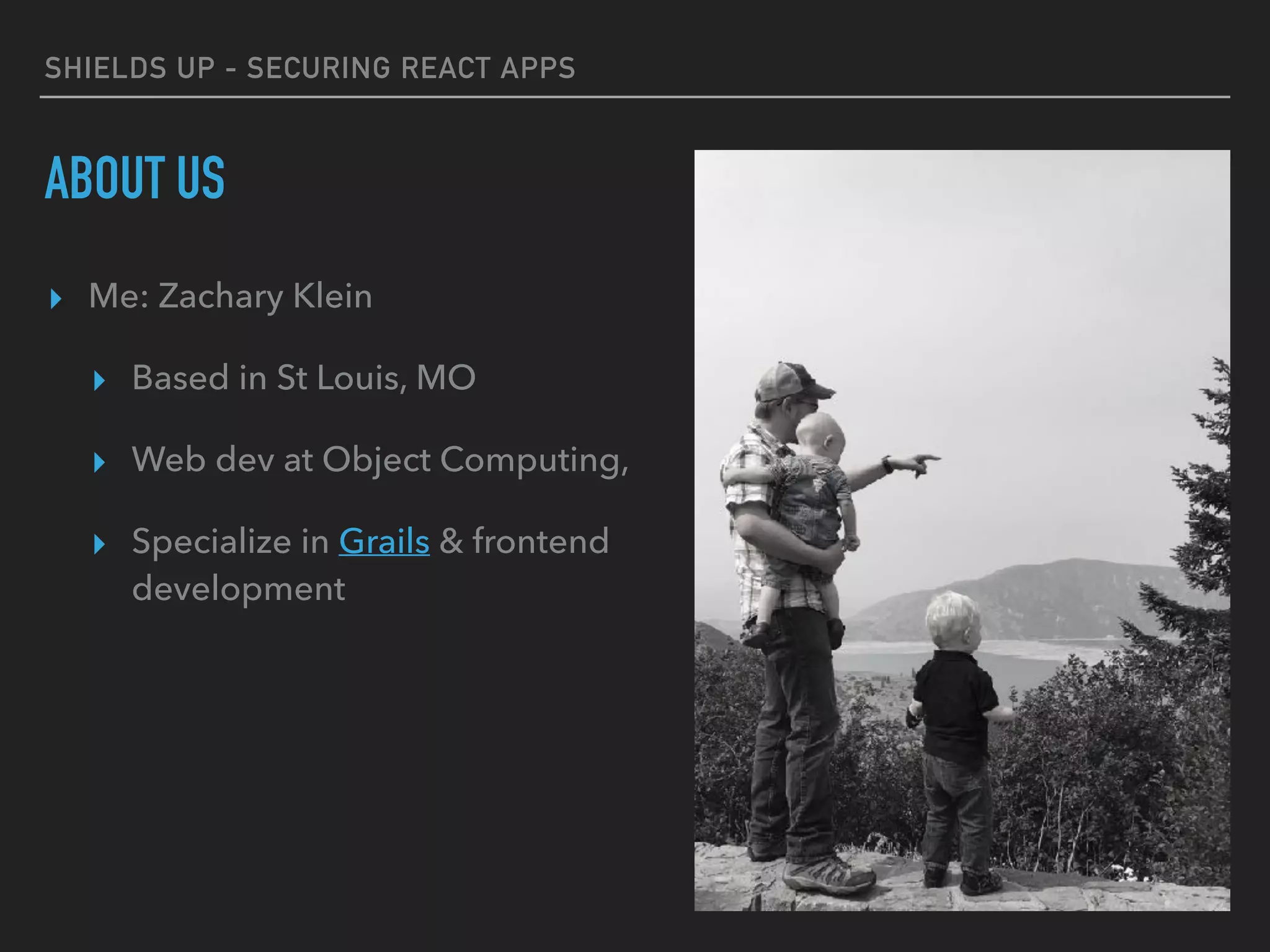
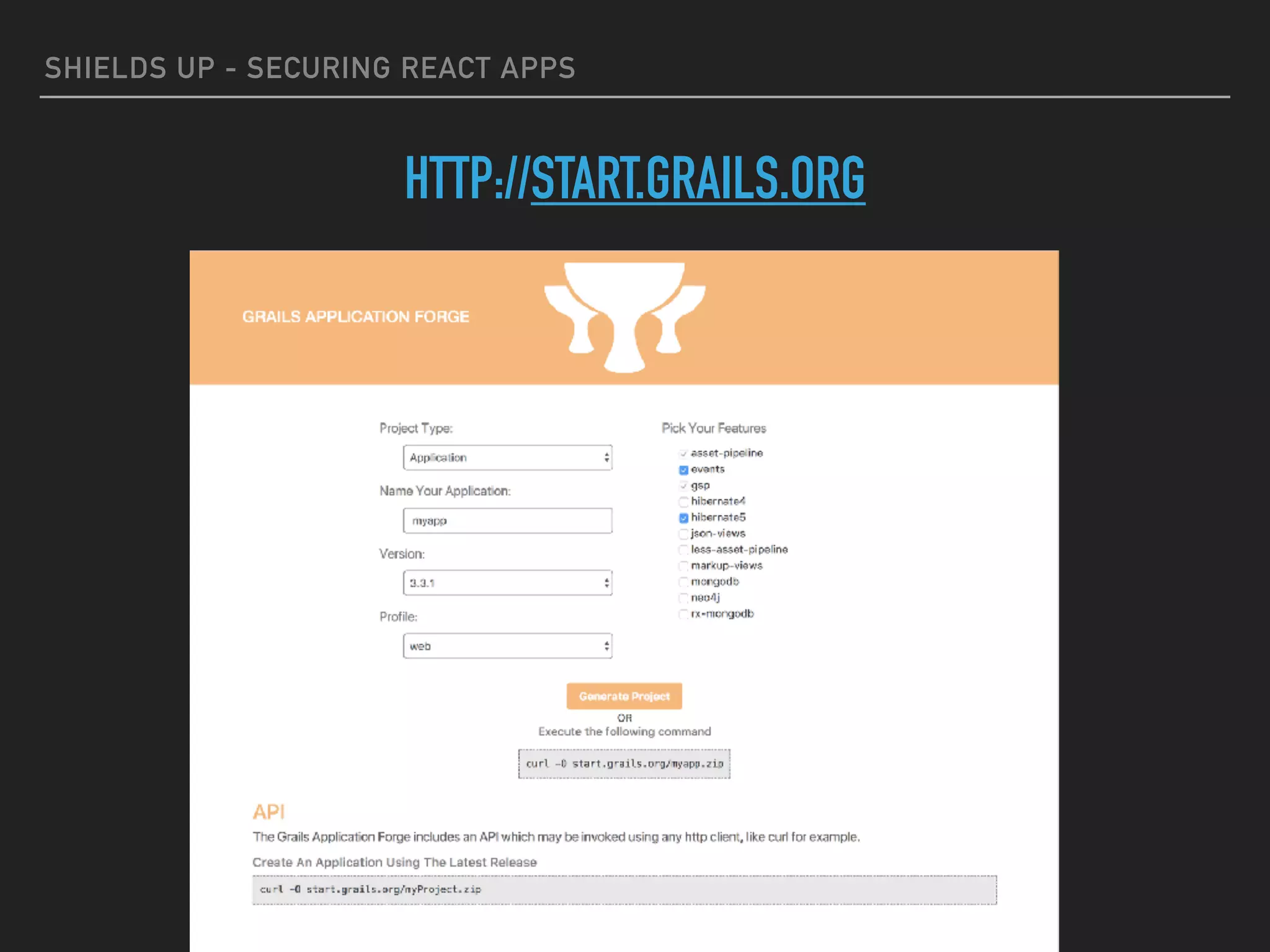
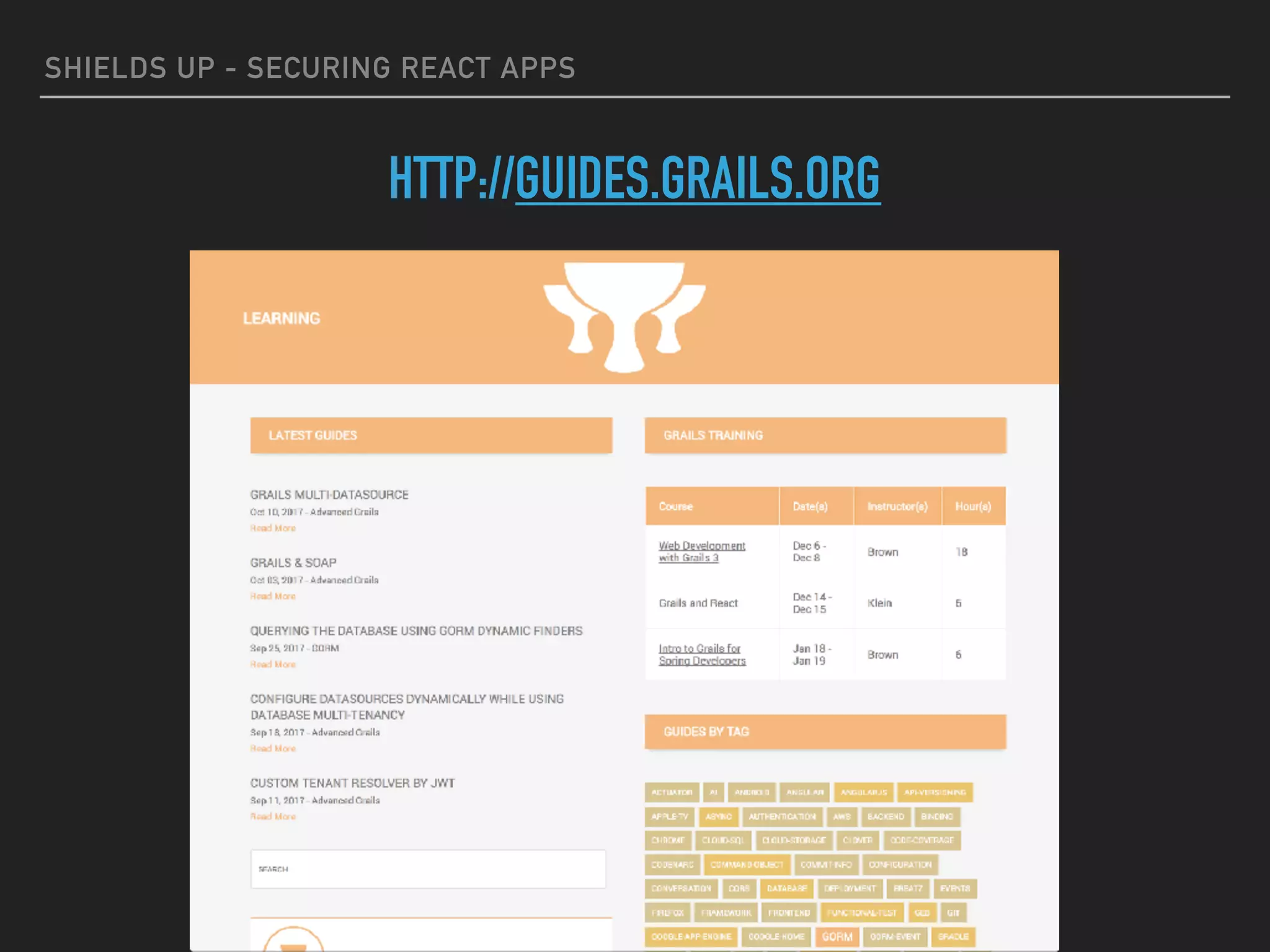
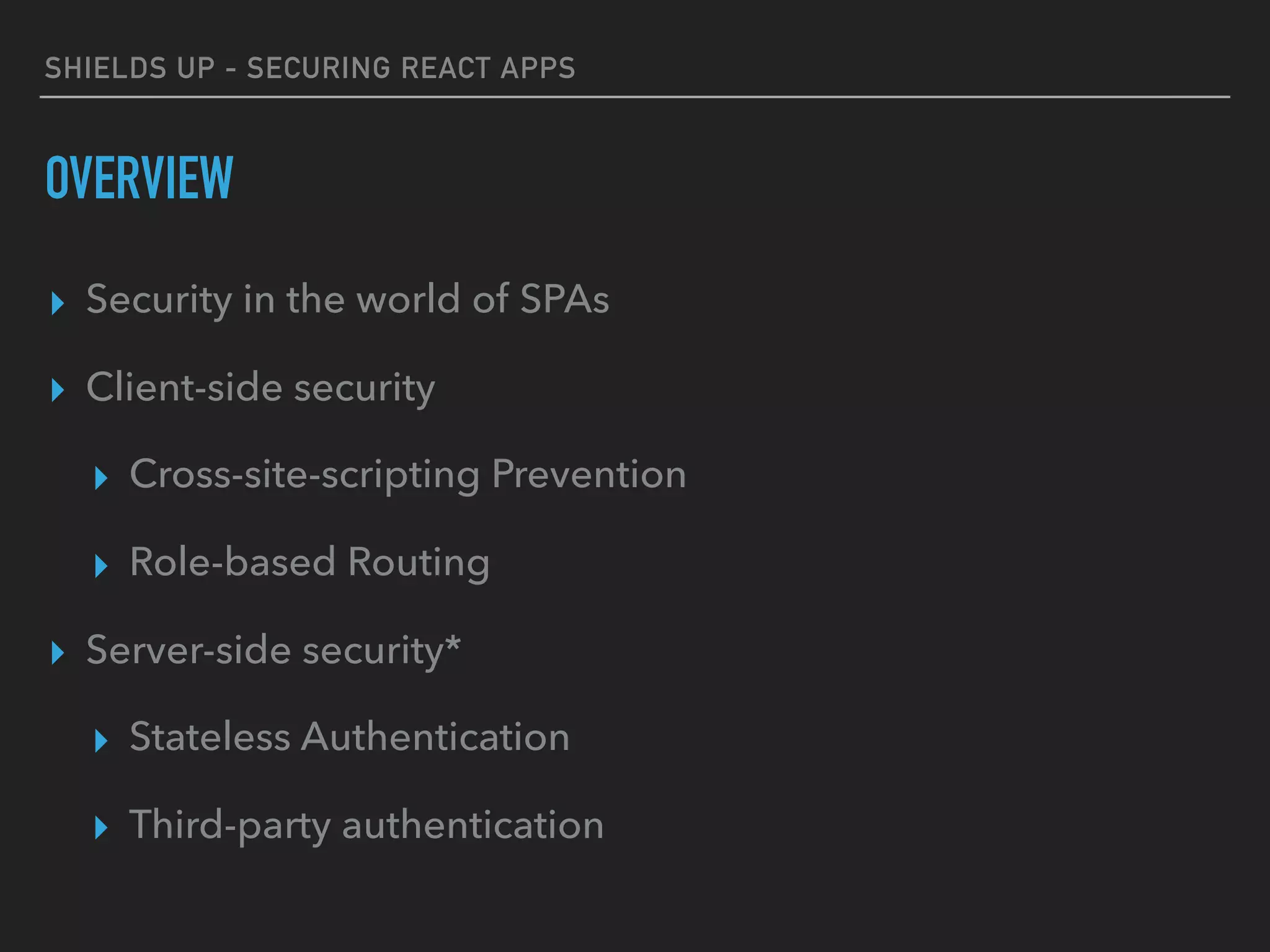
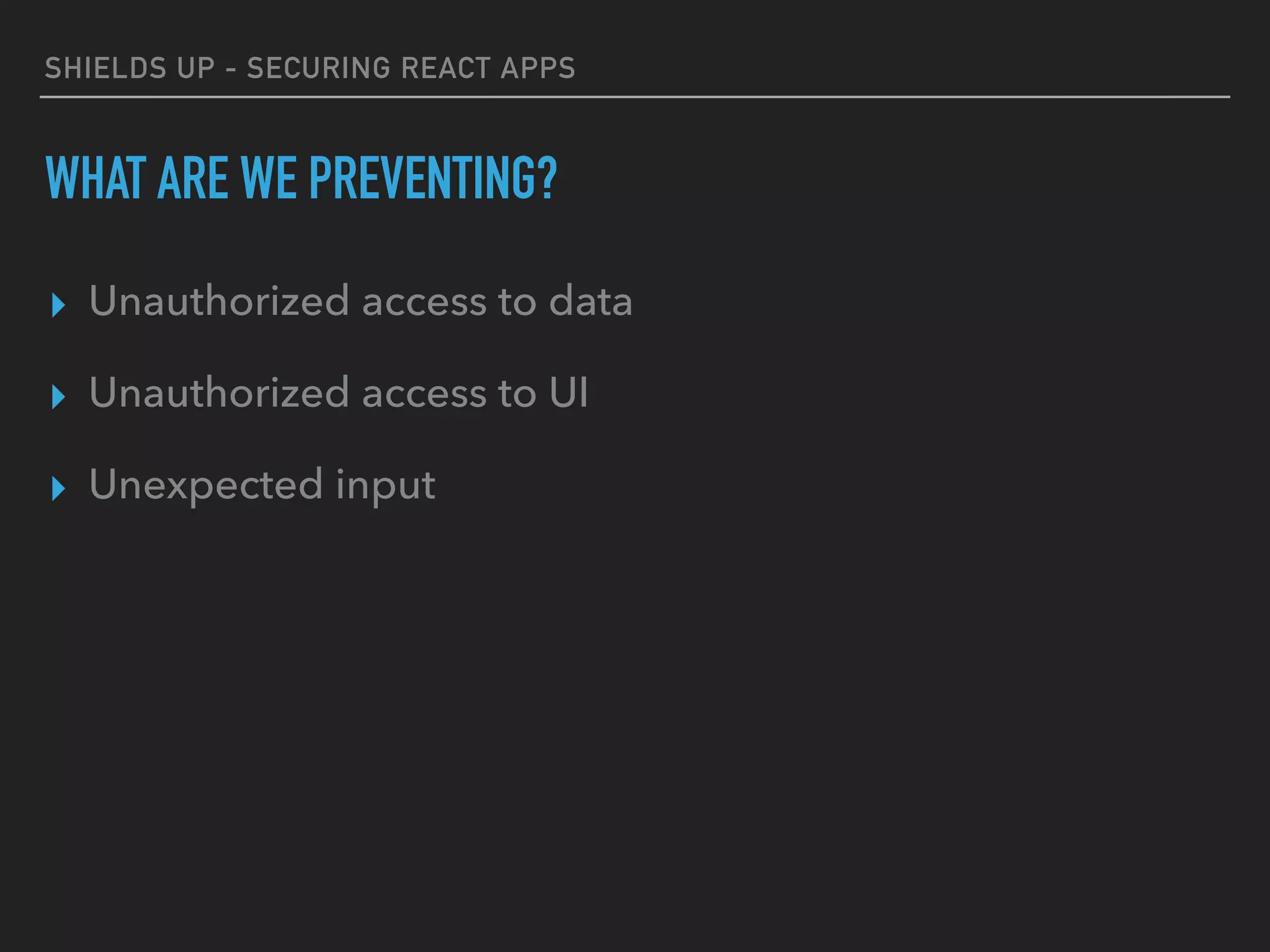
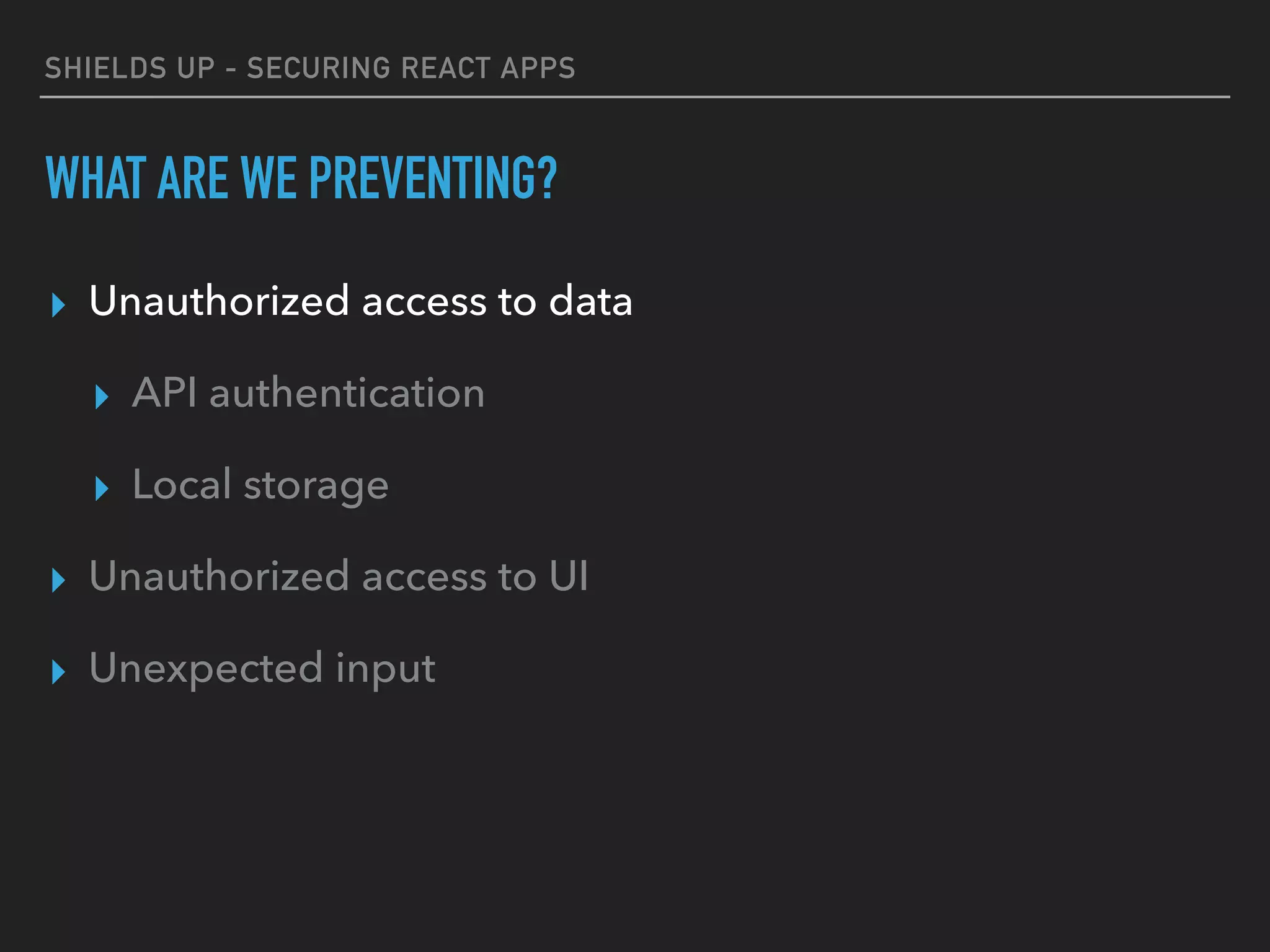
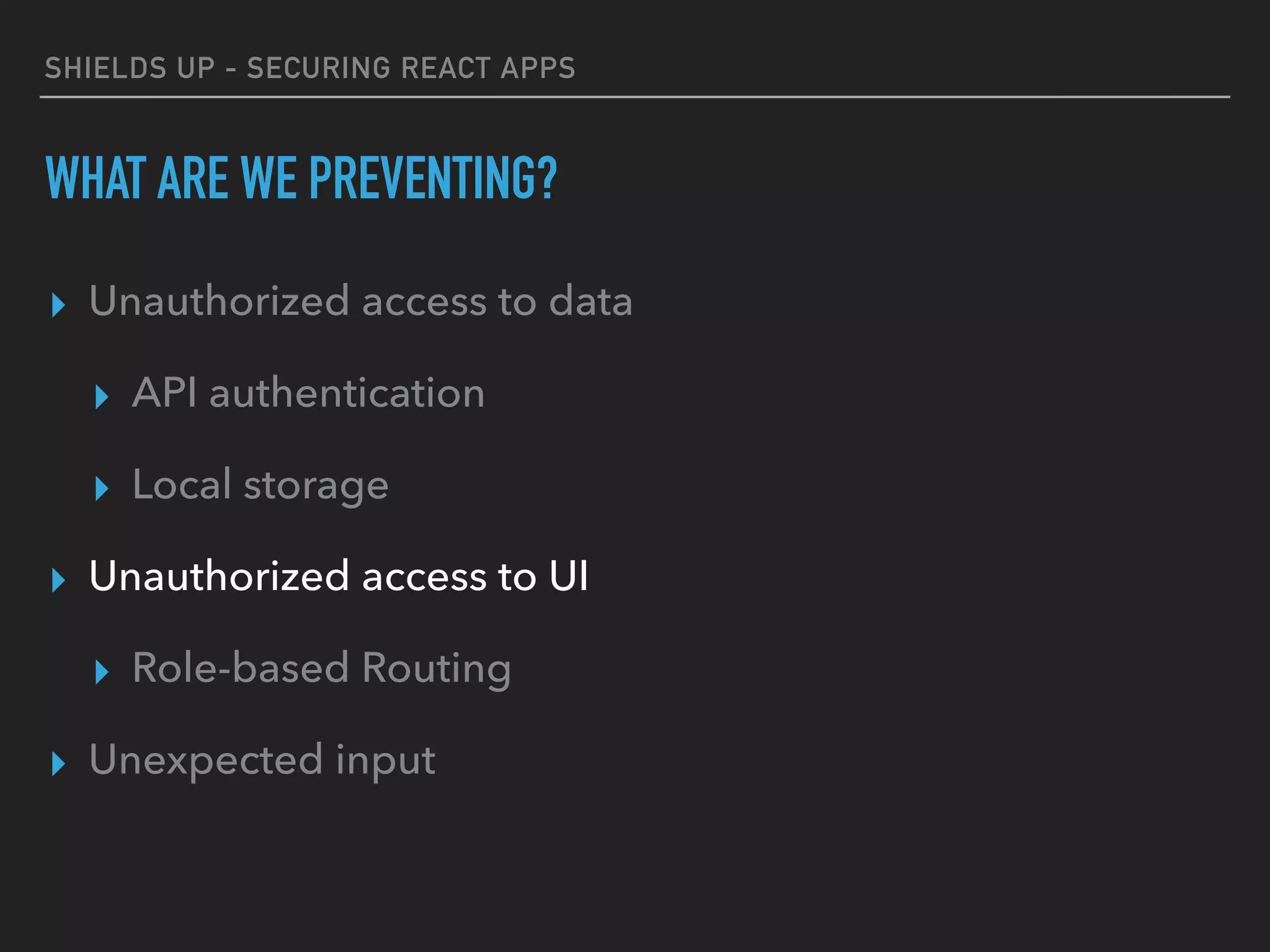
