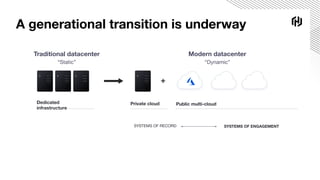
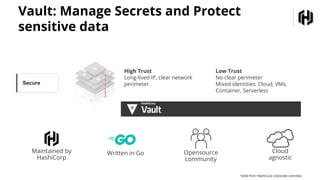
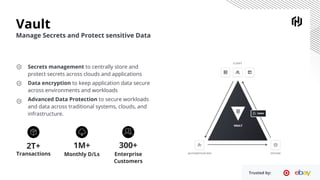
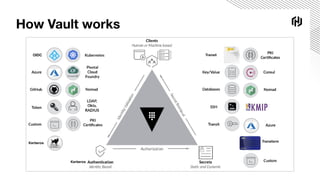
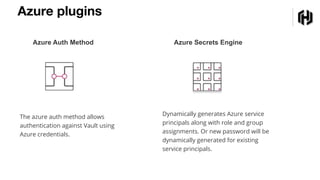
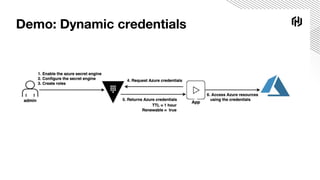
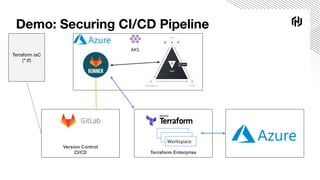
The document details a webinar on dynamic Azure credentials for applications and CI/CD pipelines presented by HashiCorp, highlighting its importance in maintaining security while transitioning to cloud infrastructure. Key topics include Vault's capabilities for managing secrets, the advantages of dynamic credentials, and a demonstration of how to secure CI/CD processes using Terraform. The session also covers benefits like unique application instance credentials, least privilege roles, and the ability to audit and revoke access easily.