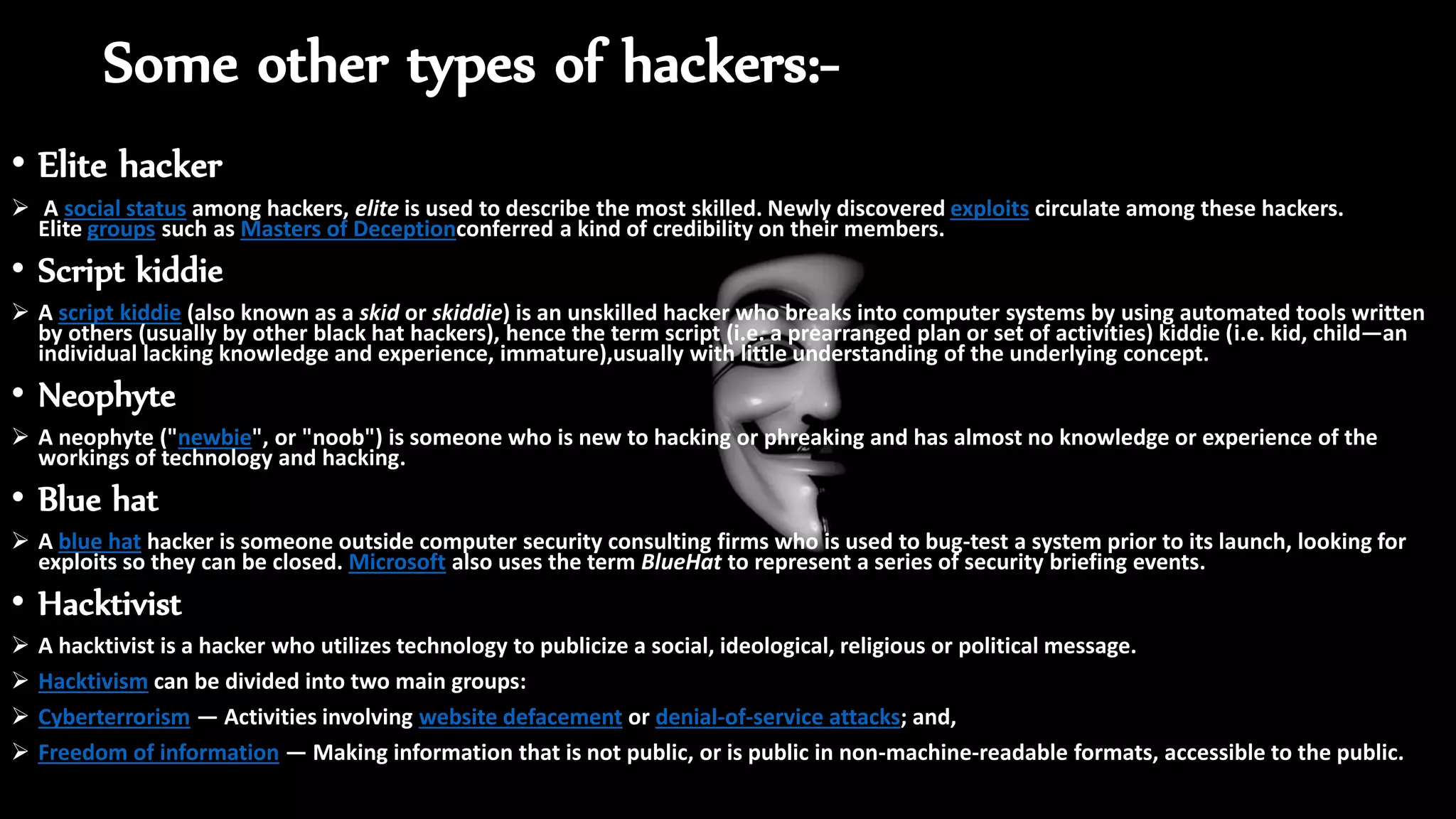
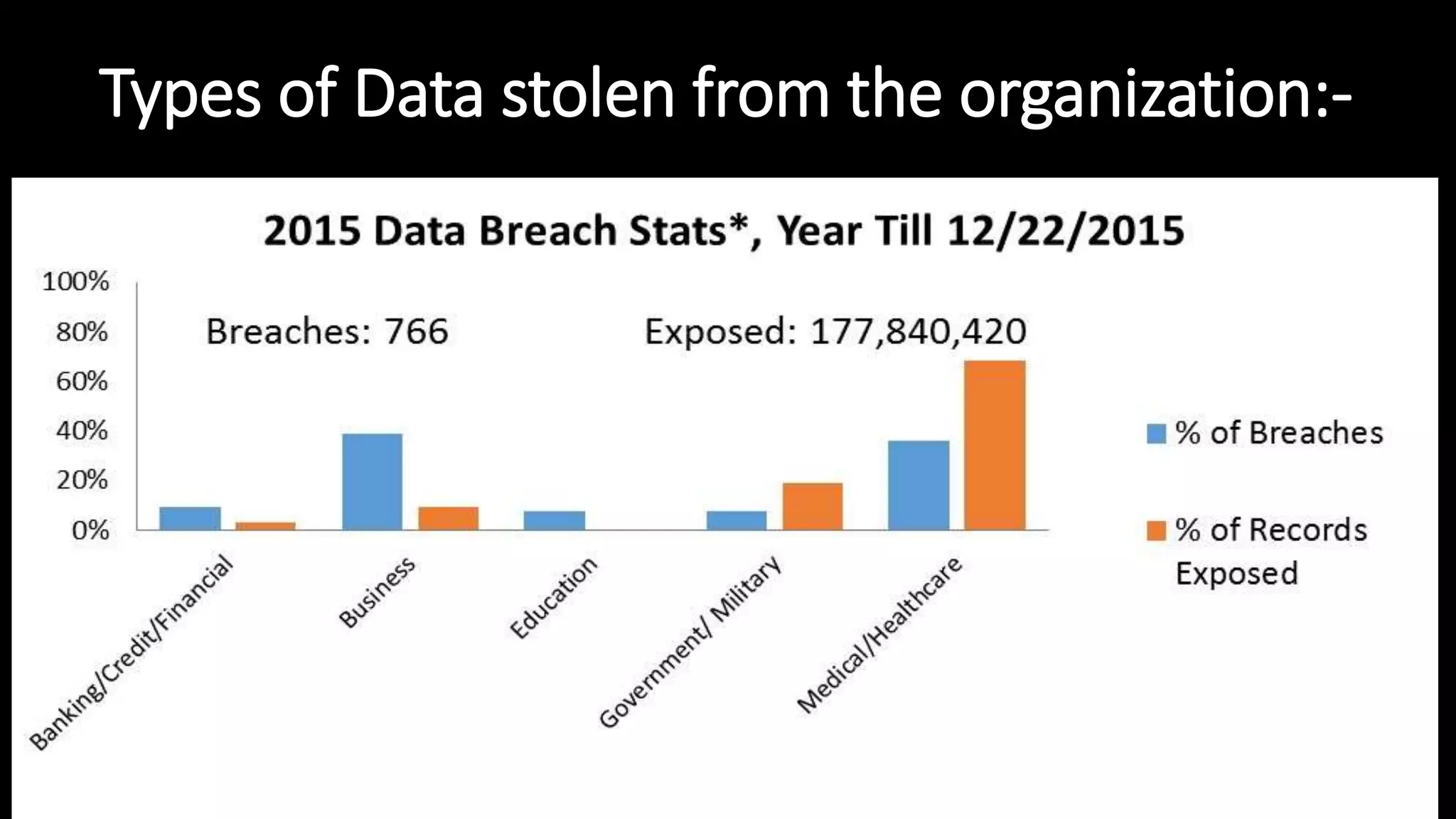
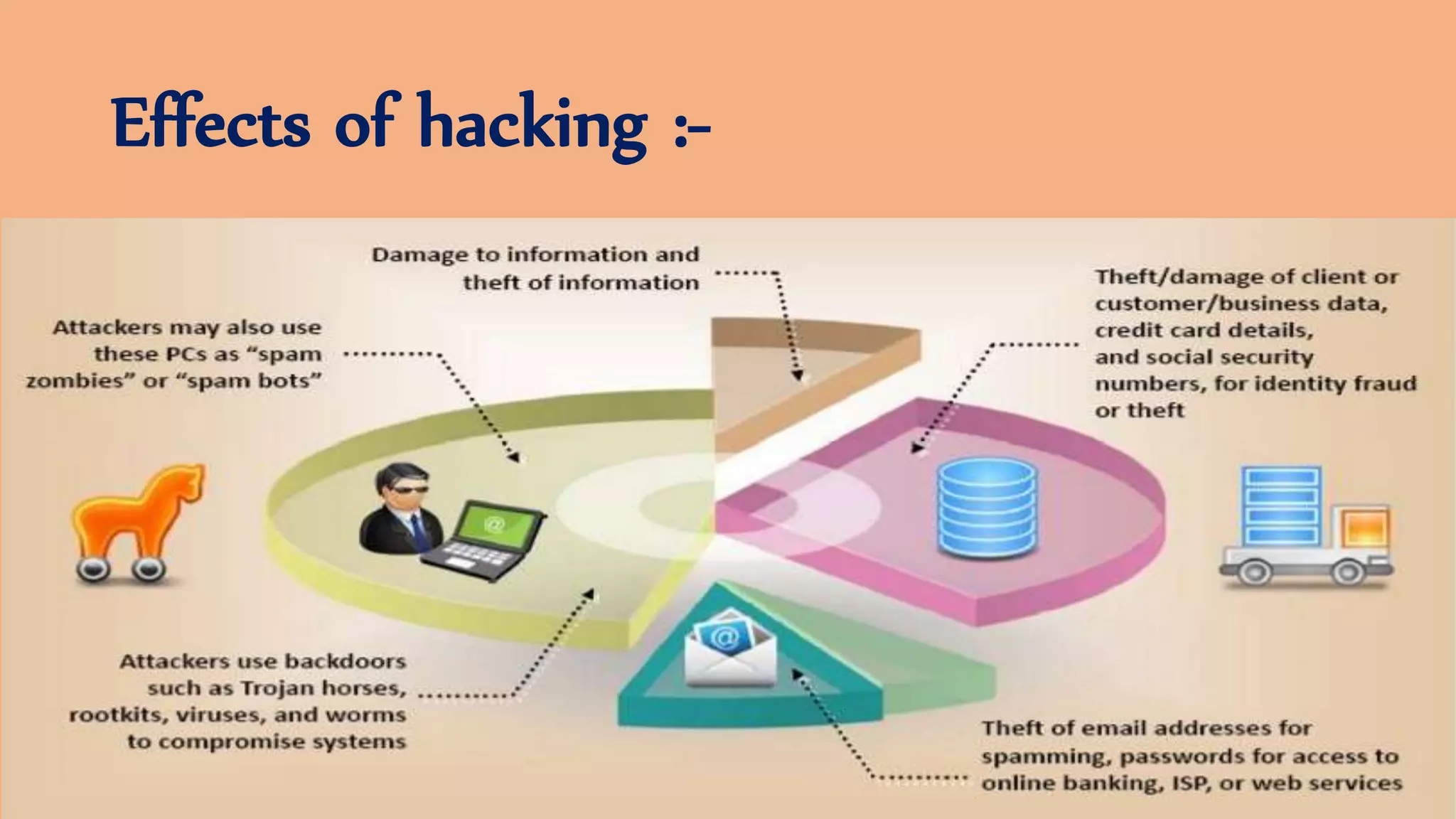
