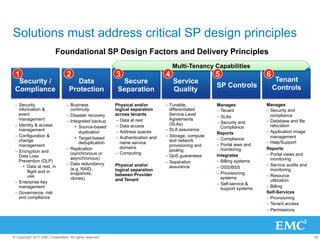
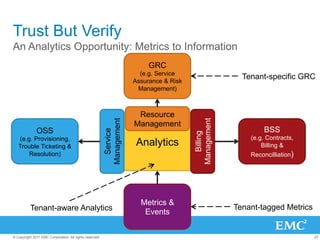
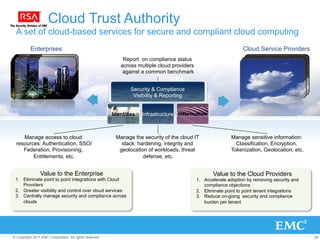
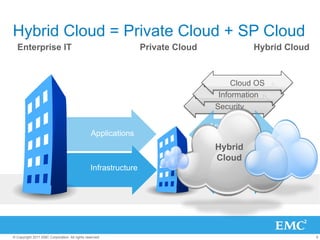
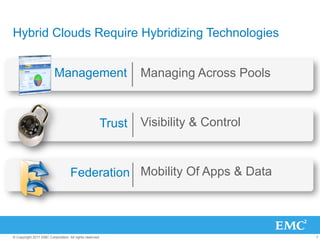
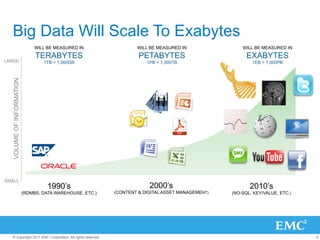
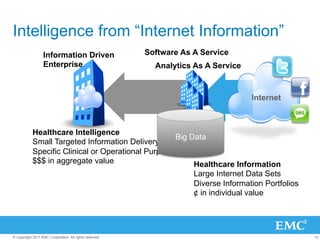
The document discusses the evolution of cloud computing, emphasizing the importance of hybrid cloud models that combine private and public services. It highlights trends in cloud adoption, the significance of big data analytics, and the necessity for improved visibility and control in a multi-tenant cloud environment. Additionally, it outlines the challenges and opportunities in managing data securely and efficiently across various cloud infrastructures.






![Disruptions in Information Marketplace
• Migration from in->out (CDN) to out->in (CIN) strategies
– Peer orientation and smart distribution improve accessibility
• Indexing to Search
– Instead of pre-classified and indexed sets, emergence of
multi-modal searchable strategies
• Enterprise Protocols to Internet Protocols
– RESTful approaches, asynchronous delivery & subscribe-able
models
– XA transactions -> eventual consistency models
• Information Structures not a priori assumed.
– Hadoop [Map Reduce] + SQL (not either/or)
© Copyright 2011 EMC Corporation. All rights reserved. 18](https://image.slidesharecdn.com/cto-07final-120217021121-phpapp02/85/PRIVATE-HYBRID-AND-PUBLIC-CLOUDS-EMCWorld-2011-18-320.jpg)



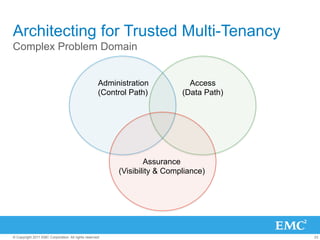
![Tenets of Trusted Multi-Tenancy (TMT)
• Make all customer-visible units of resource logical not physical
– Known MT properties/capabilities on any layer directly exposed to
customers
• Put those logical objects into containers [nested] with recursive
delegated administration capabilities @ the container layer
– Separates the implementation of a resource from its contract
– Provides a common point of mediation and aggregation
– Hierarchical (Layered) relationships must be supported on both the data
path and the control path
• Implement out-of-band monitoring of management activity that
verifies actual state of system remains in compliance
throughout any management / state changes
– Out-of-band monitoring must be done at the container boundary for the
container to support multi-tenancy
– Multi-tenant correlation (actual vs. expected) becomes critical to GRC
© Copyright 2011 EMC Corporation. All rights reserved. 24](https://image.slidesharecdn.com/cto-07final-120217021121-phpapp02/85/PRIVATE-HYBRID-AND-PUBLIC-CLOUDS-EMCWorld-2011-24-320.jpg)