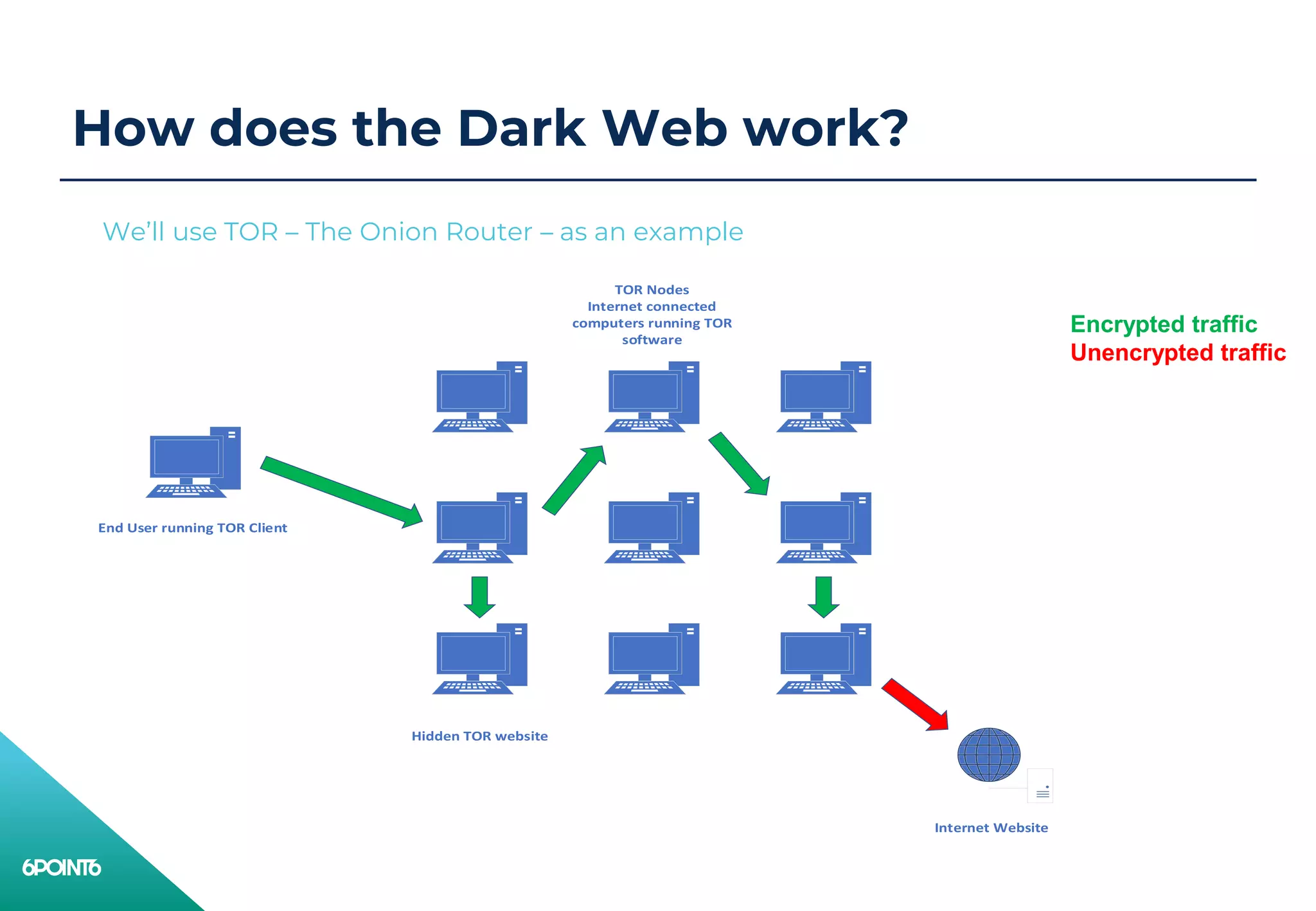
The document provides an overview of the dark web, including why attackers use it, what is available on it, how it works, and its positives and negatives. The dark web allows for anonymous planning and execution of cyber attacks through secret forums to sell stolen data and hire criminal services. While it provides innovation in security and privacy, it is also used for illegal activities and hacking due to its anonymity.