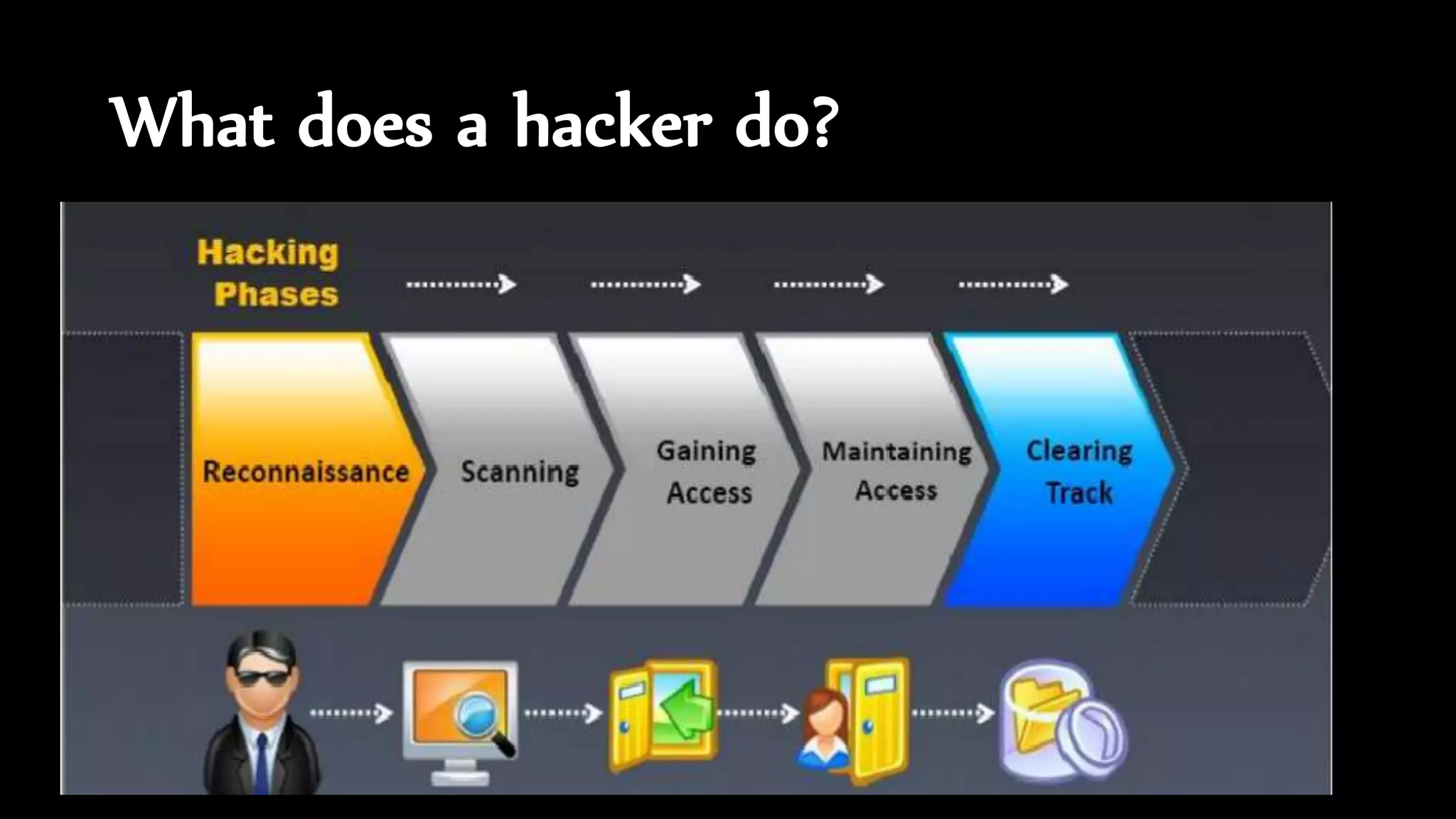
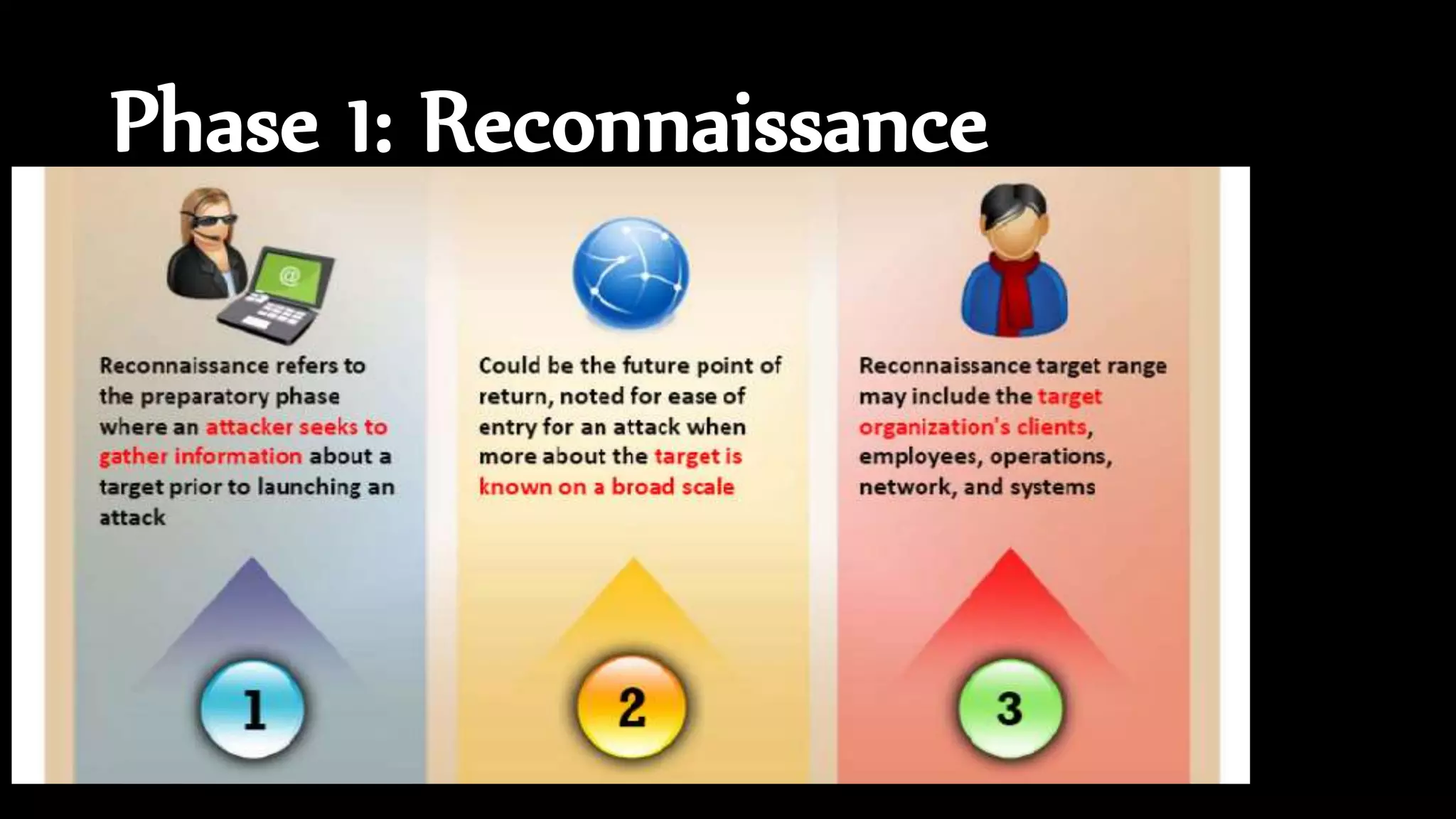
