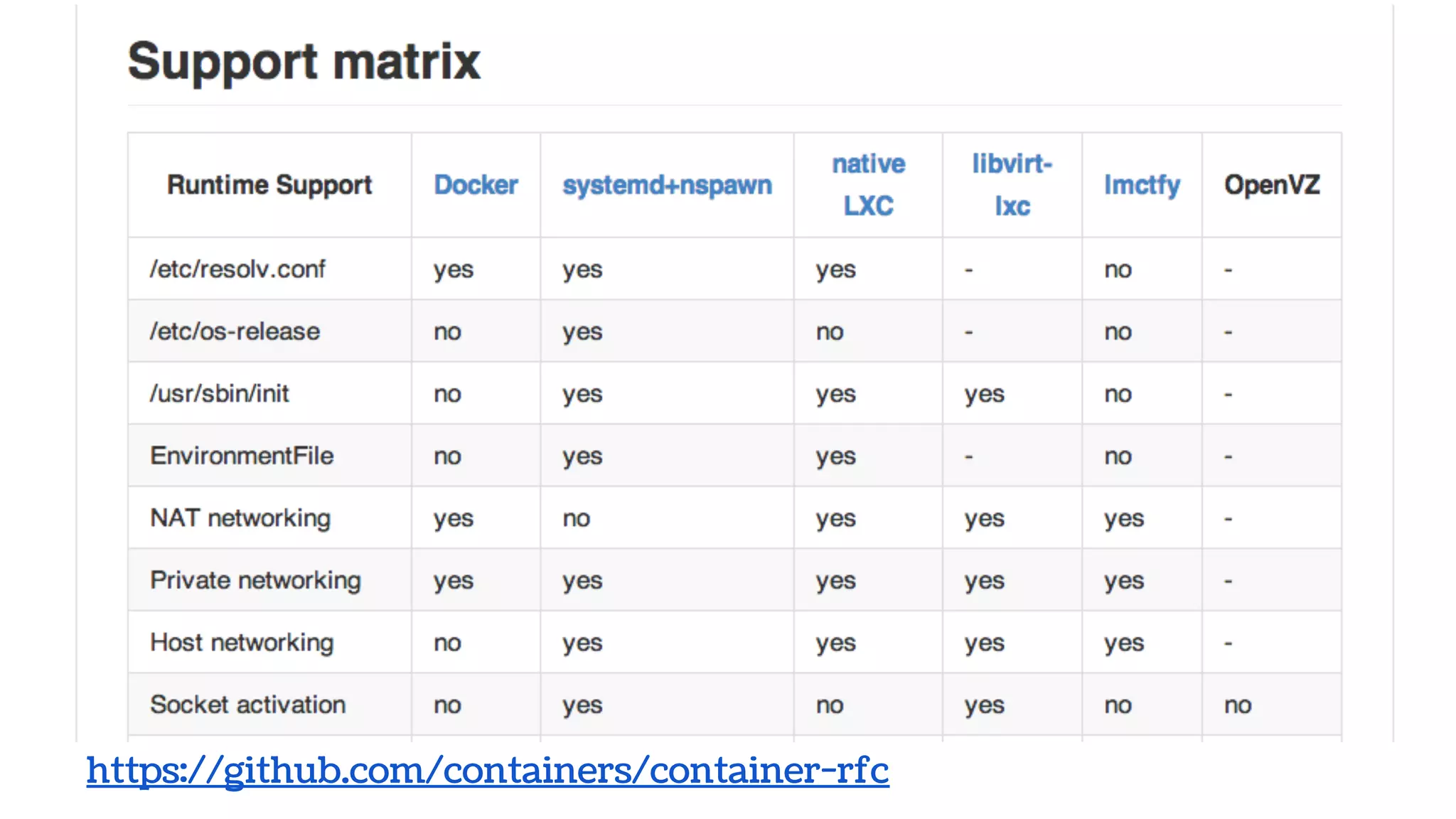
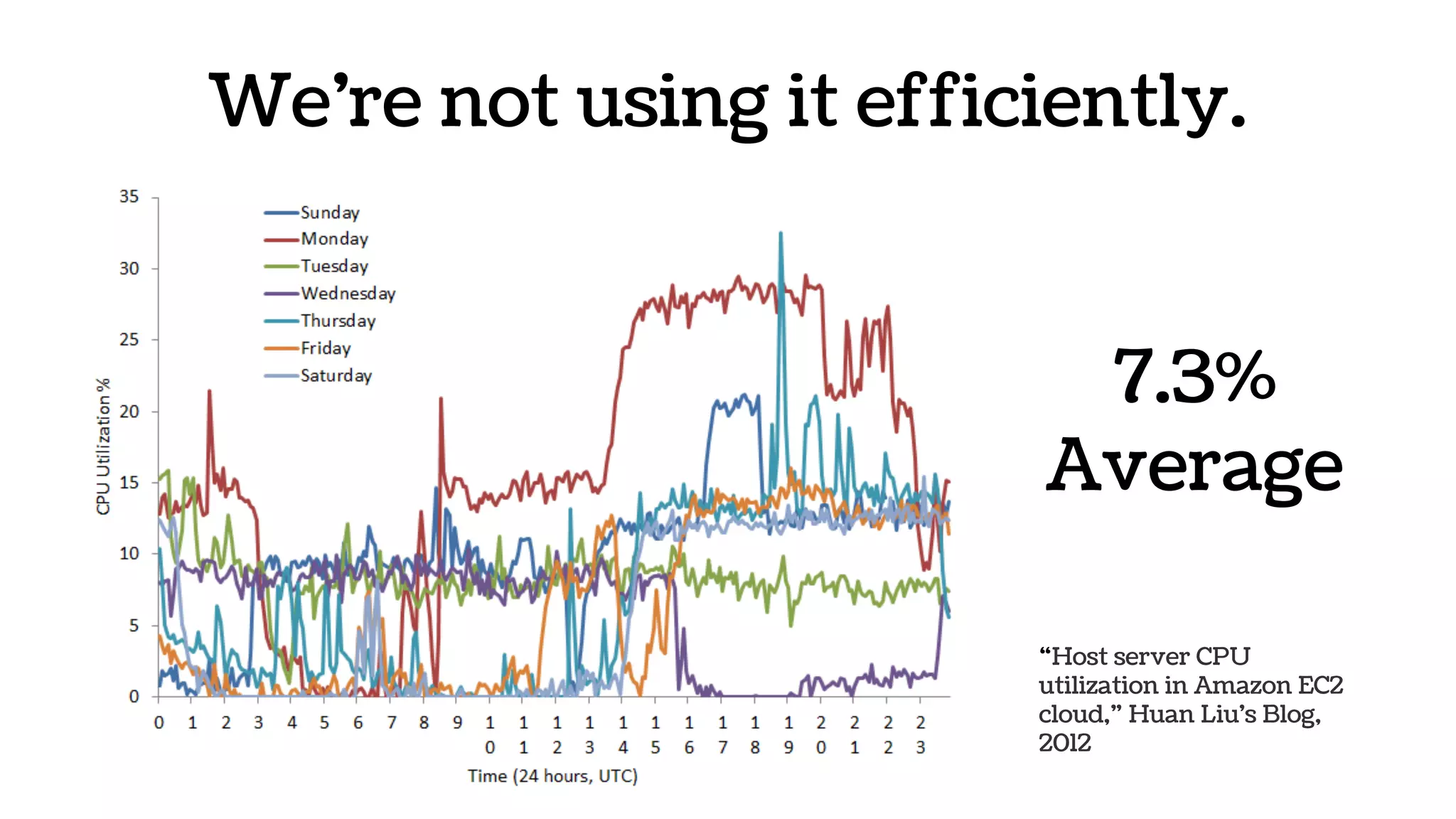
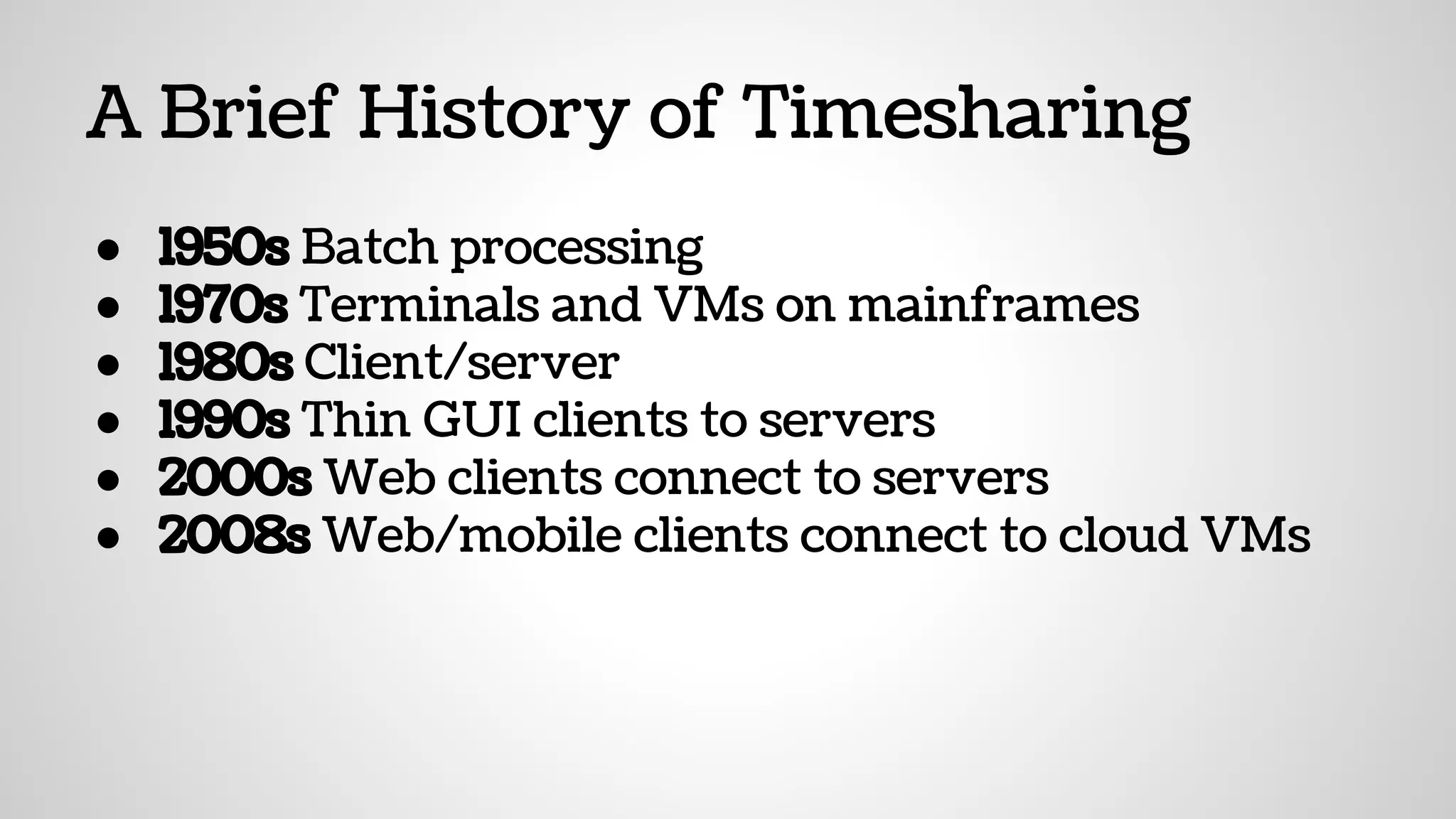
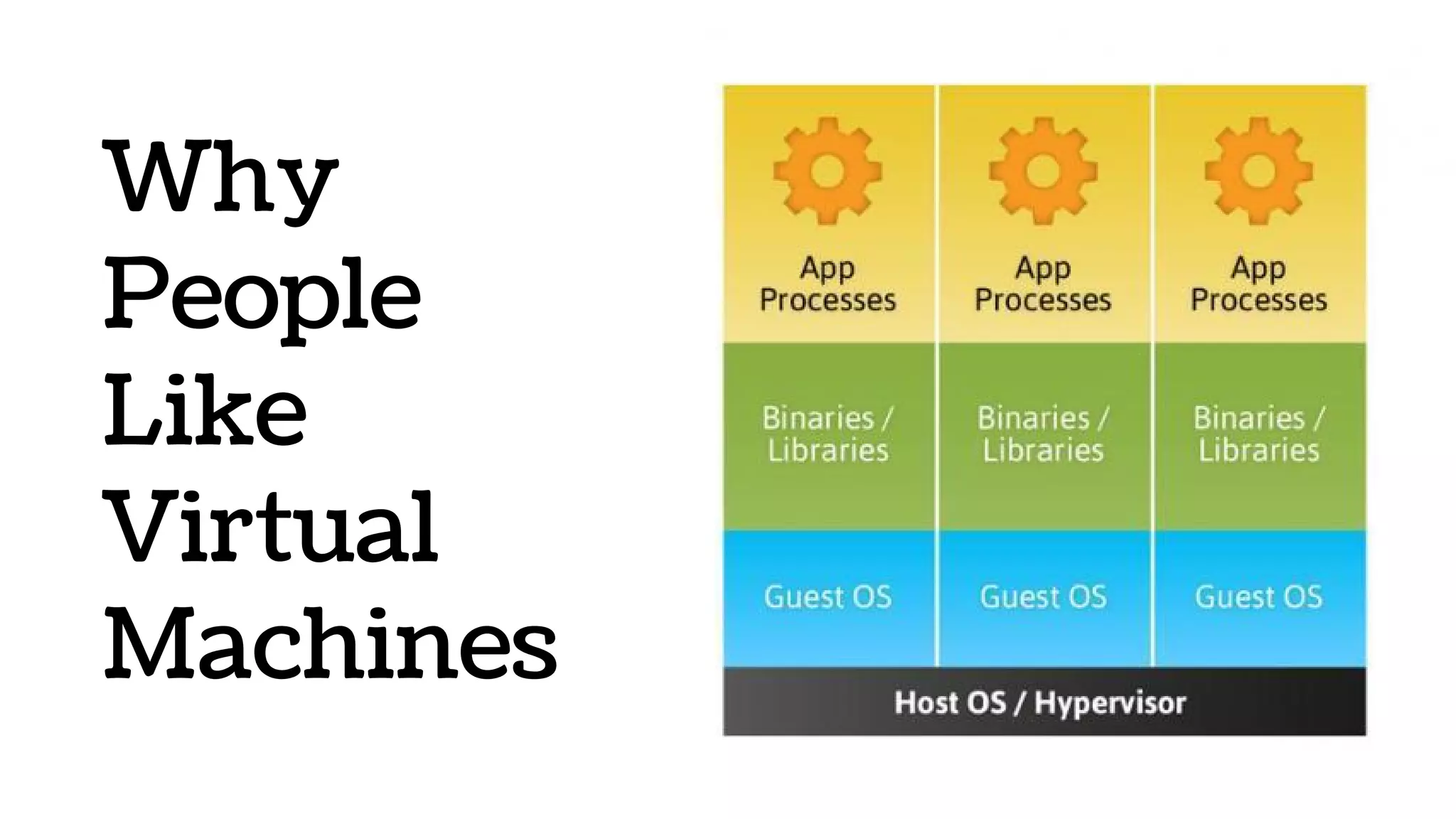
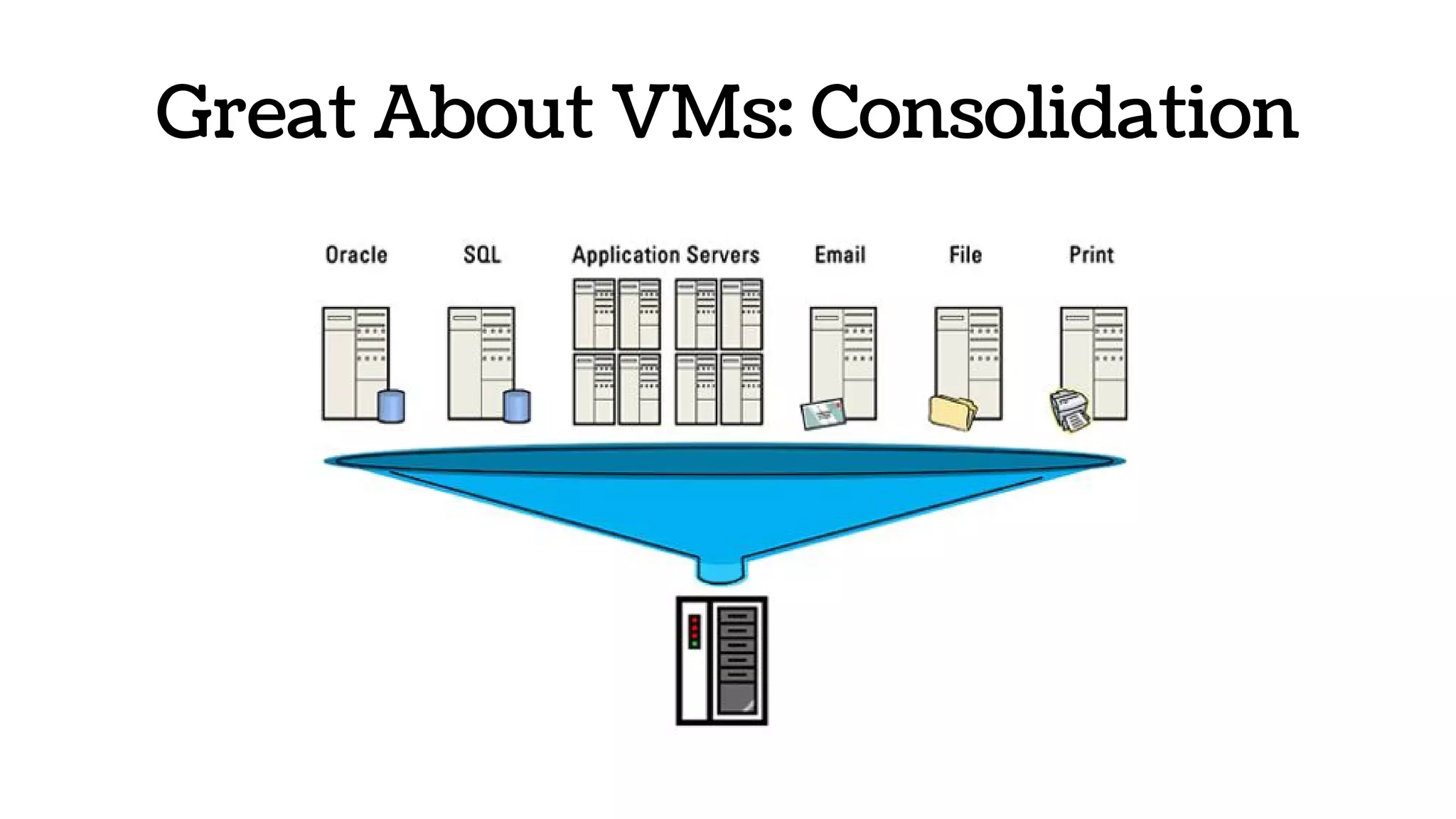
