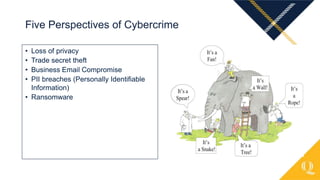
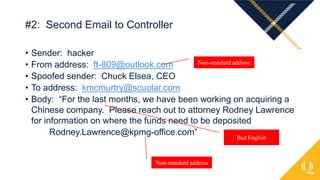
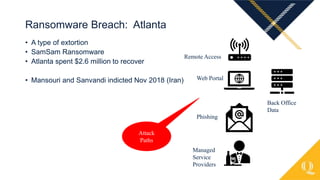
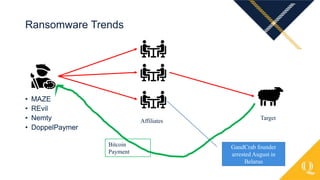
This document provides an overview of various cybercrime topics including common cybercrimes like business email compromise, ransomware, and data breaches. It discusses statistics on internet usage and economic factors related to cybercrime. Examples are given of real data breaches at companies like Equifax and First American Title that resulted from unpatched vulnerabilities. Lessons learned are outlined around the importance of swift patch management, user education, and an organizational approach to information security where technology, policies, and human factors all play a role. Emerging trends mentioned include increased COVID and election related cyber attacks relying on disinformation.