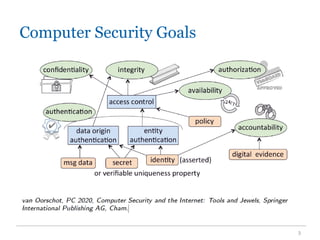
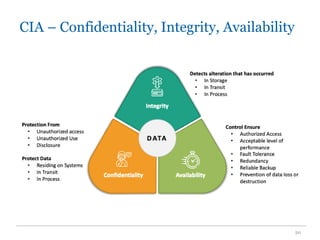
The document provides an overview of key security goals in cybersecurity, focusing on confidentiality, integrity, and availability (CIA). It emphasizes the importance of authentication, authorization, and accountability in ensuring data security and outlines various measures for maintaining these goals. Additionally, it discusses challenges and threats to security, along with the importance of training and best practices for individuals handling sensitive information.