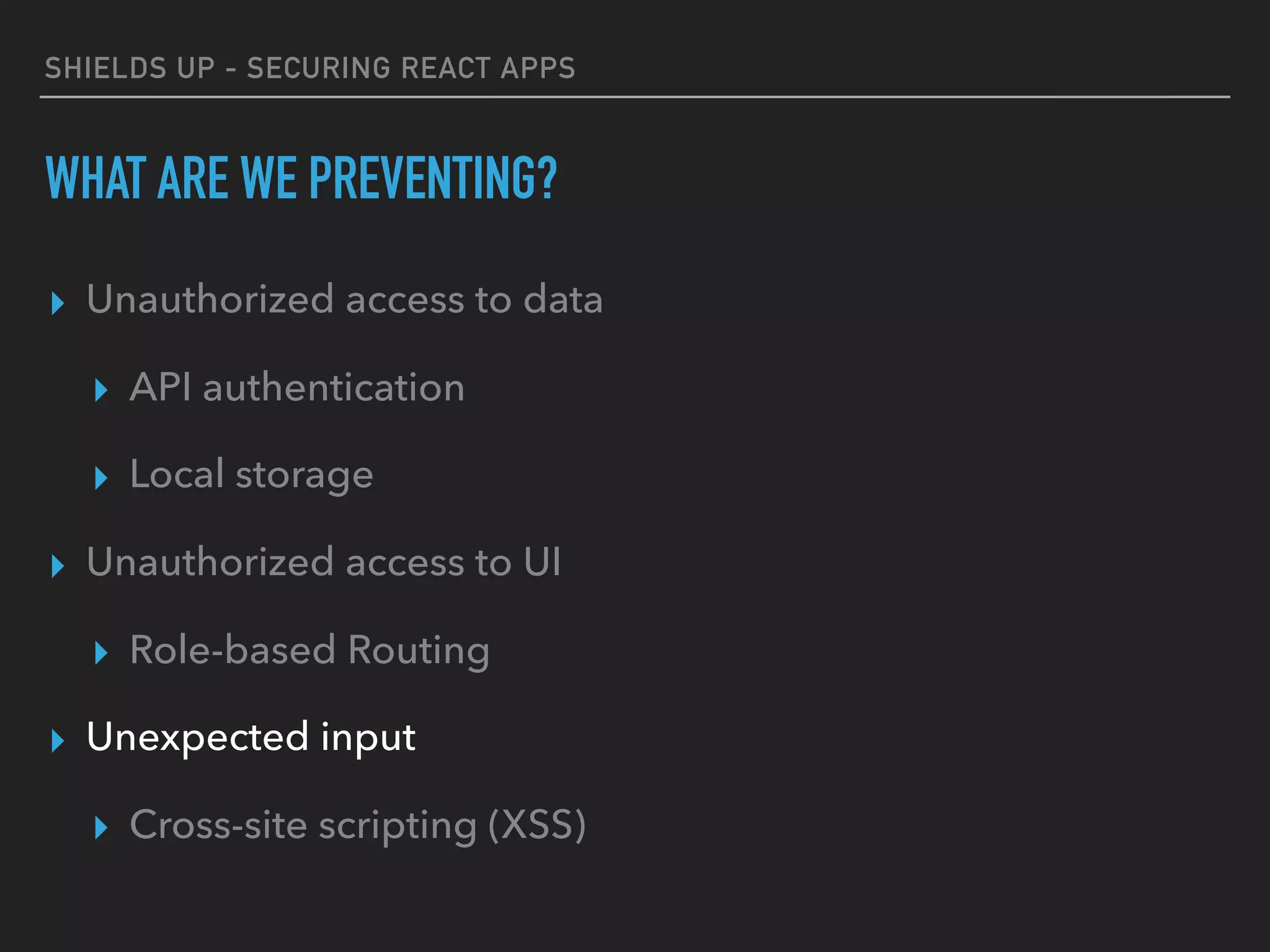
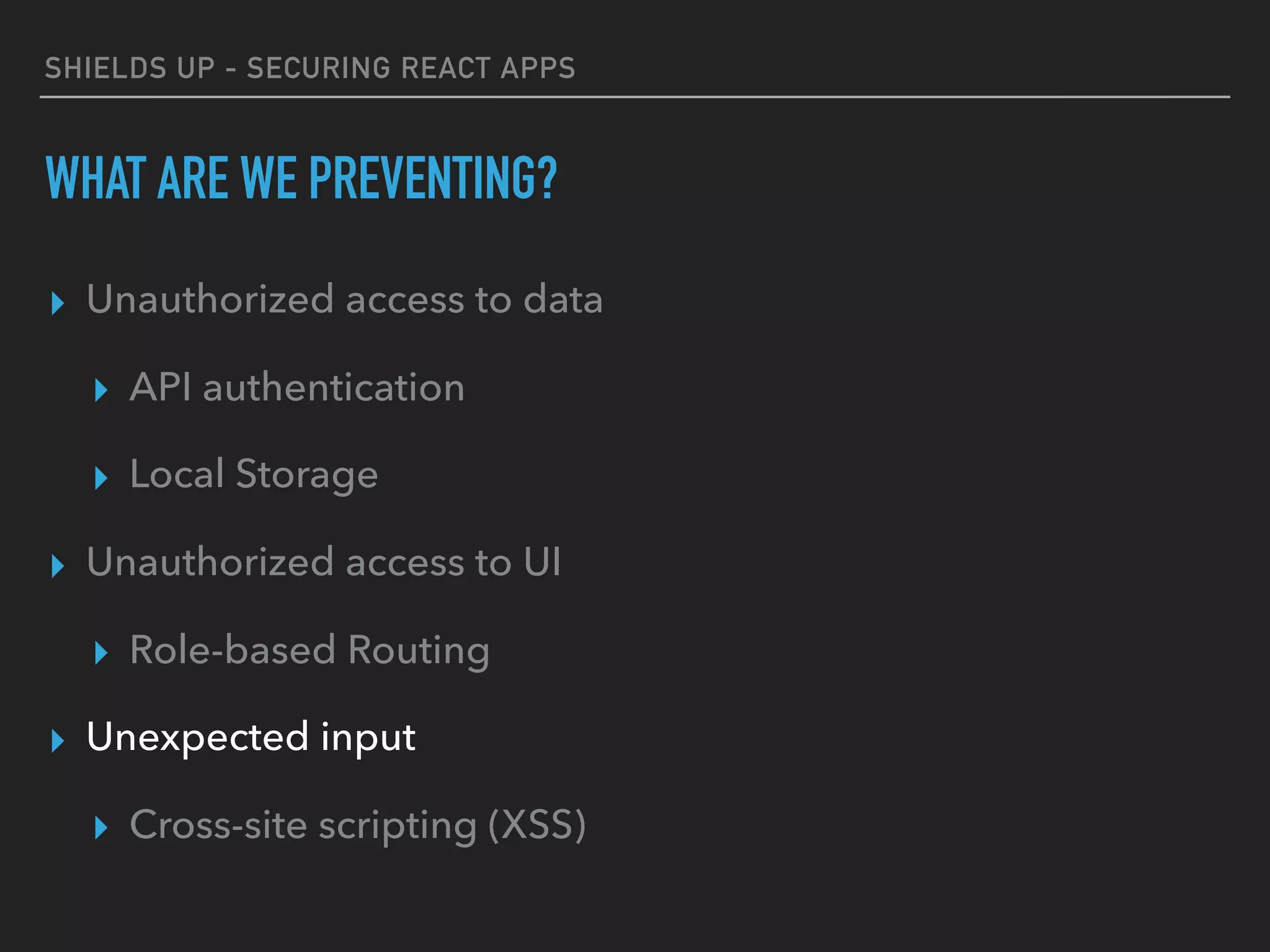
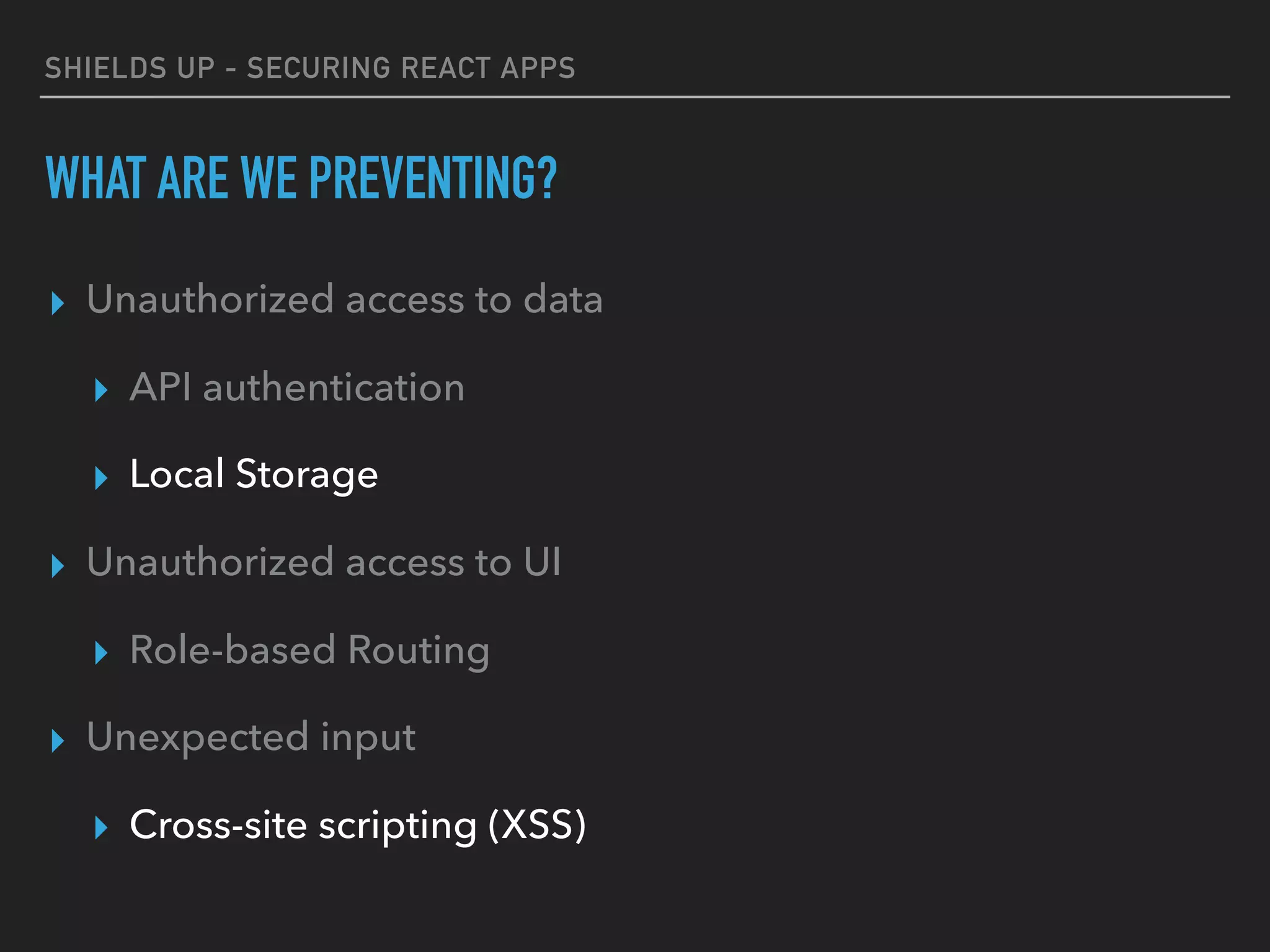
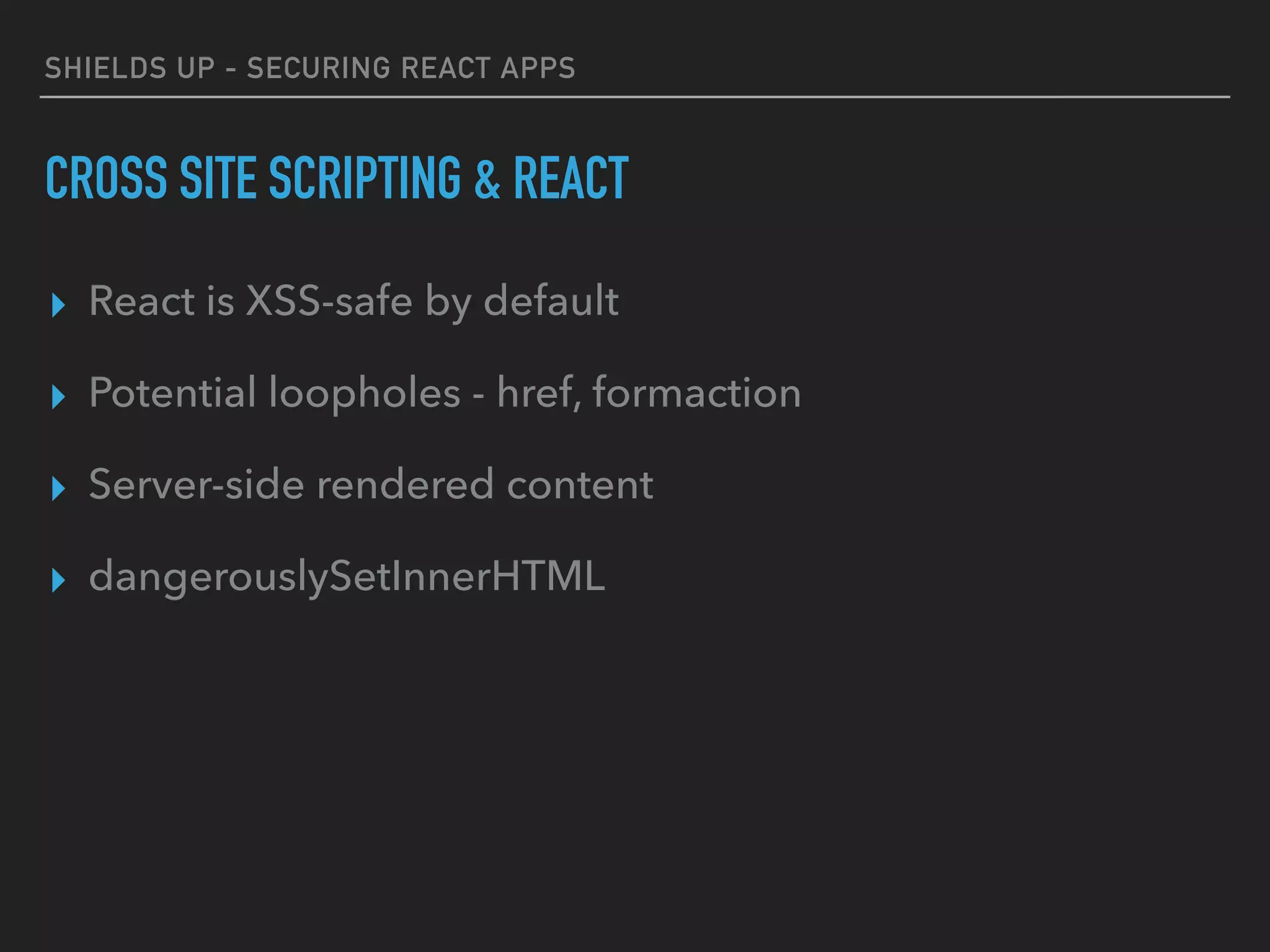
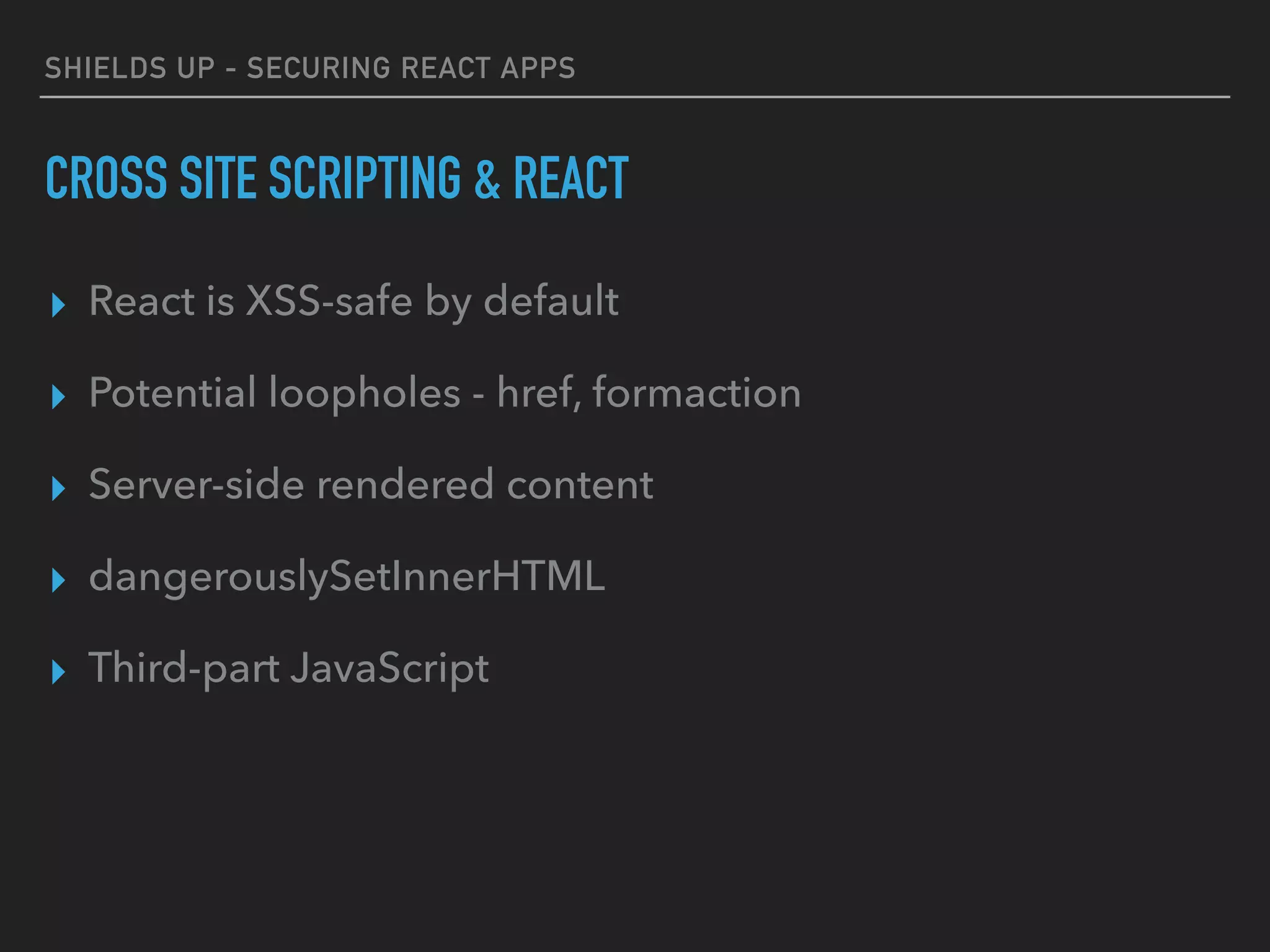
The document provides a comprehensive guide on securing React applications, emphasizing the importance of client-side