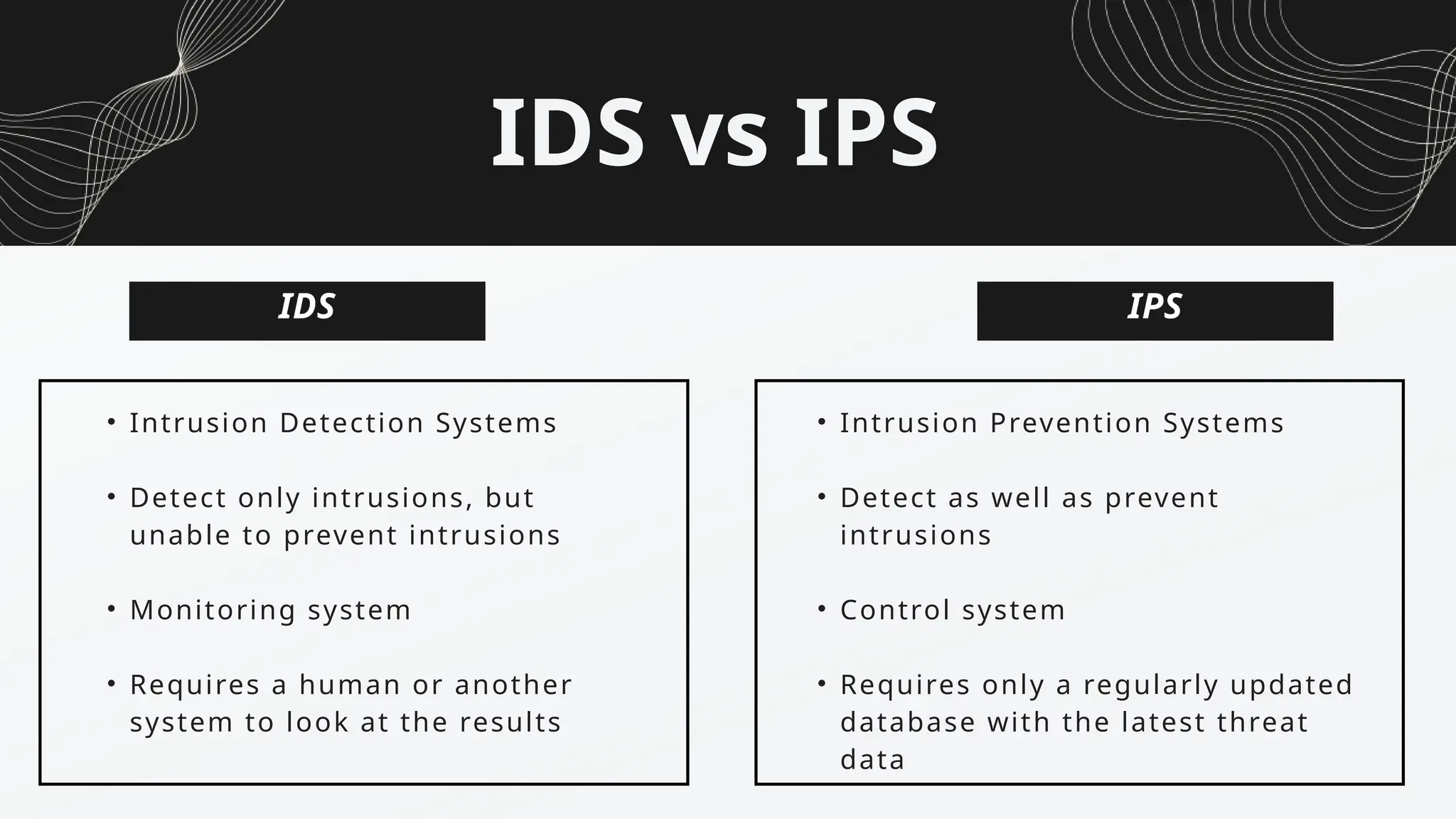
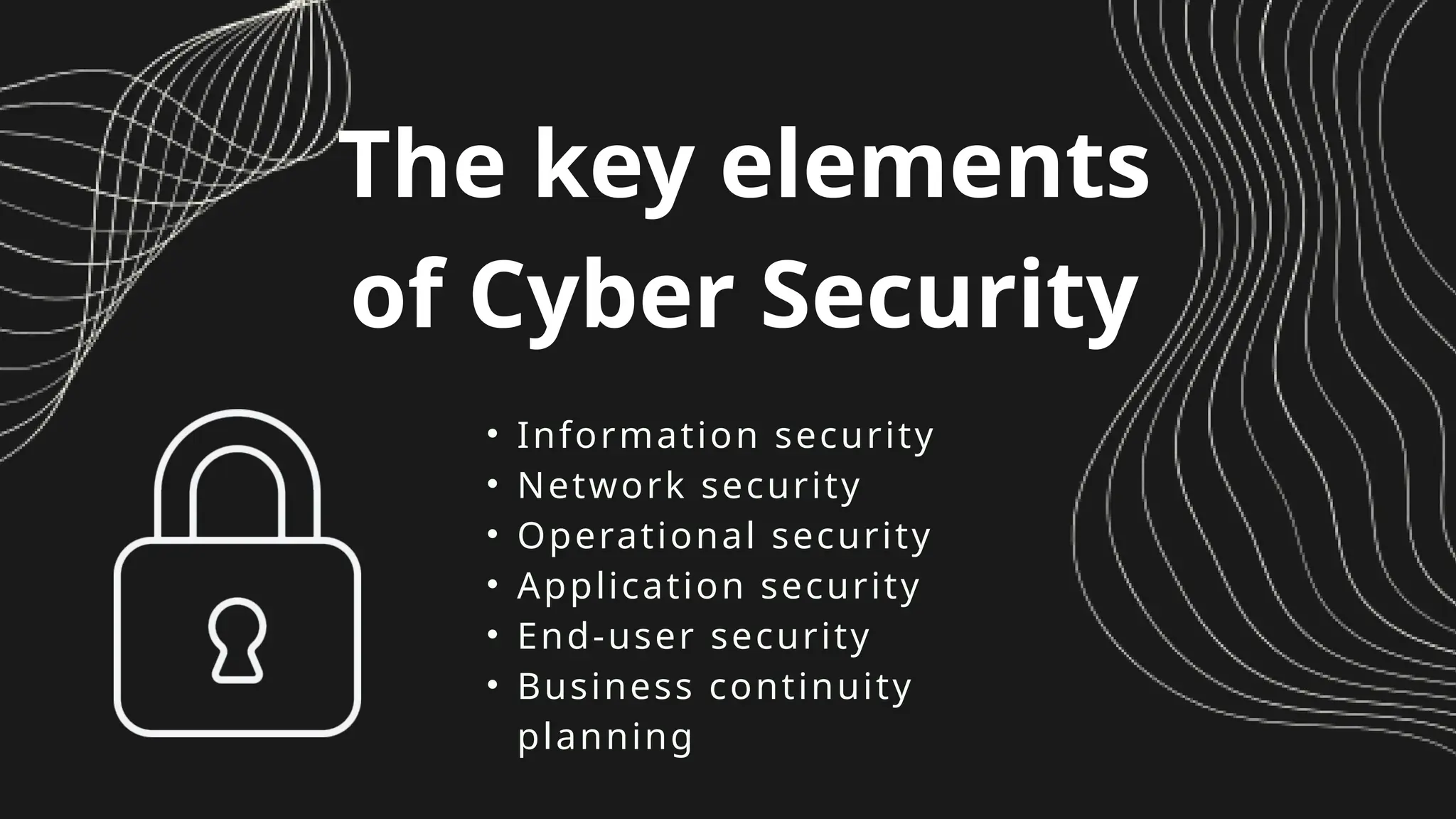