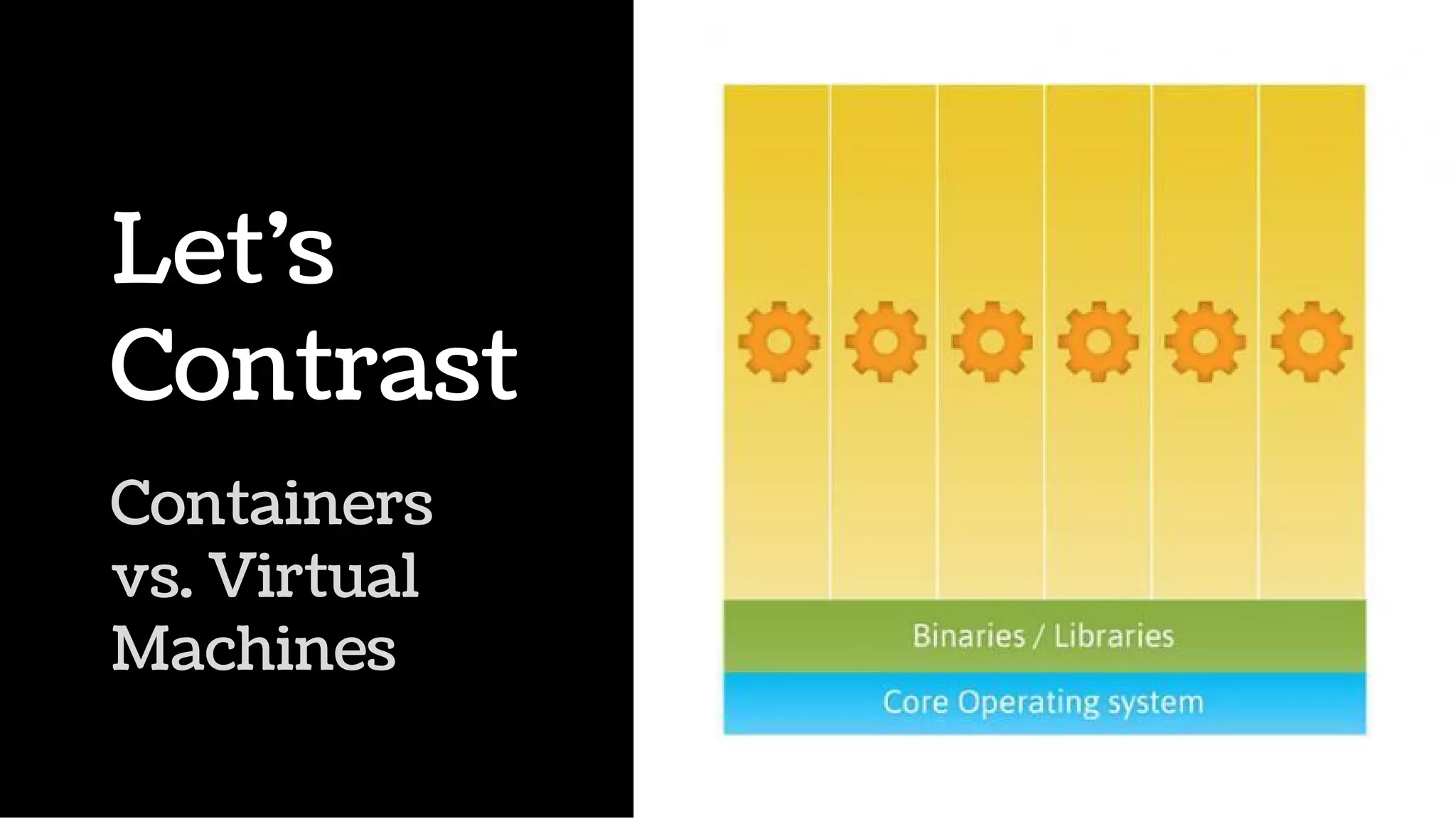
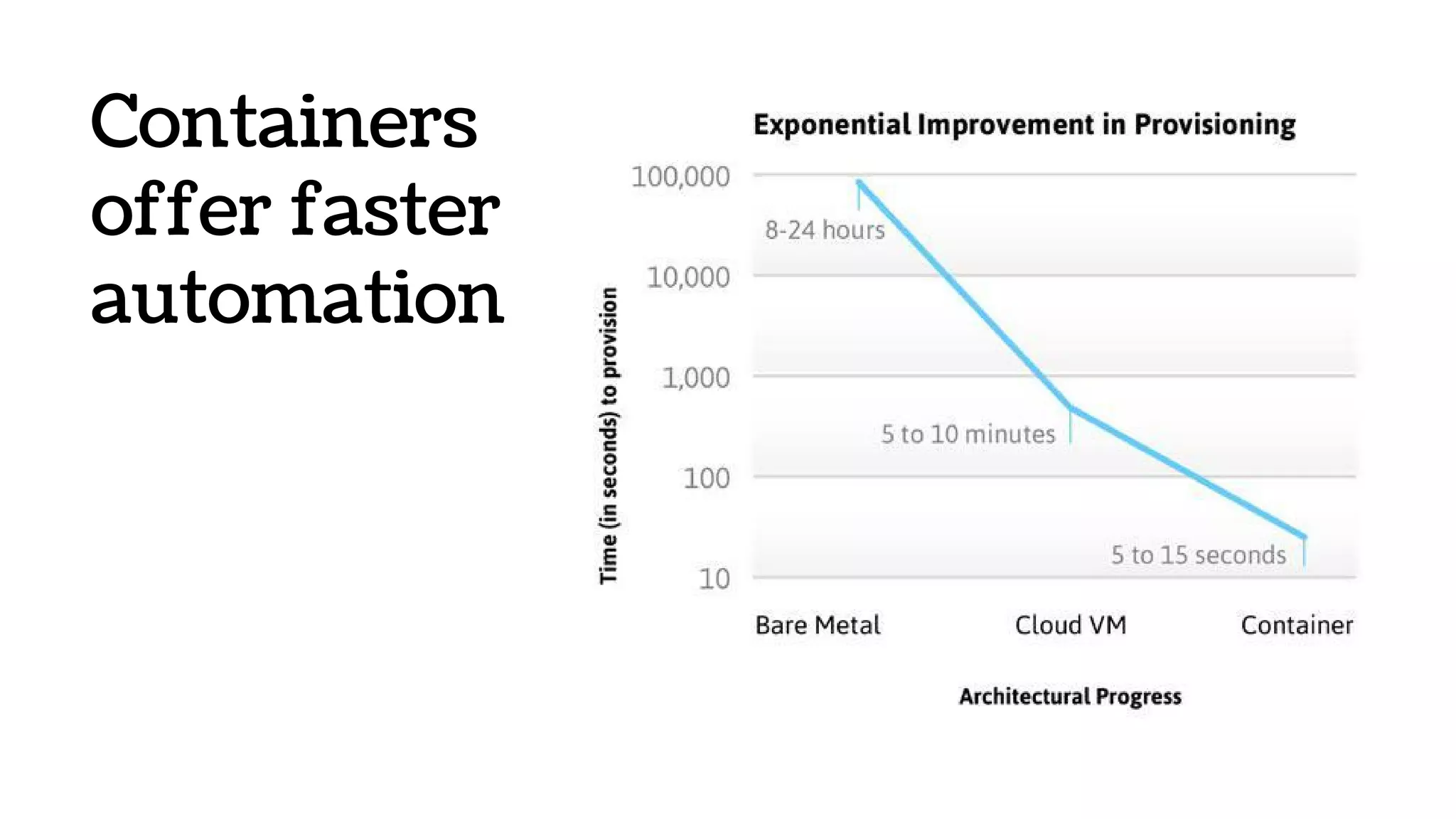
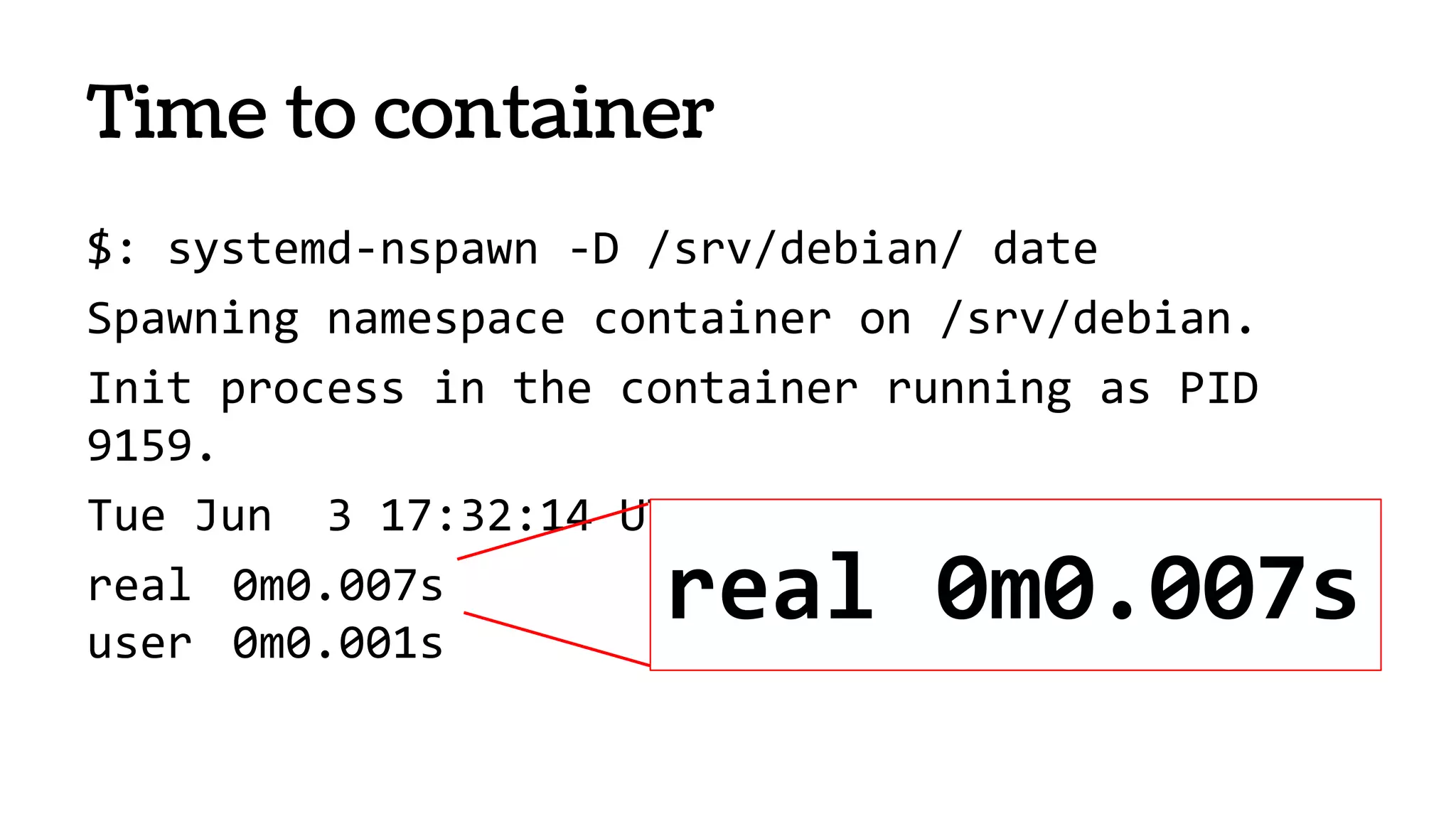
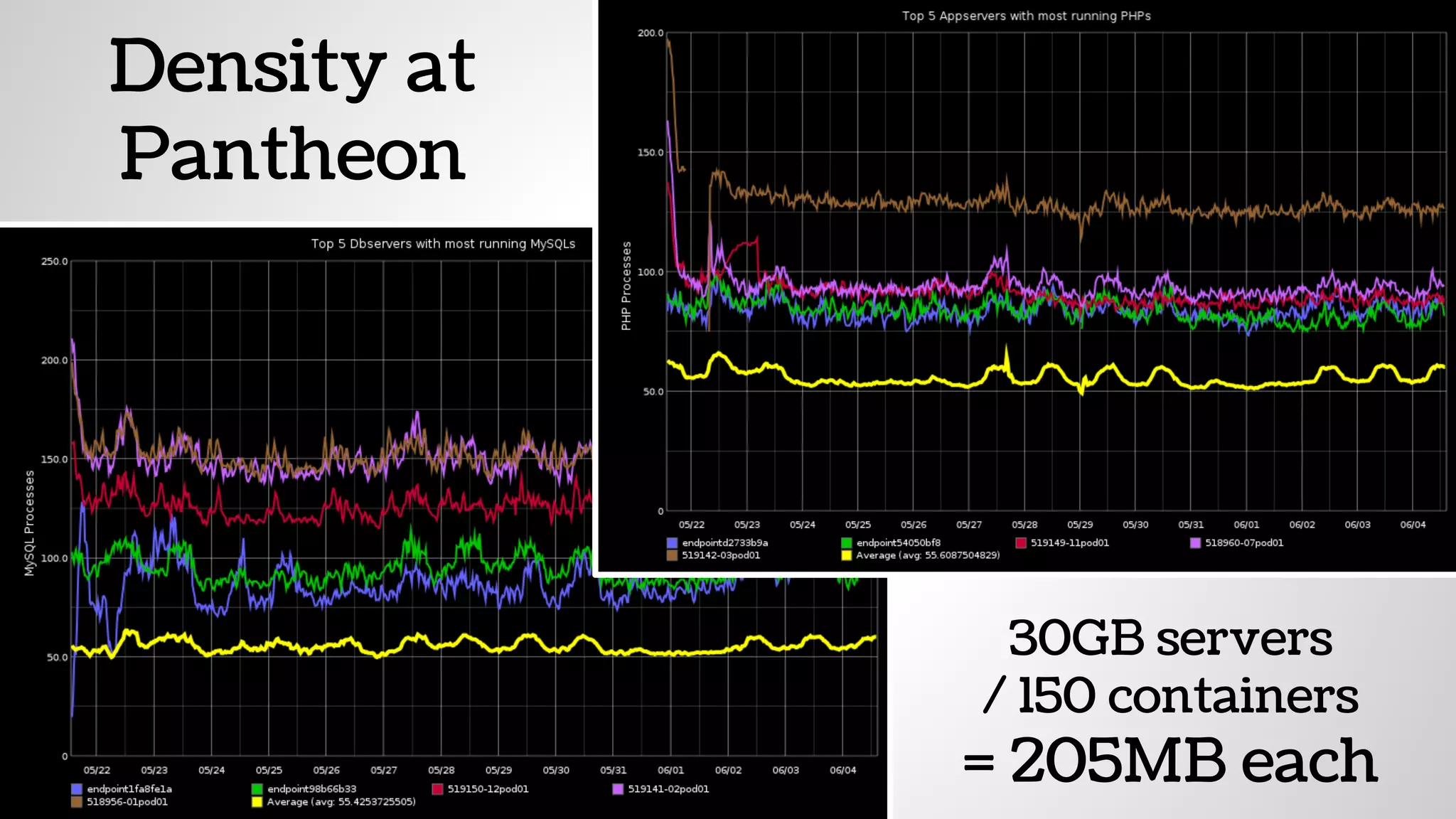
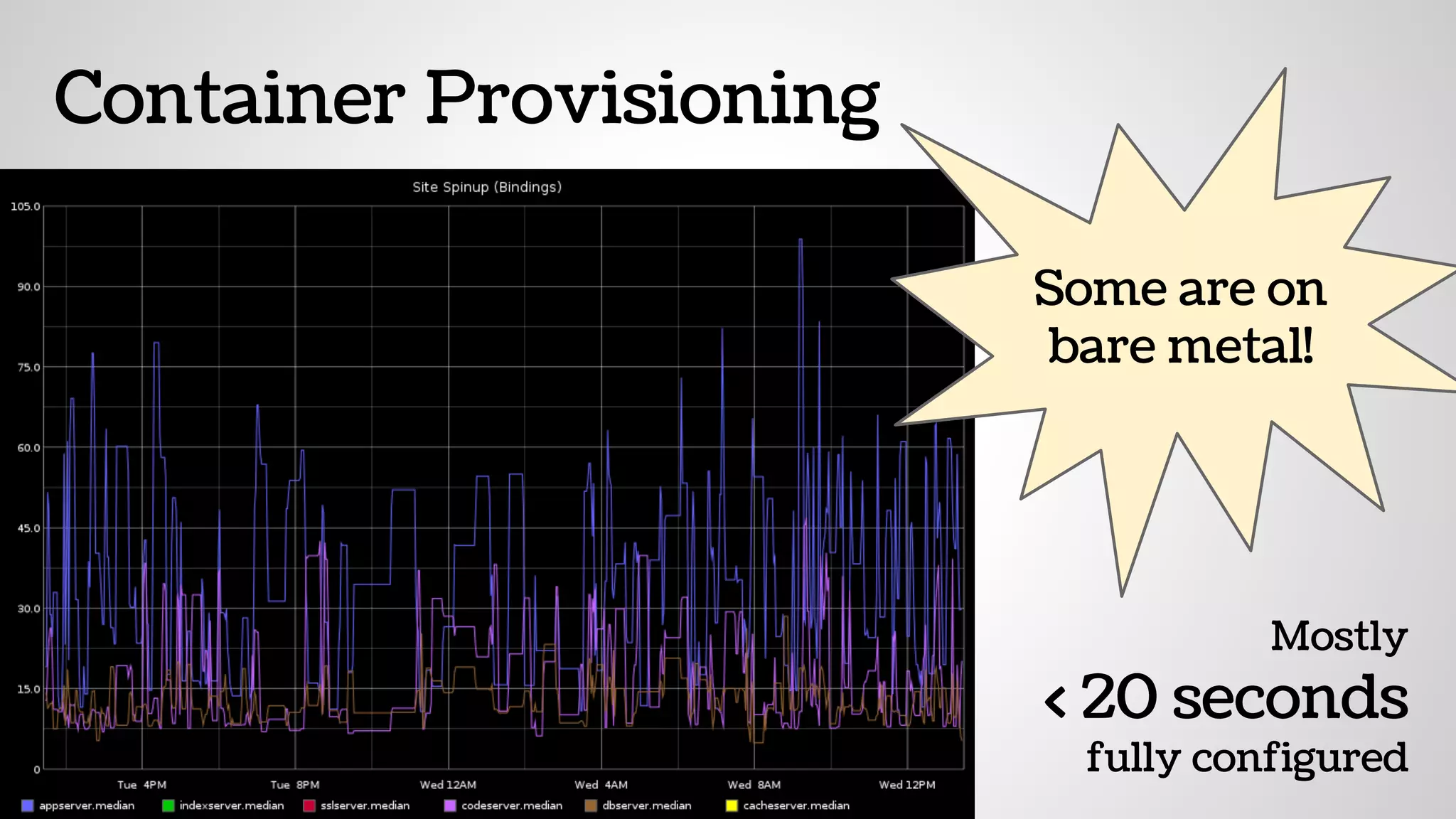
