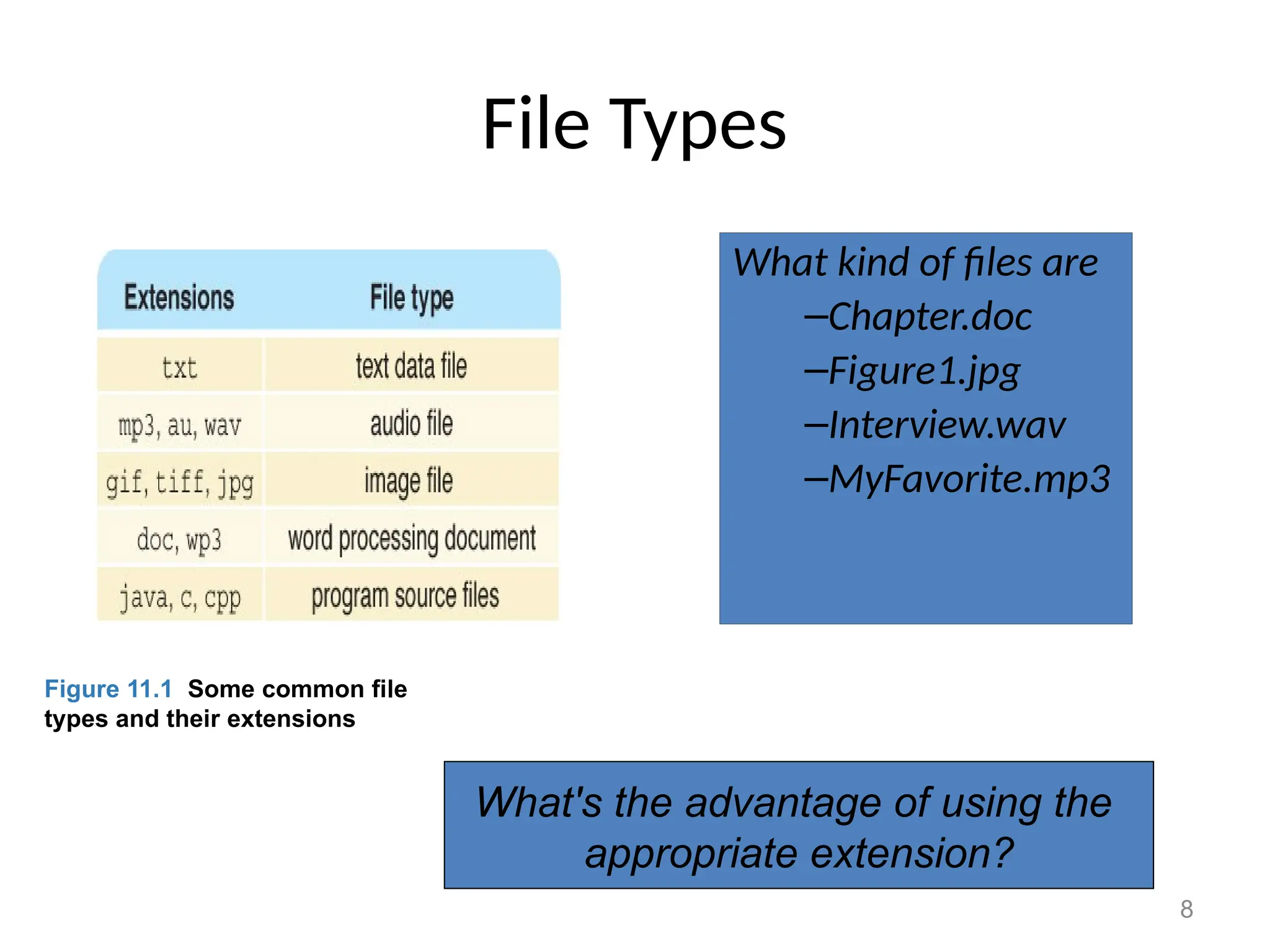
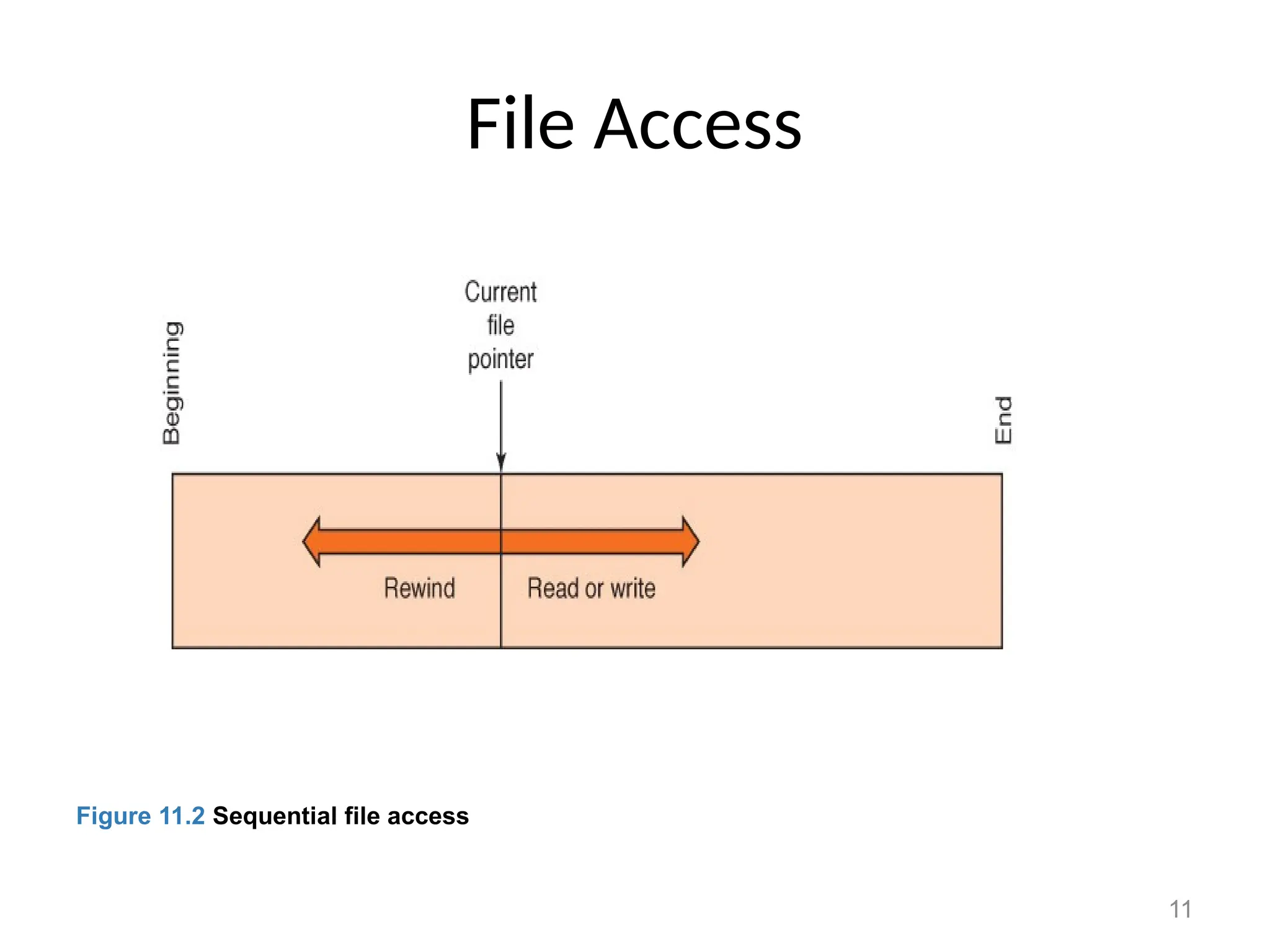
