Secret Data Hiding Projects
•
0 likes•14 views
Takeoff Projects helps students complete their academic projects.You can enrol with friends and receive Stegnography Projects kits at your doorstep. You can learn from experts, build latest projects, showcase your project to the world and grab the best jobs. Get started today!
Report
Share
Report
Share
Download to read offline
Recommended
More Related Content
What's hot
What's hot (18)
ATIPS - Advanced Technology Information Processing Systems

ATIPS - Advanced Technology Information Processing Systems
Secure Data Transfer Over Internet Using Image Crypto-Steganography

Secure Data Transfer Over Internet Using Image Crypto-Steganography
Steganography Tutorial | How To Hide Text Inside The Image | Cybersecurity Tr...

Steganography Tutorial | How To Hide Text Inside The Image | Cybersecurity Tr...
APPLICATION OF DATA HIDING IN AUDIO-VIDEO USING ANTIN FORENSICS TECHNIQUE FOR...

APPLICATION OF DATA HIDING IN AUDIO-VIDEO USING ANTIN FORENSICS TECHNIQUE FOR...
Similar to Secret Data Hiding Projects
Similar to Secret Data Hiding Projects (20)
Video Steganography using Discrete Wavelet Transform and Artificial Intelligence

Video Steganography using Discrete Wavelet Transform and Artificial Intelligence
STEGANALYSIS ALGORITHM FOR PNG IMAGES BASED ON FUZZY LOGIC TECHNIQUE

STEGANALYSIS ALGORITHM FOR PNG IMAGES BASED ON FUZZY LOGIC TECHNIQUE
A Comparative Study And Literature Review Of Image Steganography Techniques

A Comparative Study And Literature Review Of Image Steganography Techniques
STEGANALYSIS ALGORITHM FOR PNG IMAGES BASED ON FUZZY LOGIC TECHNIQUE

STEGANALYSIS ALGORITHM FOR PNG IMAGES BASED ON FUZZY LOGIC TECHNIQUE
Optimized WES-System with Image Bit Embedding for Enhancing the Security of H...

Optimized WES-System with Image Bit Embedding for Enhancing the Security of H...
A Survey Paper On Different Steganography Technique

A Survey Paper On Different Steganography Technique
More from keerthanapothula
More from keerthanapothula (11)
Recently uploaded
Model Call Girl in Bikash Puri Delhi reach out to us at 🔝9953056974🔝

Model Call Girl in Bikash Puri Delhi reach out to us at 🔝9953056974🔝9953056974 Low Rate Call Girls In Saket, Delhi NCR
call girls in Kamla Market (DELHI) 🔝 >༒9953330565🔝 genuine Escort Service 🔝✔️✔️

call girls in Kamla Market (DELHI) 🔝 >༒9953330565🔝 genuine Escort Service 🔝✔️✔️9953056974 Low Rate Call Girls In Saket, Delhi NCR
Recently uploaded (20)
MARGINALIZATION (Different learners in Marginalized Group

MARGINALIZATION (Different learners in Marginalized Group
internship ppt on smartinternz platform as salesforce developer

internship ppt on smartinternz platform as salesforce developer
TataKelola dan KamSiber Kecerdasan Buatan v022.pdf

TataKelola dan KamSiber Kecerdasan Buatan v022.pdf
Historical philosophical, theoretical, and legal foundations of special and i...

Historical philosophical, theoretical, and legal foundations of special and i...
Model Call Girl in Bikash Puri Delhi reach out to us at 🔝9953056974🔝

Model Call Girl in Bikash Puri Delhi reach out to us at 🔝9953056974🔝
Interactive Powerpoint_How to Master effective communication

Interactive Powerpoint_How to Master effective communication
Hierarchy of management that covers different levels of management

Hierarchy of management that covers different levels of management
Capitol Tech U Doctoral Presentation - April 2024.pptx

Capitol Tech U Doctoral Presentation - April 2024.pptx
18-04-UA_REPORT_MEDIALITERAСY_INDEX-DM_23-1-final-eng.pdf

18-04-UA_REPORT_MEDIALITERAСY_INDEX-DM_23-1-final-eng.pdf
call girls in Kamla Market (DELHI) 🔝 >༒9953330565🔝 genuine Escort Service 🔝✔️✔️

call girls in Kamla Market (DELHI) 🔝 >༒9953330565🔝 genuine Escort Service 🔝✔️✔️
Secret Data Hiding Projects
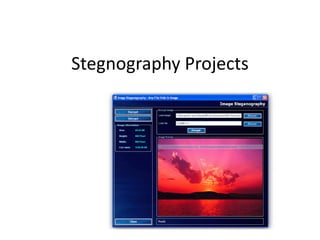
- 2. ARTICLE • Art of Keeping Information secret and to safeguard the embedded information is known as Steganography Projects.Goal of Steganography Projects is to hide and retrieve Secret Information in an Image,Audio,Video,Text files and to safeguard information from attackers.We provide Steganography projects for all academic students in which the paper title is being updated from ISI journal.Example of Steganography Projects is F5 which uses Steganography algorithm for hiding information in JPEG images.The way of adding some matter by all the methods using some carrier is called Steganography matlab. In computer, forensic field, Investigators should know about the Steganography that it can hide the data by using files without any harm.Steganography Projects is the most preferred method to hide data from the attackers.There are five different types in steganography Projects. 1.Design and implementation of hardware based watermarking solutions for CMOS image sensors. 2.Medical image watermarking with tamper detection and recovery using reversible watermarking with LSB modification and run length encoding (RLE) compression. 3.Attack Model of Text Watermarking Based on Communications. 4.Image Watermarking Based on Wavelet-Based Contourlet Packet Transform with Best Tree. 5.Digital Image Watermarking Algorithm with Double Encryption by Arnold Transform and Logistic.