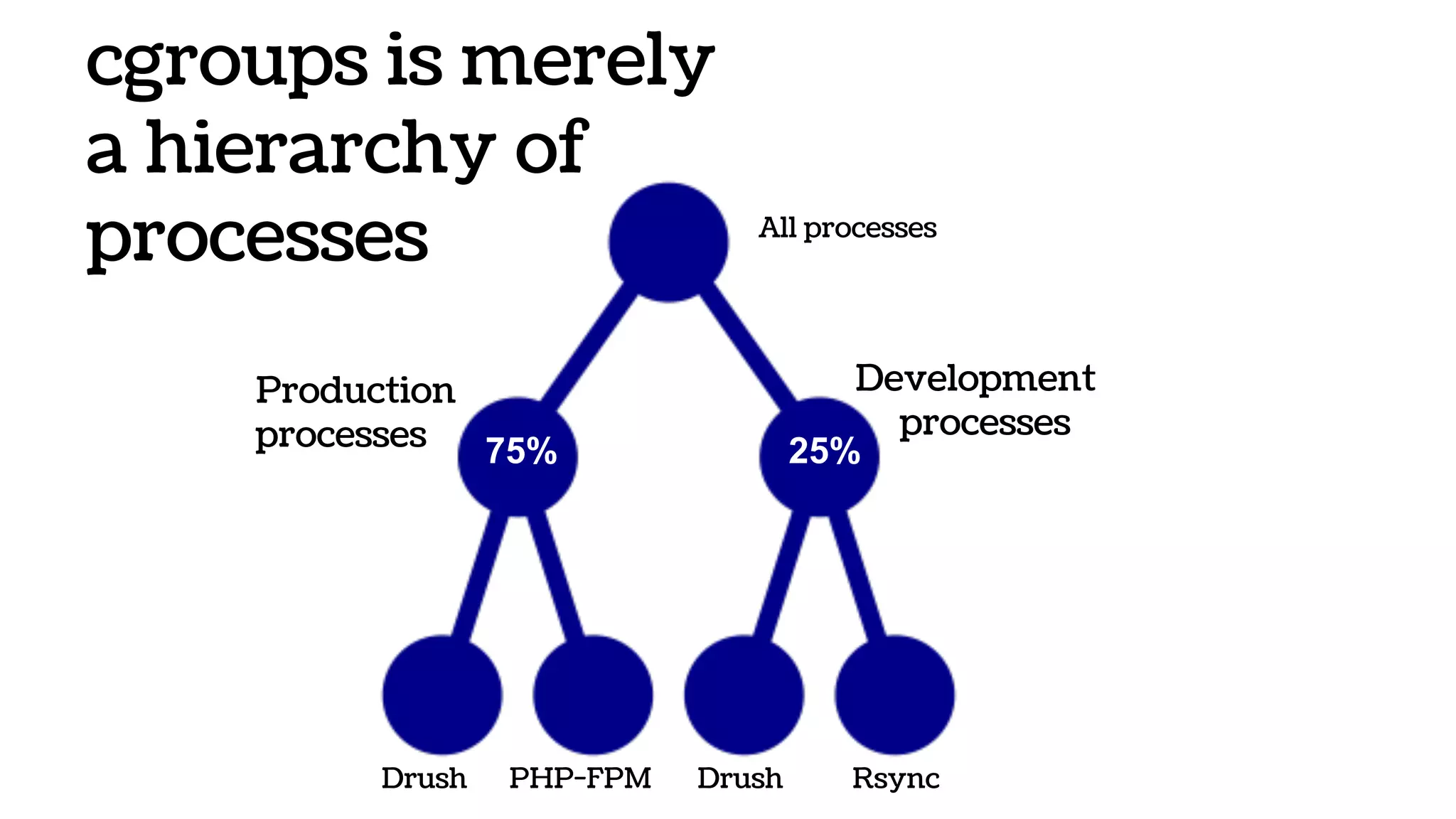
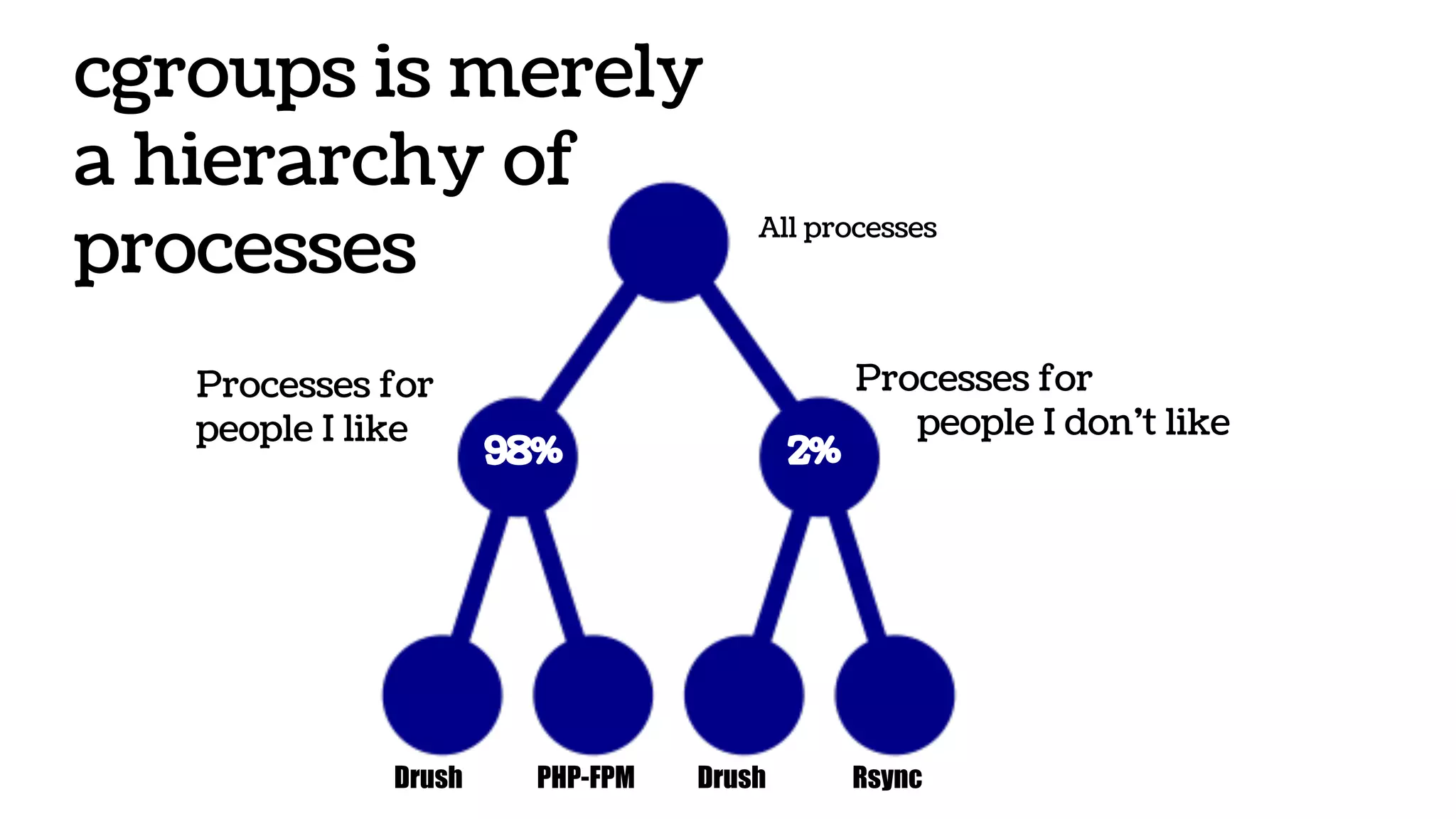
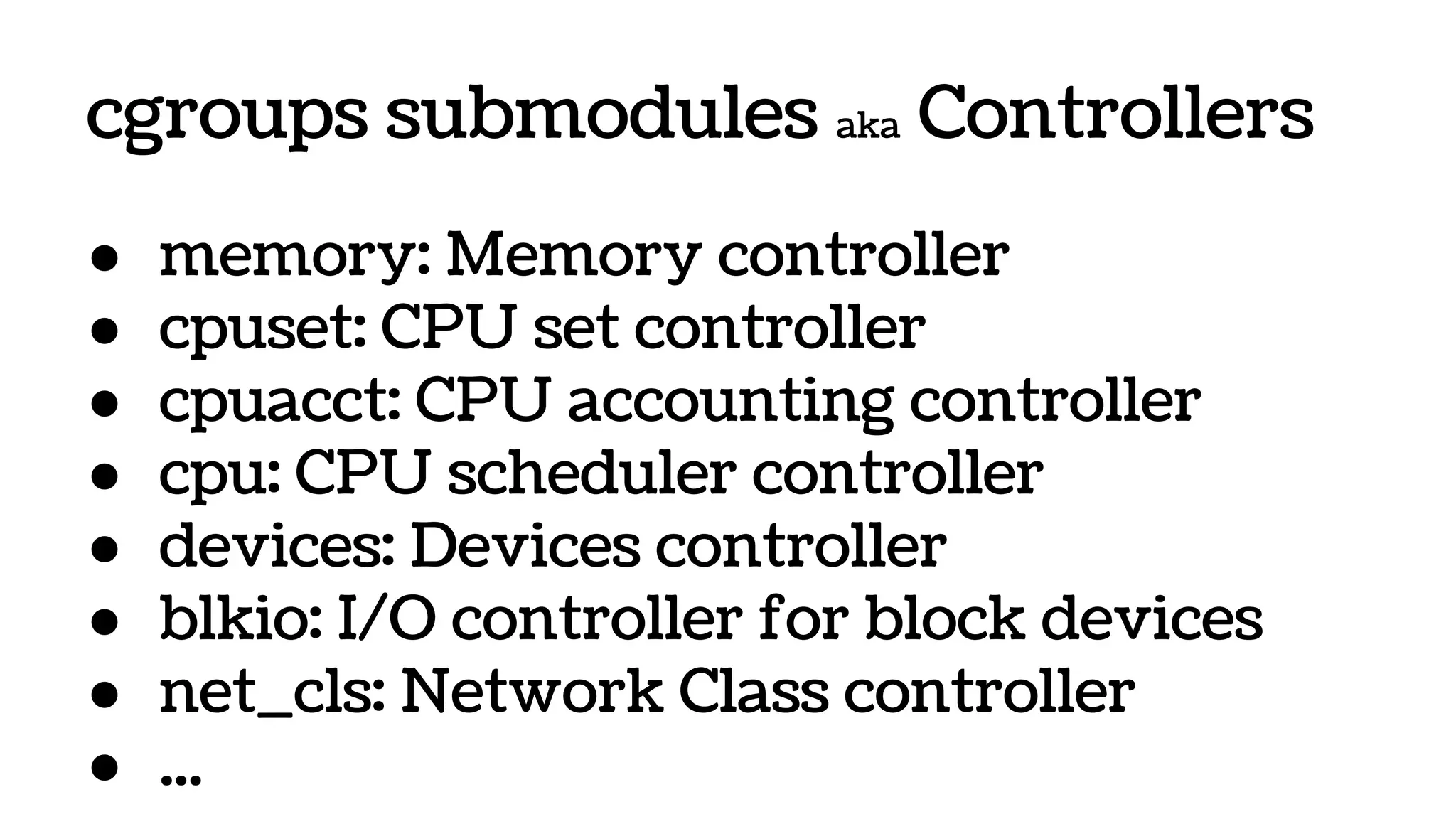
The document discusses the evolution and advantages of virtualization and containerization in computing, highlighting