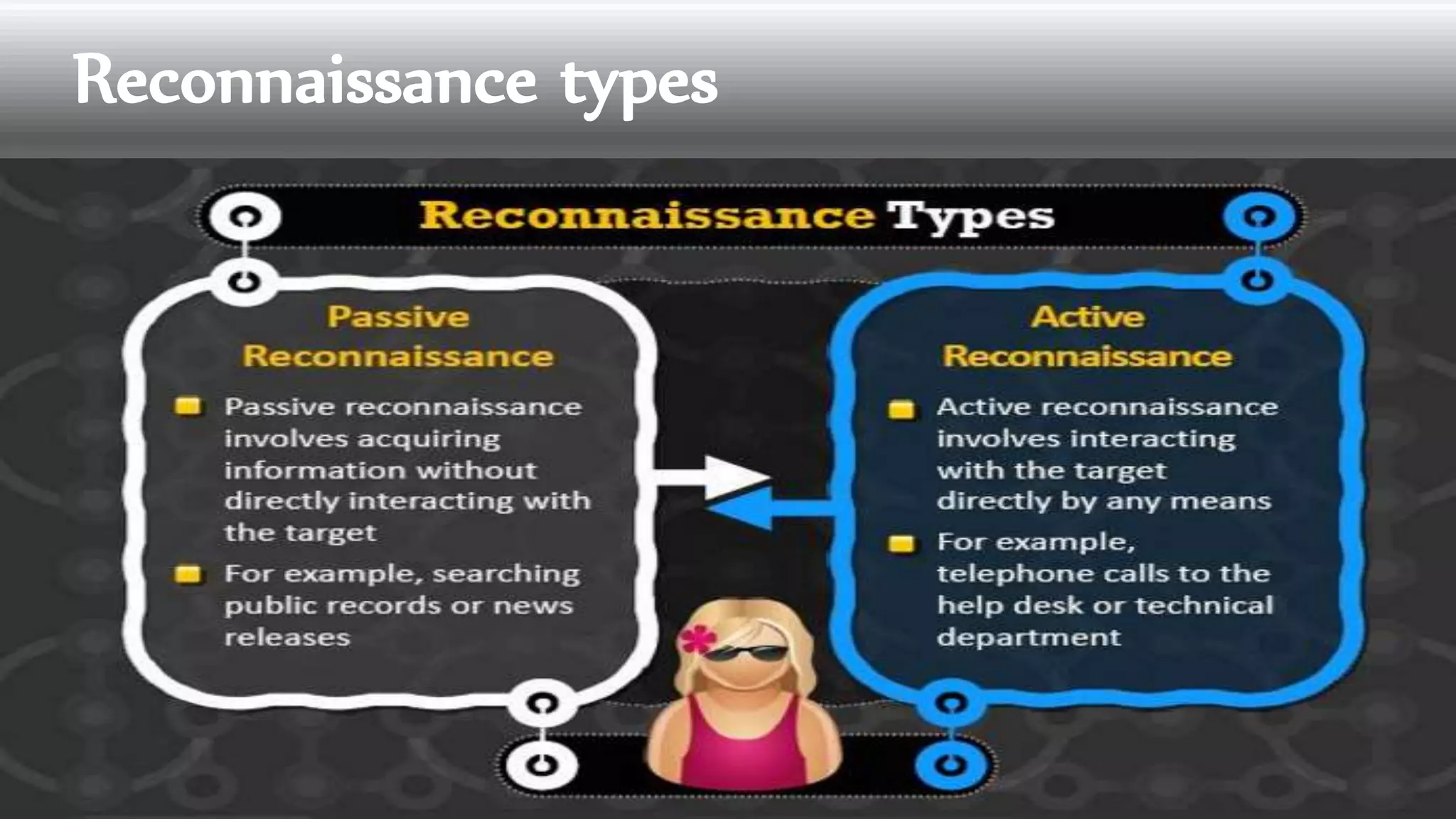
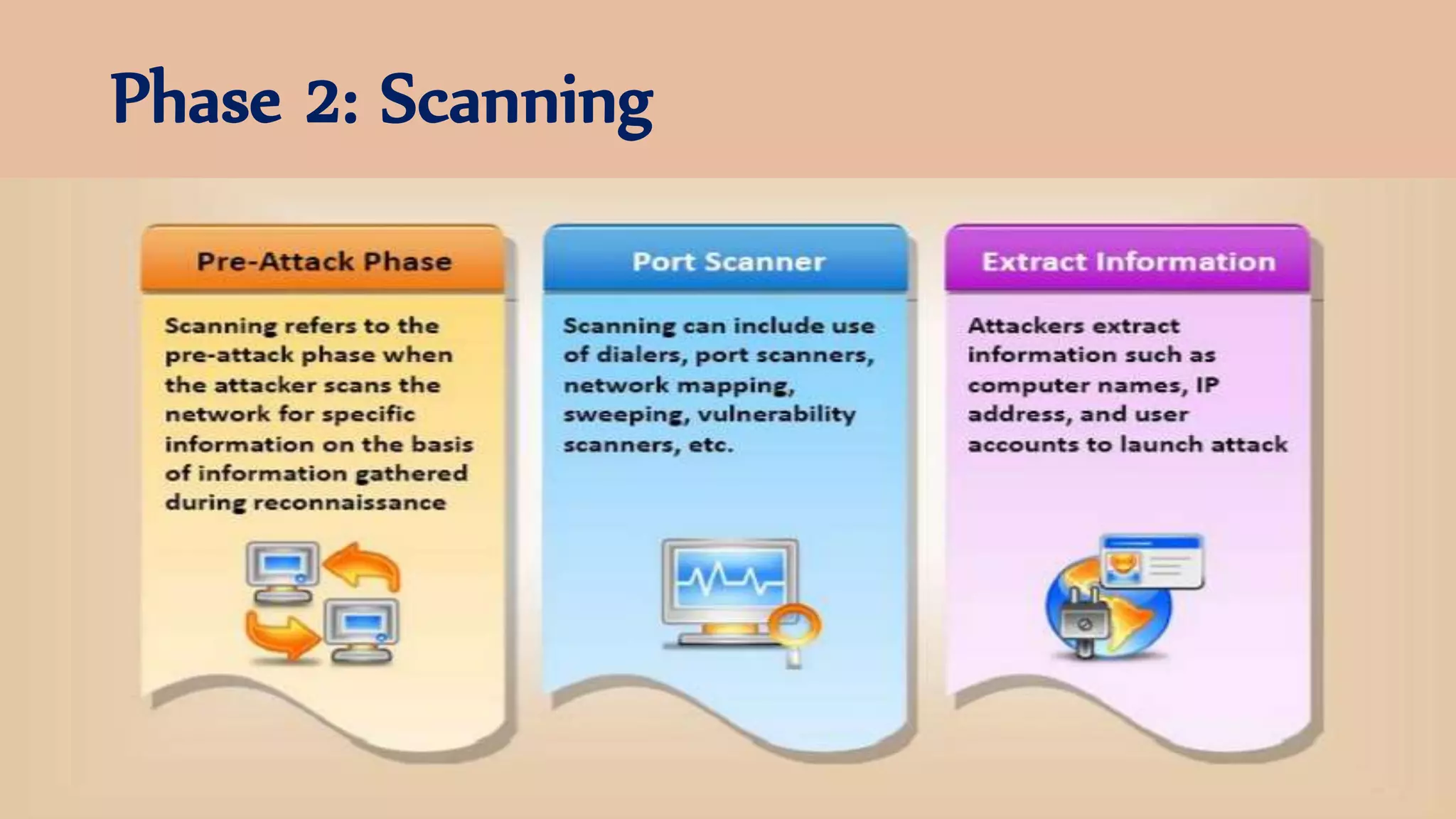
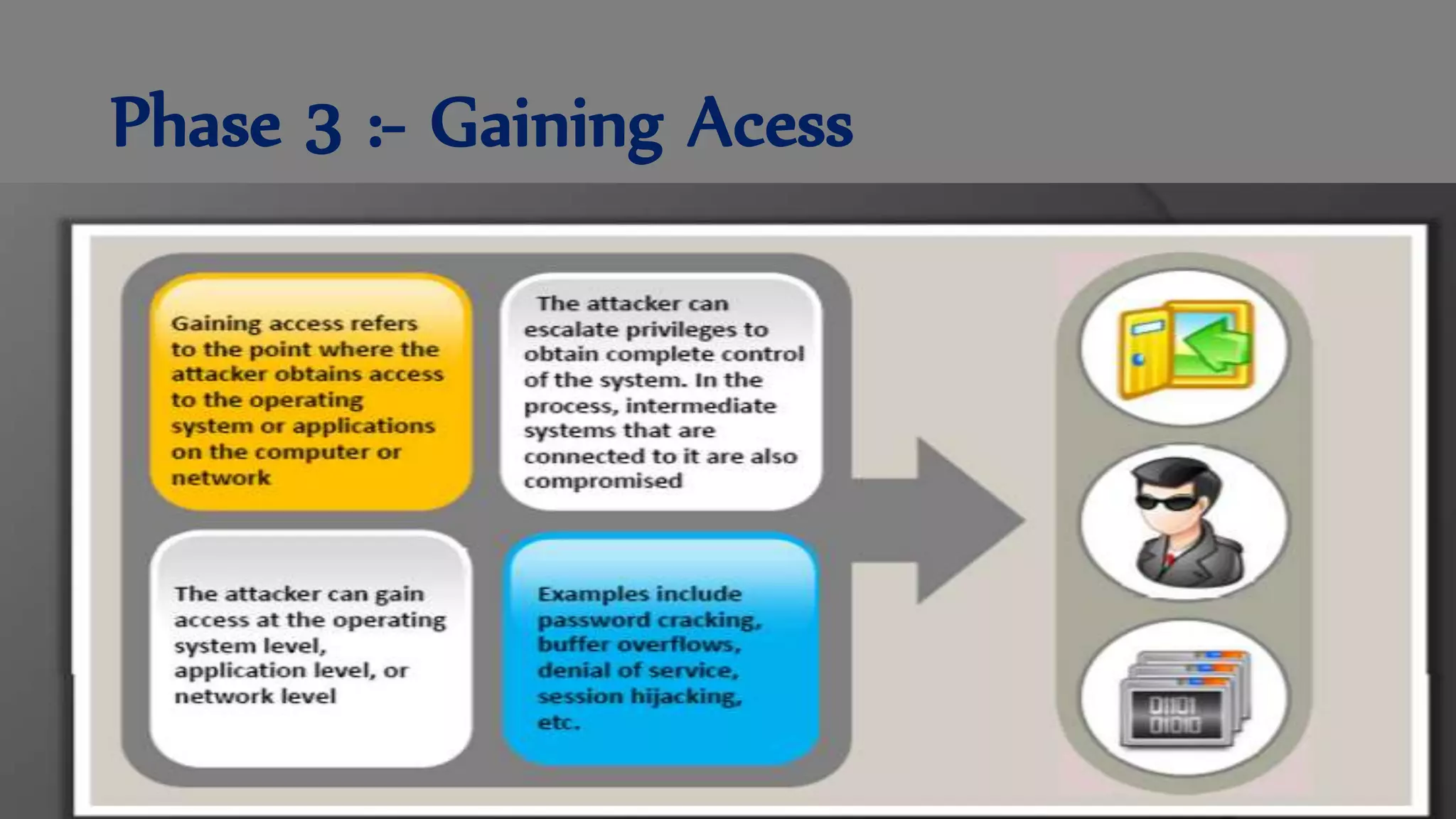
