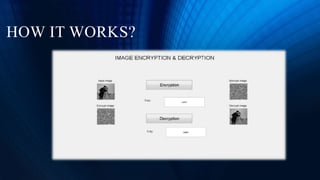
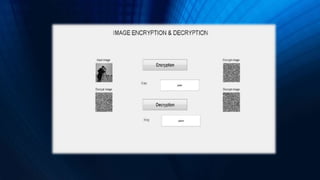
This document discusses a project to implement encryption and decryption of images using OpenGL. The objectives are to study JPEG image file architecture, develop an application using OpenGL for image encryption, and ensure secure password handling. The application aims to protect sensitive images from unauthorized access during transfer or at destination. It allows encrypted images to only be decrypted by the application itself using a password. The project provides easy-to-use and fast encryption/decryption capabilities along with more secure data transmission.