security, prevention of unauthorized access, and effective role-based routing. It covers various security measures including cross-site scripting (XSS) protection, API authentication, session management, and the use of third-party authentication methods like OAuth2 and Auth0. Additionally, it highlights best practices for maintaining security while developing single-page applications (SPAs).


![SHIELDS UP - SECURING REACT APPS
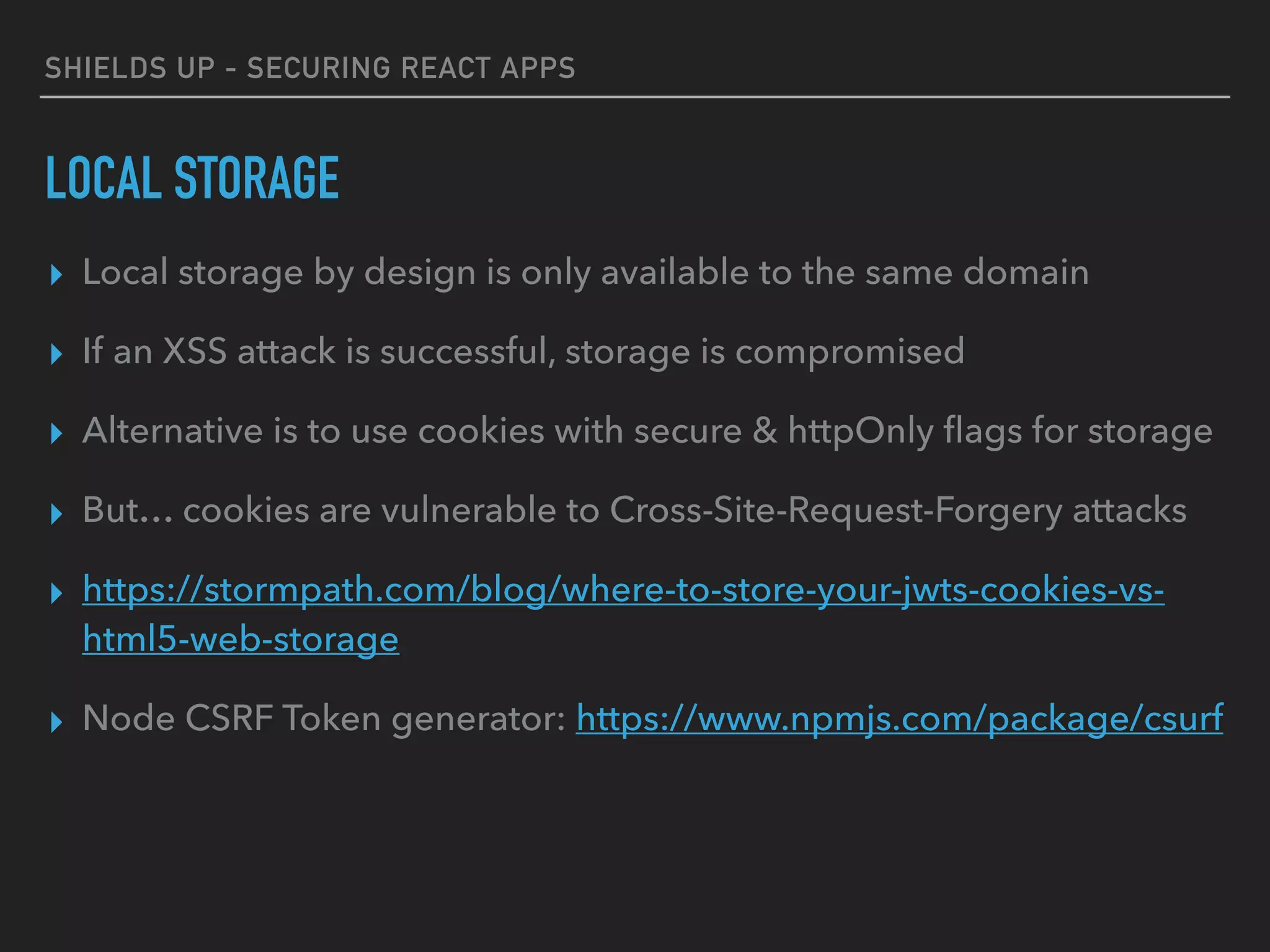
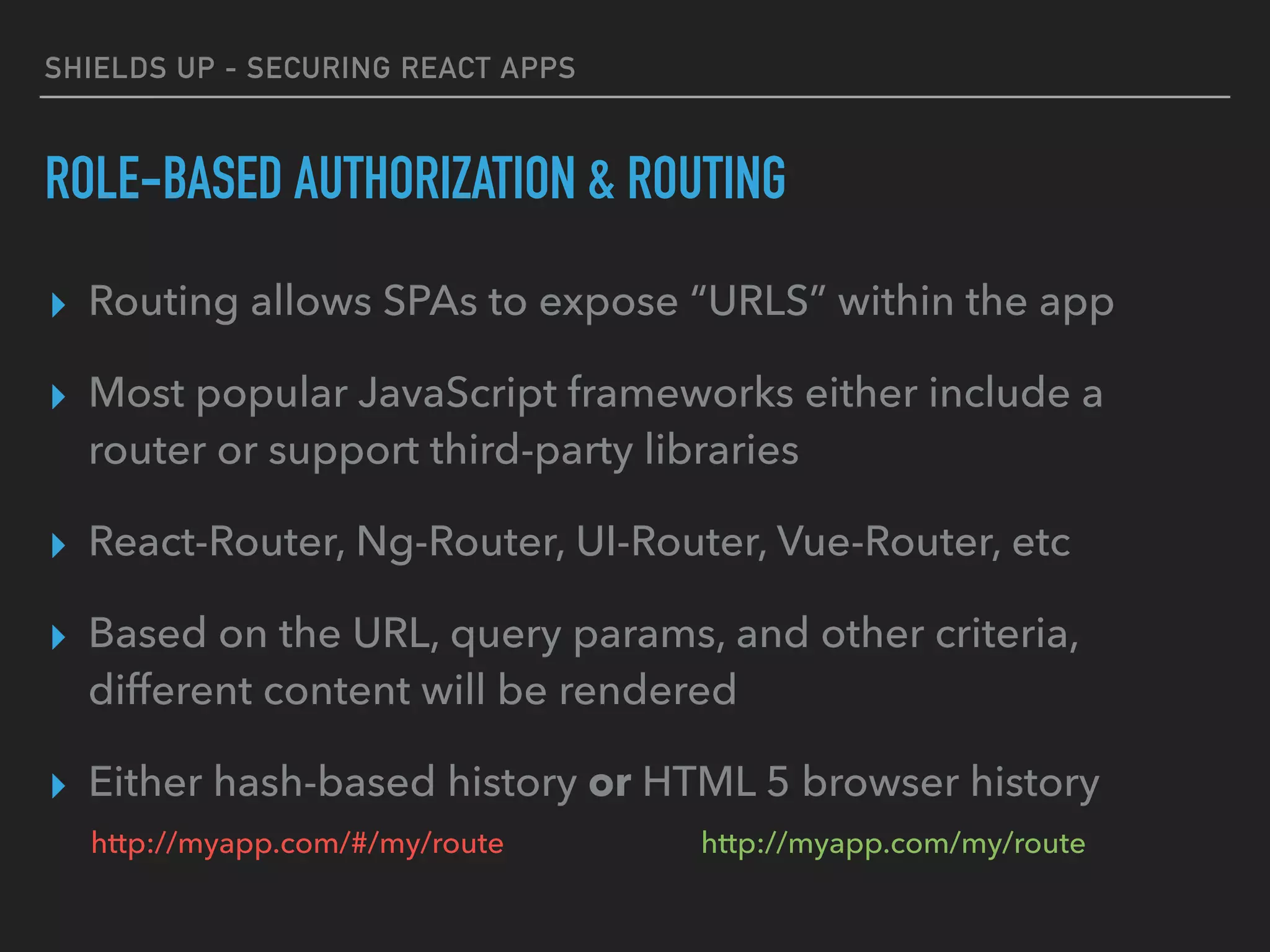
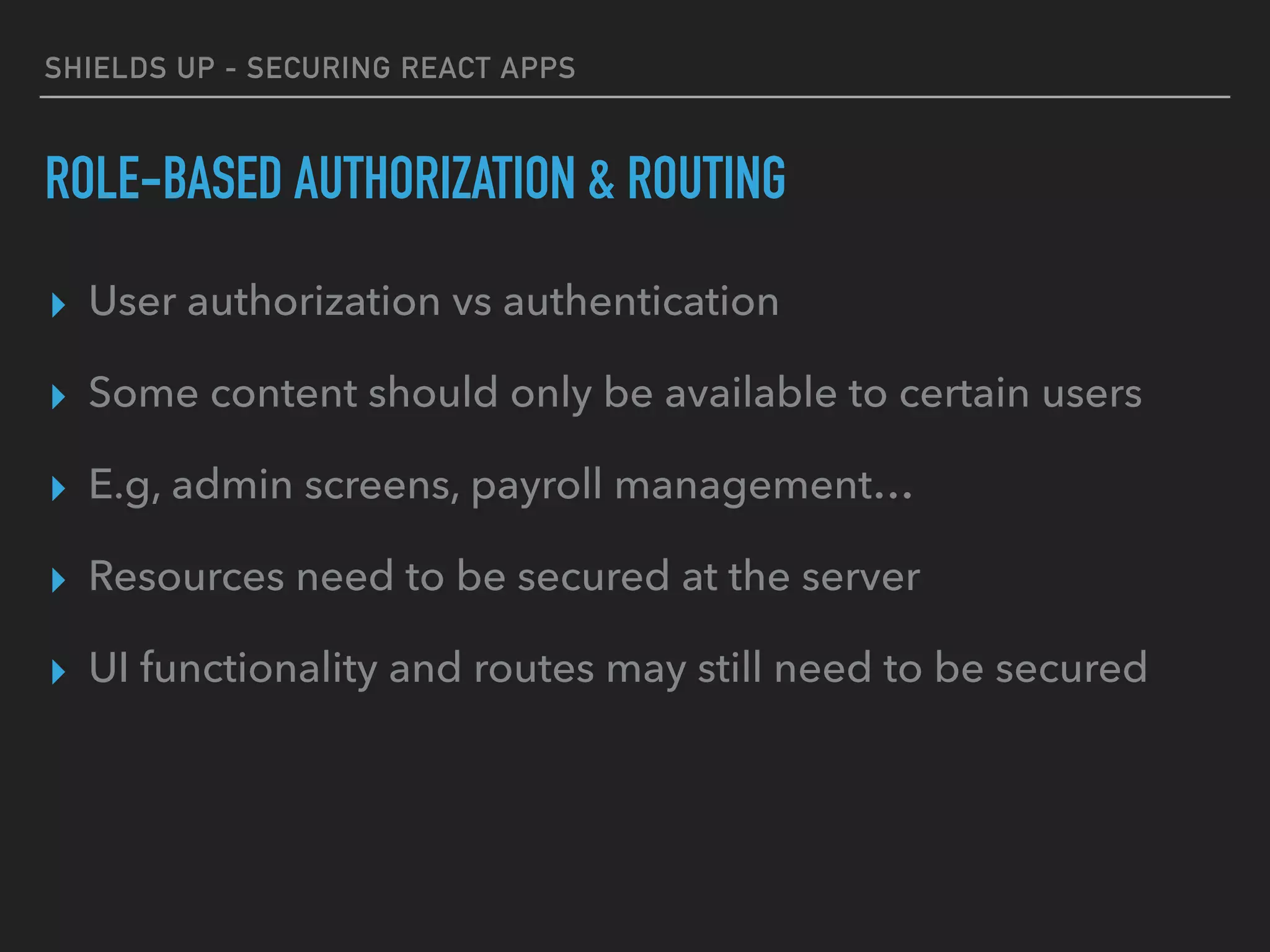
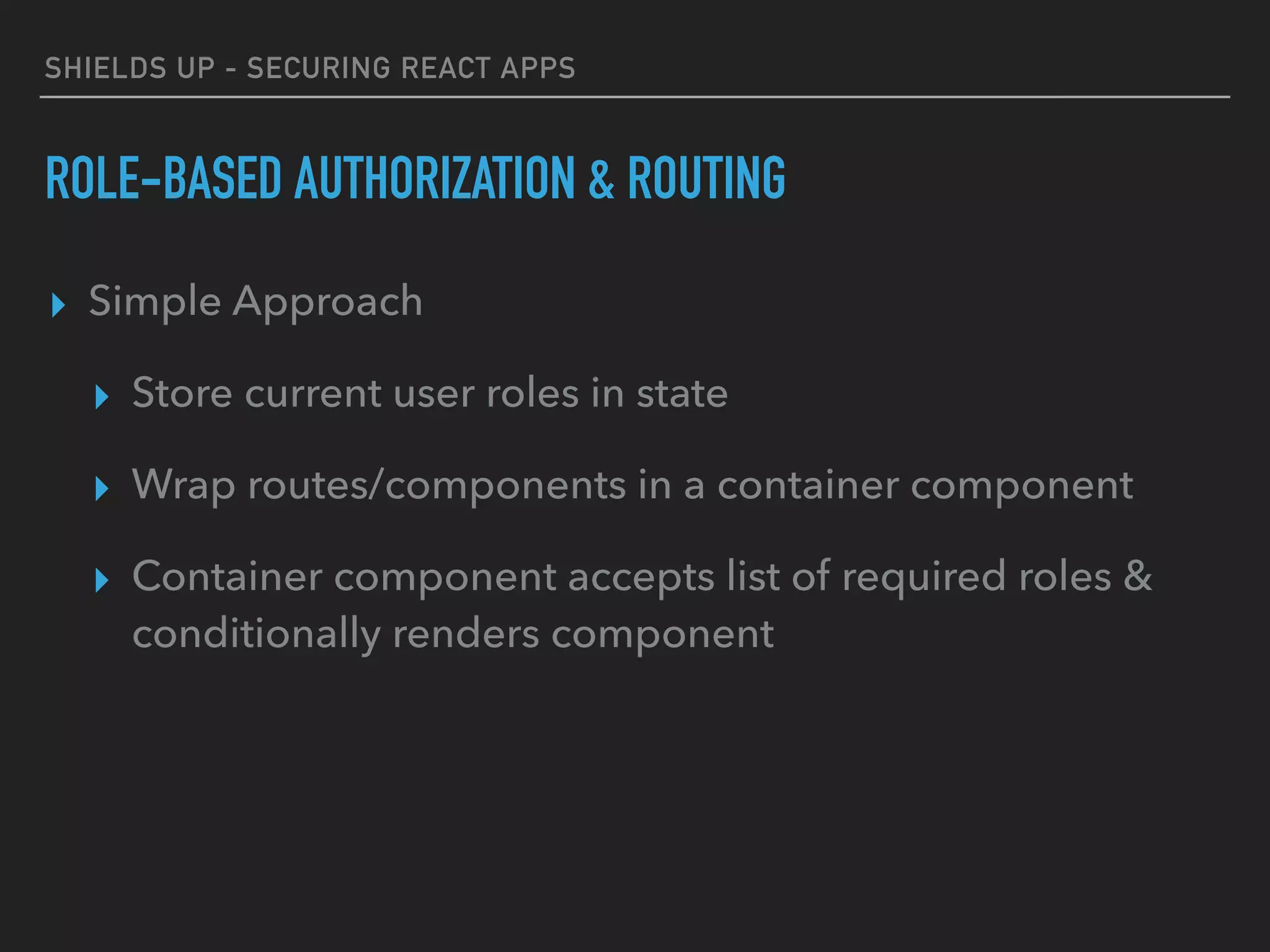
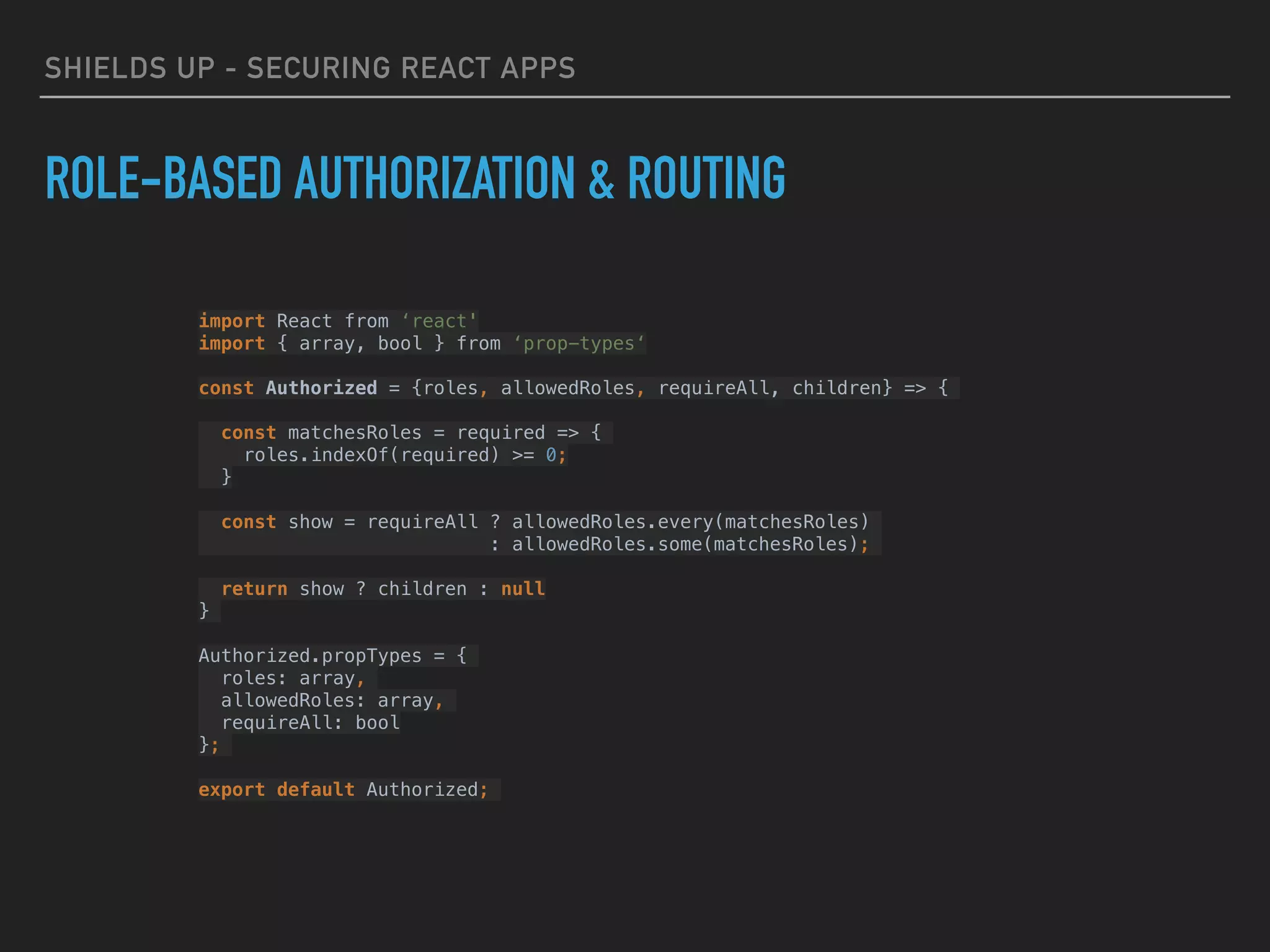
