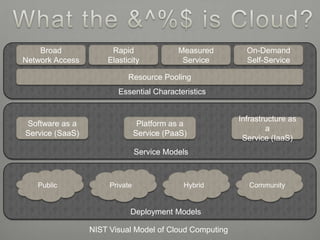
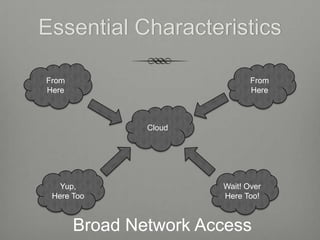
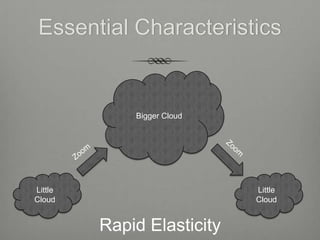
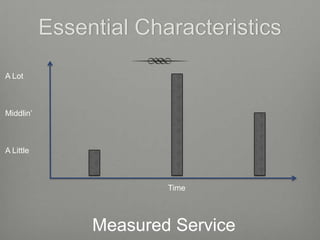
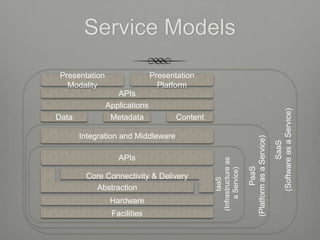
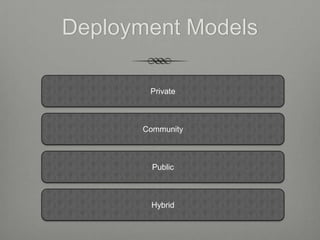
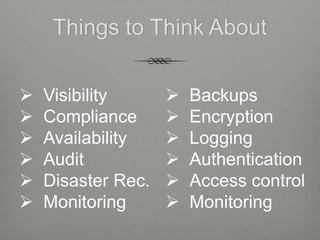
The document provides an overview of cloud computing including its essential characteristics, service models, and deployment models. It discusses the cloud computing model as composed of on-demand self-service, broad network access, resource pooling, rapid elasticity, and measured service. The service models are described as software as a service (SaaS), platform as a service (PaaS), and infrastructure as a service (IaaS). The deployment models covered are public, private, hybrid, and community clouds.