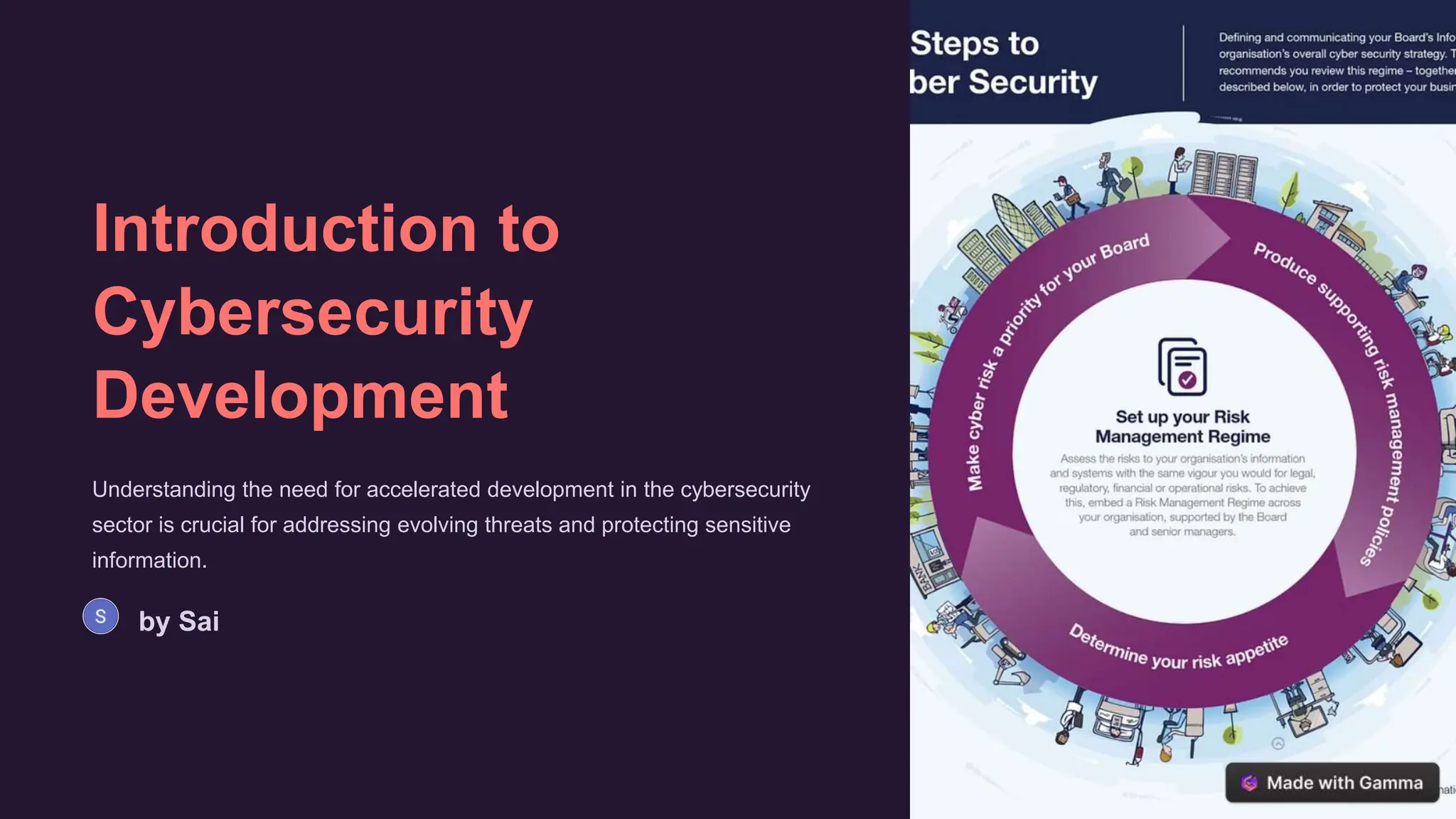
The document discusses the importance of accelerating development in cybersecurity to address evolving digital threats and protect sensitive data. It outlines key challenges to rapid development like the complexity of threats and lack of resources. The document recommends strategies such as collaborative partnerships, agile development, and leveraging automation/AI. It also stresses the need to invest in cybersecurity talent and skill development. The conclusion emphasizes that continuous adaptation, an integrated approach, and embracing the dynamic cyber landscape are essential for sustainable progress in cybersecurity.