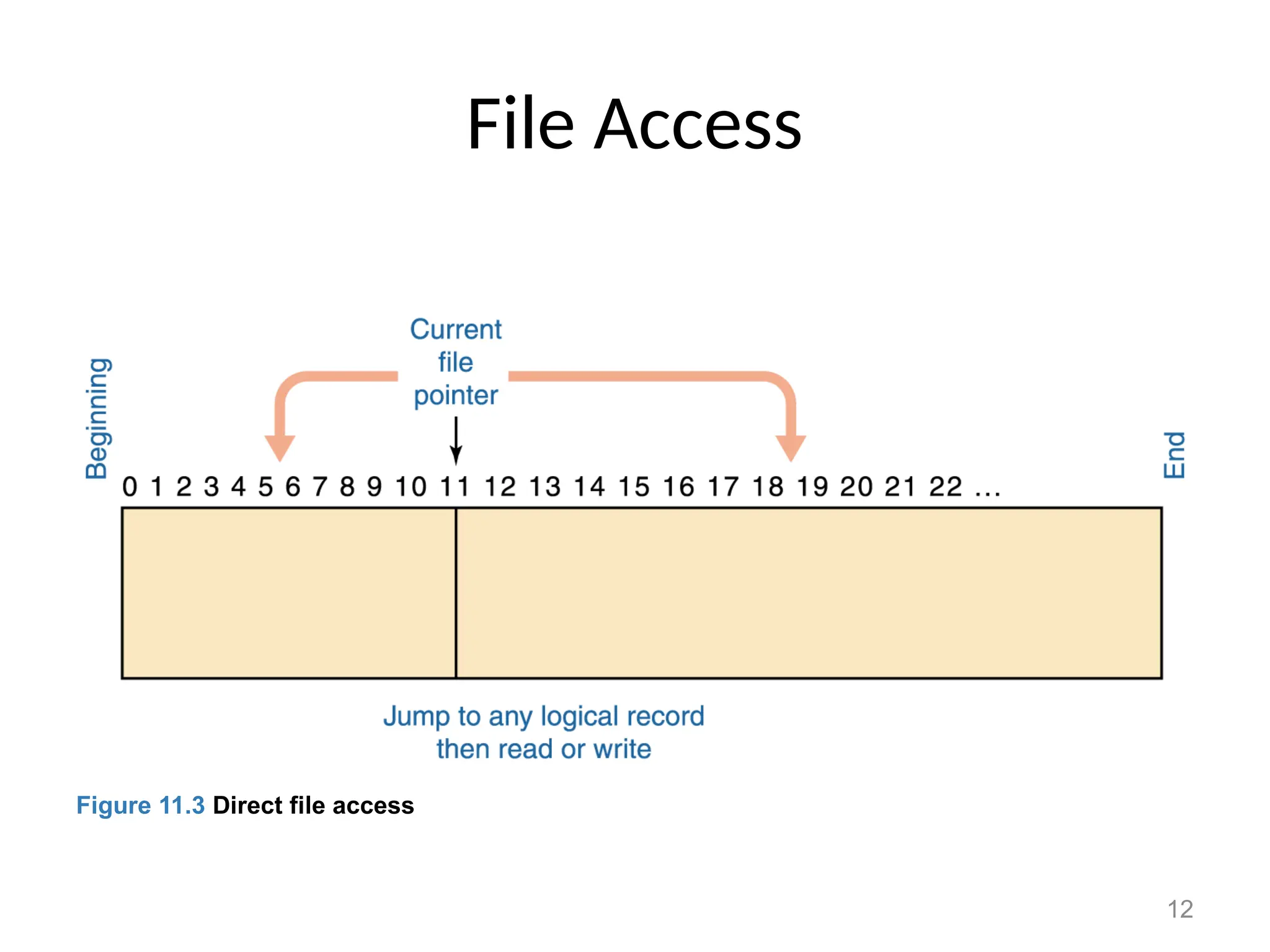
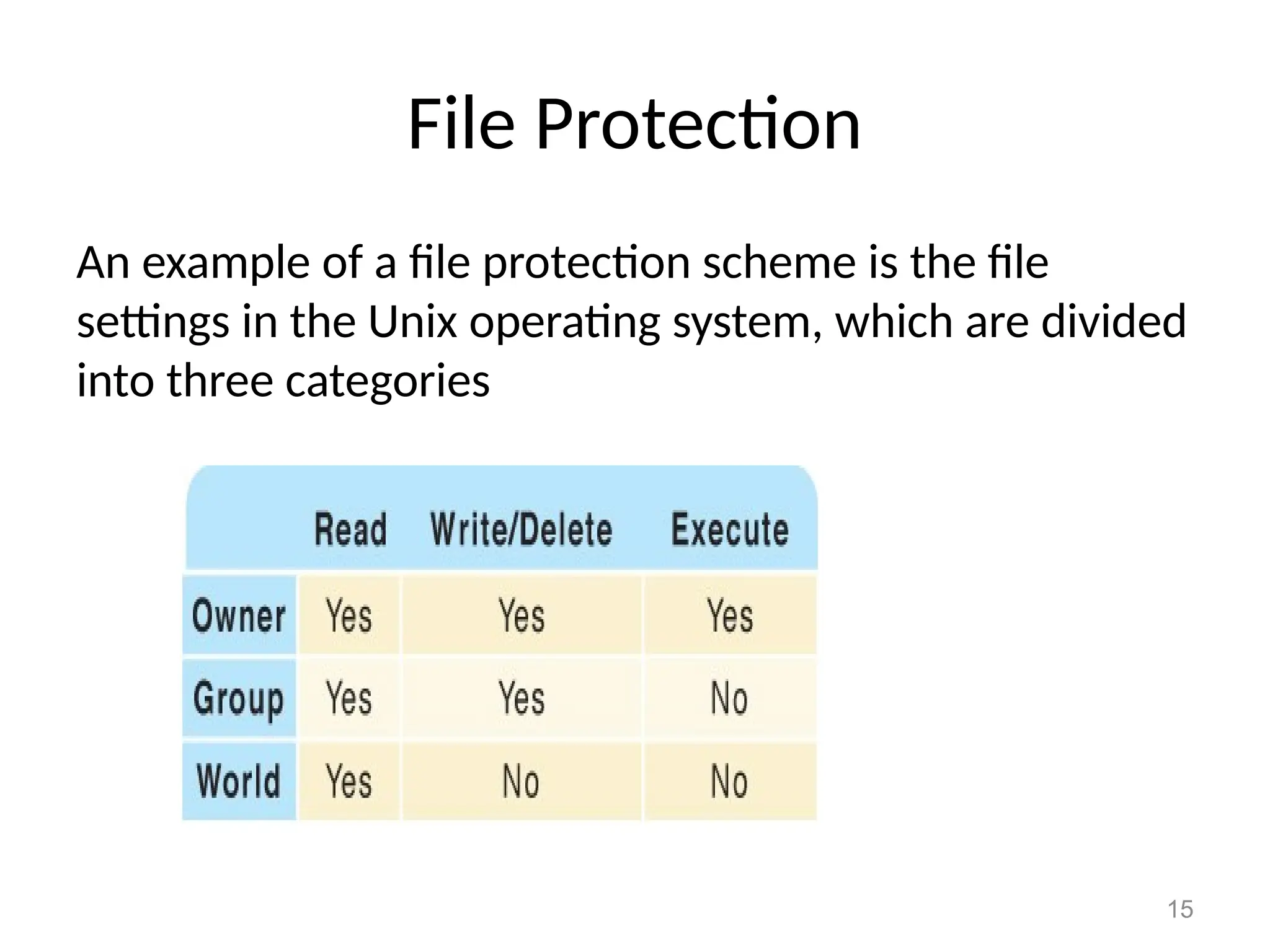
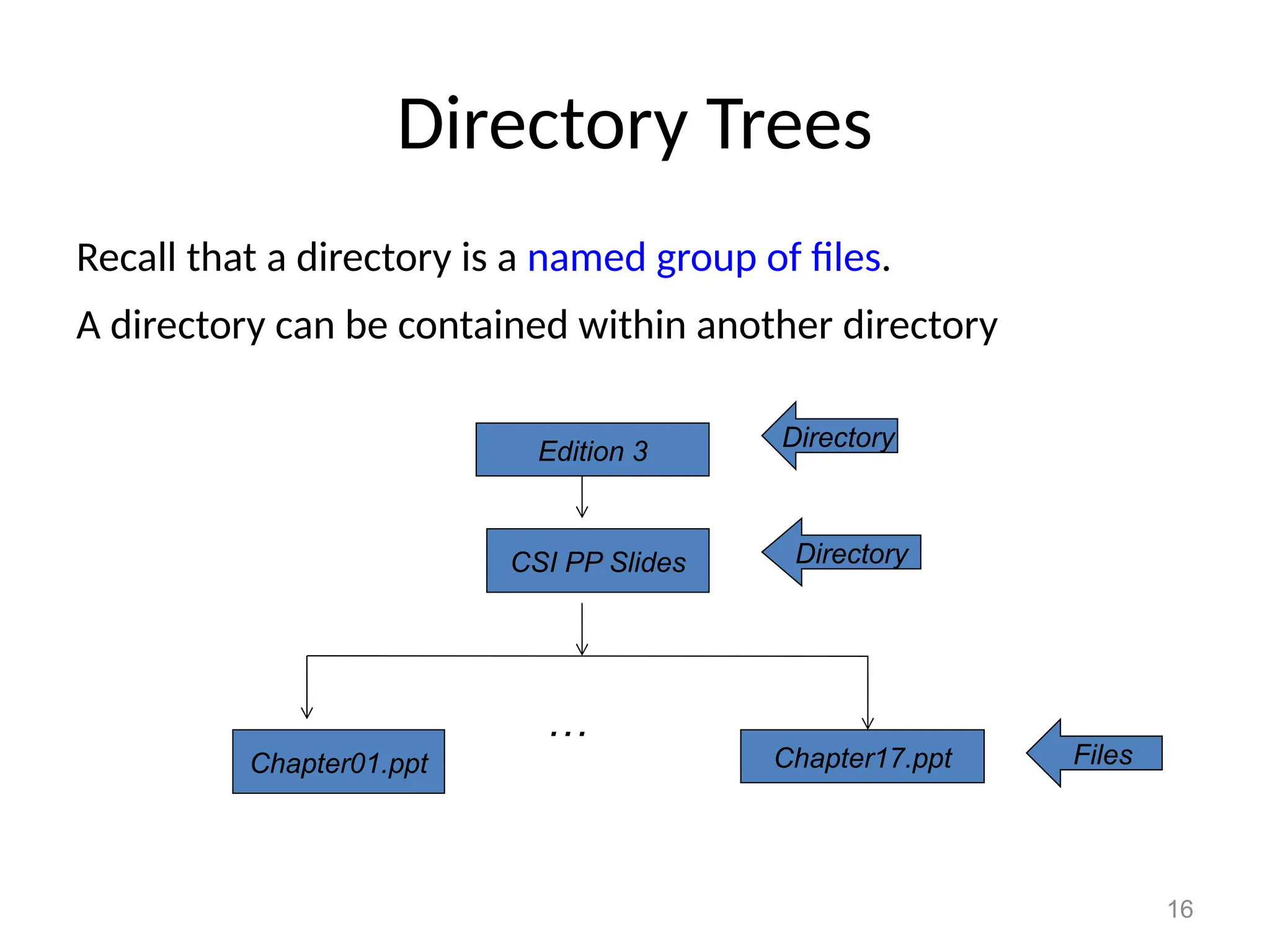
