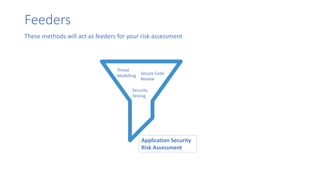
The document discusses the importance of conducting application security risk assessments throughout the Software Development Life Cycle (SDLC) to identify and mitigate risks. It highlights key strategies, including threat modeling during the design phase, secure code reviews during development, and security testing during the testing phase. Continuous risk assessment is emphasized as a critical process to ensure vulnerabilities are addressed before software release.