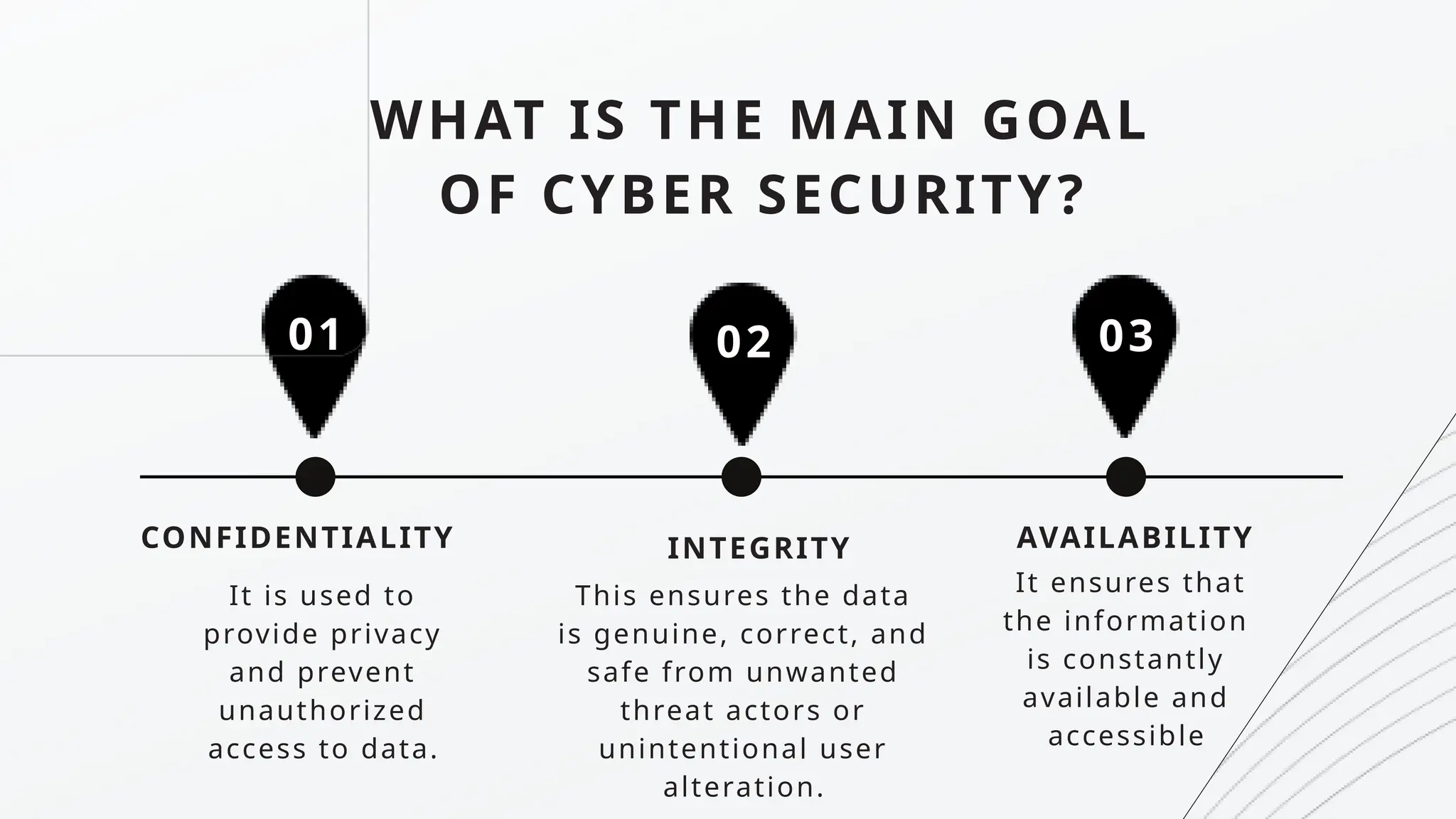
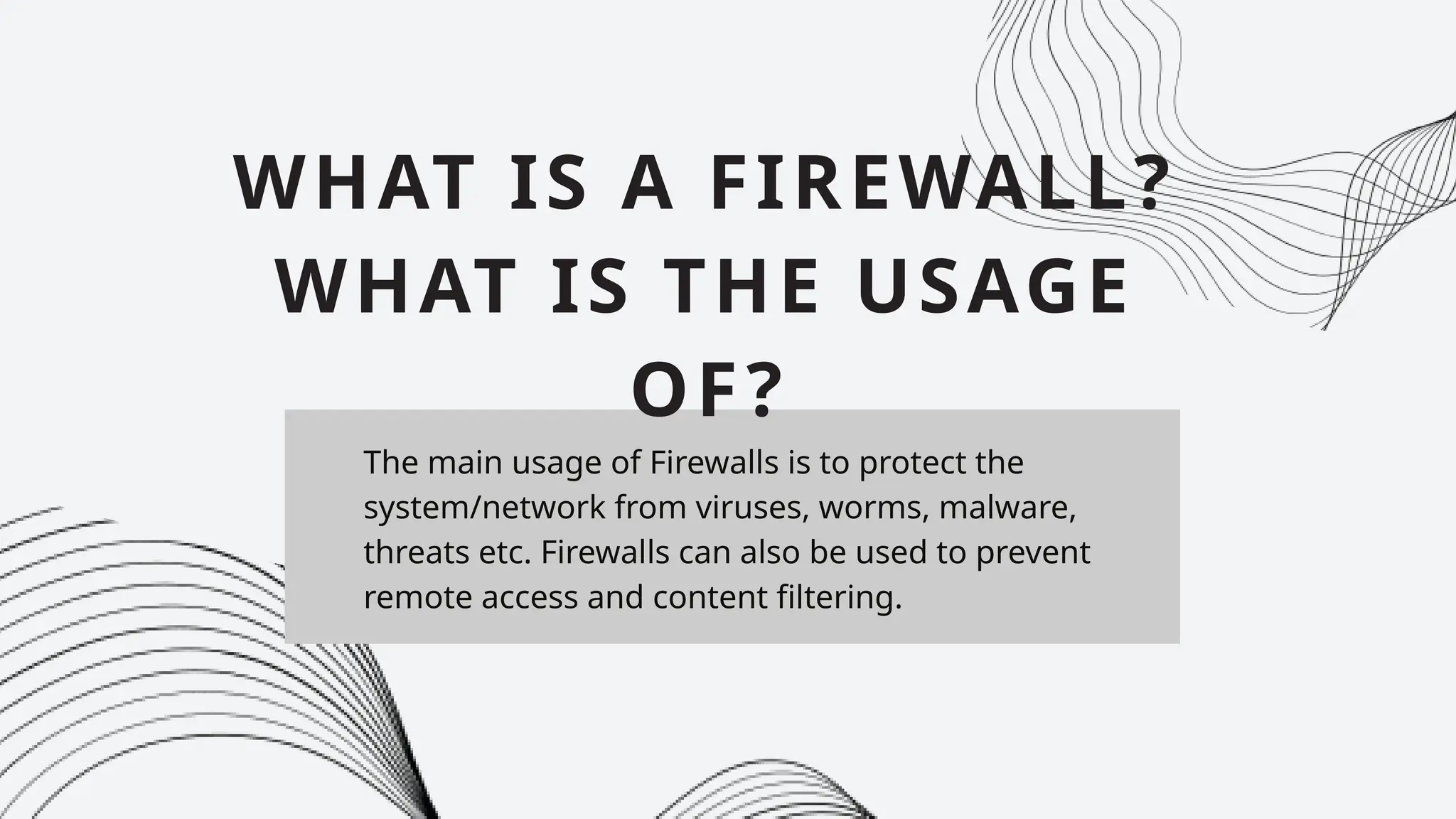
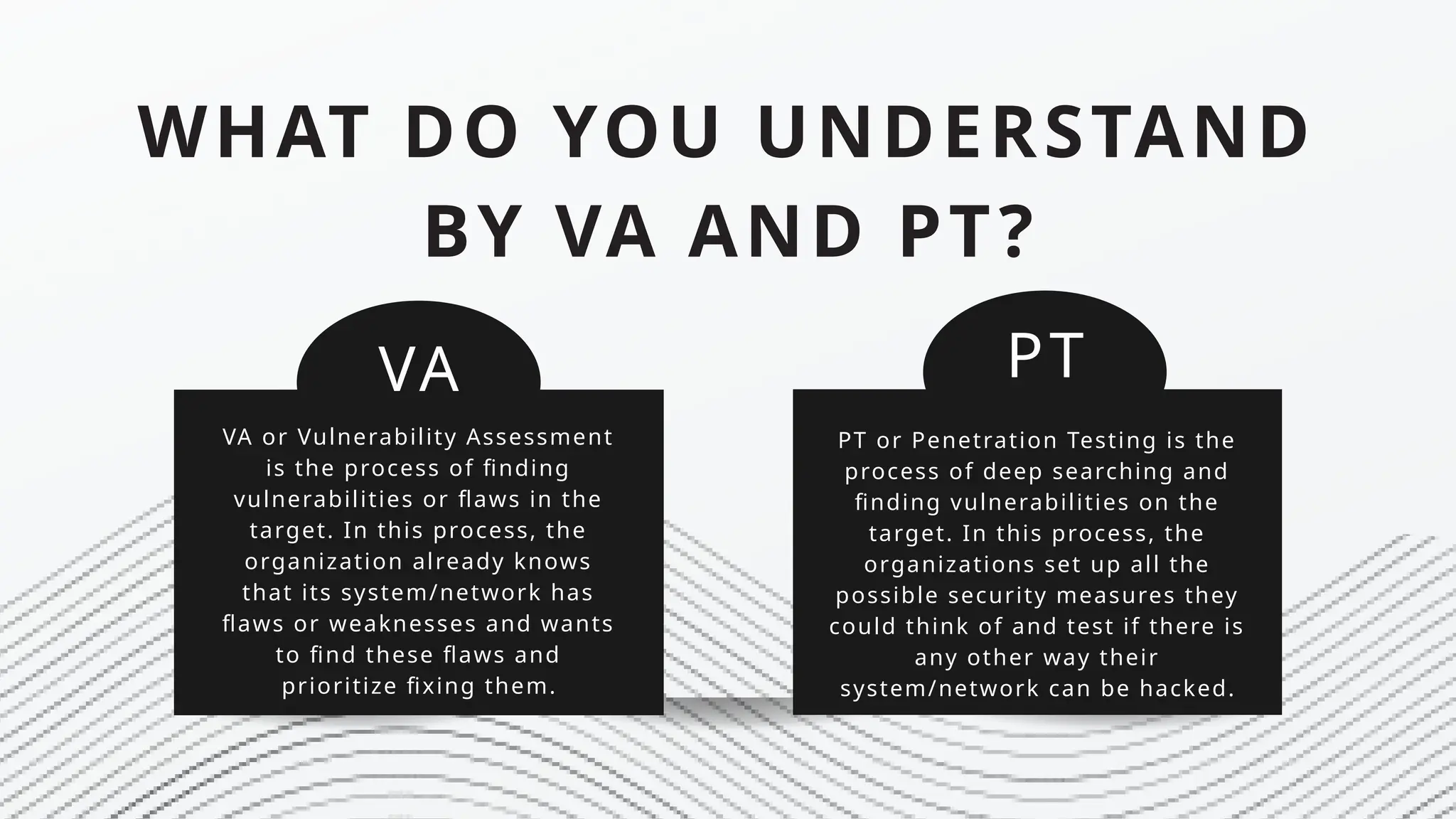
Cyber Security is a practice of protecting internet-connected systems such as hardware, software, programs, computers, servers, mobile devices, electronic systems, networks, and data from malicious digital attacks.
https://www.tpointtech.com/cyber-security-tnterview-questions