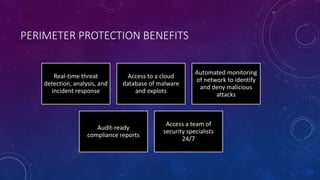
The document discusses perimeter protection solutions offered by the TNS Group to safeguard networks against cybercriminals. It highlights the importance of combining next generation firewalls (NGFW) with intrusion detection (IDS) and prevention systems (IPS) for effective monitoring and security management. Key benefits include real-time threat detection, automated network monitoring, and 24/7 access to security specialists.