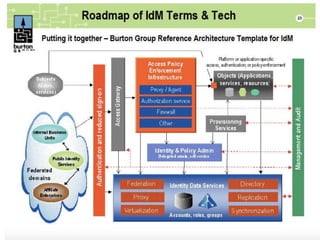
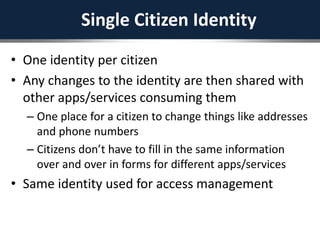
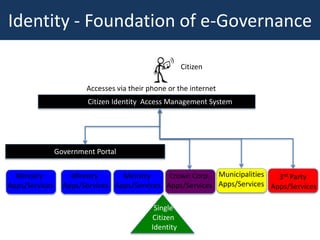
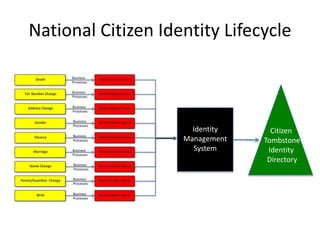
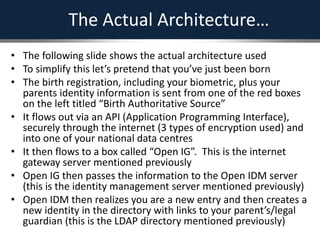
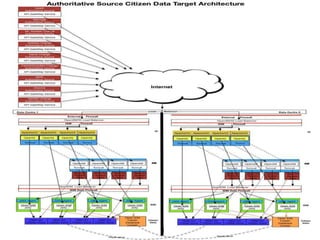
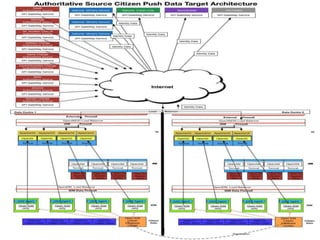
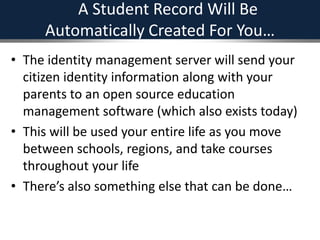
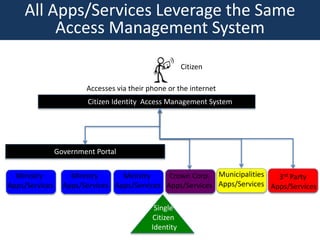
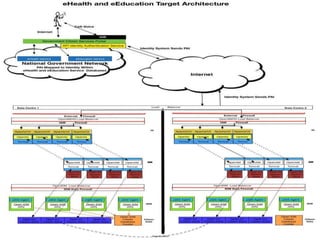
The document outlines a strategic framework for addressing the issue of 'ghost' students and enhancing education through a national identity management system that leverages cellular technology for authentication. It highlights the benefit of maintaining a lifelong student management system that keeps parents informed about their children's education while ensuring accurate funding allocation. Additionally, it draws parallels with Estonia's success in utilizing a unified identity system to improve public services and education outcomes.