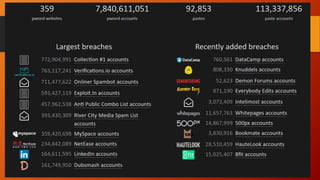
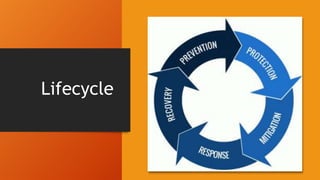
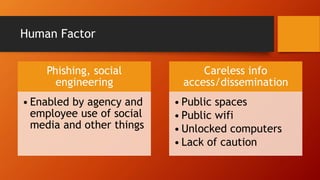
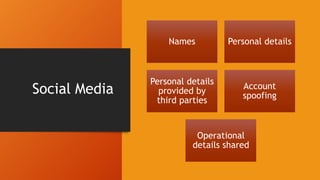
This document discusses cybersecurity issues for emergency managers. It notes that cybersecurity is everyone's responsibility, not just IT, and outlines common threats like data breaches, human error, and cyber warfare. It then details steps in the cybersecurity lifecycle including prevention through policies and training, protection, mitigation through backups and monitoring, response planning, and recovery procedures. The document warns that most organizations lack comprehensive cybersecurity policies and enforcement. It also discusses social engineering threats and provides examples of cyber incidents including a case where prank 911 calls overloaded emergency systems.