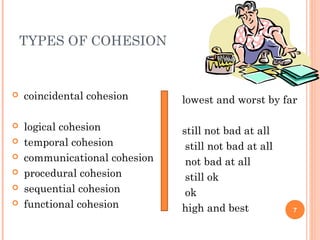
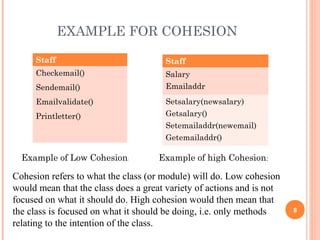
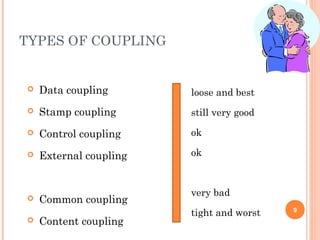
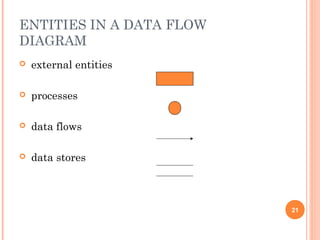
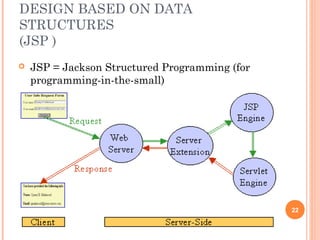
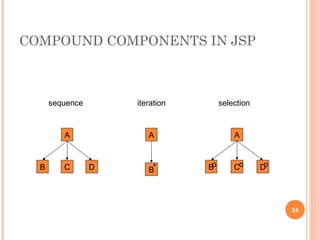
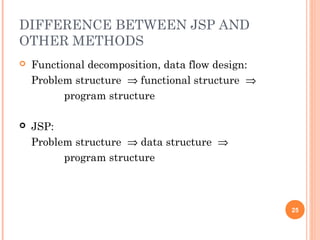
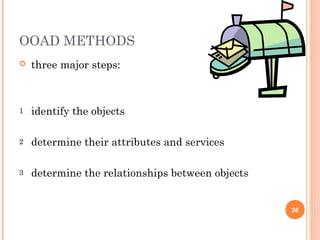
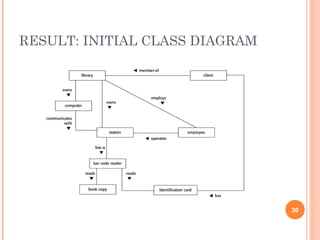
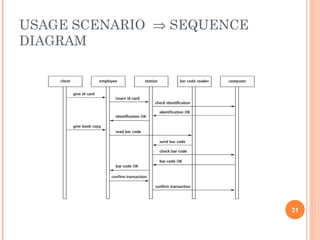
This document discusses software design principles and methods. It covers topics like abstraction, modularity, coupling and cohesion, and information hiding. It also describes different design methods including functional decomposition, data flow design, design based on data structures, and object-oriented design. Key aspects of these methods are explained, such as the stages of object-oriented analysis and design. The document provides examples to illustrate different design concepts and metrics.