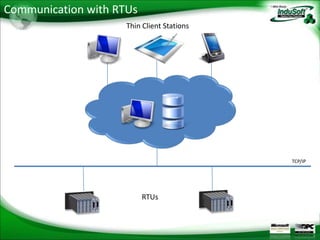
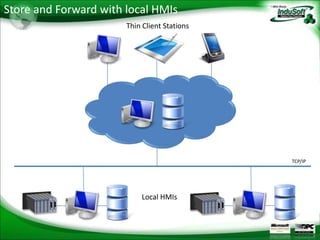
Cloud computing provides on-demand access to shared computing resources like servers, storage, databases, networking, software, analytics and more over the internet. It has 5 essential characteristics: self-service use, broad network access, resource pooling, rapid elasticity, and measured service. There are 3 main deployment models (private, public, hybrid cloud) and 3 main service models (Infrastructure as a Service, Platform as a Service, Software as a Service). Cloud computing provides economic, agility, accessibility and reliability benefits but also faces challenges around system complexity, data protection, availability and loss of control.