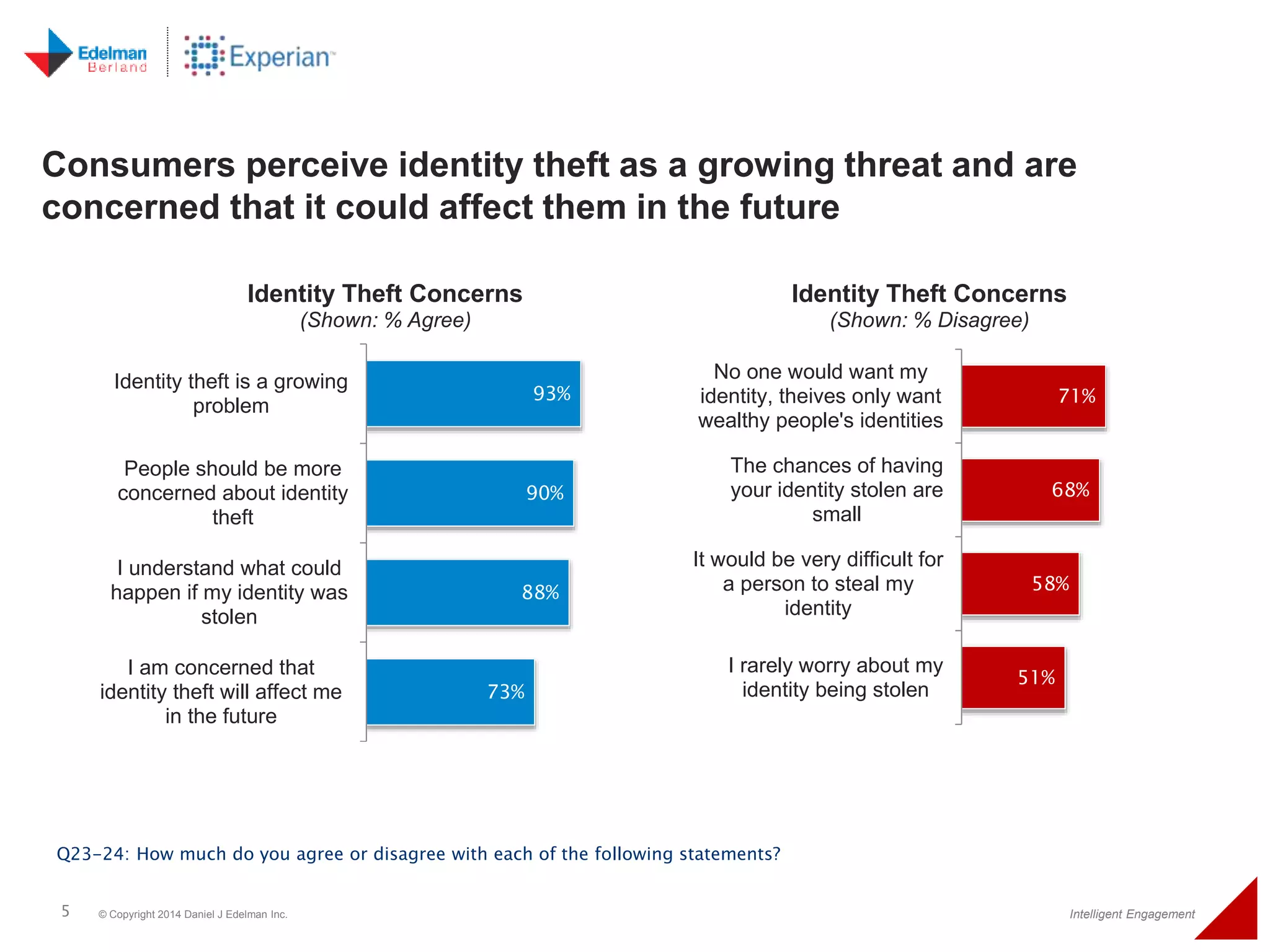
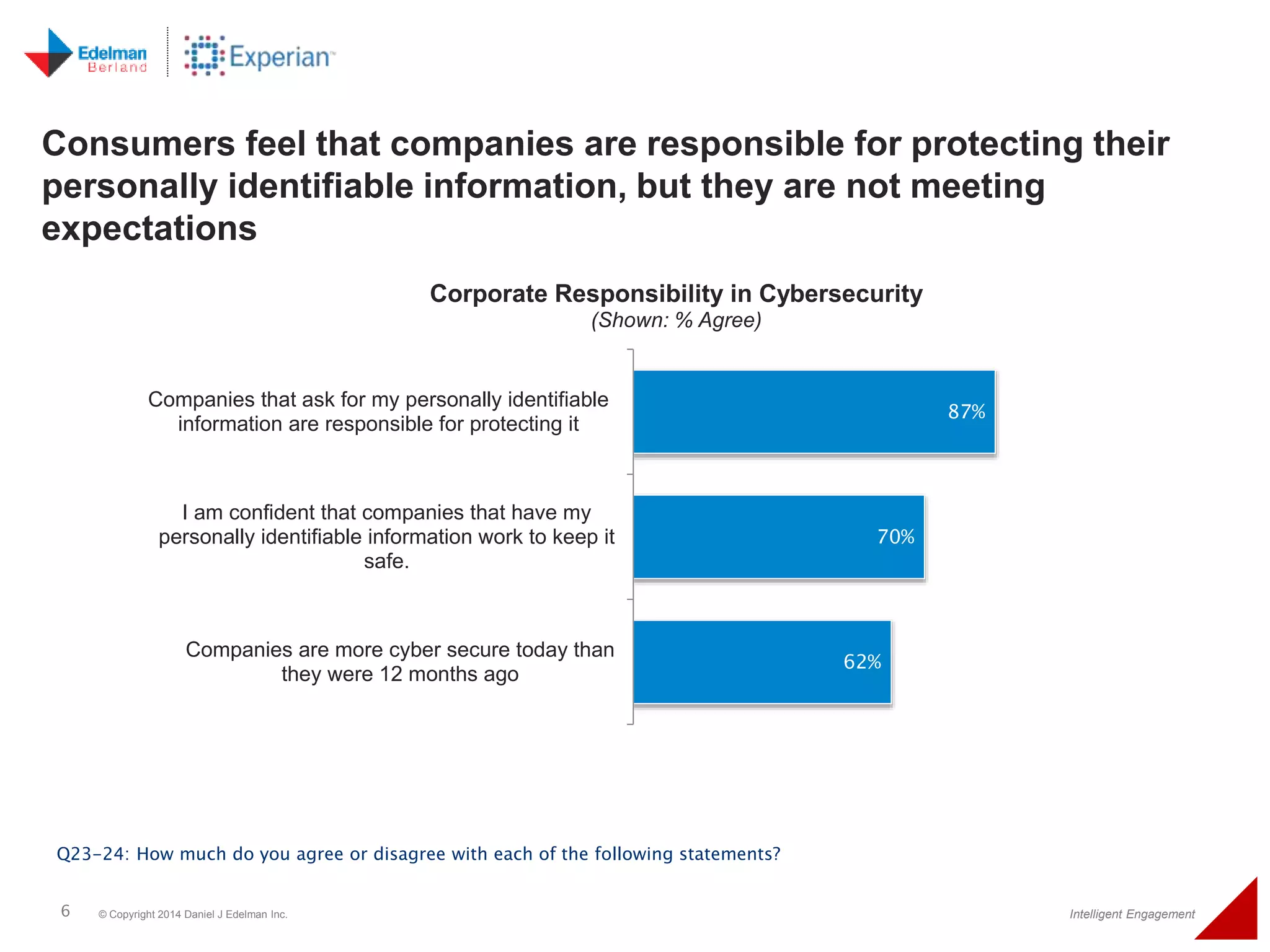
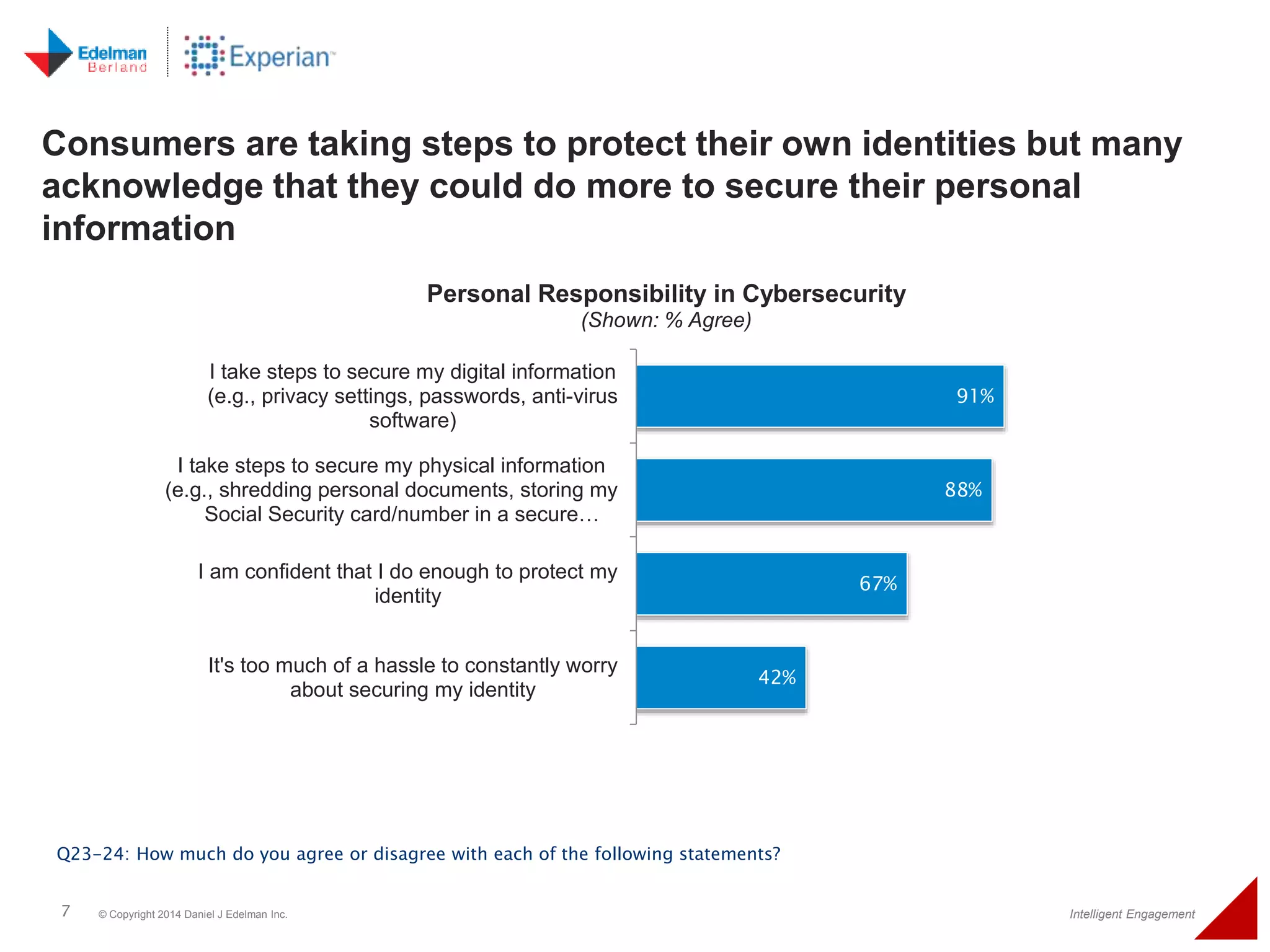