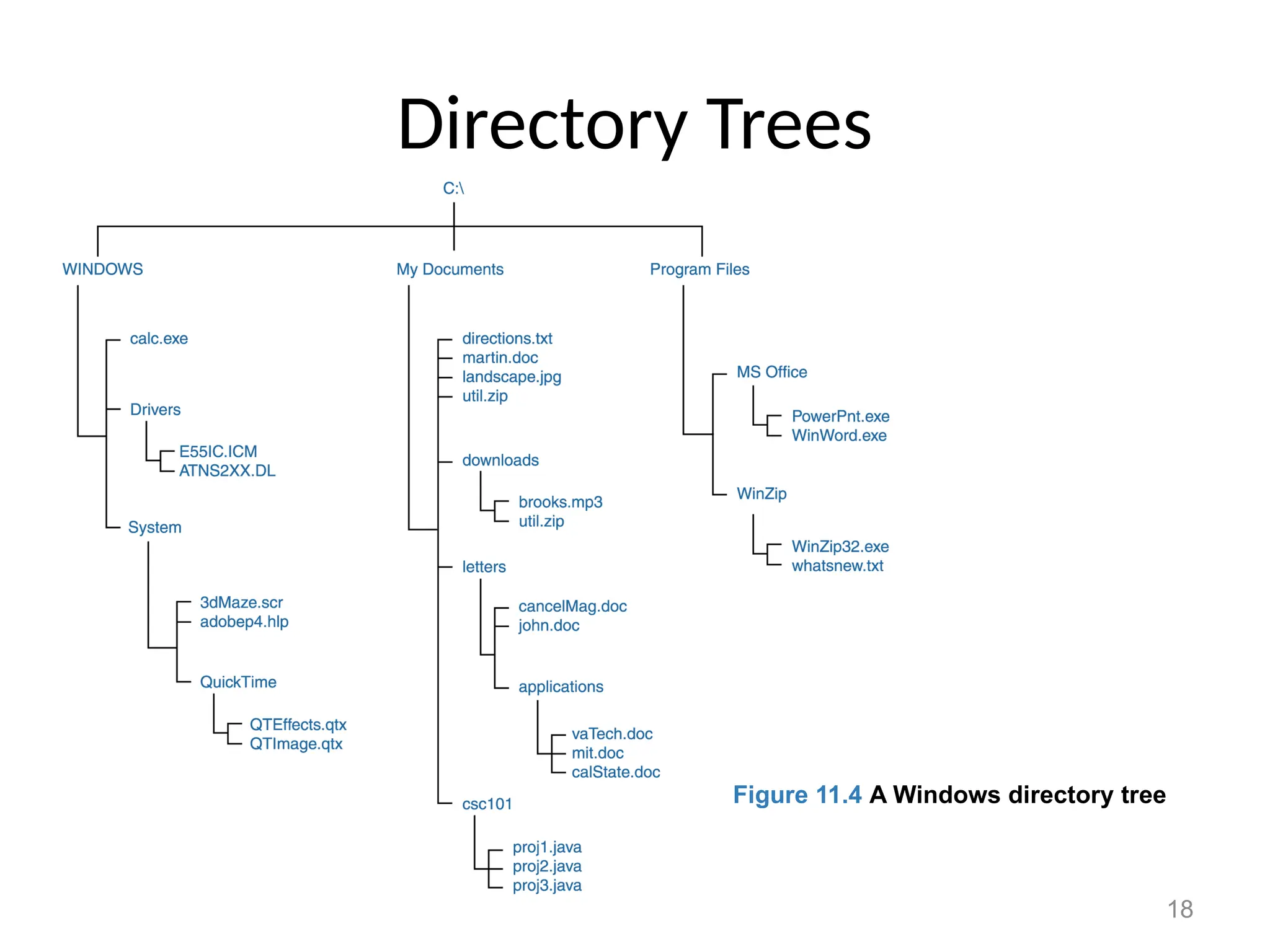
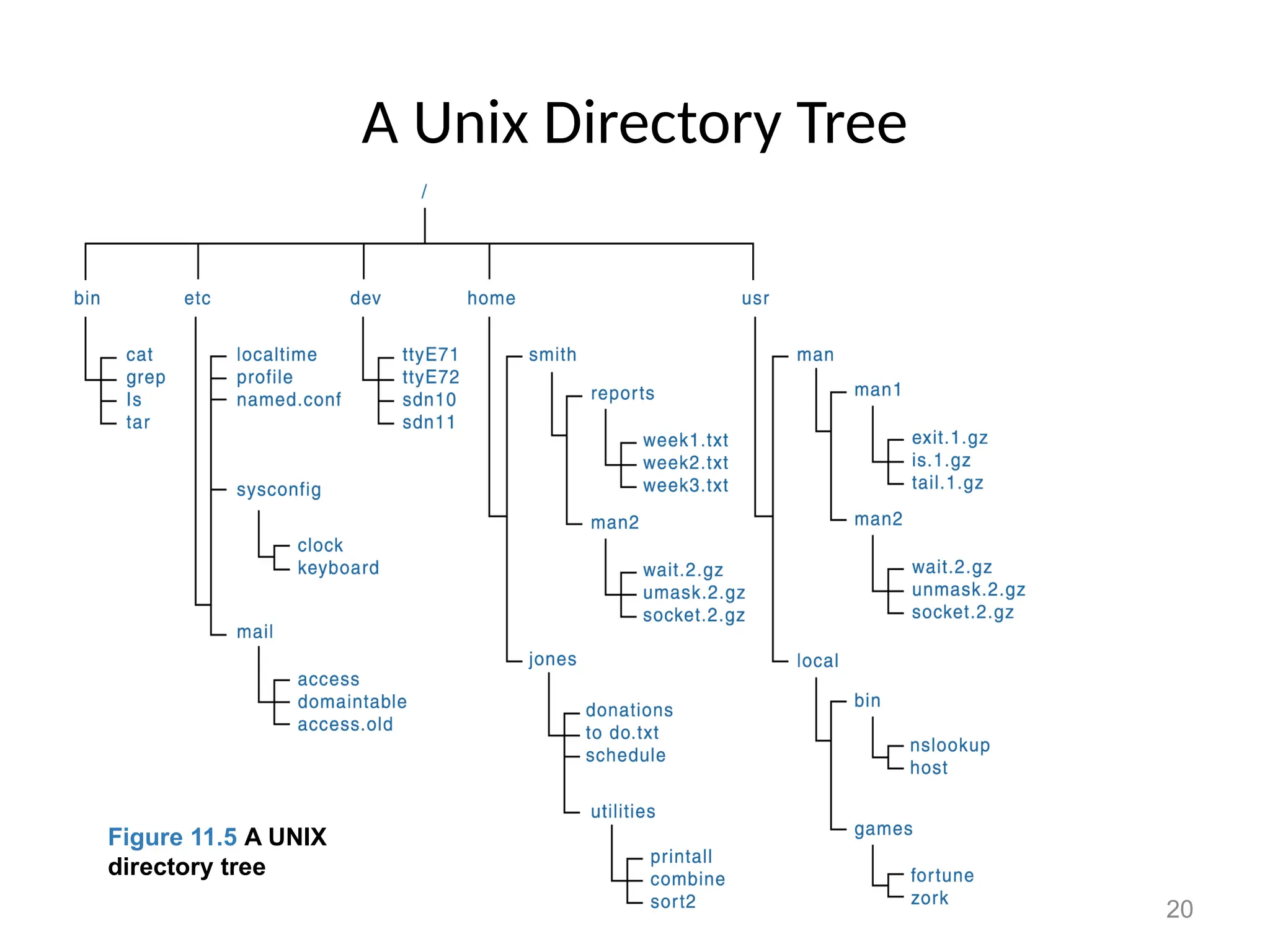
