Cyber liability and the growing threat to emergency services
•
0 likes•134 views
Emergency service organizations are high value targets of cybercriminals due to patient medical records, personal and organizationa information and more.
Report
Share
Report
Share
Download to read offline
Recommended
Recommended
More Related Content
What's hot
What's hot (20)
Critical Controls Might Have Prevented the Target Breach

Critical Controls Might Have Prevented the Target Breach
Rapid7 Report: Data Breaches in the Government Sector

Rapid7 Report: Data Breaches in the Government Sector
Protecting Patient Health Information in the HITECH Era

Protecting Patient Health Information in the HITECH Era
The Unseen Enemy - Protecting the Brand, the Assets and the Customers 

The Unseen Enemy - Protecting the Brand, the Assets and the Customers
The Sedona Canada Panel on Privacy and E-Discovery

The Sedona Canada Panel on Privacy and E-Discovery
Viewers also liked
Small Business ‐ How to Become and Stay a Successful Construction Contractor

Small Business ‐ How to Become and Stay a Successful Construction ContractorThe Frisby Group - Construction Consultants
Total Quality Management for Improved Project Success - Construction Claims M...

Total Quality Management for Improved Project Success - Construction Claims M...The Frisby Group - Construction Consultants
Viewers also liked (16)
The Role of Documentation & The Key to Labor Management

The Role of Documentation & The Key to Labor Management
The 25/10 Concept - Improving the Probability of Success

The 25/10 Concept - Improving the Probability of Success
Small Business ‐ How to Become and Stay a Successful Construction Contractor

Small Business ‐ How to Become and Stay a Successful Construction Contractor
Old Bottle New Wine - Lean Management In Construction

Old Bottle New Wine - Lean Management In Construction
Total Quality Management for Improved Project Success - Construction Claims M...

Total Quality Management for Improved Project Success - Construction Claims M...
Similar to Cyber liability and the growing threat to emergency services
Similar to Cyber liability and the growing threat to emergency services (20)
American Bar Association guidelines on Cyber Security standards

American Bar Association guidelines on Cyber Security standards
Cost of Data Breach Study in 2015 - United States - Presented by IBM and Pono...

Cost of Data Breach Study in 2015 - United States - Presented by IBM and Pono...
The Protected Harbor 2022 Legal Services Data Breach Trend Report (2).pdf

The Protected Harbor 2022 Legal Services Data Breach Trend Report (2).pdf
Advanced PII / PI data discovery and data protection

Advanced PII / PI data discovery and data protection
4 Steps to Financial Data Security Compliance Technologies to Help Your Finan...

4 Steps to Financial Data Security Compliance Technologies to Help Your Finan...
iStart feature: Protect and serve how safe is your personal data?

iStart feature: Protect and serve how safe is your personal data?
Who is the next target and how is big data related ulf mattsson

Who is the next target and how is big data related ulf mattsson
Recently uploaded
APM Welcome, APM North West Network Conference, Synergies Across Sectors

APM Welcome, APM North West Network Conference, Synergies Across SectorsAssociation for Project Management
Organic Name Reactions for the students and aspirants of Chemistry12th.pptx

Organic Name Reactions for the students and aspirants of Chemistry12th.pptxVS Mahajan Coaching Centre
“Oh GOSH! Reflecting on Hackteria's Collaborative Practices in a Global Do-It...

“Oh GOSH! Reflecting on Hackteria's Collaborative Practices in a Global Do-It...Marc Dusseiller Dusjagr
Recently uploaded (20)
APM Welcome, APM North West Network Conference, Synergies Across Sectors

APM Welcome, APM North West Network Conference, Synergies Across Sectors
A Critique of the Proposed National Education Policy Reform

A Critique of the Proposed National Education Policy Reform
Contemporary philippine arts from the regions_PPT_Module_12 [Autosaved] (1).pptx![Contemporary philippine arts from the regions_PPT_Module_12 [Autosaved] (1).pptx](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Contemporary philippine arts from the regions_PPT_Module_12 [Autosaved] (1).pptx](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Contemporary philippine arts from the regions_PPT_Module_12 [Autosaved] (1).pptx
Measures of Central Tendency: Mean, Median and Mode

Measures of Central Tendency: Mean, Median and Mode
Incoming and Outgoing Shipments in 1 STEP Using Odoo 17

Incoming and Outgoing Shipments in 1 STEP Using Odoo 17
Presentation by Andreas Schleicher Tackling the School Absenteeism Crisis 30 ...

