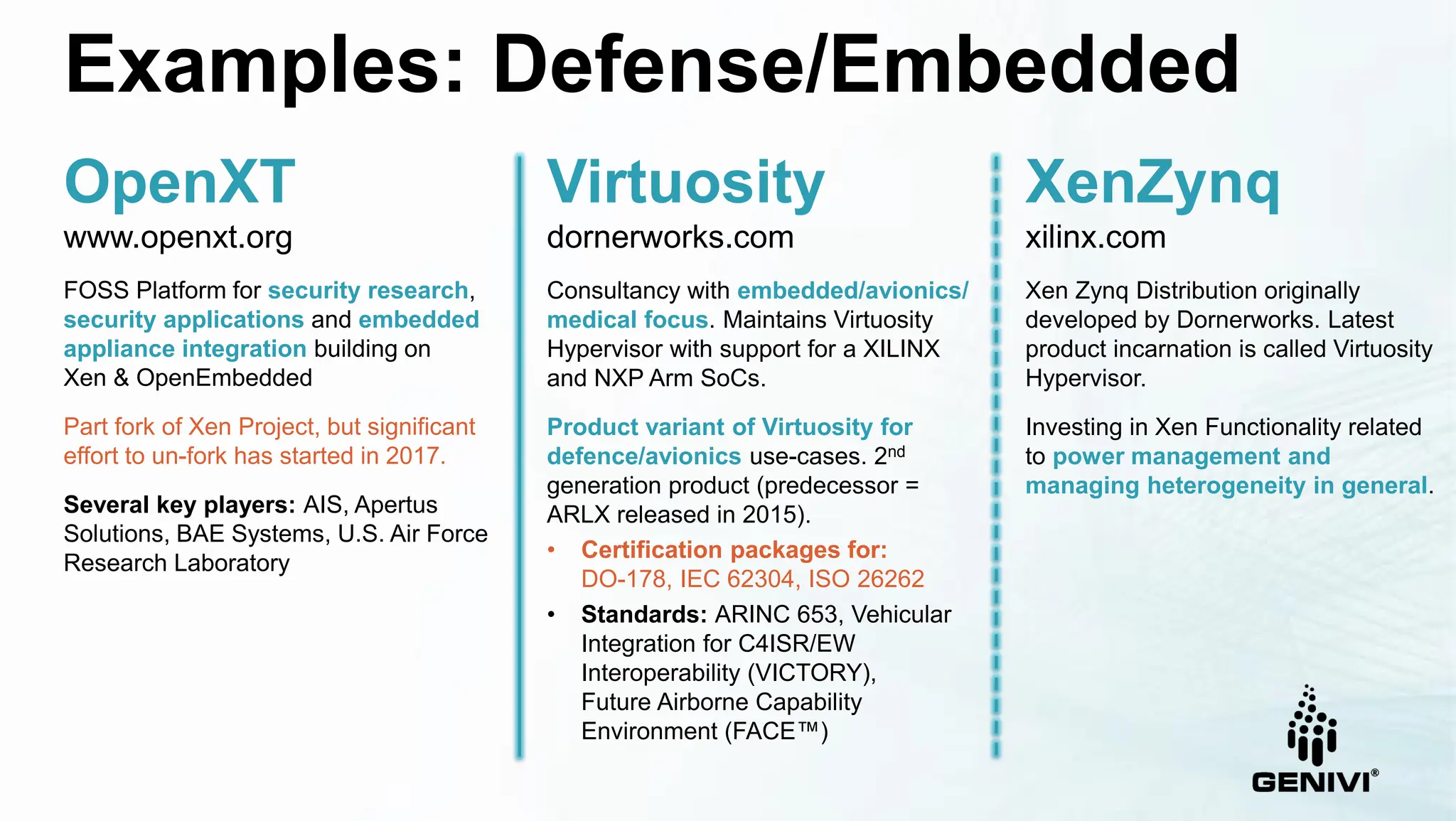
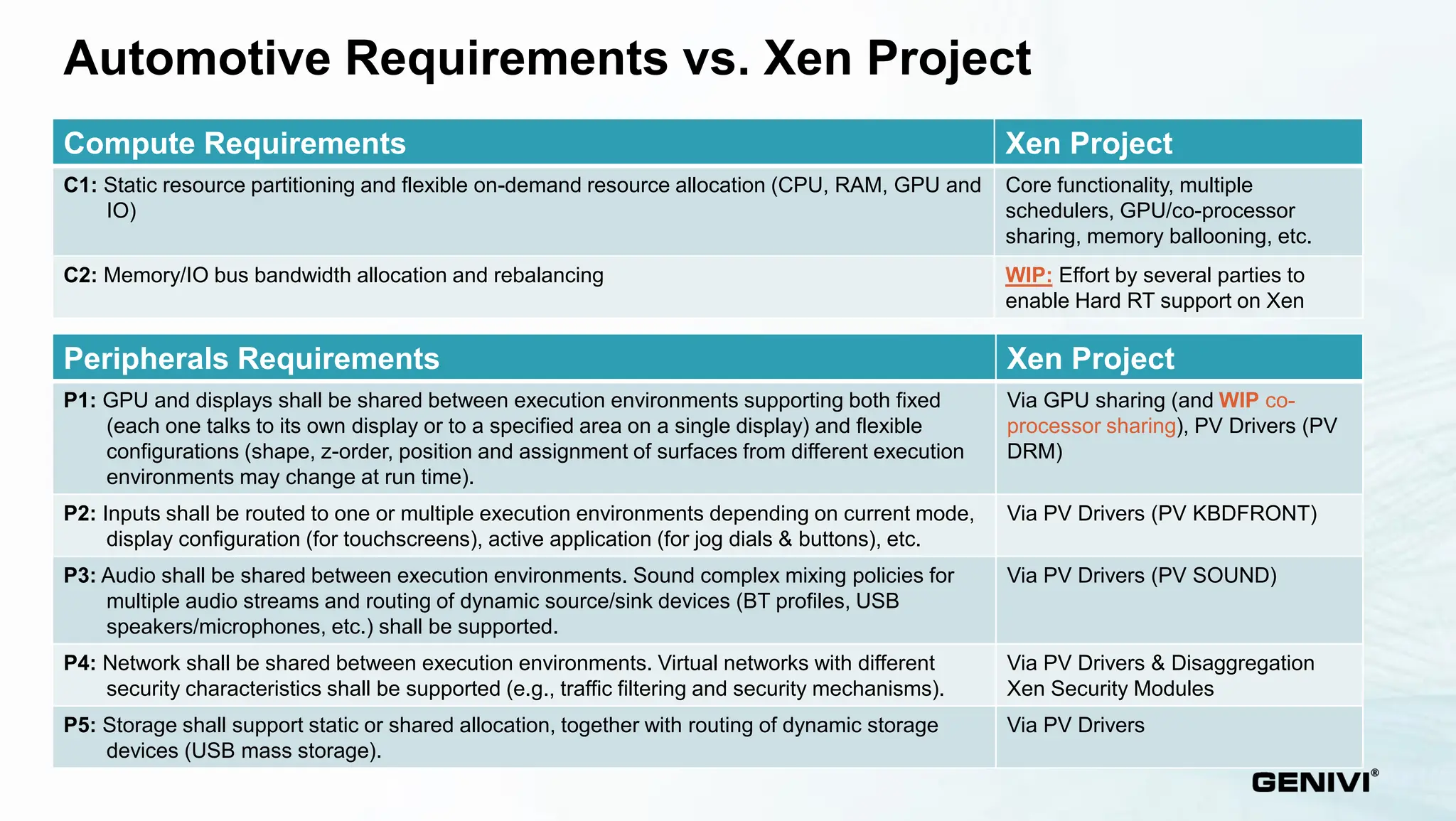
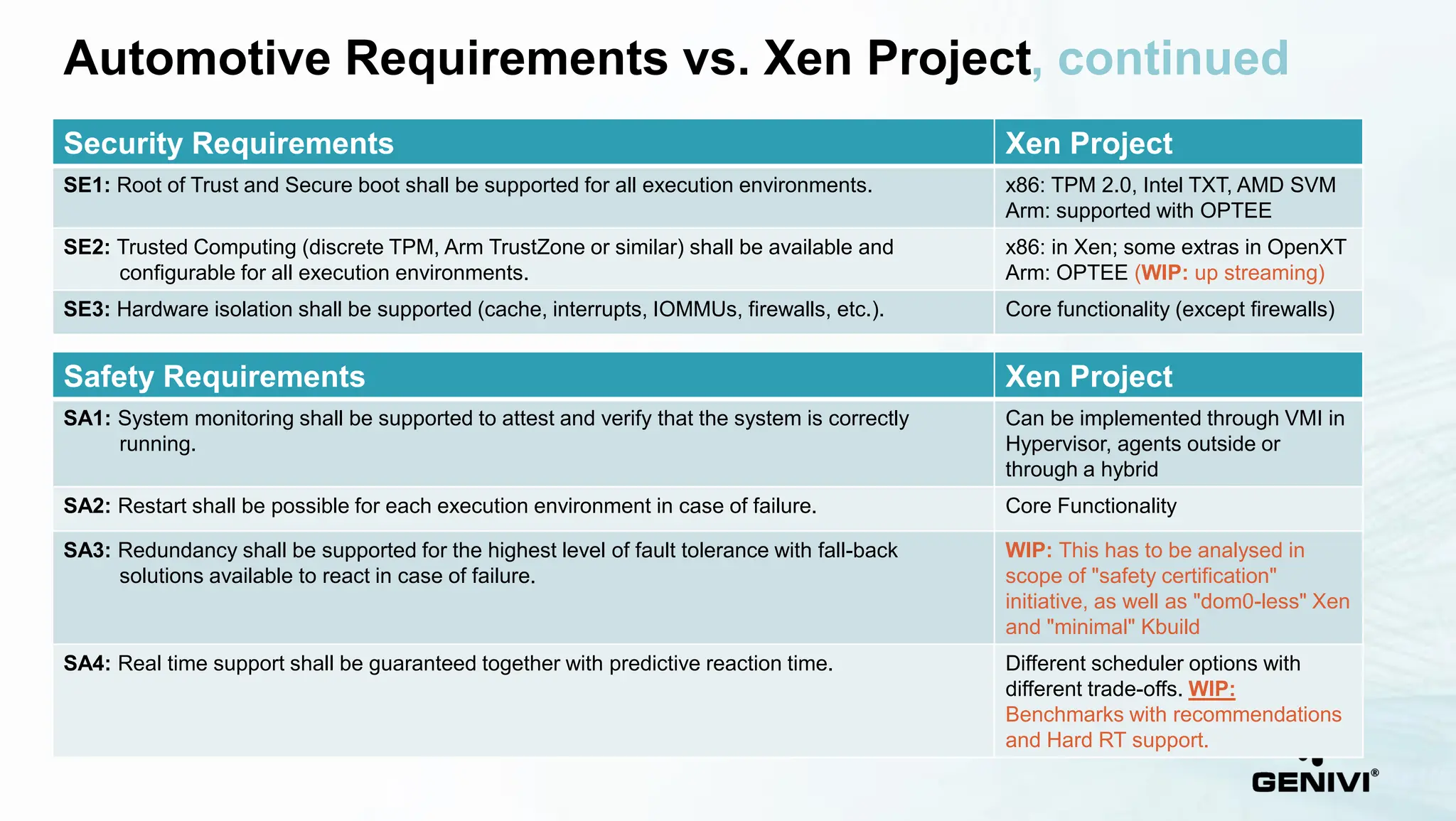
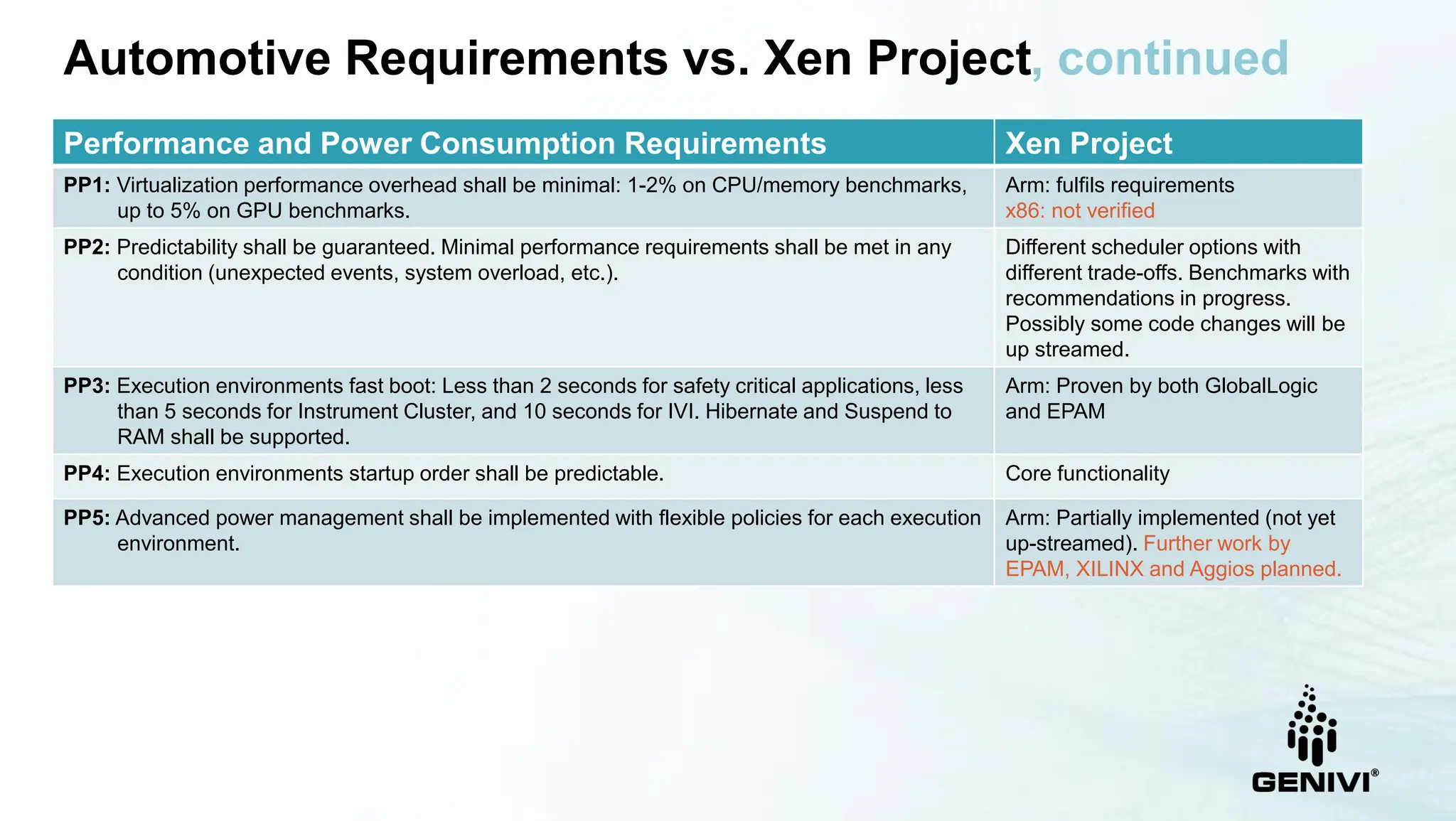