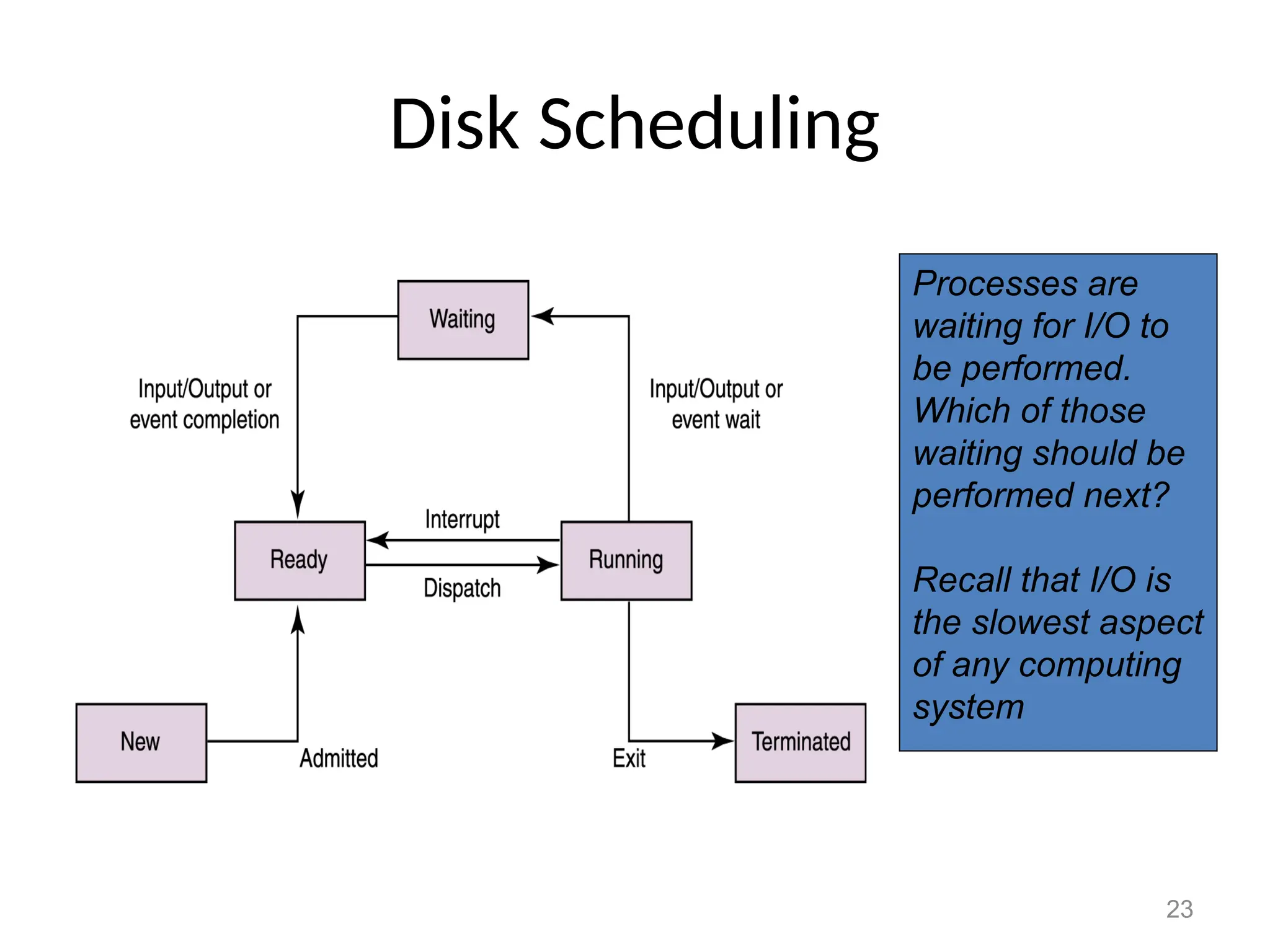
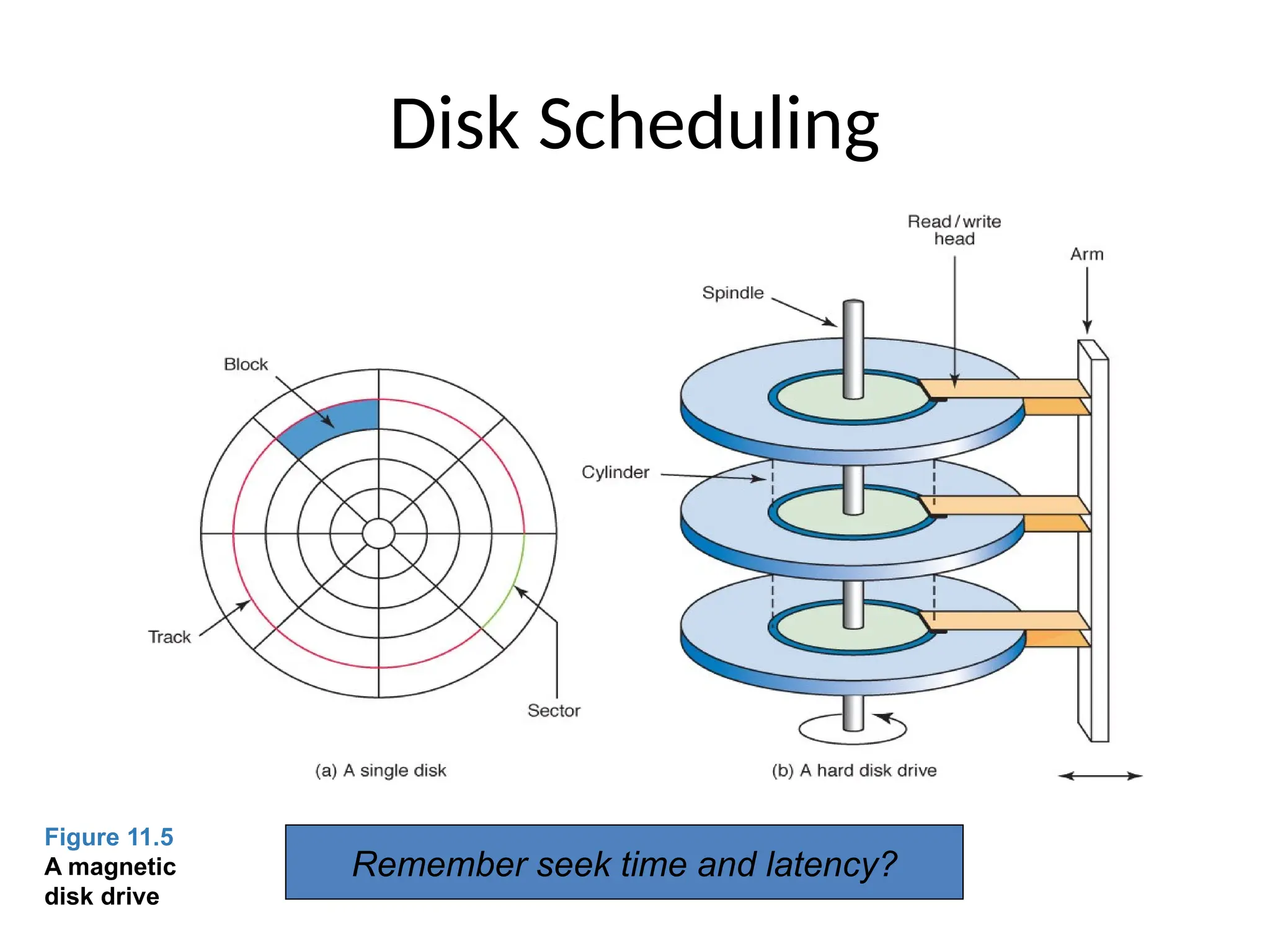
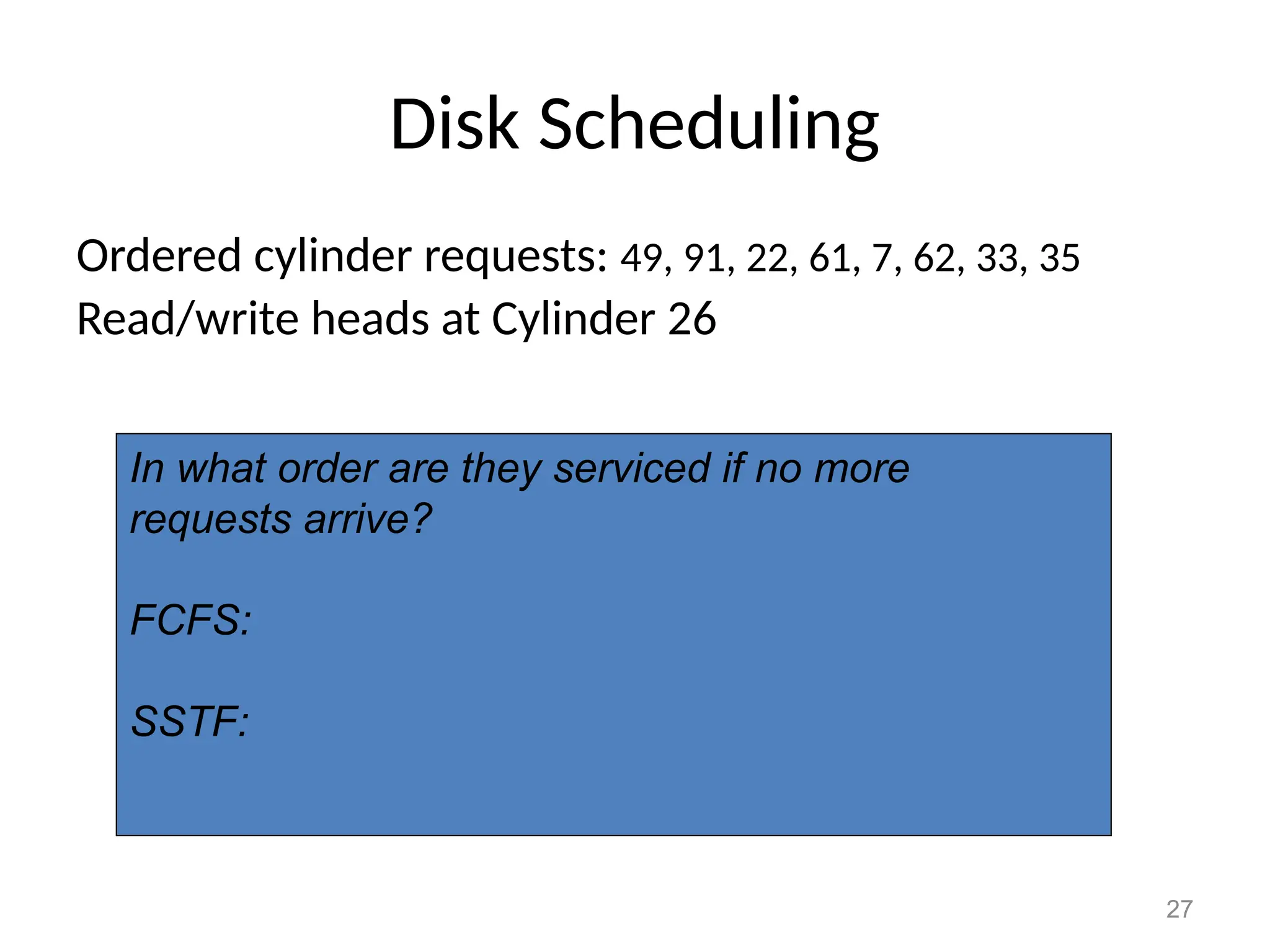
The document covers essential concepts related to file systems, including file types, operations, access methods, and protection mechanisms. It discusses sequential and direct file access, the significance of file extensions, and the organization of directories in a directory tree. Additionally, it explains disk scheduling algorithms used by operating systems to manage multiple I/O requests efficiently.