Presentation by Andreas Schleicher Tackling the School Absenteeism Crisis 30 ...
Separation of Lanthanides/ Lanthanides and Actinides

Separation of Lanthanides/ Lanthanides and Actinides
Organic Name Reactions for the students and aspirants of Chemistry12th.pptx

Organic Name Reactions for the students and aspirants of Chemistry12th.pptx
“Oh GOSH! Reflecting on Hackteria's Collaborative Practices in a Global Do-It...

“Oh GOSH! Reflecting on Hackteria's Collaborative Practices in a Global Do-It...
Industrial Policy - 1948, 1956, 1973, 1977, 1980, 1991

Industrial Policy - 1948, 1956, 1973, 1977, 1980, 1991
Presiding Officer Training module 2024 lok sabha elections

Presiding Officer Training module 2024 lok sabha elections
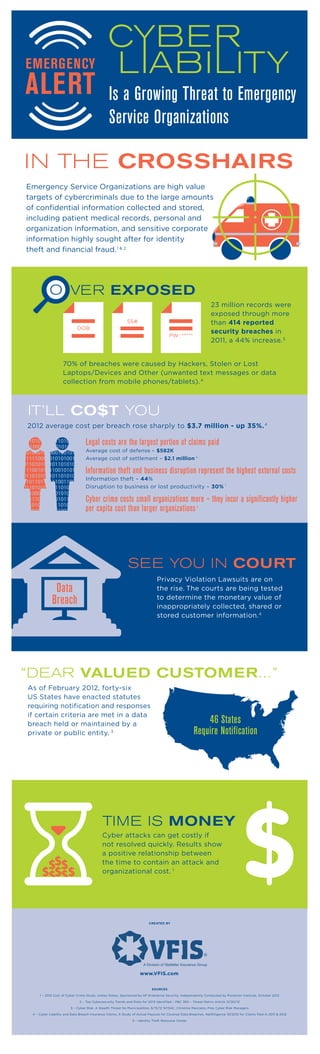
Cyber liability and the growing threat to emergency services
- 1. IN THE CROSSHAIRS Emergency Service Organizations are high value targets of cybercriminals due to the large amounts of confidential information collected and stored, including patient medical records, personal and organization information, and sensitive corporate information highly sought after for identity theft and financial fraud.1 & 2 VER EXPOSED PW: ***** SS# DOB 23 million records were exposed through more than 414 reported security breaches in 2011, a 44% increase.5 70% of breaches were caused by Hackers, Stolen or Lost Laptops/Devices and Other (unwanted text messages or data collection from mobile phones/tablets).4 IT’LL CO$T YOU 2012 average cost per breach rose sharply to $3.7 million - up 35%.4 4 1 SEE YOU IN COURT Privacy Violation Lawsuits are on the rise. The courts are being tested to determine the monetary value of inappropriately collected, shared or stored customer information.4 TIME IS MONEY Cyber attacks can get costly if not resolved quickly. Results show a positive relationship between the time to contain an attack and organizational cost. 1 “DEAR VALUED CUSTOMER…” As of February 2012, forty-six US States have enacted statutes requiring notification and responses if certain criteria are met in a data breach held or maintained by a private or public entity. 3 46 States Require Notification Data Breach Legal costs are the largest portion of claims paid Average cost of defense – $582K Average cost of settlement – $2.1 million Information theft and business disruption represent the highest external costs Information theft – 44% Disruption to business or lost productivity – 30% Cyber crime costs small organizations more – they incur a significantly higher per capita cost than larger organizations1 Is a Growing Threat to Emergency Service Organizations EMERGENCY ALERT www.VFIS.com CREATED BY SOURCES 1 – 2012 Cost of Cyber Crime Study: Unites States, Sponsored by HP Enterprise Security, Independently Conducted by Ponemon Institute, October 2012 2 – Top Cybersecurity Trends and Risks for 2013 Identified – P&C 360 – Threat Matrix Article 12/20/12 3 – Cyber Risk: A Stealth Threat for Municipalities, 6/15/12 NYSAC, Christine Marciano, Pres Cyber Risk Managers 4 – Cyber Liability and Data Breach Insurance Claims, A Study of Actual Payouts for Covered Data Breaches, NetDiligence 10/2012 for Claims filed in 2011 & 2012 5 – Identity Theft Resource Center