the history and efficiency of virtual machines (VMs) and containers. It explains how containers, which require fewer resources than traditional VMs and eliminate the need for a full operating system, offer improved portability, automation, and performance. The piece also delves into technical aspects like cgroups and namespaces in Linux, comparing various container frameworks and their applications.

















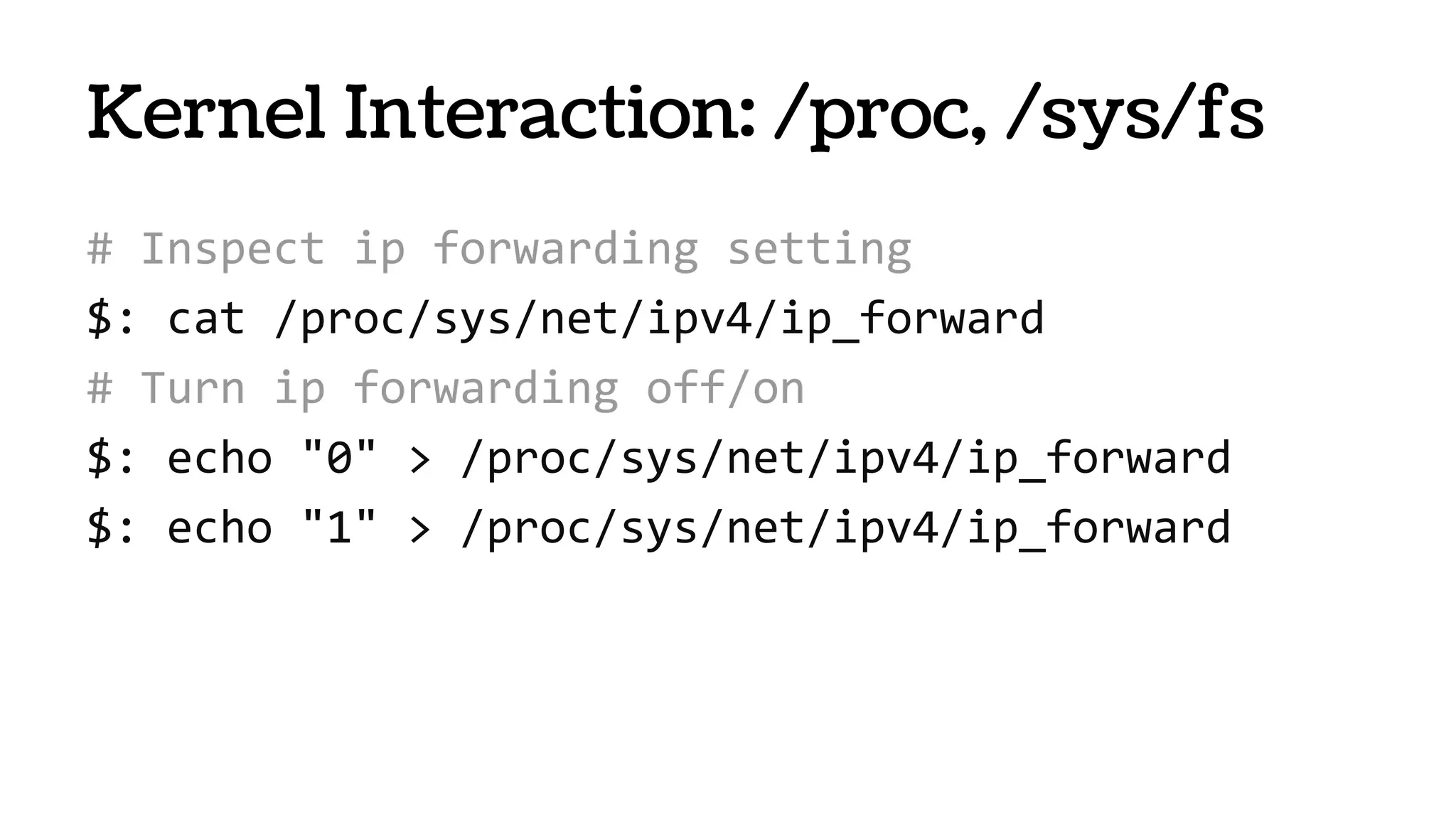
![# Examine file descriptors used by nginx..
$: ls -l /proc/$NGINX_PID/fd/
lrwx------ 1 root Jun 3 13:48 0 -> /dev/null
lrwx------ 1 root Jun 3 13:48 10 -> socket:[64376]
