Embed presentation
Downloaded 282 times




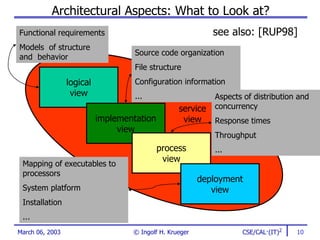


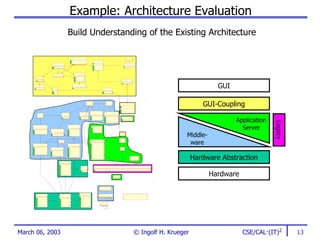



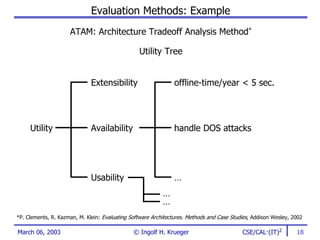










The document discusses the evaluation of software architectures, emphasizing the importance of stakeholder involvement, identification of goals, and understanding architectural views. It outlines the methods and metrics used for evaluation and offers strategies for migrating to improved architectures. The aim is to enhance system quality, mitigate risks, and ensure alignment with business objectives across development teams.



























