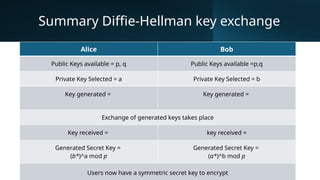
The document discusses the Diffie-Hellman algorithm, a secure method for exchanging cryptographic keys over insecure channels, developed by Martin Hellman and Whitfield Diffie in 1976. It outlines how two users, Alice and Bob, can agree on public numbers and use their private keys to calculate a shared secret key without transmitting it over the network. This method ensures secure communication, as the private keys are never shared, making it nearly impossible for hackers to derive the shared key.