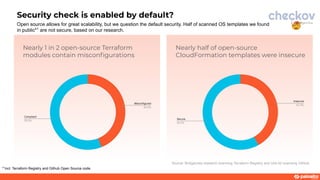
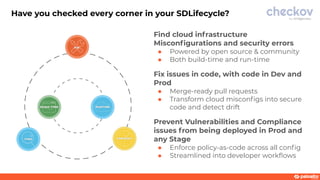
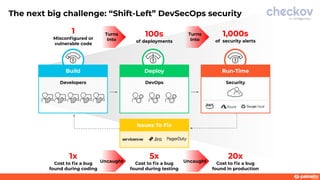
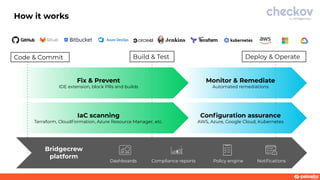
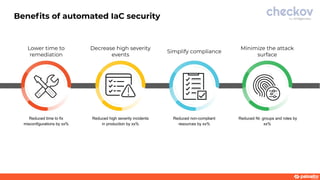
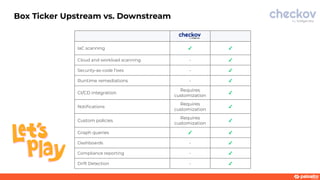
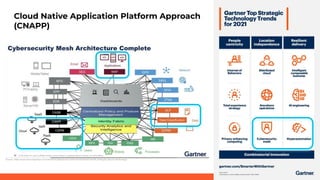
This document discusses a webinar about integrating infrastructure as code (IaC) security into the development lifecycle using Checkov. It notes that nearly half of open source Terraform and CloudFormation templates contain security issues. Checkov is introduced as an open source IaC scanning tool that supports multiple frameworks and cloud providers. The benefits of Checkov include lower remediation times, reduced security incidents, and simplifying compliance. Integrations with DevOps tools and the Cloud Native Application Platform Approach (CNAPP) are also discussed. A demo of Checkov is then shown including using it with VS Code and Azure DevOps.