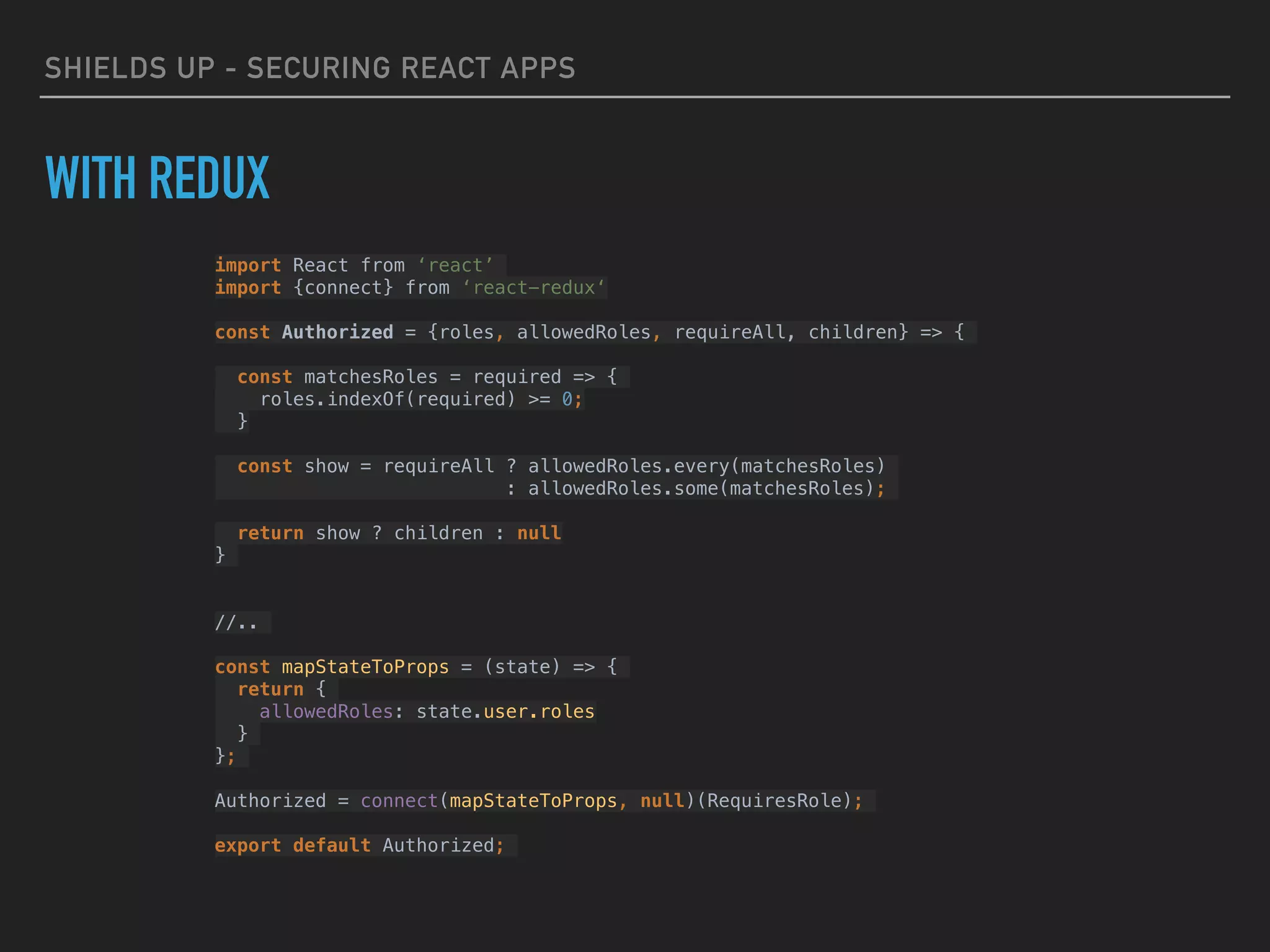
ROLE-BASED AUTHORIZATION & ROUTING
<Authorized allowedRoles={[‘ROLE_ADMIN', 'ROLE_ADMIN', 'ROLE_USER']}>
<Profile user={user} />
</Authorized>
<Authorized allowedRoles={['ROLE_ADMIN', 'ROLE_MANAGER']}>
<ManageEmployees />
</Authorized>
