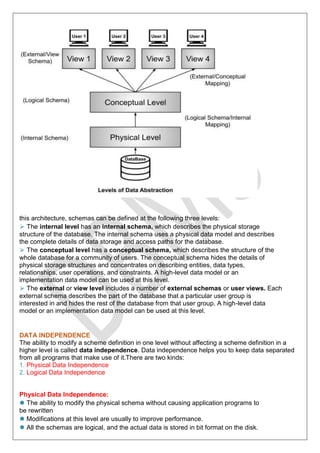
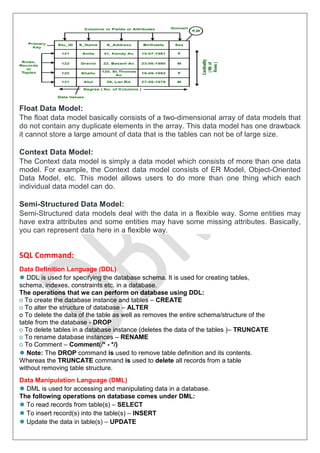
The document outlines the objectives and contents of a Database Management System (DBMS) course for the academic year 2024-25, covering fundamental concepts such as what a DBMS is, its advantages over file processing systems, SQL data types, schema definitions, and database architecture. It details the roles of database administrators and the various applications of DBMS, as well as providing insights into data independence, data abstraction, and the differences between hierarchical, network, and relational data models. Additionally, it includes an overview of SQL and the types of commands used for database management.