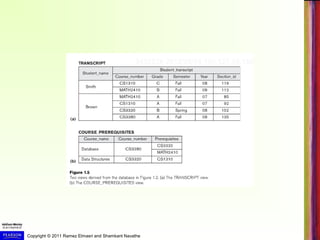
The document discusses databases and database management systems (DBMS). It provides an example of a UNIVERSITY database to illustrate how data is structured and related. Key advantages of the database approach include controlling redundancy, restricting unauthorized access, and enforcing integrity constraints. The history of database applications is reviewed, from early hierarchical and network systems to current technologies like XML, no-sql, and using databases on the web.