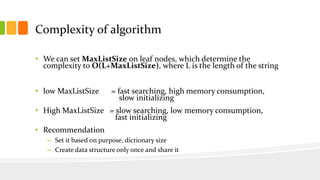
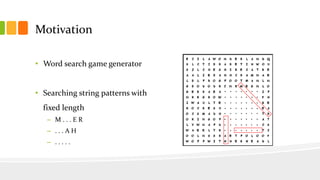
The document presents a fast exact string pattern-matching algorithm for fixed length patterns, designed to improve the efficiency of word search games. It details the motivation, problem definition, existing solutions, and the implemented algorithm, highlighting its dynamic in-memory data structure achieving approximately O(1) complexity. Testing results indicate the new algorithm is over 1300 times faster than naive methods, with varying memory consumption and initialization times based on list size settings.

![Problem Definition
• Design fast in-memory data structure (class)
• Requirements
– fast searching, if it is possible with O(1) complexity
– each founded word get only once
– each founded word must be randomly chosen
– founded word have to match the pattern
class Model
FastStringPatternSearch
+ FastStringPatternSearch(String[], Random)
+ FastStringPatternSearch(String[])
+ reset() : void
+ searchPattern(String) : String](https://image.slidesharecdn.com/2013transcomtakac-130827070632-phpapp02/85/Fast-Exact-String-Pattern-Matching-Algorithm-for-Fixed-Length-Patterns-4-320.jpg)


![Root
• 3 dimensional matrix of root nodes with linked shuffled lists
– alphabet dimension
– word length dimension
– character position dimension
• Example
– We put the word “NAUTICAL” into nodes [N][8][1], [A][8][2], [U][8][3], …,
[L][8][8]
– When we search for pattern “. . U . . . . .”, we are looking into root node [U][8][3]
where we find word “NAUTICAL” in linked list](https://image.slidesharecdn.com/2013transcomtakac-130827070632-phpapp02/85/Fast-Exact-String-Pattern-Matching-Algorithm-for-Fixed-Length-Patterns-7-320.jpg)


![Searching algorithm
• Searching for pattern “. . T . E R . .”
1. Get the first defined character, pattern length and the position of first
defined character (T, 8, 3). Get a node of three-dimensional array data structure
at [character][length][position] ([T][8][3]). Continue to step 2 with this node.
2. If a node is null, string with this pattern does not exists. – END.
If a node is not null and a node has not children (leaf node) or pattern has no
further defined characters, find the first string in a node list which matches the
pattern. Return founded string or null if no string matches the pattern. – END.
If a node is not null and a node has children (not leaf node), take the next
defined character in pattern (E, position 5) and access two-dimensional array of
children nodes of node at element [position][character] ([5][E]), go to step 2
with the given node.](https://image.slidesharecdn.com/2013transcomtakac-130827070632-phpapp02/85/Fast-Exact-String-Pattern-Matching-Algorithm-for-Fixed-Length-Patterns-10-320.jpg)