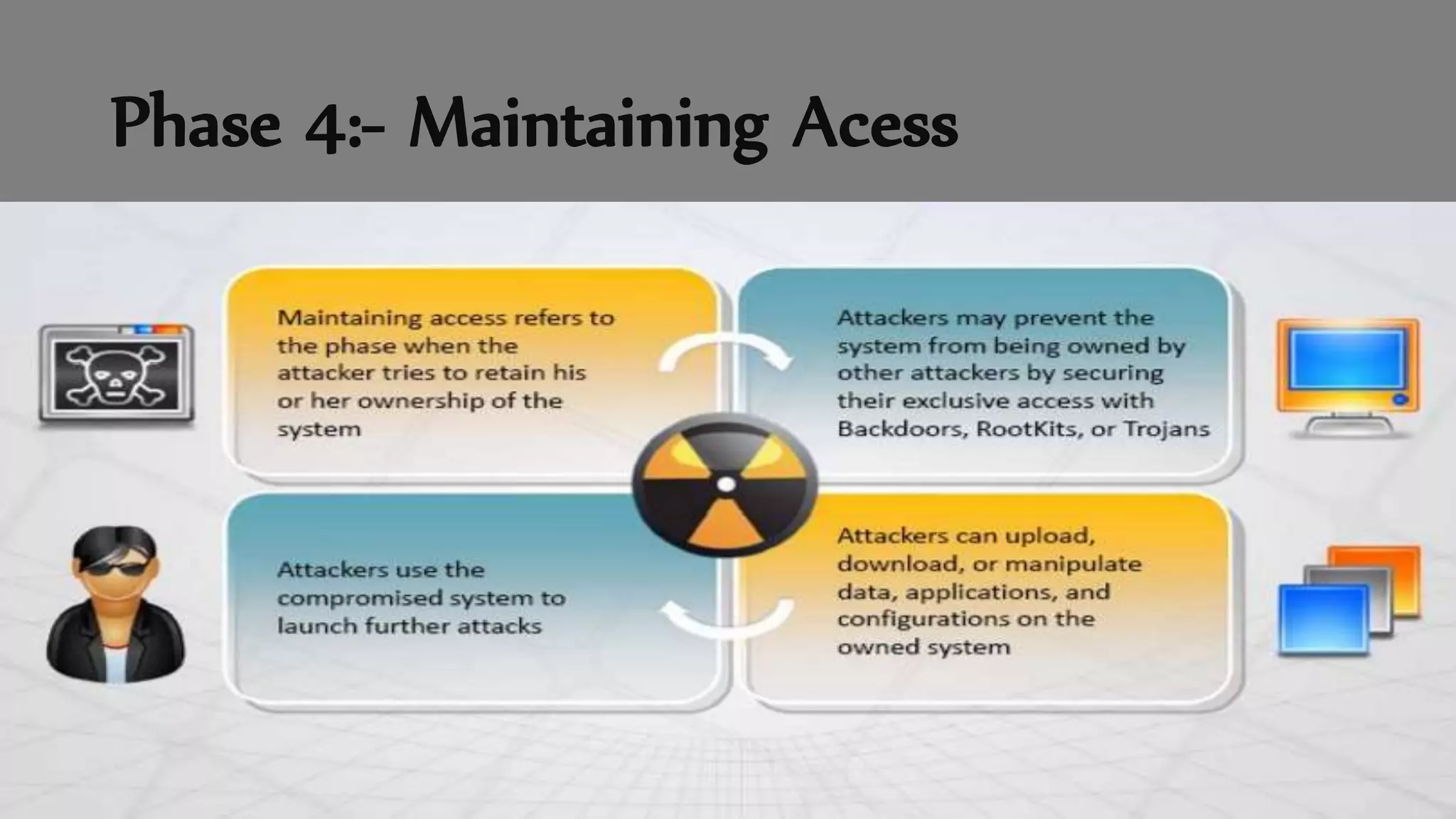
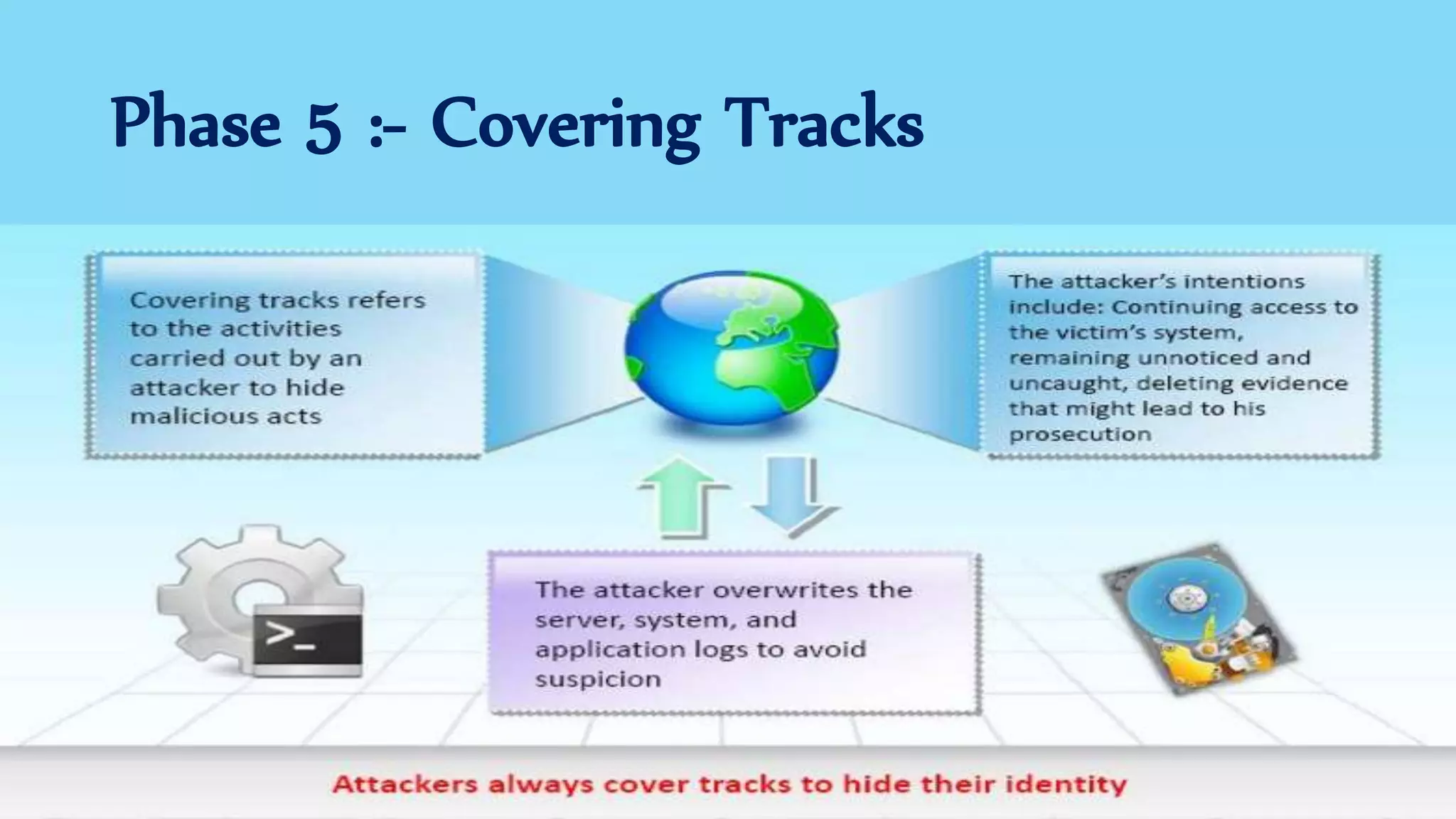
The document discusses ethical hacking, defining the terminology and various types of hackers, including black hat, white hat, and gray hat hackers. It also outlines the history of hacking, notable figures, and different hacking methods such as social engineering and phishing attacks. The text emphasizes the distinction between ethical hacking for security improvement and illegal activities for personal gain.