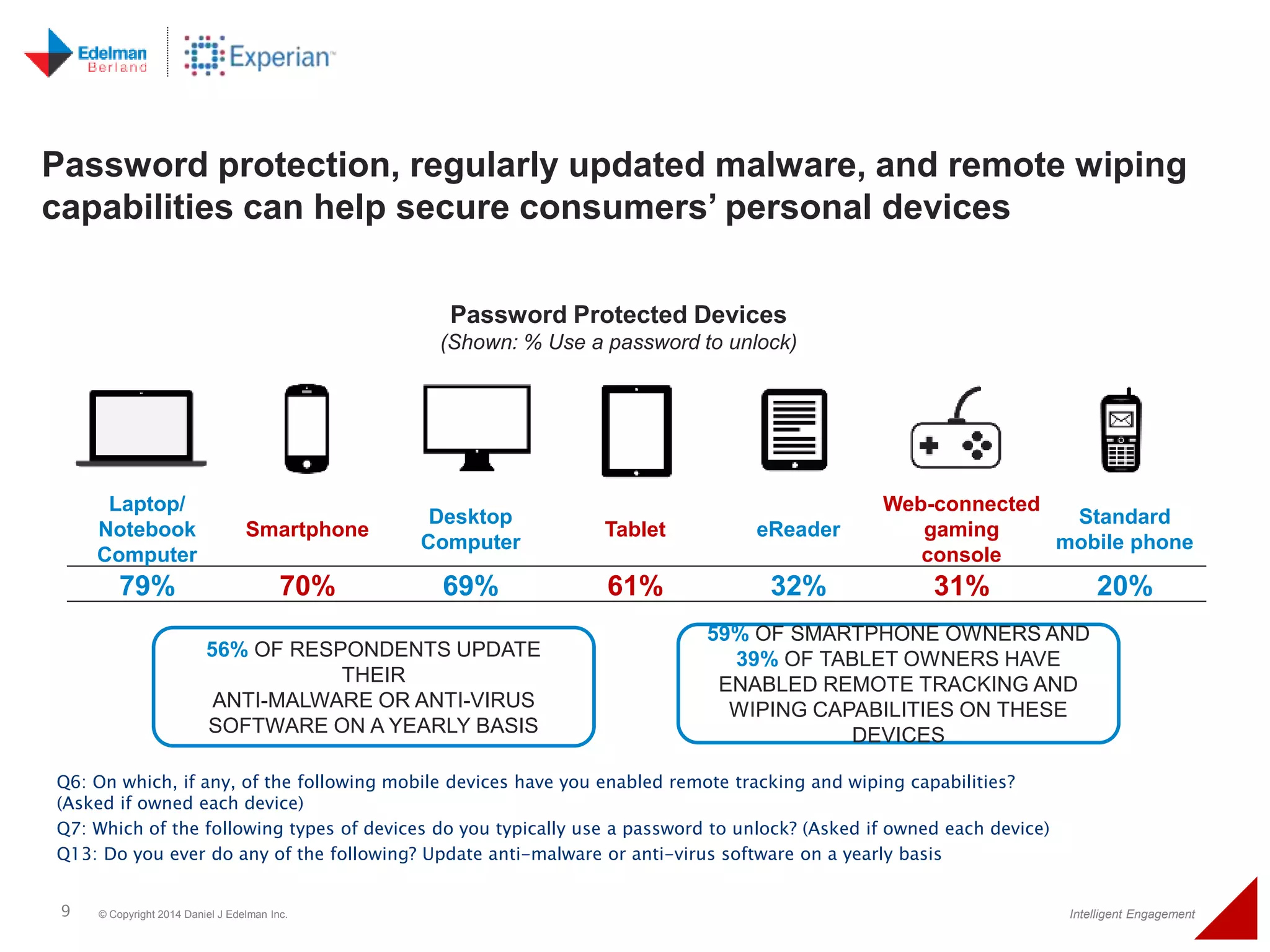
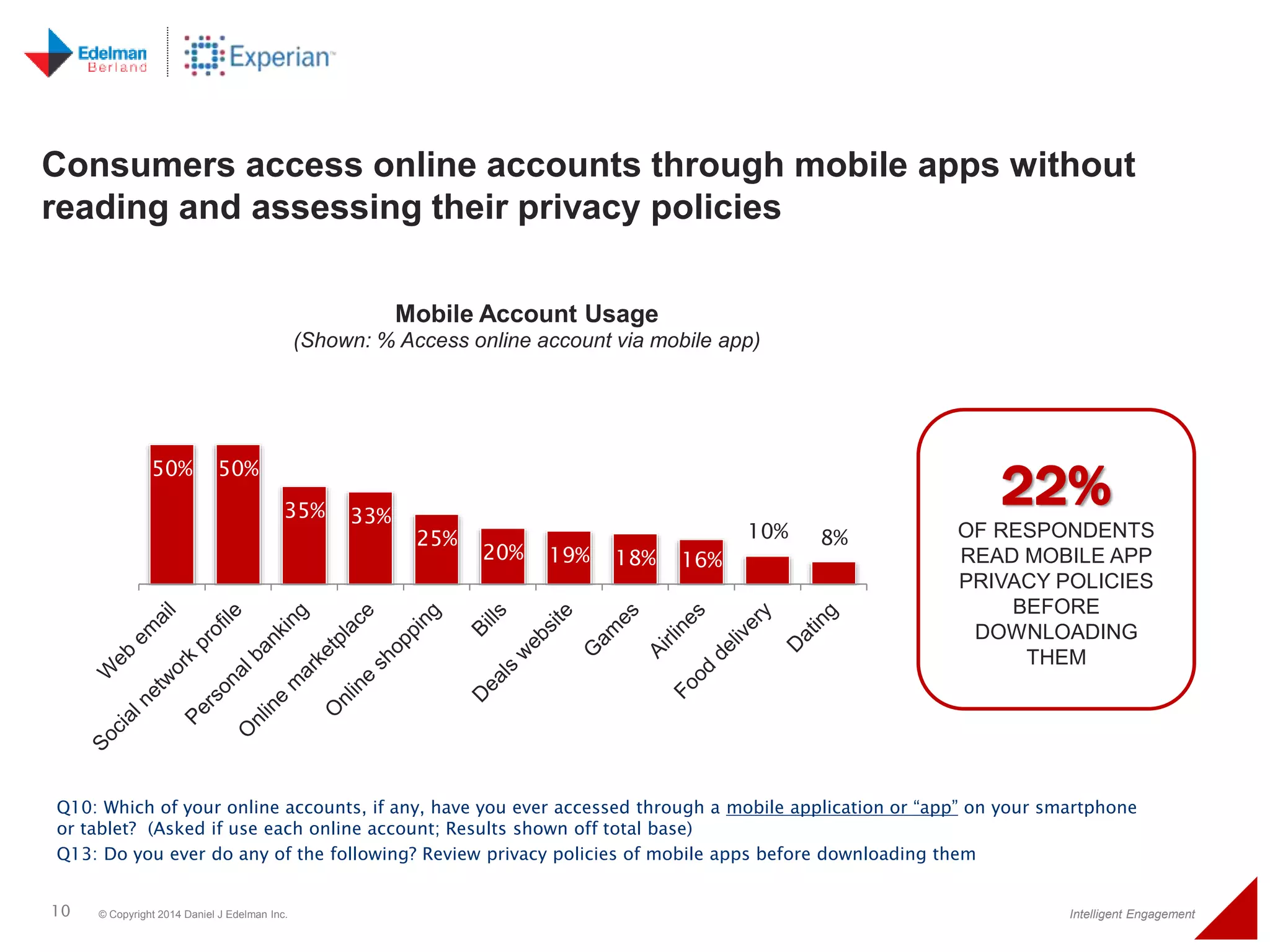
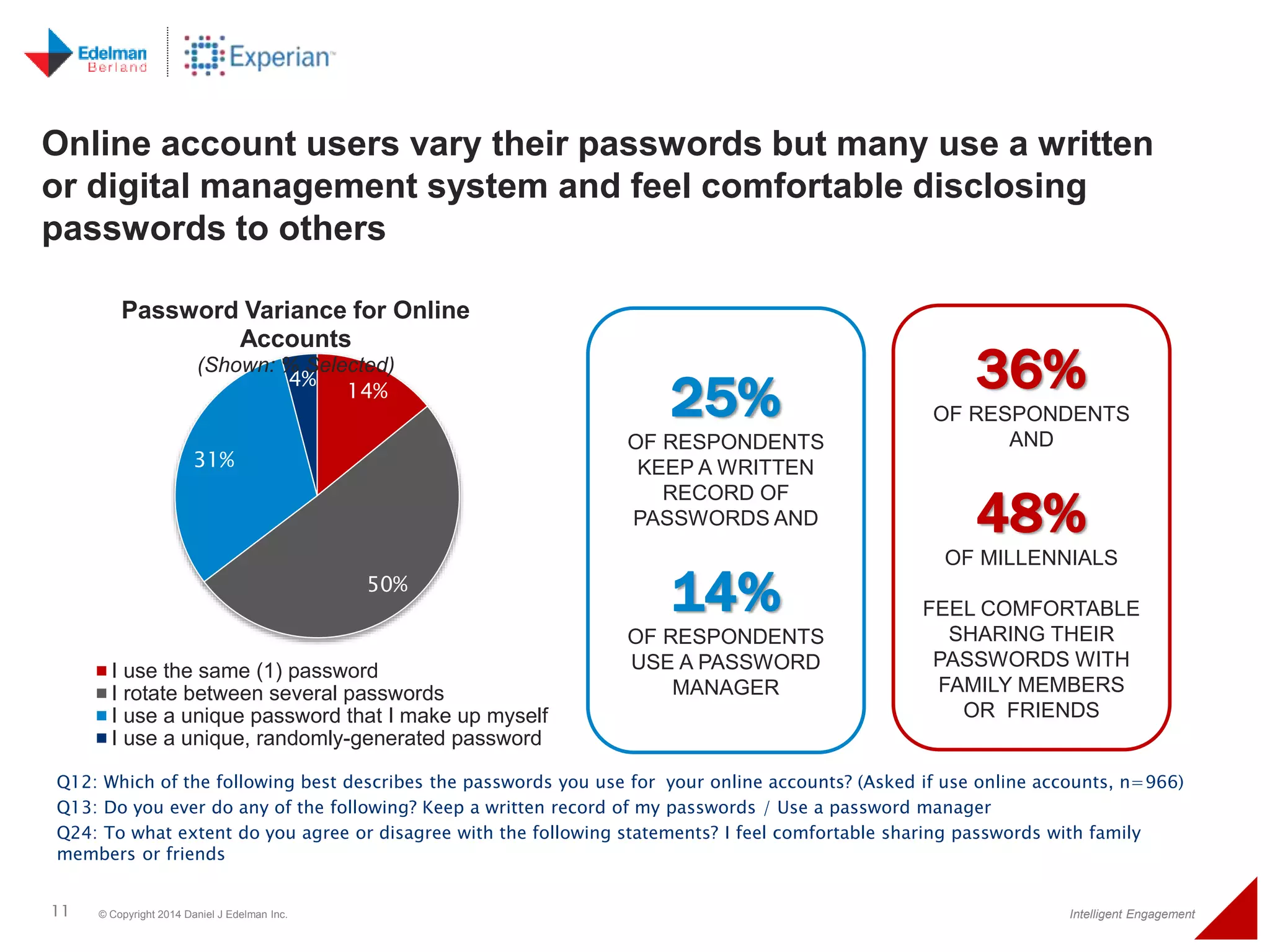
