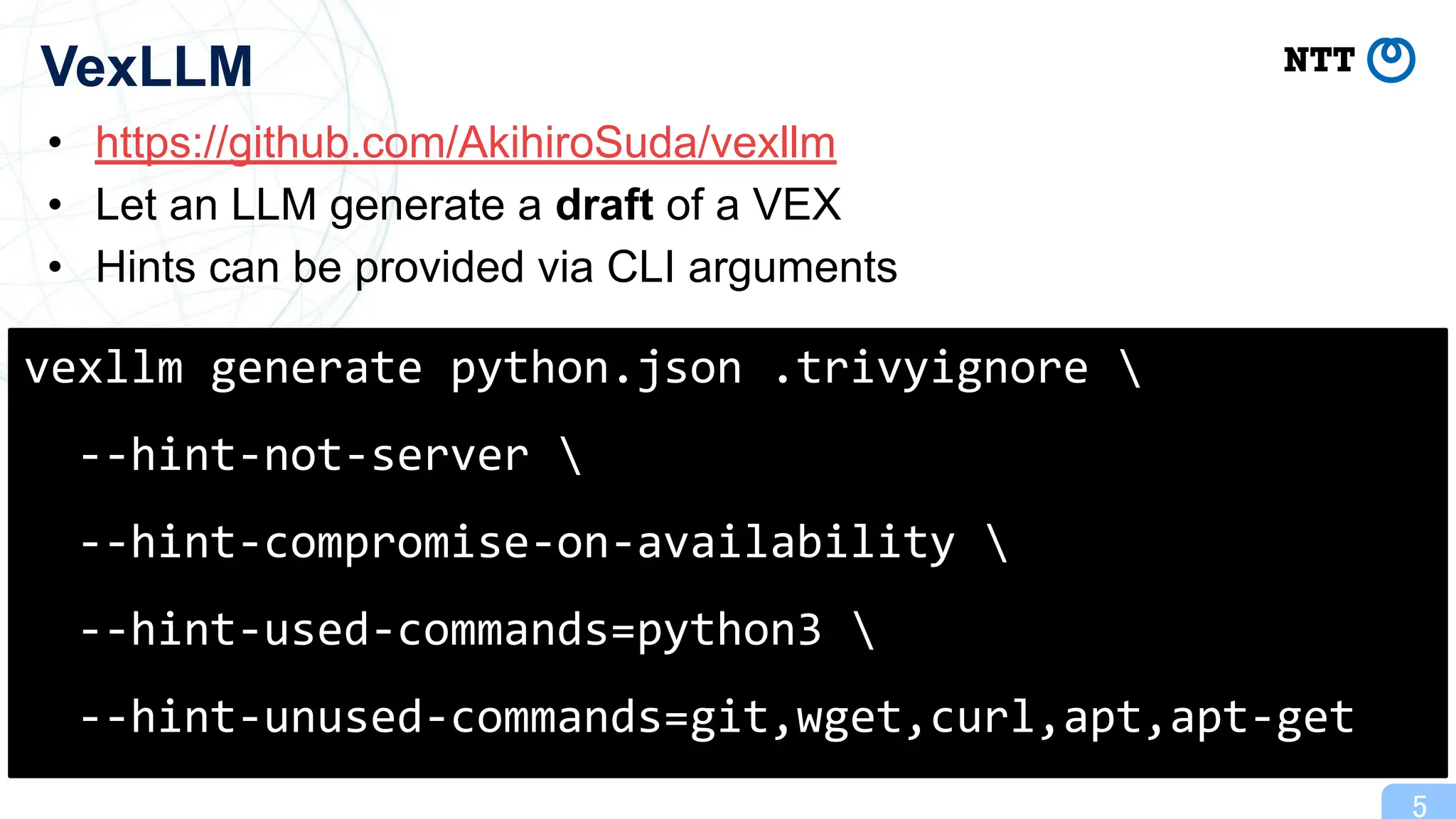
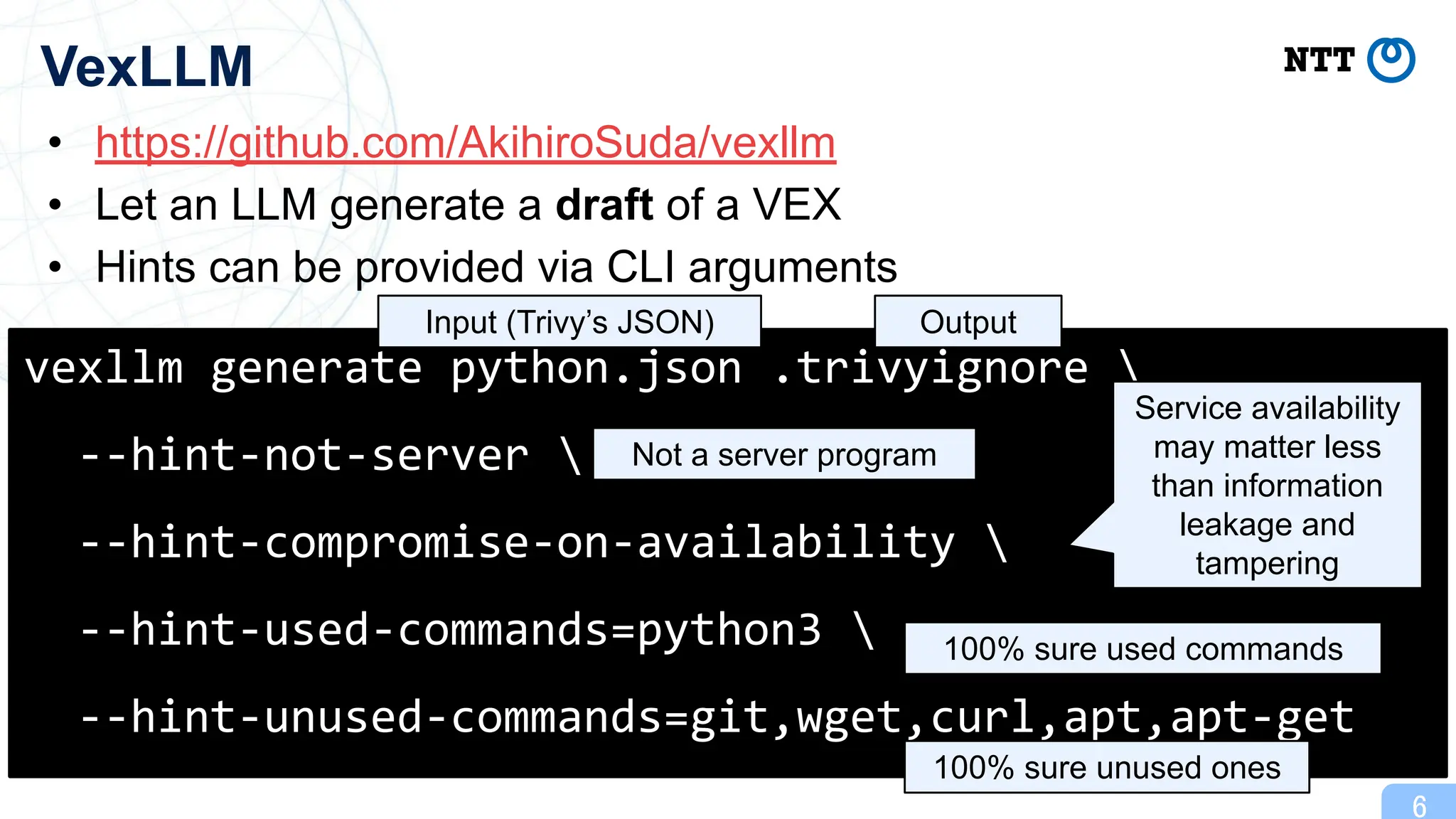
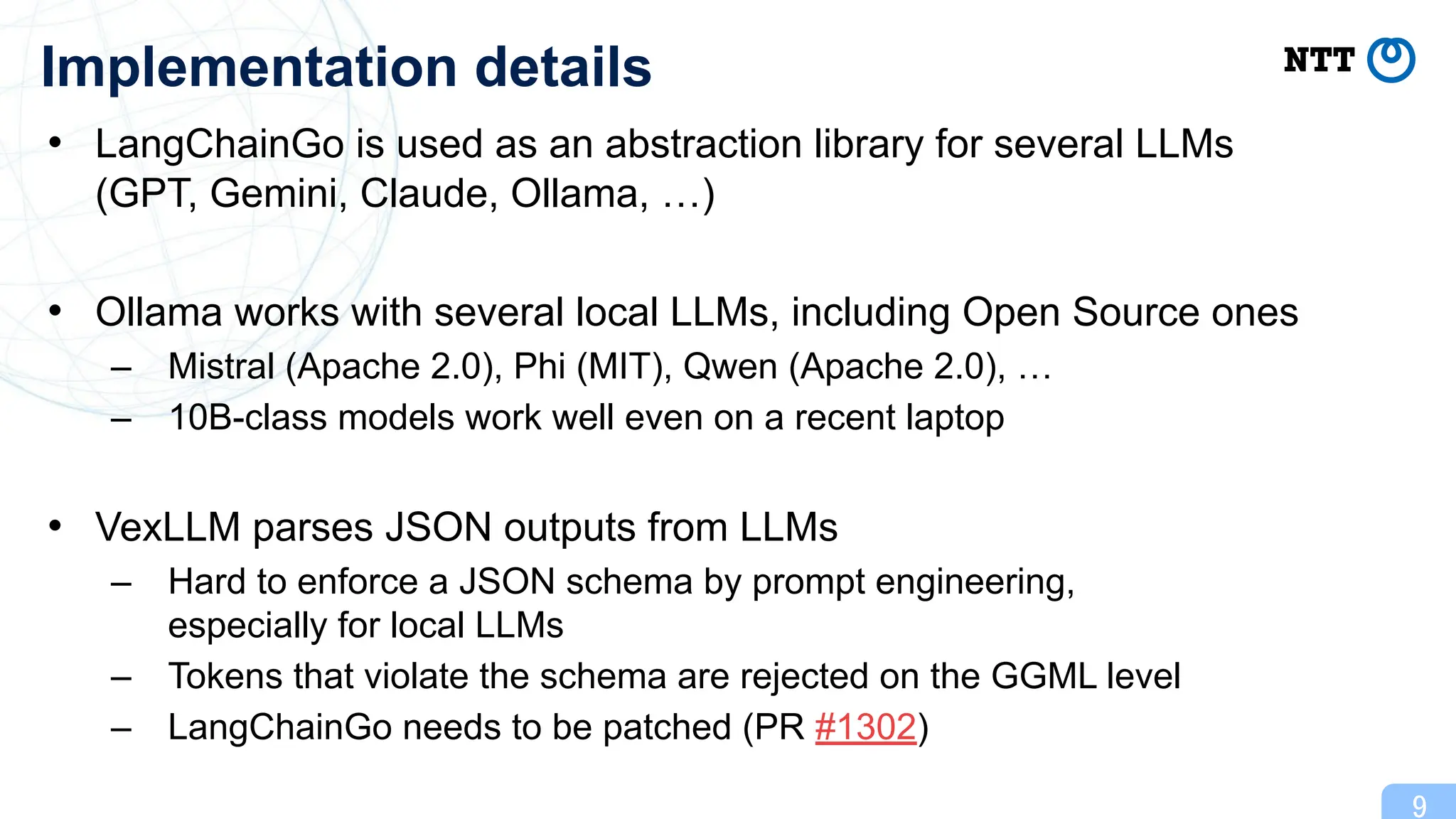
This presentation introduces VexLLM, a tool that helps writing VEX by leveraging LLMs. VexLLM is available as a plugin for Trivy.
GitHub: https://github.com/AkihiroSuda/vexllm
https://kccncjpn2025.sched.com/event/1x70c

![• Container image scanners such as Trivy
produce an extreme amount of vuln alerts
• But you do NOT need to care all of them
– You don’t actually use all the command line tools in the image
– You don’t actually use all the functions of all the libraries in the image
• Only 3% of vulns are actually exploitable [1] [2]
2
Background: too many vuln alerts](https://image.slidesharecdn.com/20250616kubeconjp2025vexllm-silencenegligiblecvealertsusingllm-250620055151-3a47410f/75/20250616-KubeCon-JP-2025-VexLLM-Silence-Negligible-CVE-Alerts-Using-LLM-pdf-2-2048.jpg)