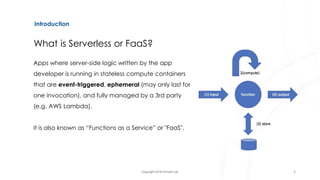
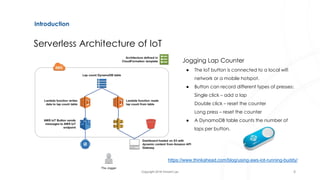
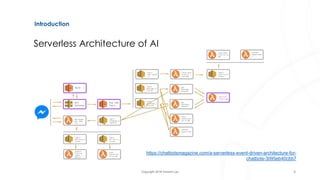
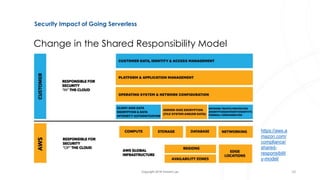
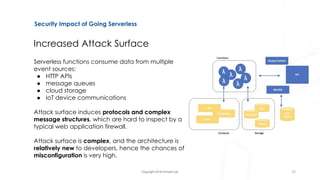
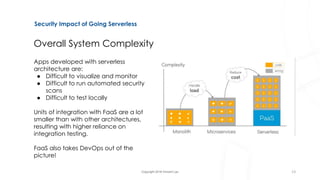
The document discusses serverless architecture, specifically Functions as a Service (FaaS), and highlights the differences between various cloud service models (IaaS, CaaS, PaaS, and FaaS). It also addresses security implications associated with serverless systems, including a shift in the responsibility model, increased attack surfaces, and top security risks such as function event data injection and insecure deployment configurations. Lastly, the document outlines strategies to mitigate these risks and emphasizes the complexity and challenges in monitoring and securing serverless applications.