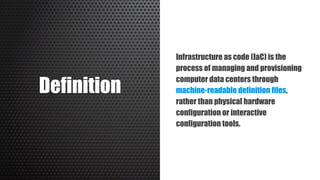
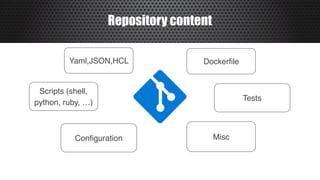
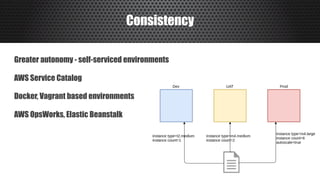
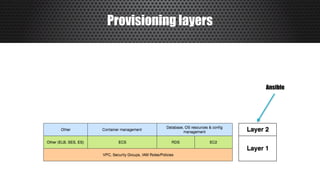
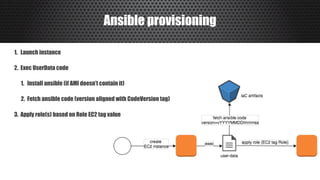
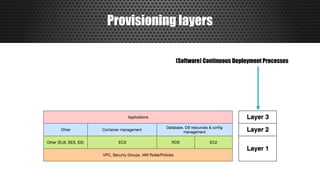
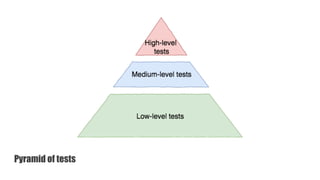
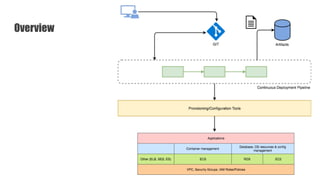
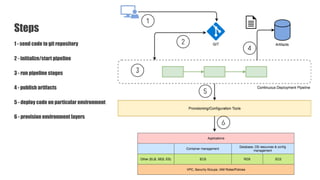
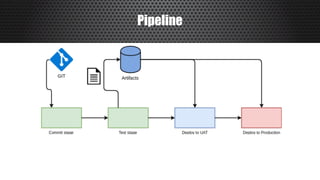
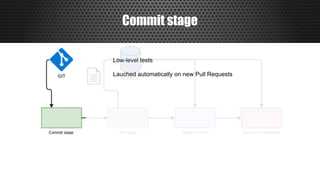
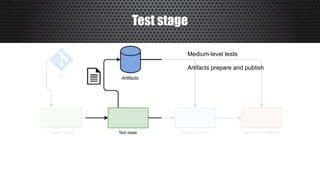
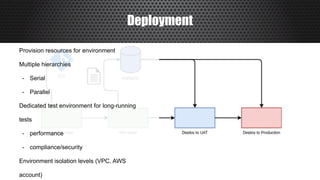
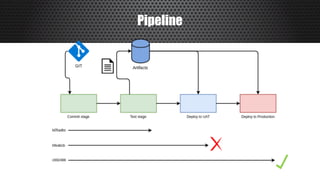
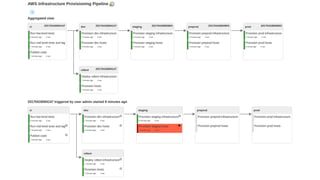
The document discusses a practical approach to Infrastructure as Code (IaC), emphasizing its definition as managing data centers via machine-readable files instead of physical configurations. Key principles include focusing on process over tools, ensuring version consistency, and continuous improvement practices, along with the importance of testing. The author provides insights into automation strategies and the necessity for configuration management in cloud environments.