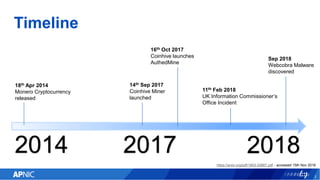
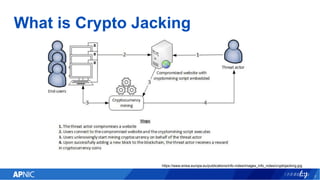
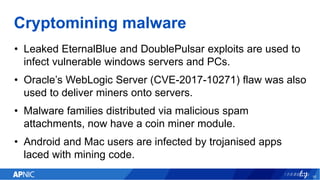
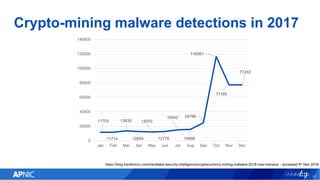
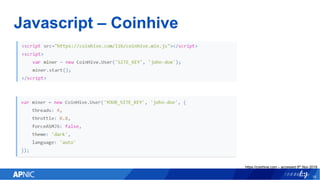
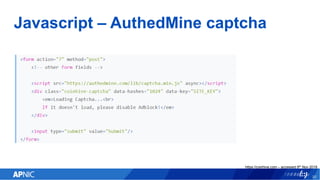
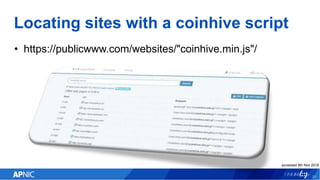
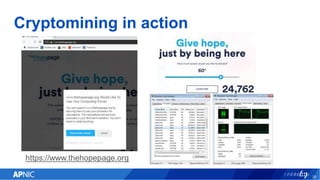
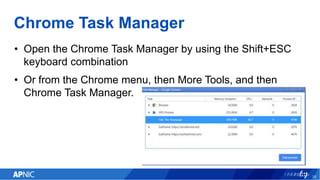
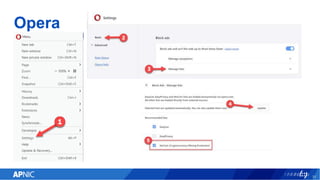
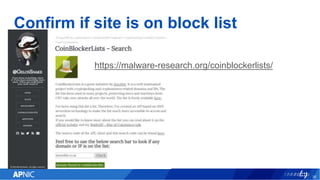
The document provides an overview of cryptojacking, highlighting its definition as the unauthorized use of computing resources to mine cryptocurrencies without consent. It discusses various web-based coin miners, cryptomining malware, and mitigation techniques to protect against such threats. The content also includes resources for identifying and blocking cryptojacking activities.