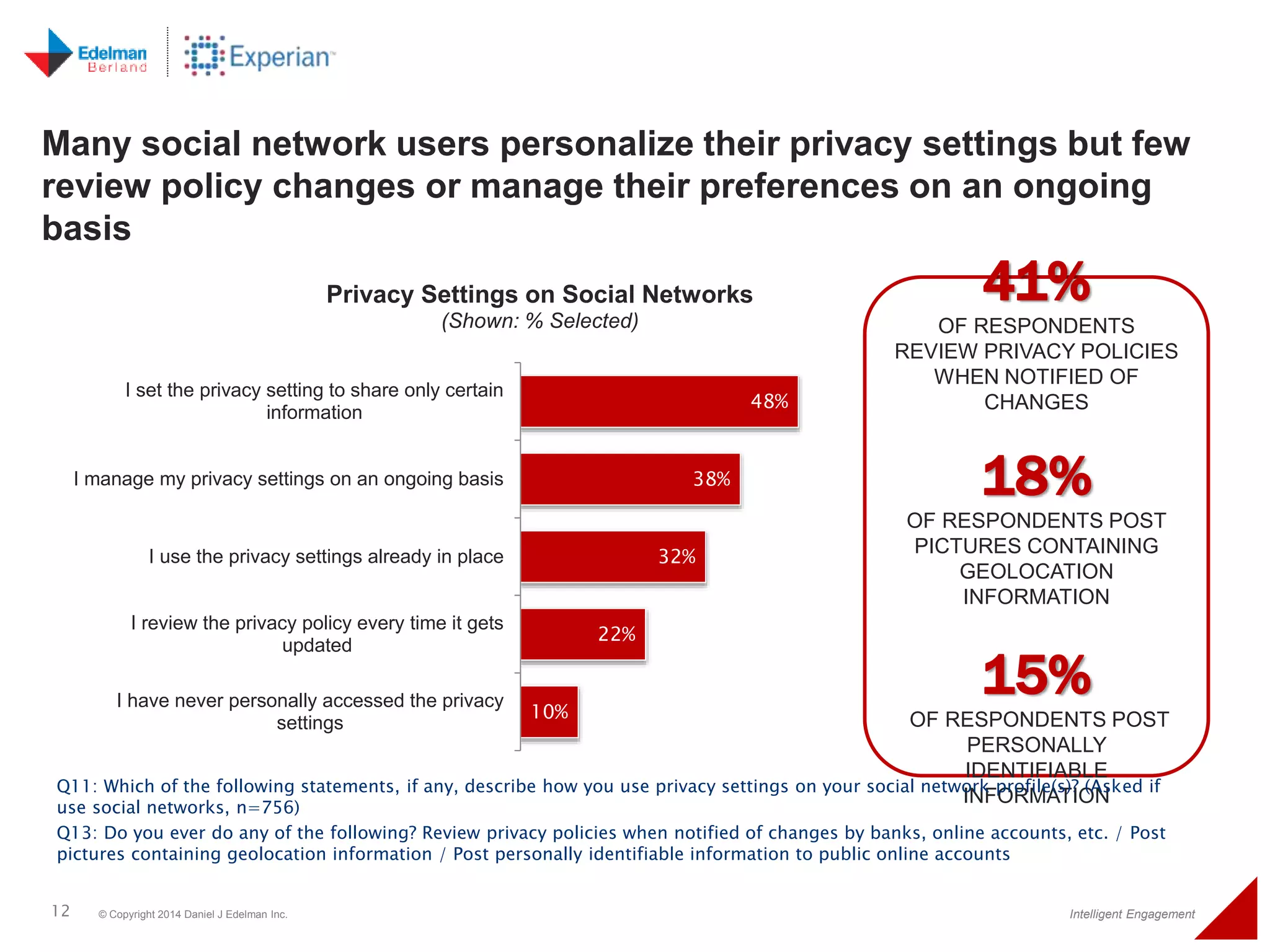
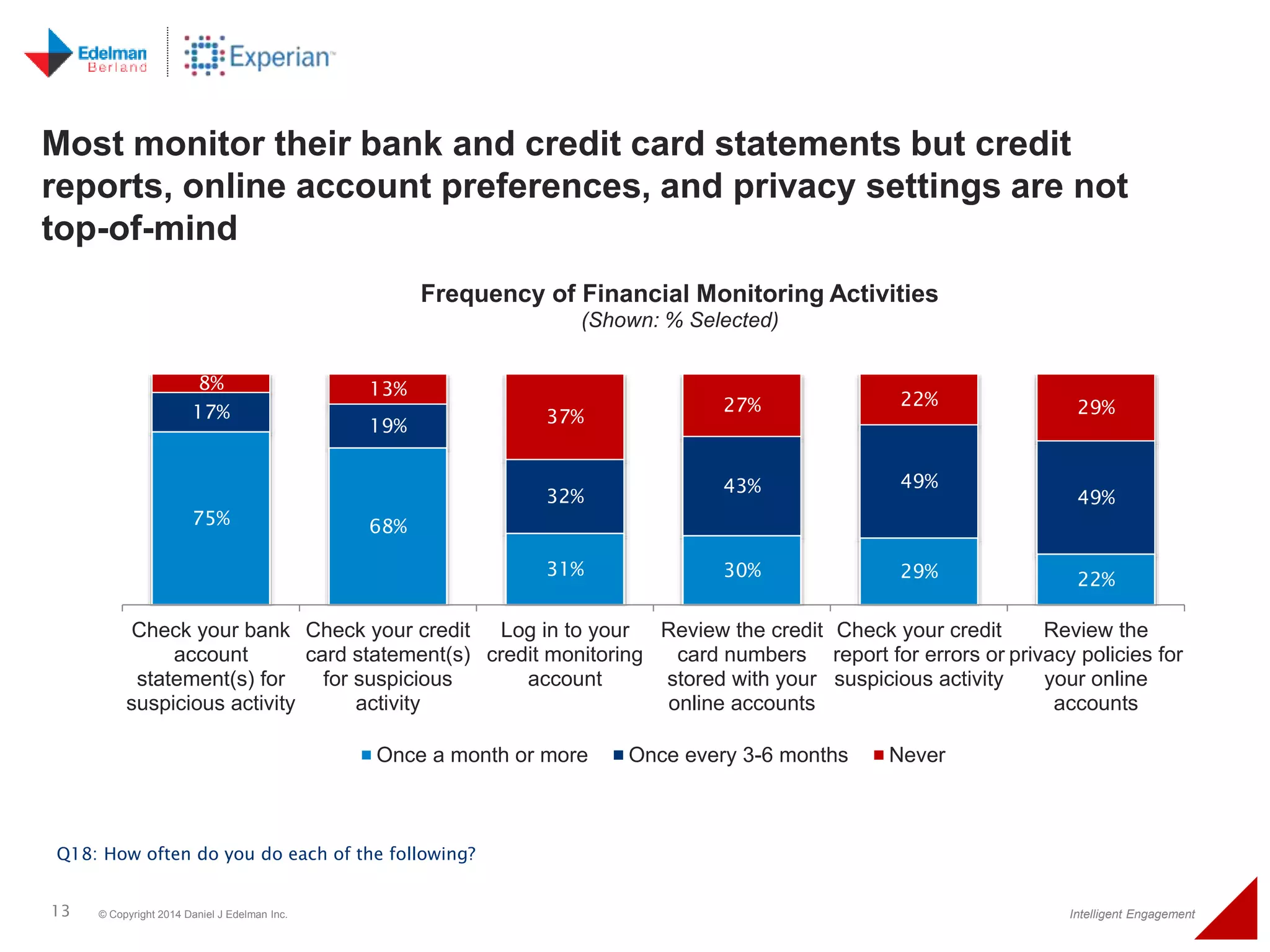
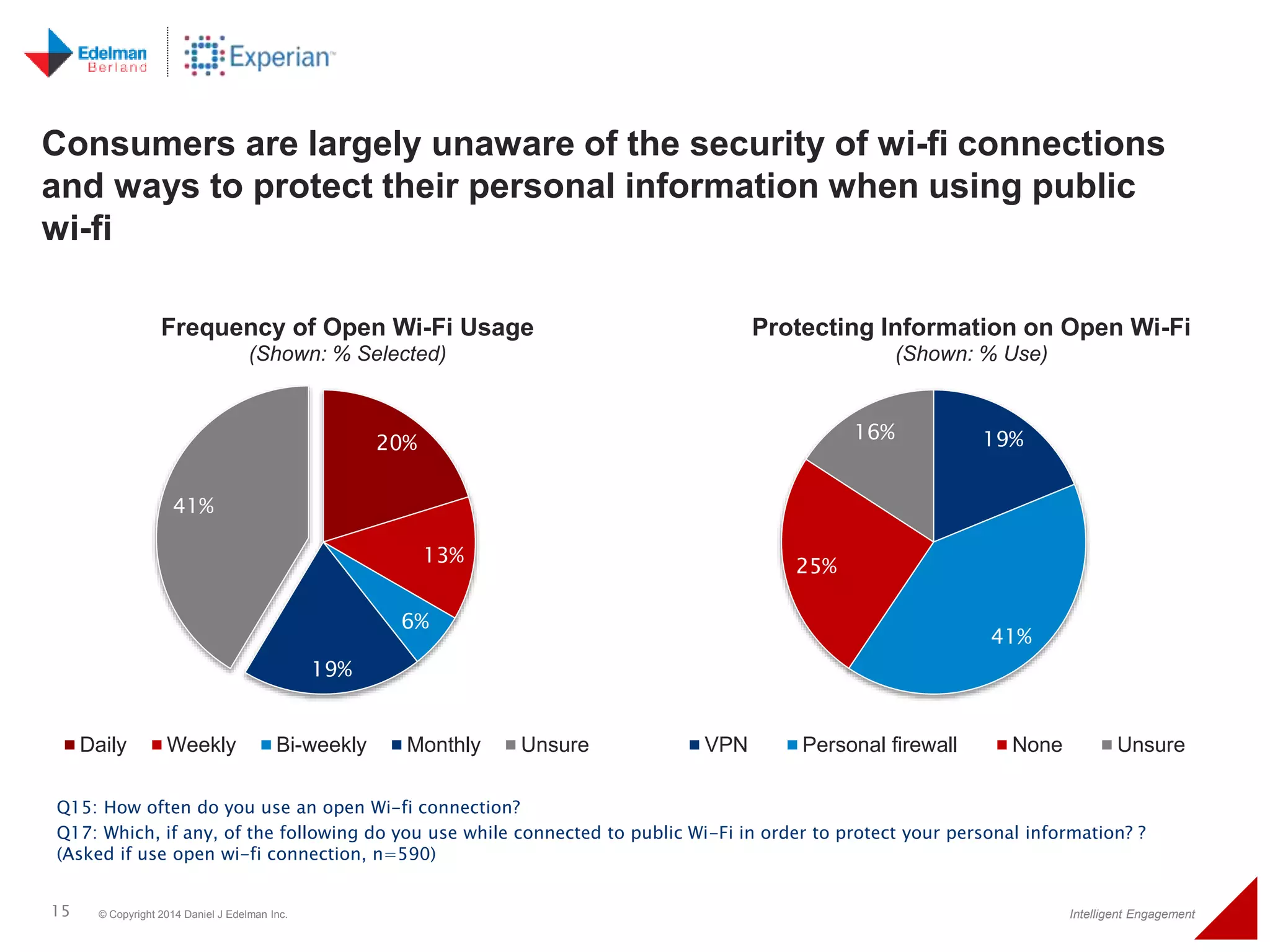