<Authorized allowedRoles={['ROLE_ADMIN', ‘ROLE_MANAGER']} requireAll={true}>
<ManageDatabase />
</Authorized>](https://image.slidesharecdn.com/shieldsupsecuringreactapps-171210035049/75/Shields-Up-Securing-React-Apps-26-2048.jpg)

![SHIELDS UP - SECURING REACT APPS
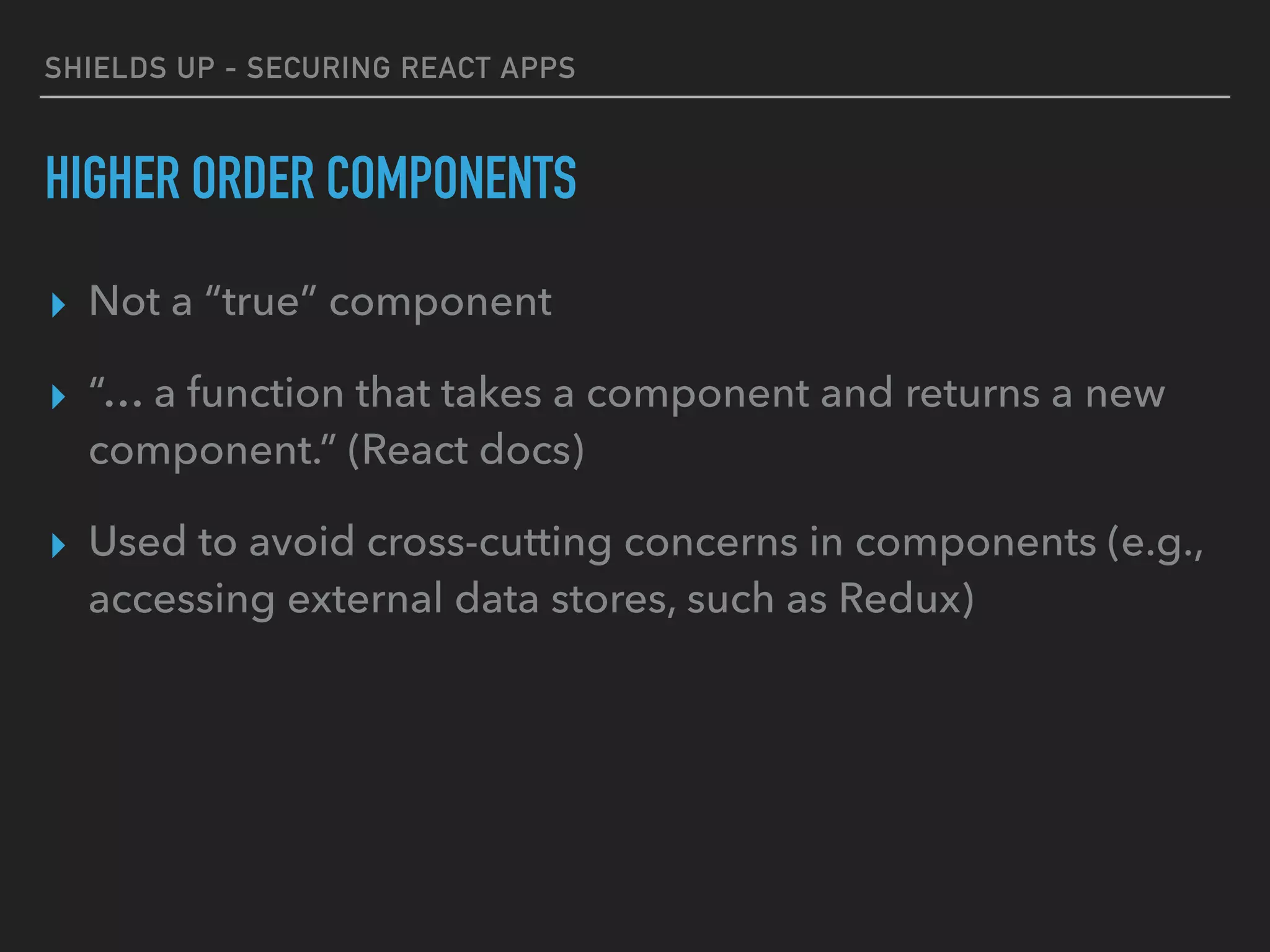
