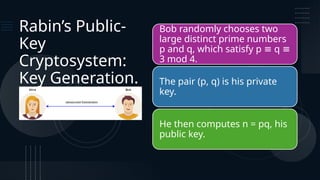
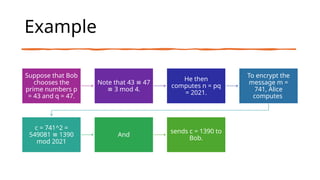
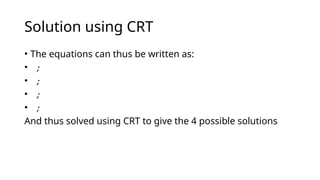
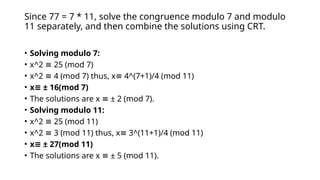
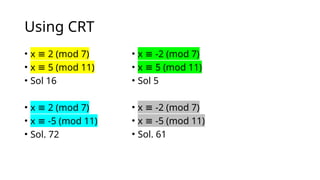
Rabin's public-key cryptosystem, developed in 1979, is based on the difficulty of computing square roots modulo a composite integer n and is secure against chosen-plaintext attacks if factoring large integers is hard. The system involves key generation with two distinct prime numbers, encryption by squaring messages, and decryption which may yield up to four possible plaintexts due to the nature of quadratic congruences. Despite its high security level, the ambiguity in decryption presents challenges for certain applications.