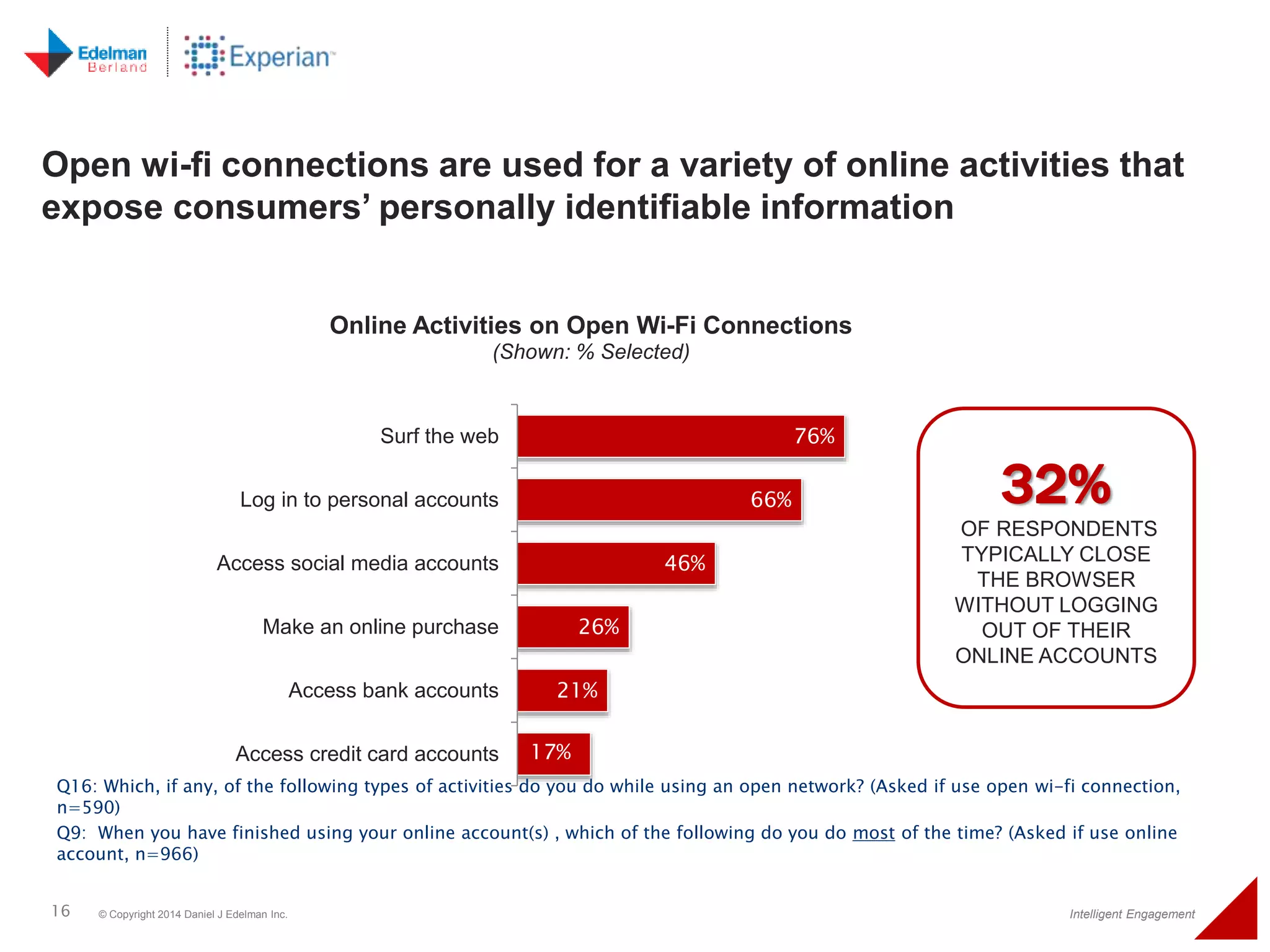
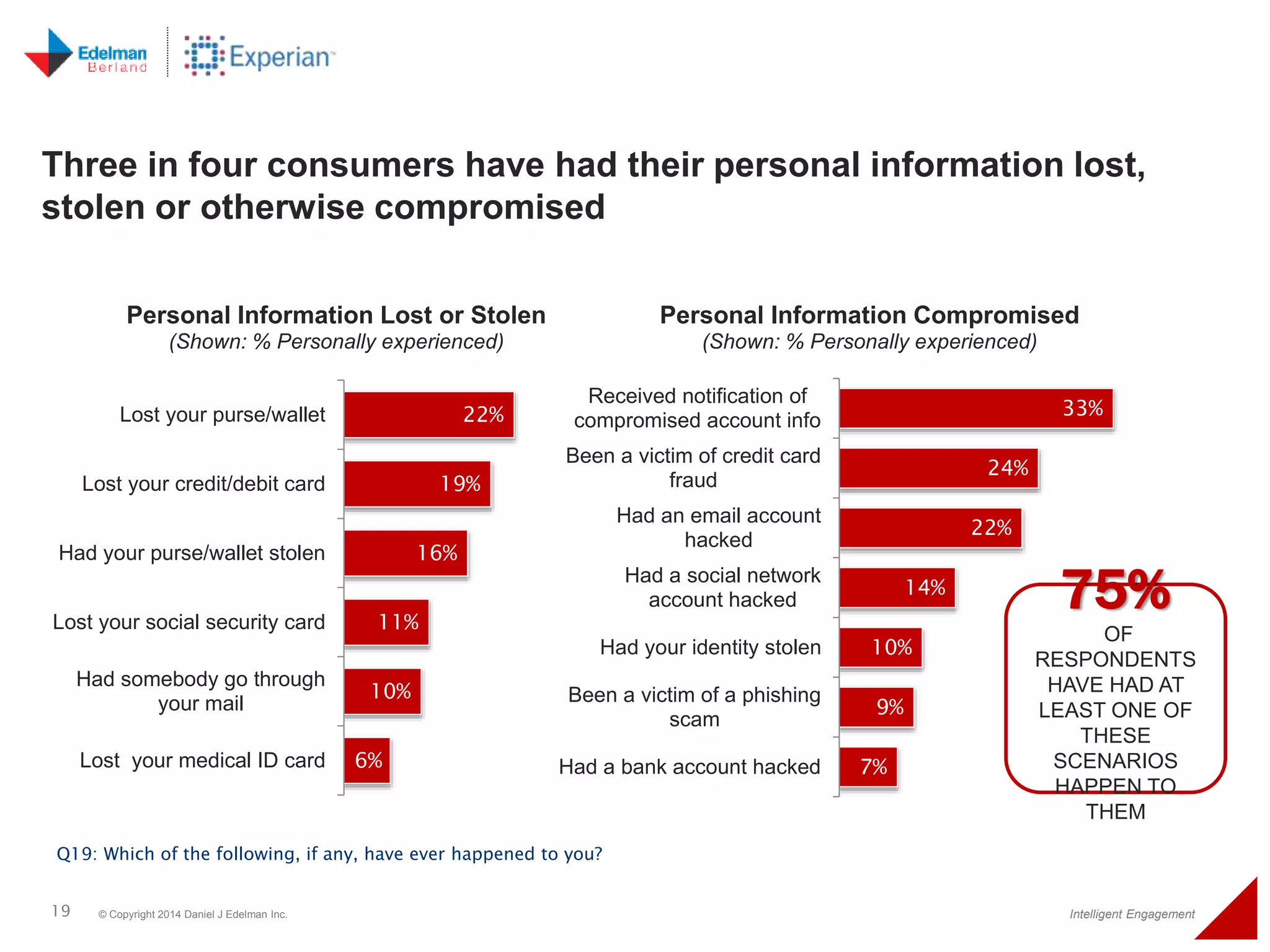
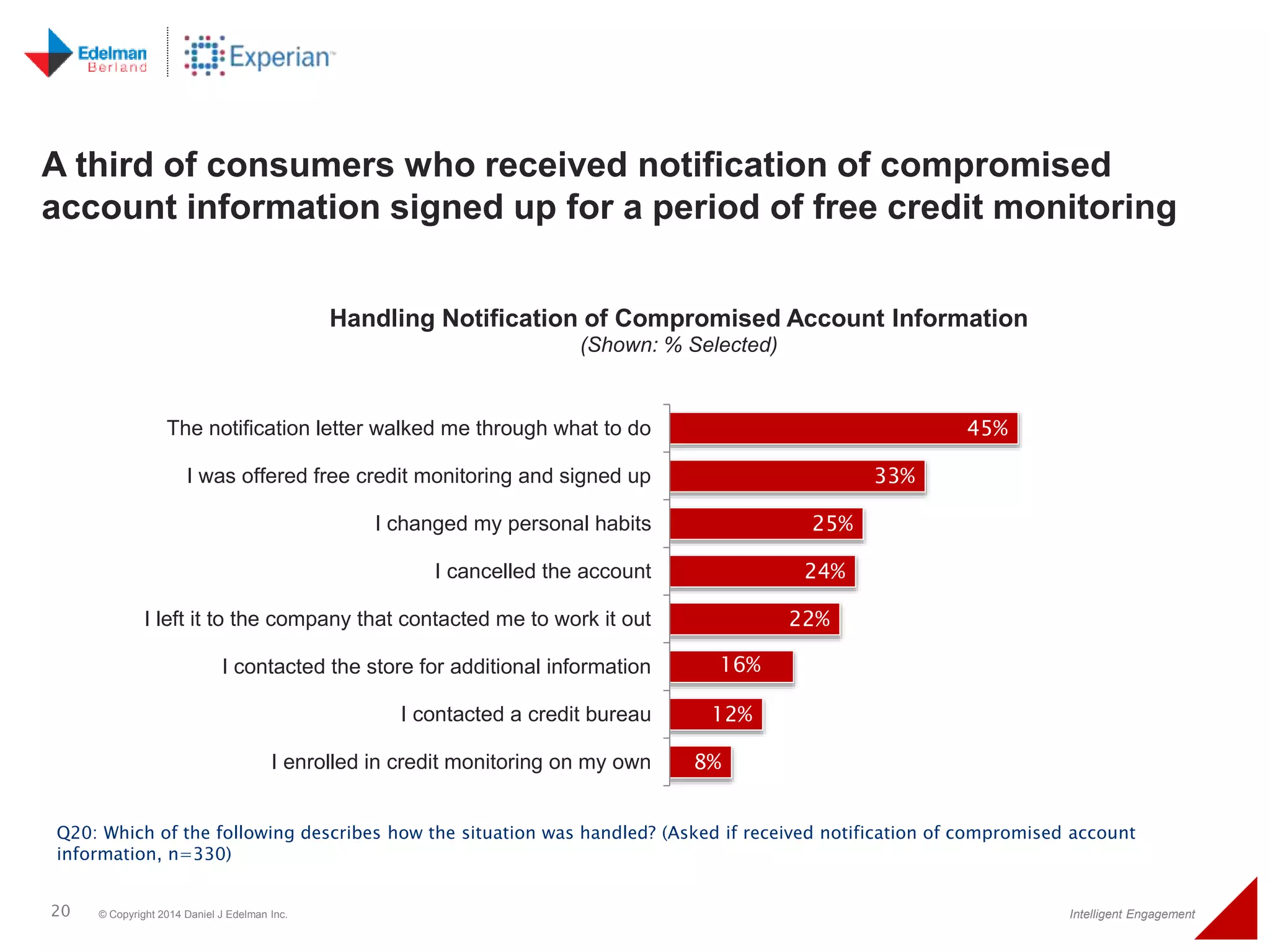