l-wx------ 1 root Jun 3 13:48 2 -> /var/log/nginx-access.log
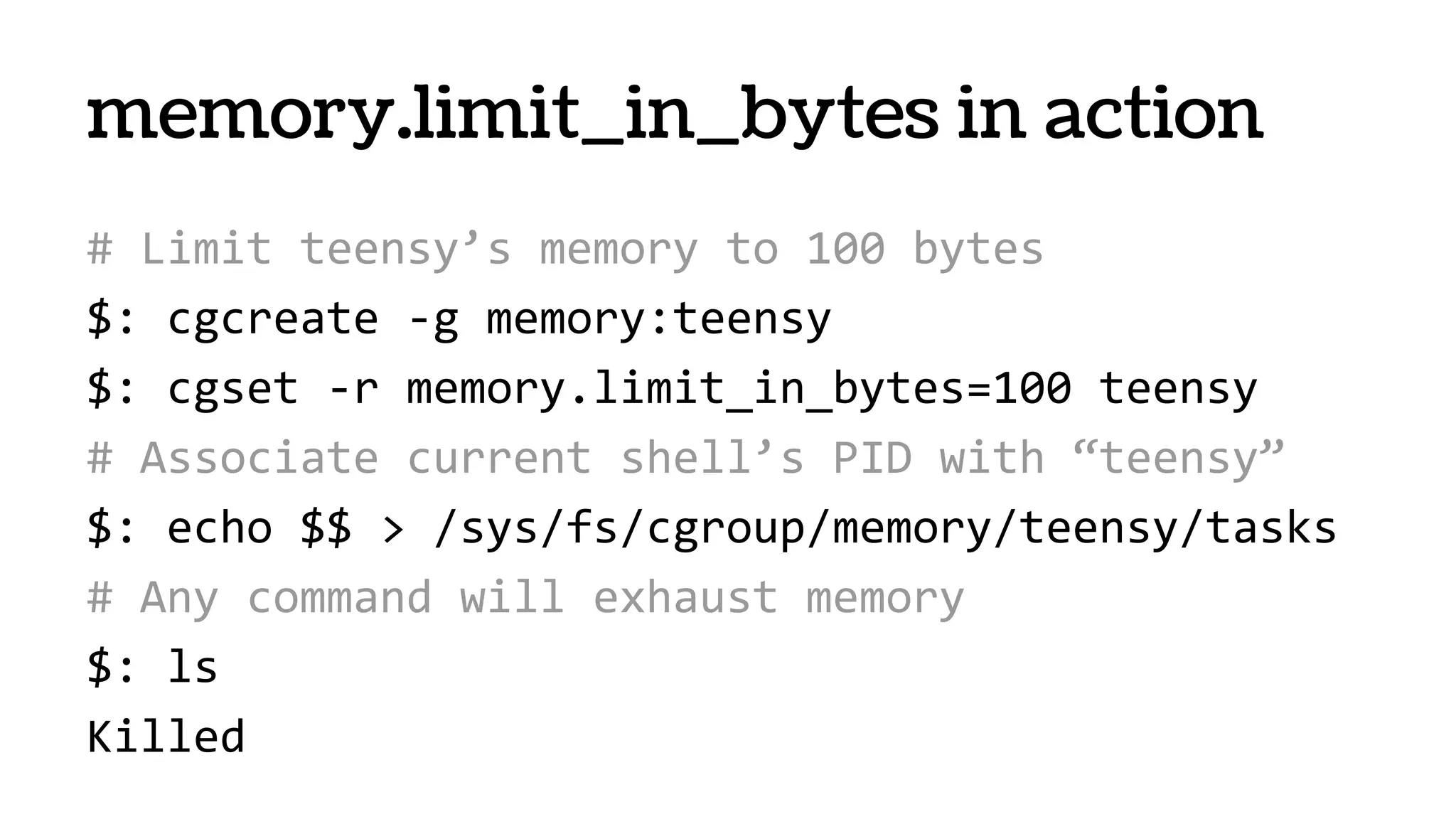
# Nuke logs
$: rm -rf /var/log/nginx-access.log
# Read log (even after you rm -rf’d it!)
$: tail /proc/$NGINX_PID/fd/2
62.211.78.166 - - [05/May/2014:10:00:54 +0000] "GET /vtiger.php
Kernel Interaction: /proc, /sys/fs](https://image.slidesharecdn.com/nbmdigncrye1hf66yvbf-140609130756-phpapp02/75/Containers-VMs-36-2048.jpg)
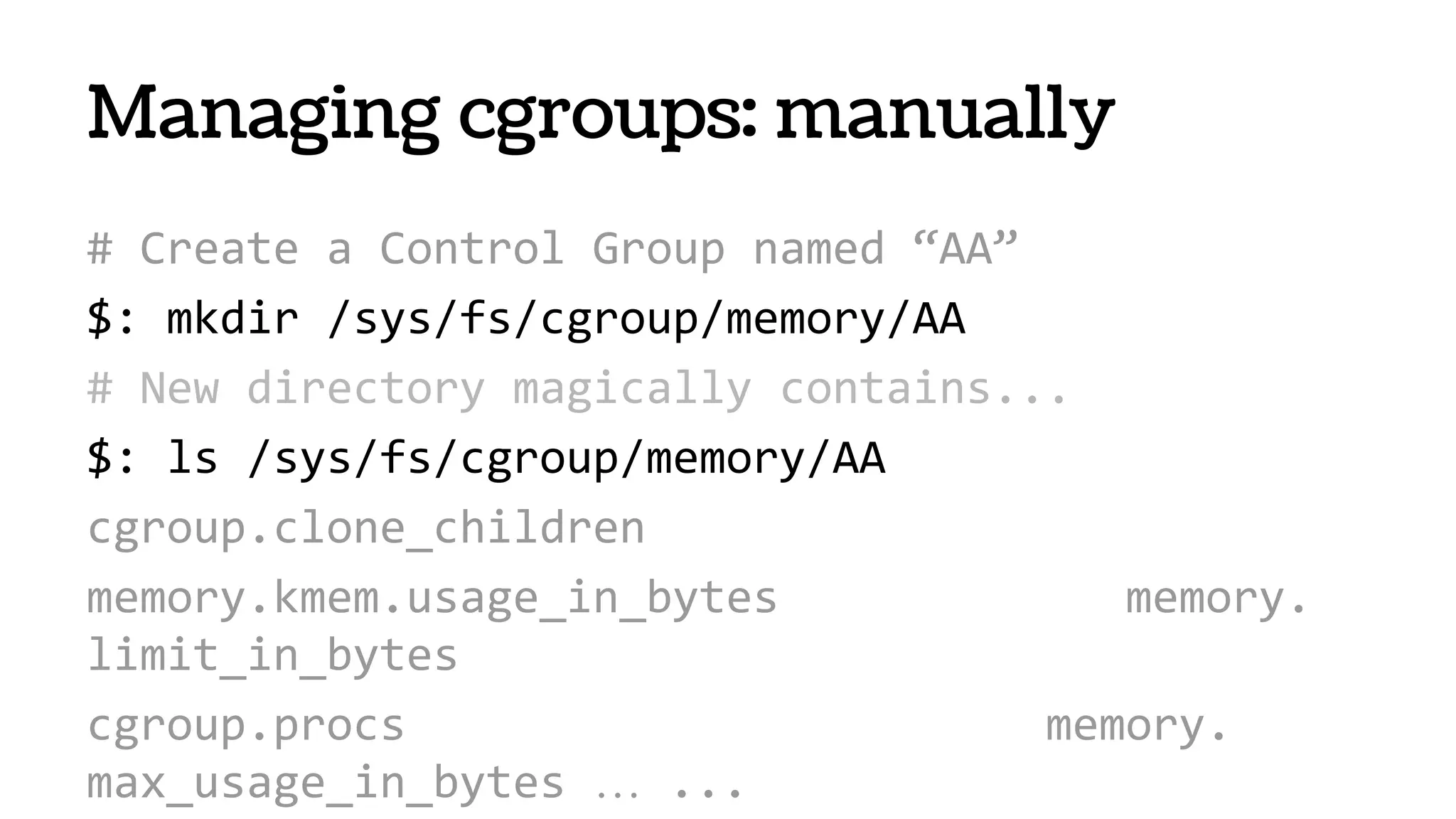
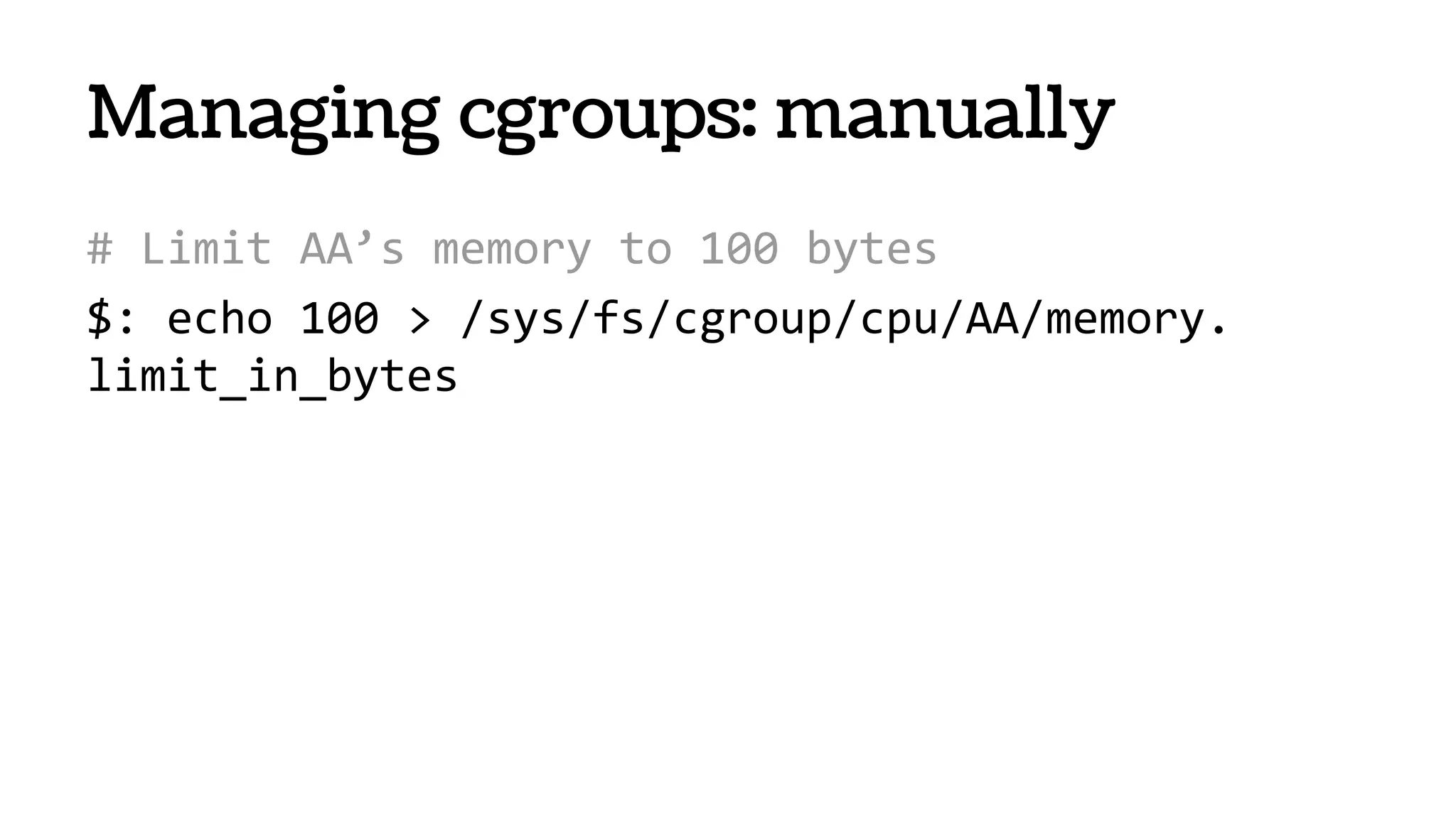
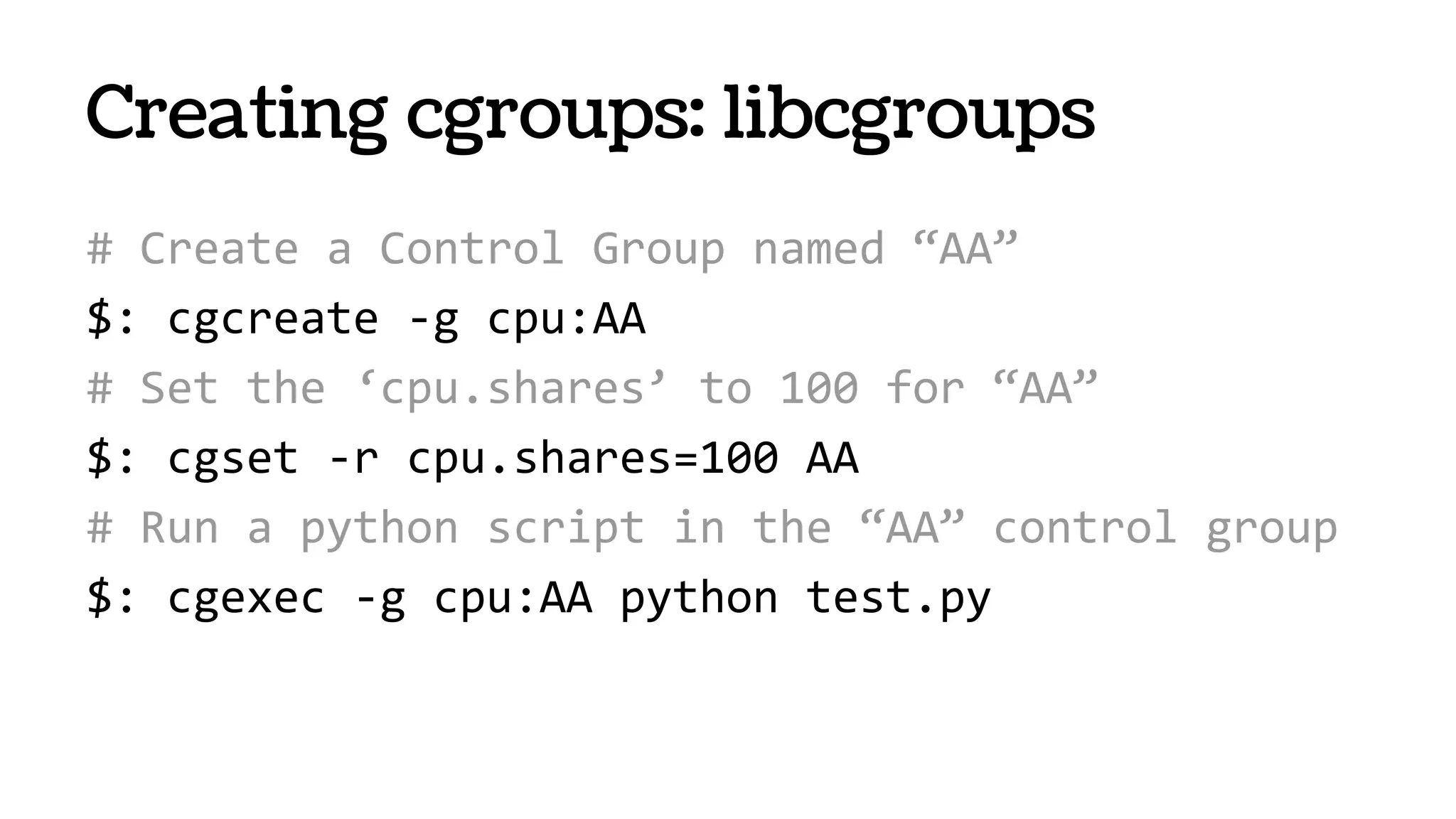
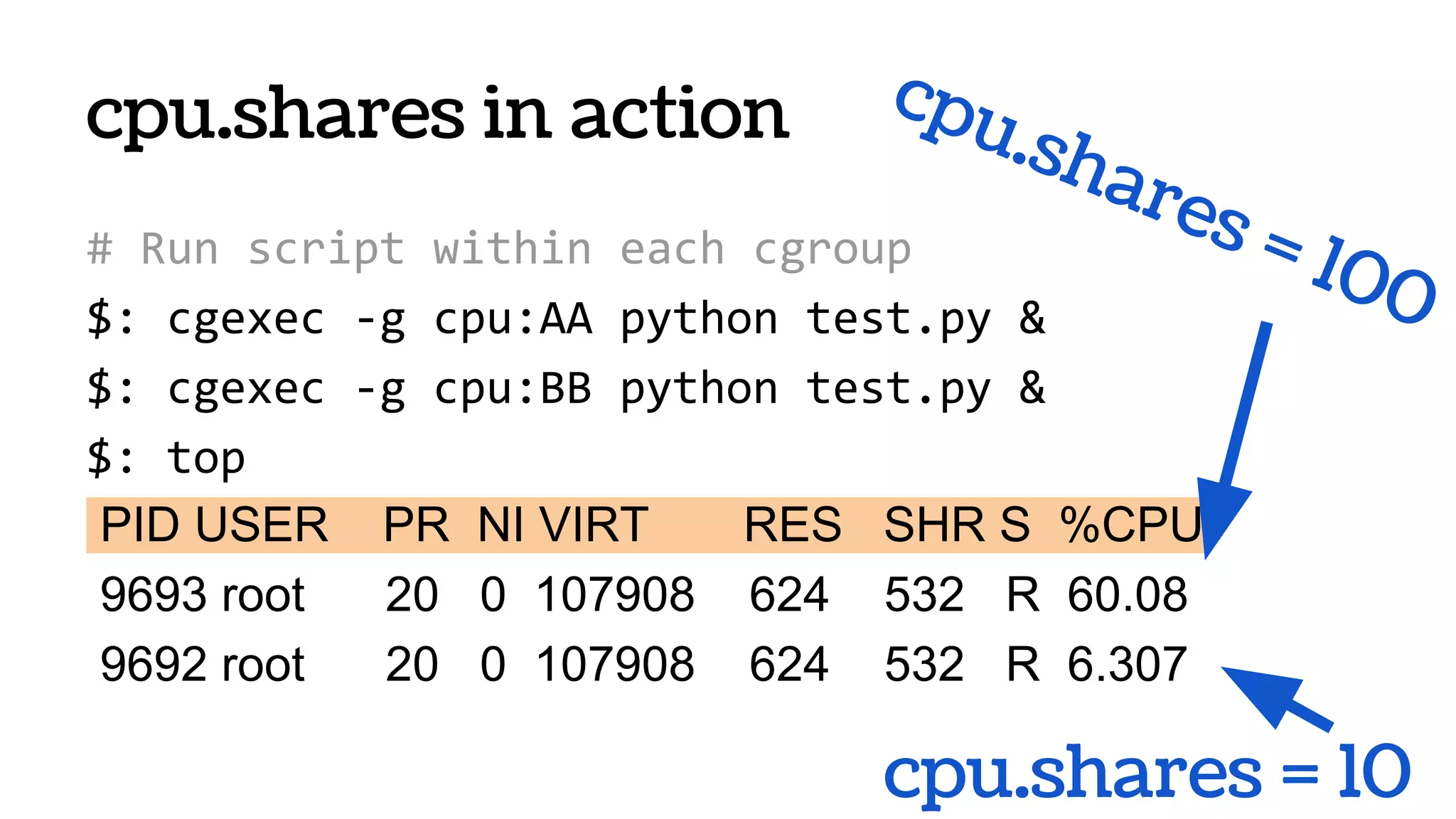




![systemd-nspawn
● From systemd project “PID EINS!”
● Will ship with all Fedora, RHEL, Ubuntu1
[1] It will ship even with you on board
https://speakerdeck.com/joemiller/systemd-for-sysadmins-what-to-expect-from-your-new-service-
overlord](https://image.slidesharecdn.com/nbmdigncrye1hf66yvbf-140609130756-phpapp02/75/Containers-VMs-47-2048.jpg)

![Docker
“In its early age, the dotCloud platform used
plain LXC (Linux Containers)....The platform evolved,
bearing less and less similarity with usual Linux
Containers.”1
[1] http://blog.dotcloud.com/under-the-hood-linux-kernels-on-dotcloud-part
[2] https://prague2013.drupal.org/session/automate-drupal-deployments-linux-containers-docker-and-
vagrant](https://image.slidesharecdn.com/nbmdigncrye1hf66yvbf-140609130756-phpapp02/75/Containers-VMs-49-2048.jpg)