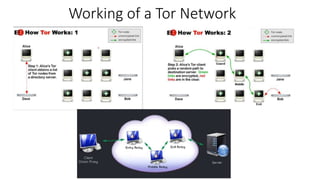
The document discusses de-anonymization of hidden services on the Tor network. Hidden services allow for anonymous hosting of websites on Tor. De-anonymization seeks to uncover the real IP addresses of hidden services that host illegal activities. The document outlines an active attack method to de-anonymize a hidden service in three phases. The attack injects malicious nodes as relays to eventually control an entry guard node and force the hidden service to select it. This allows the attacker to directly connect to the server and learn its IP address, completing the de-anonymization.