Embed presentation
Downloaded 61 times




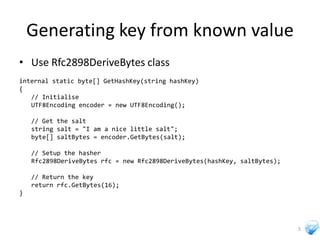
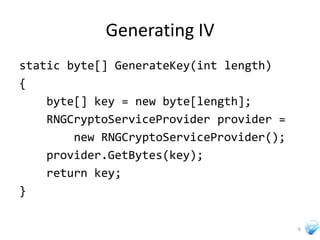
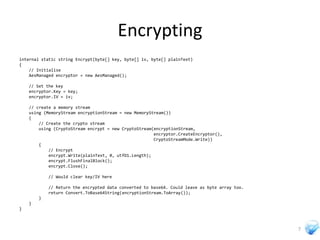


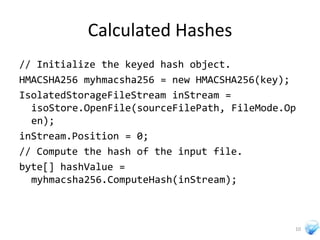

The document discusses cryptography techniques that can be used in Silverlight applications, including encrypting data stored in isolated storage using AES encryption with a key derived from a password. It also describes how to generate initialization vectors, encrypt and decrypt data, and calculate hashes of data using SHA algorithms or MD5.