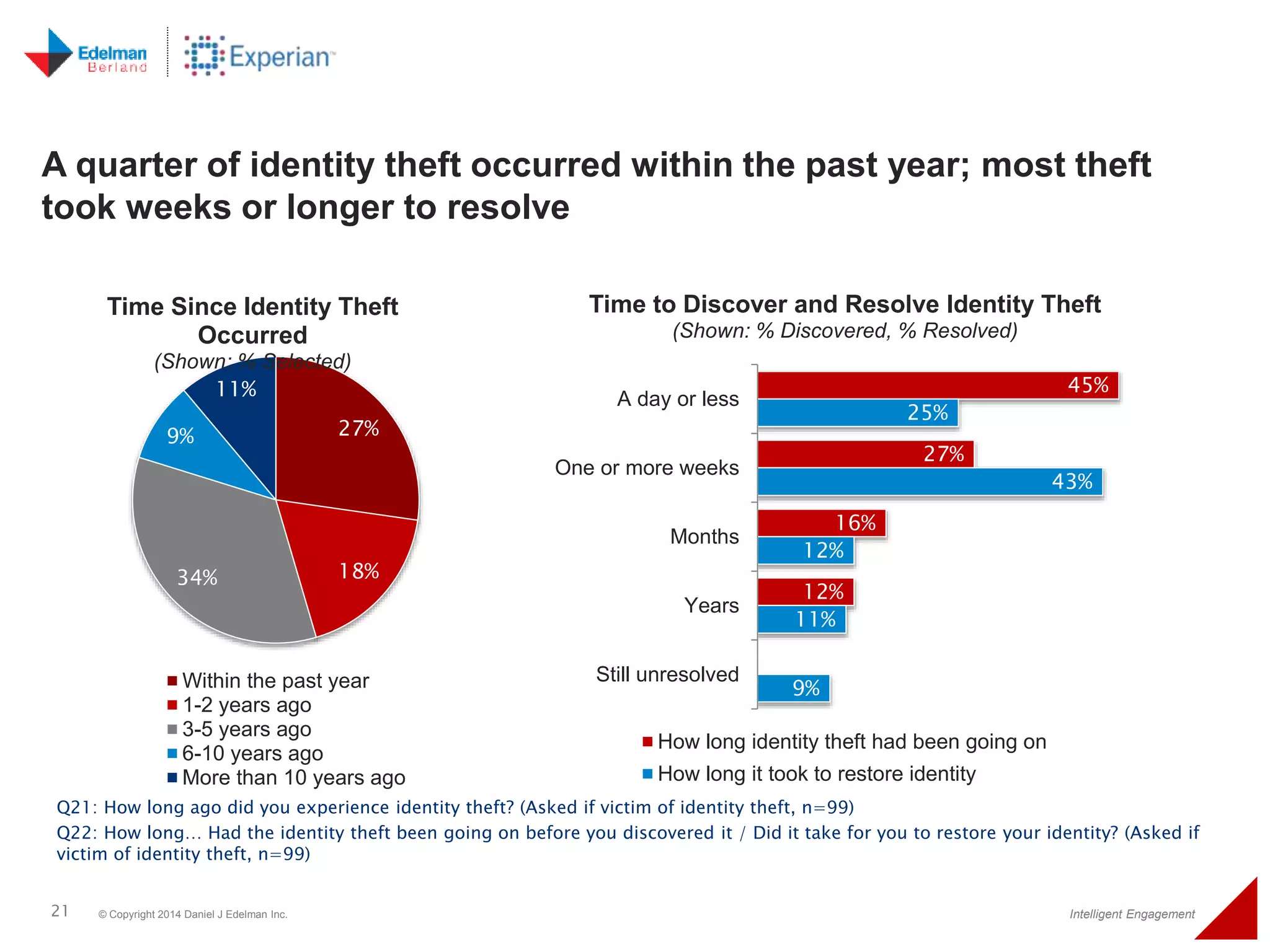
The 2014 Experian cybersecurity survey reveals significant consumer concern about identity theft, with 93% agreeing it is a growing problem. While many individuals take steps to protect their personal information, a lack of confidence remains, with 33% feeling they are not doing enough. The survey highlights disparities in consumer behavior regarding cybersecurity practices, including inadequate password protections and often ignoring privacy policies.