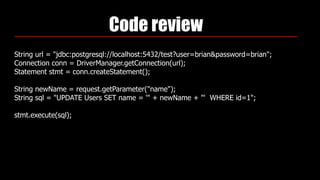
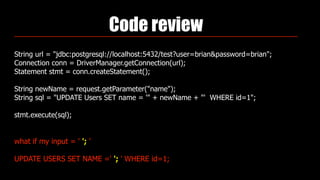
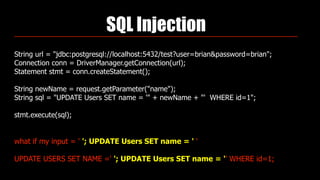
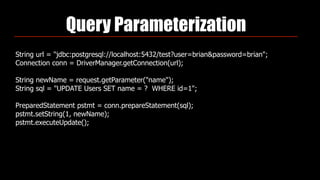
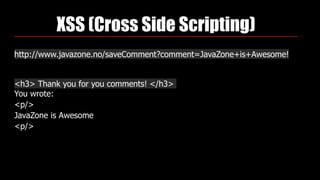
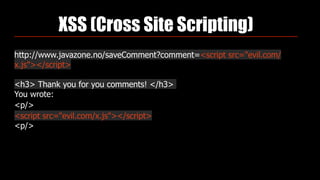
Identity theft and cybercrime pose real threats that are growing as organized criminal networks engage in cybercrime as a profitable business. As developers, we must be aware of security risks and integrate protections into our work, including securing passwords, preventing SQL injection, and avoiding cross-site scripting vulnerabilities. The Open Web Application Security Project (OWASP) provides guidance on application security best practices developers should follow.