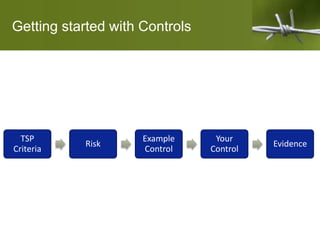
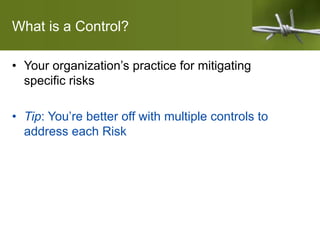
Brian Henerey discusses how DevOps practices require different controls than traditional IT approaches when conducting a SOC2 audit. He explains that SOC2 reports assess controls related to security, availability, confidentiality, processing integrity, and privacy. While controls aim to mitigate risk, they can be overly optimized for speed in DevOps. The talk provides examples of how to structure controls around common criteria and risks, while still honoring DevOps principles like autonomy, collaboration, and minimizing bureaucracy. Controls should leverage existing DevOps tools and processes to avoid busywork.