Cyber liability and public entities infographic
•
0 likes•209 views
Did you know there is a growing threat of cyber liability to public entities? Click on the infographic from Glatfelter Public Practice to learn cyber statistics, the average cost per breach and more.
Report
Share
Report
Share
Download to read offline
Recommended
Recommended
More Related Content
What's hot
What's hot (20)
Managing and insuring cyber risk - coverage of insurance policies

Managing and insuring cyber risk - coverage of insurance policies
The Unseen Enemy - Protecting the Brand, the Assets and the Customers 

The Unseen Enemy - Protecting the Brand, the Assets and the Customers
Complacency in the Face of Evolving Cybersecurity Norms is Hazardous

Complacency in the Face of Evolving Cybersecurity Norms is Hazardous
iStart feature: Protect and serve how safe is your personal data?

iStart feature: Protect and serve how safe is your personal data?
Corporate role in protecting consumers from the risk of identity theft

Corporate role in protecting consumers from the risk of identity theft
New York State Department of Financial Services Expands Its Cyber Focus to In...

New York State Department of Financial Services Expands Its Cyber Focus to In...
Cyber-Security: A Shared Responsibility -- November 2013

Cyber-Security: A Shared Responsibility -- November 2013
Similar to Cyber liability and public entities infographic
By David F. Larcker, Peter C. Reiss, and Brian Tayan
Stanford Closer Look Series, November 16, 2017
The board of directors is expected to ensure that management has identified and developed processes to mitigate risks facing the organization, including risks arising from data theft and the loss of information. Unfortunately, recent experience suggests that companies are not doing a sufficient job of securing this data. In this Closer Look, we examine they types of cyberattacks that occur and how companies respond to them.
We ask:
• What steps can the board take to prevent, monitor, and mitigate data theft?
• What data, metrics, and information should board members review to satisfy themselves that management has taken proper steps to minimize cyber risks?
• What qualifications should a board member have in order to constructively contribute to boardroom discussions on cybersecurity?
• How difficult is it to find board candidates with these skills?
Critical Update Needed: Cybersecurity Expertise in the Boardroom

Critical Update Needed: Cybersecurity Expertise in the BoardroomStanford GSB Corporate Governance Research Initiative
Similar to Cyber liability and public entities infographic (20)
Cyber liability and the growing threat to emergency services

Cyber liability and the growing threat to emergency services
Advanced PII / PI data discovery and data protection

Advanced PII / PI data discovery and data protection
American Bar Association guidelines on Cyber Security standards

American Bar Association guidelines on Cyber Security standards
CBIZ Cyber Security - What Every Business Needs to Know

CBIZ Cyber Security - What Every Business Needs to Know
Network Security and Privacy Liability - Four Reasons Why You need This Cove...

Network Security and Privacy Liability - Four Reasons Why You need This Cove...
Cost of Data Breach Study in 2015 - United States - Presented by IBM and Pono...

Cost of Data Breach Study in 2015 - United States - Presented by IBM and Pono...
Critical Update Needed: Cybersecurity Expertise in the Boardroom

Critical Update Needed: Cybersecurity Expertise in the Boardroom
Eamonn O Raghallaigh Major Security Issues In E Commerce

Eamonn O Raghallaigh Major Security Issues In E Commerce
Who is the next target and how is big data related ulf mattsson

Who is the next target and how is big data related ulf mattsson
Etude PwC/CIO/CSO sur la sécurité de l'information (2014)

Etude PwC/CIO/CSO sur la sécurité de l'information (2014)
Cyber liability and public entities infographic
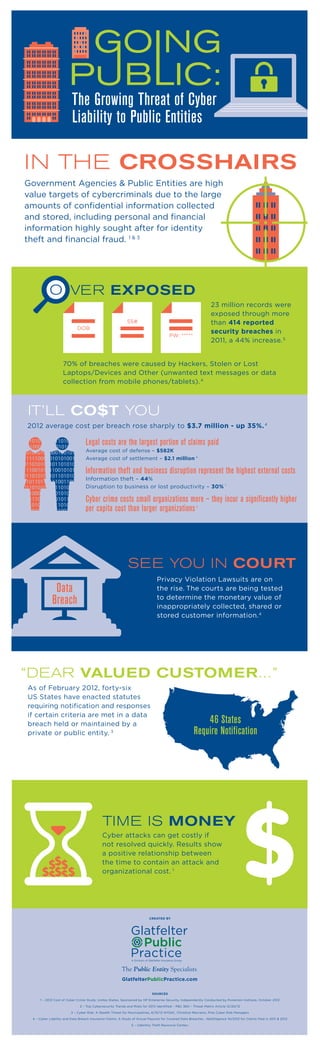
- 1. GlatfelterPublicPractice.com CREATED BY SOURCES 1 – 2012 Cost of Cyber Crime Study: Unites States, Sponsored by HP Enterprise Security, Independently Conducted by Ponemon Institute, October 2012 2 – Top Cybersecurity Trends and Risks for 2013 Identified – P&C 360 – Threat Matrix Article 12/20/12 3 – Cyber Risk: A Stealth Threat for Municipalities, 6/15/12 NYSAC, Christine Marciano, Pres Cyber Risk Managers 4 – Cyber Liability and Data Breach Insurance Claims, A Study of Actual Payouts for Covered Data Breaches , NetDiligence 10/2012 for Claims filed in 2011 & 2012 5 – (Identity Theft Resource Center) VER EXPOSED PW: ***** SS# DOB 23 million records were exposed through more than 414 reported security breaches in 2011, a 44% increase.5 70% of breaches were caused by Hackers, Stolen or Lost Laptops/Devices and Other (unwanted text messages or data collection from mobile phones/tablets).4 The Growing Threat of Cyber Liability to Public Entities IN THE CROSSHAIRS Government Agencies & Public Entities are high value targets of cybercriminals due to the large amounts of confidential information collected and stored, including personal and financial information highly sought after for identity theft and financial fraud. 1 & 3 IT’LL CO$T YOU 2012 average cost per breach rose sharply to $3.7 million - up 35%.4 4 1 SEE YOU IN COURT Privacy Violation Lawsuits are on the rise. The courts are being tested to determine the monetary value of inappropriately collected, shared or stored customer information.4 TIME IS MONEY Cyber attacks can get costly if not resolved quickly. Results show a positive relationship between the time to contain an attack and organizational cost. 1 “DEAR VALUED CUSTOMER…” As of February 2012, forty-six US States have enacted statutes requiring notification and responses if certain criteria are met in a data breach held or maintained by a private or public entity. 3 46 States Require Notification Data Breach Legal costs are the largest portion of claims paid Average cost of defense – $582K Average cost of settlement – $2.1 million Information theft and business disruption represent the highest external costs Information theft – 44% Disruption to business or lost productivity – 30% Cyber crime costs small organizations more – they incur a significantly higher per capita cost than larger organizations1
