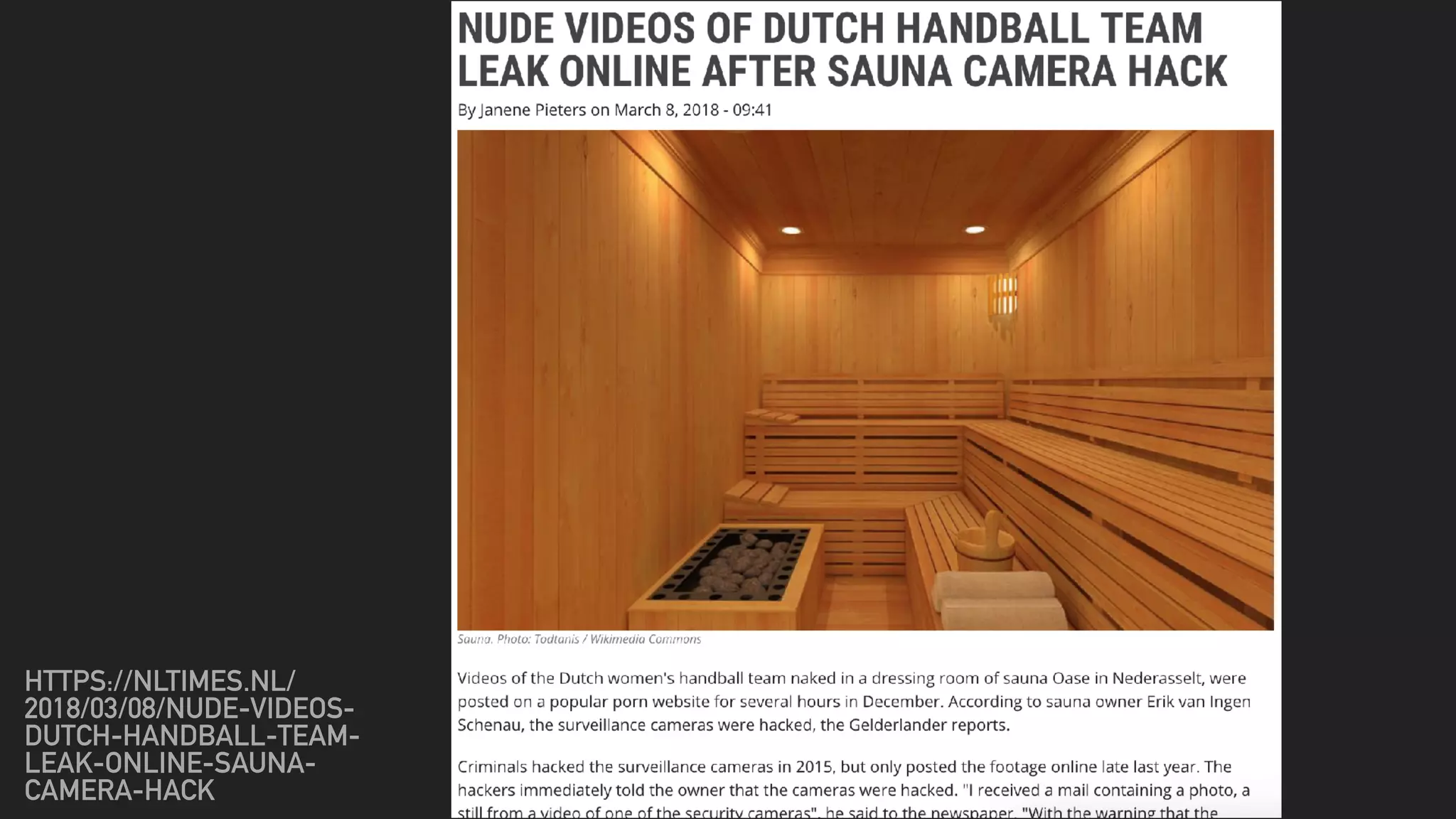
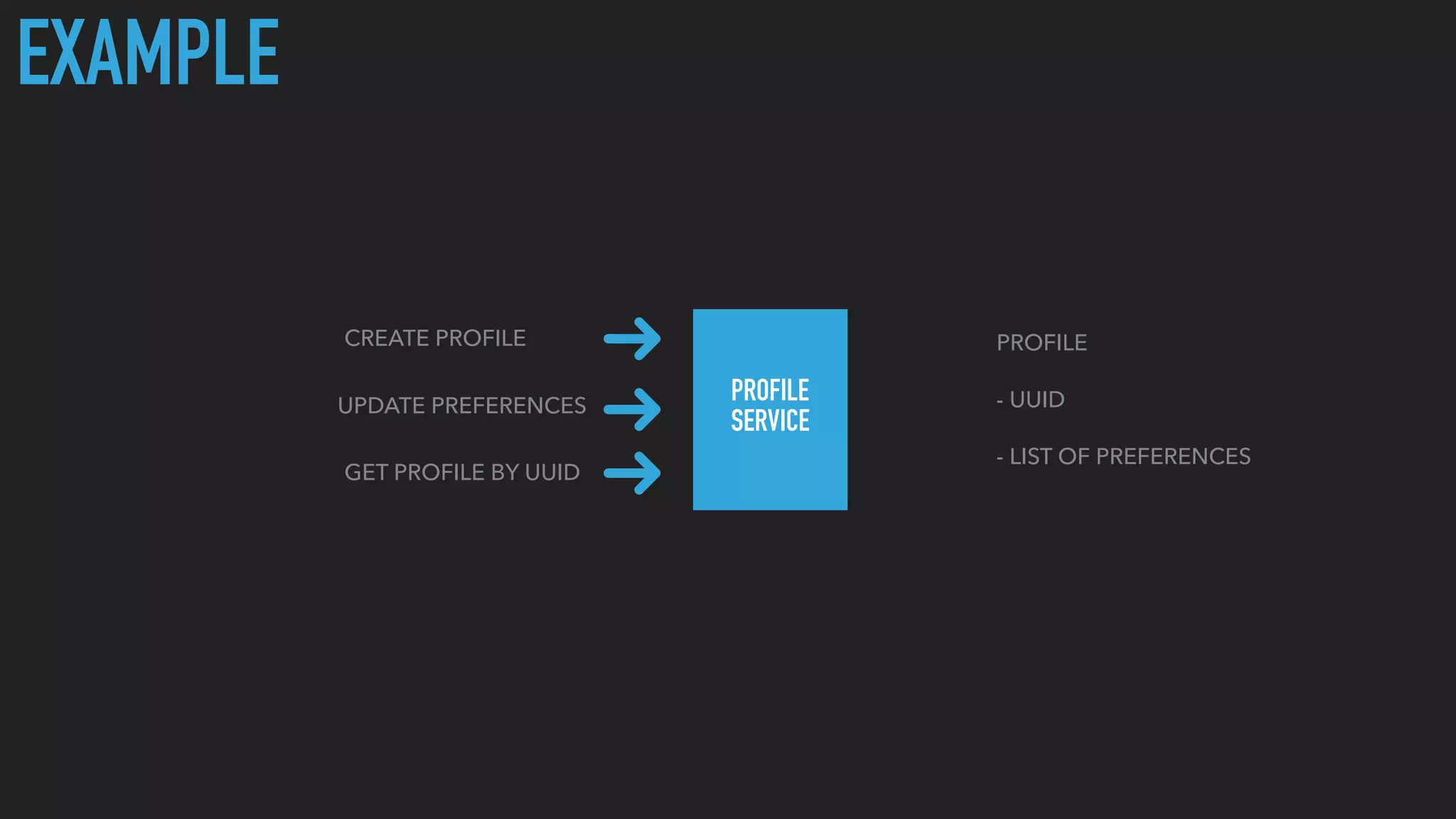
This document discusses cybersecurity threats and best practices for software development. It notes that cybercrime is a large and growing business, with damages estimated at $3 trillion worldwide in 2016. The document advocates designing systems with security in mind from the start, avoiding exposing unnecessary data, logging all activity, reviewing code for vulnerabilities, using secure password practices, and working with security teams. Developers are warned that without care, software can be "trojanized" over time to expose more data or capabilities than intended.