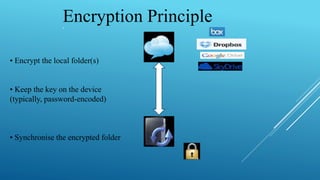
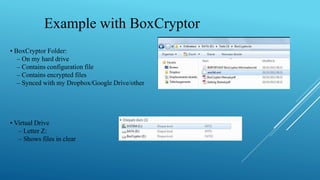
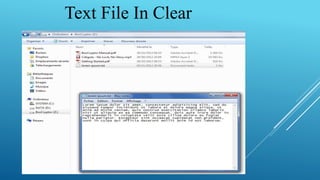
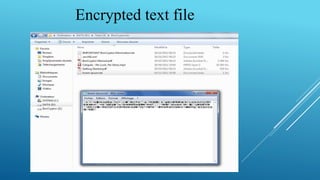
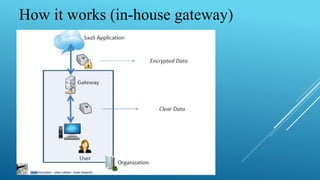
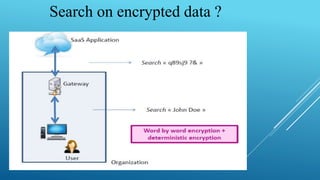
This document summarizes a seminar on encrypted cloud storage. It discusses the need for cloud encryption due to security concerns about data privacy when using cloud providers. It recommends encrypting data stored in the cloud and keeping encryption keys controlled by the organization rather than the cloud provider. It also describes how user-oriented cloud storage solutions can provide local encryption of files that are synced with cloud services in a transparent way. Finally, it discusses how cloud security gateways aim to allow confidential use of software as a service applications in the cloud through encryption while potentially impacting some cloud features.