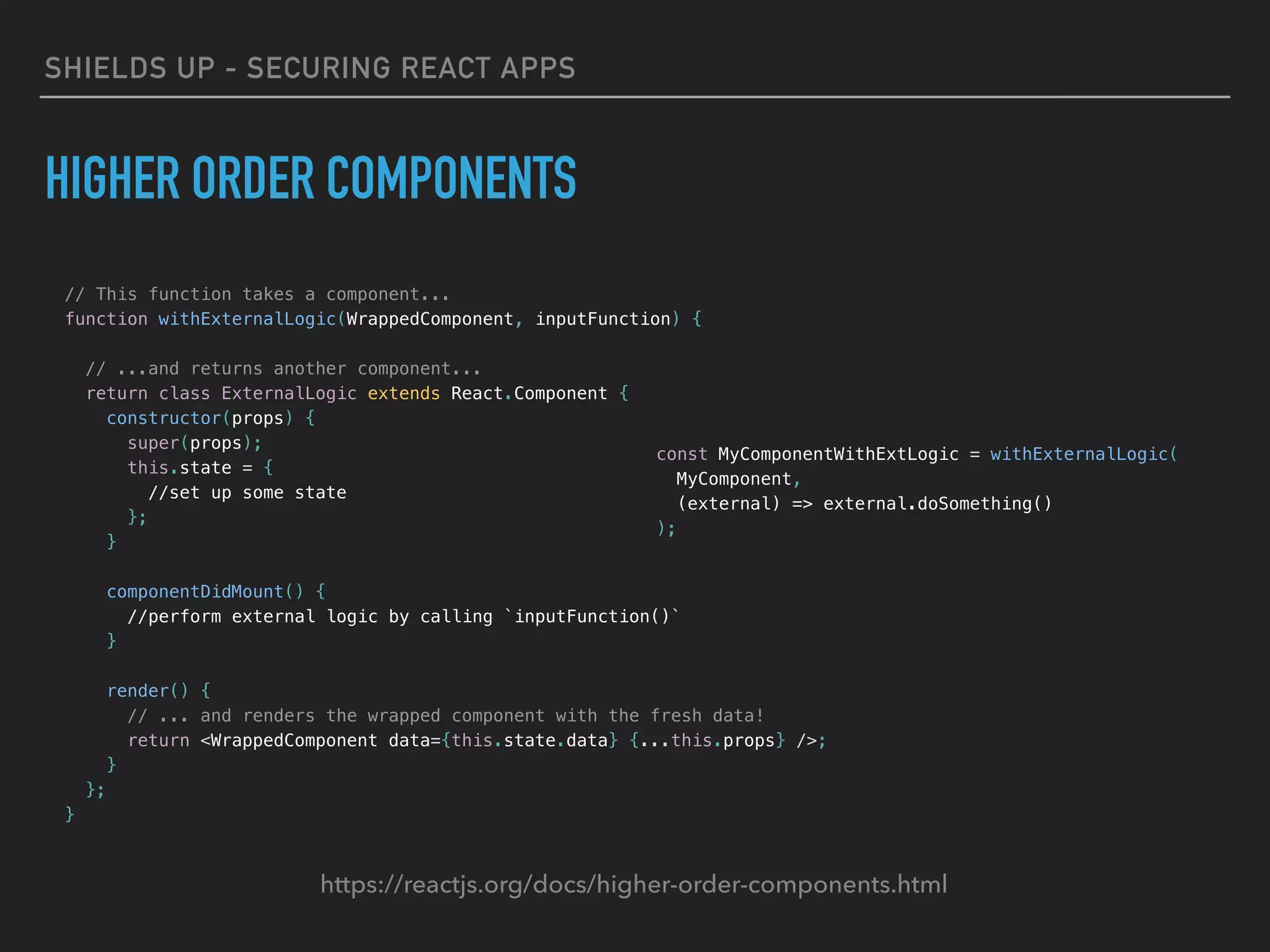
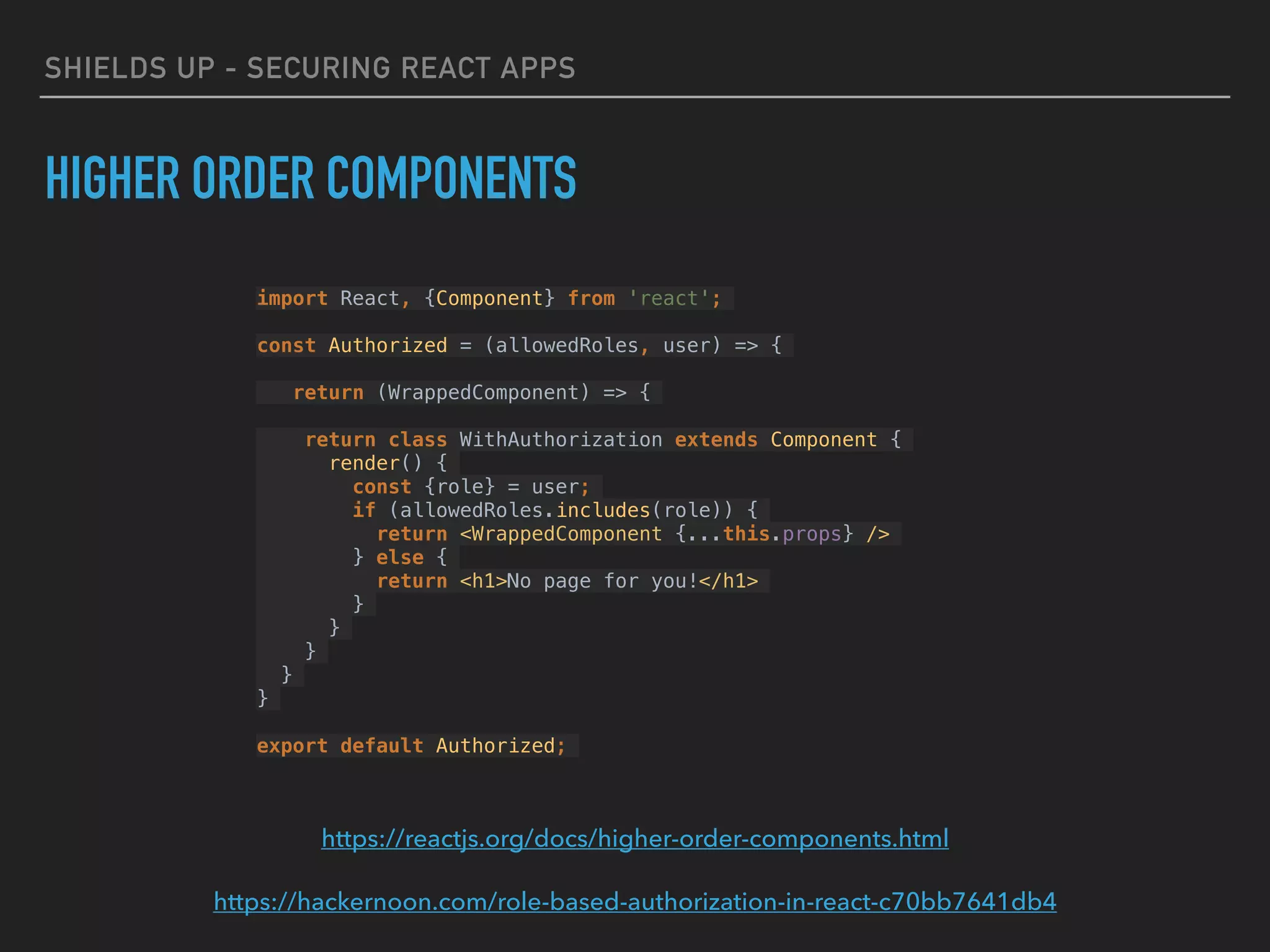
HIGHER ORDER COMPONENTS
https://reactjs.org/docs/higher-order-components.html
import Authorized from "./Authorized";
render() {
const {user, loggedIn} = this.state;
const withAdminRole = Authorized(['admin'], user);
const withUserRole = Authorized(['user', 'admin'], user);
return (
<Router>
<Route path="/restricted" component={withUserRole(Restricted)}/>
<Route path="/admin" component={withAdminRole(Admin)}/>
</Router>
);](https://image.slidesharecdn.com/shieldsupsecuringreactapps-171210035049/75/Shields-Up-Securing-React-Apps-31-2048.jpg)