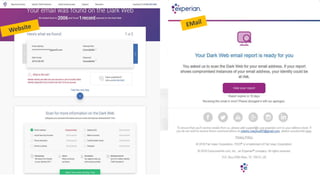
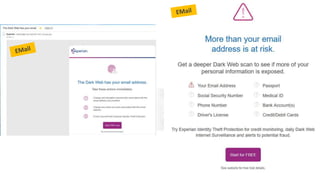
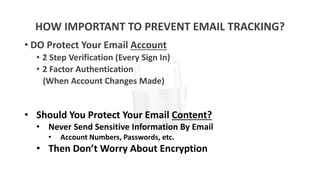
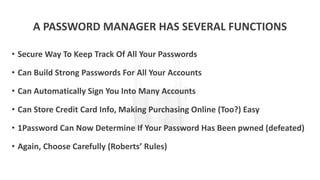
Identity theft is becoming more common and personal data is at risk from many sources. Protecting personal data requires vigilance both offline and online. Some key steps include using strong and unique passwords for all accounts, enabling two-factor authentication whenever possible, keeping software and devices updated, using a password manager to generate and store passwords, and employing a VPN and ad blockers when browsing online. The "Internet of Things" introduces new risks as more devices collect and transmit personal data, so security settings on devices must be carefully reviewed and adjusted. Overall, people need a tailored system for protecting their data and digital lifestyle.