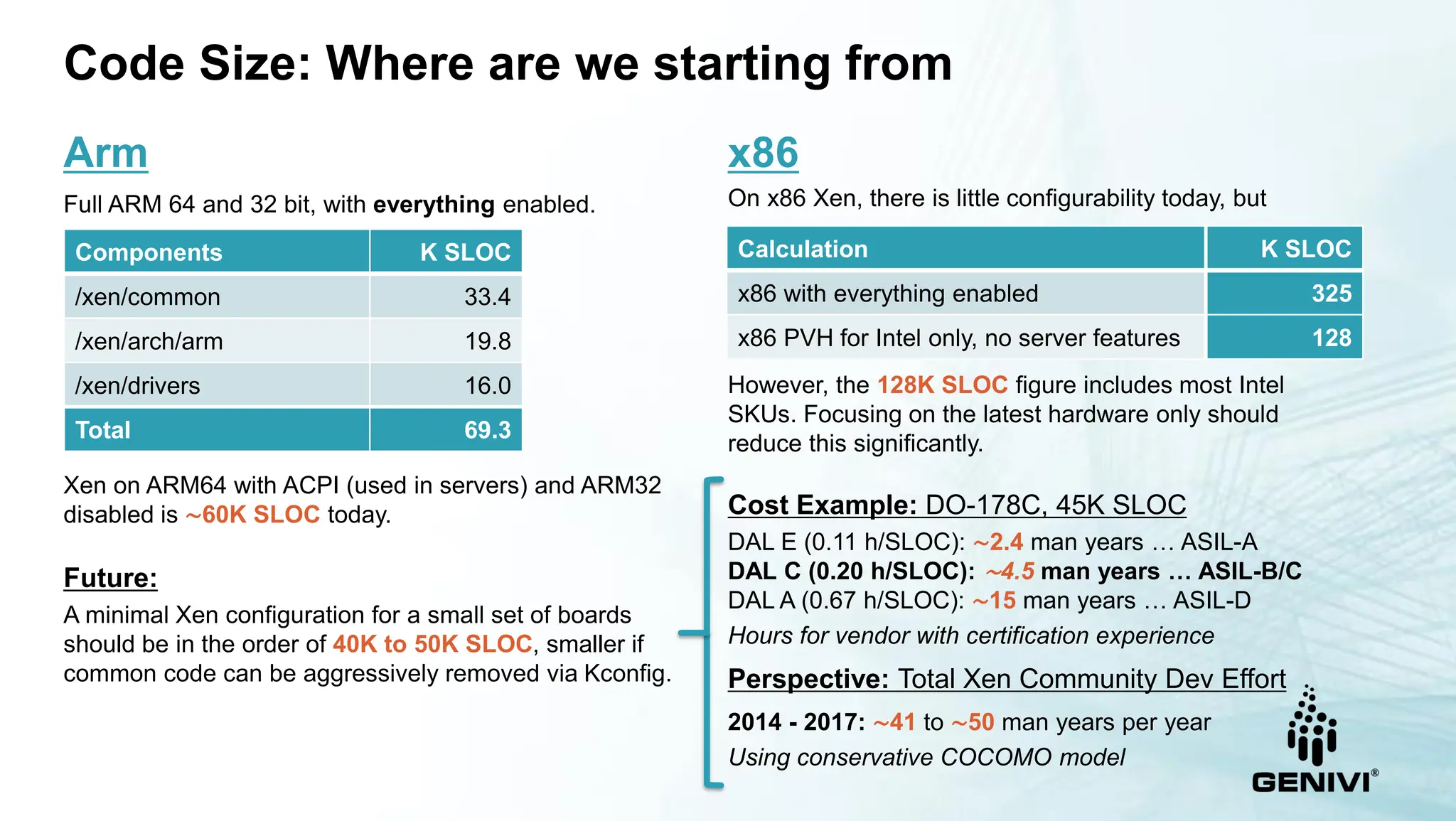
The document provides an overview of the Xen Project's capabilities in the automotive and embedded sectors, emphasizing challenges related to safety certification and resource management. It discusses various contributions, partnerships, and the development of specific products like the Virtuosity hypervisor, alongside automotive service platforms that utilize Xen's virtualization. The ongoing efforts to meet automotive safety standards while managing performance and power consumption needs are also highlighted.