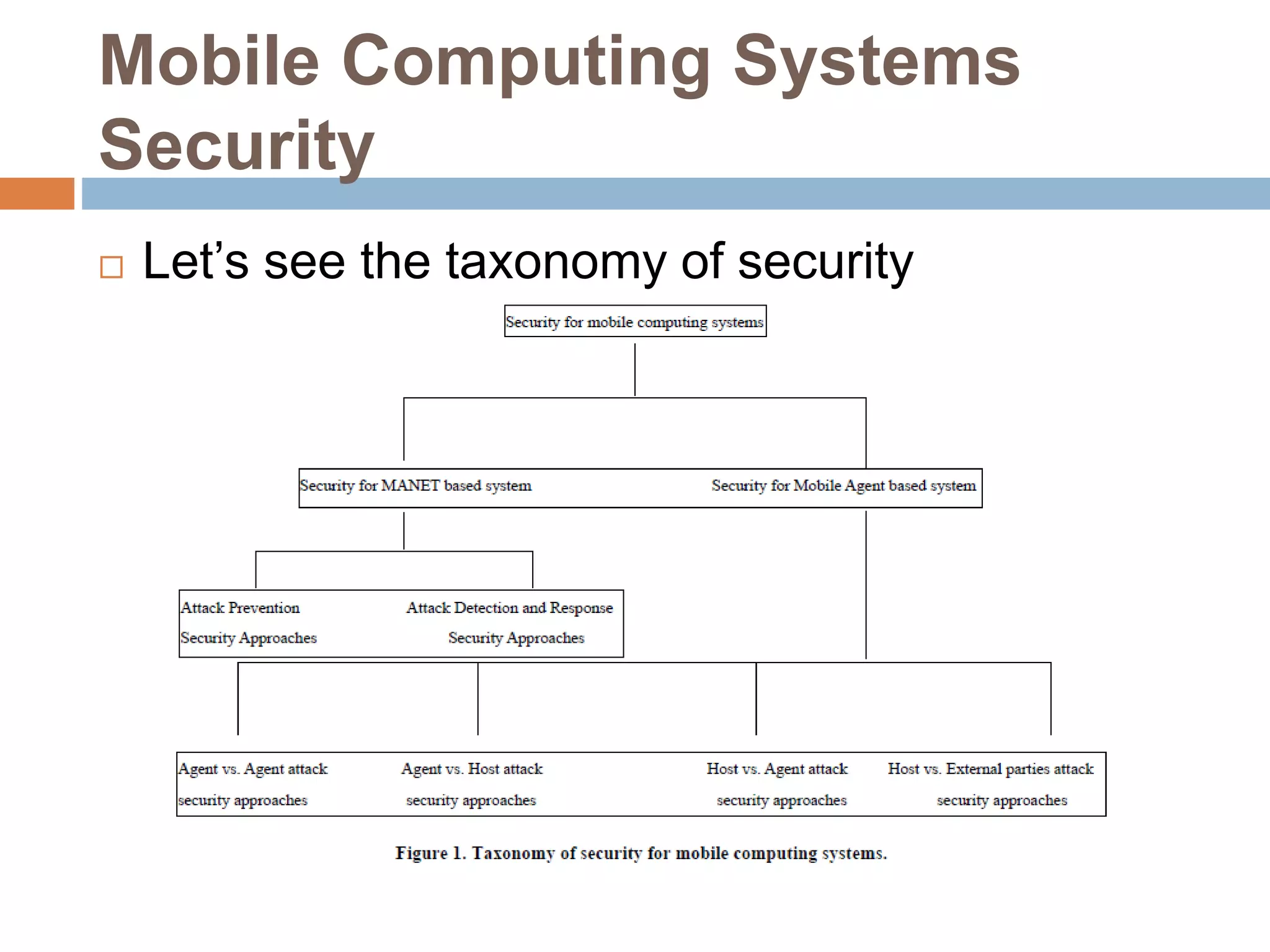
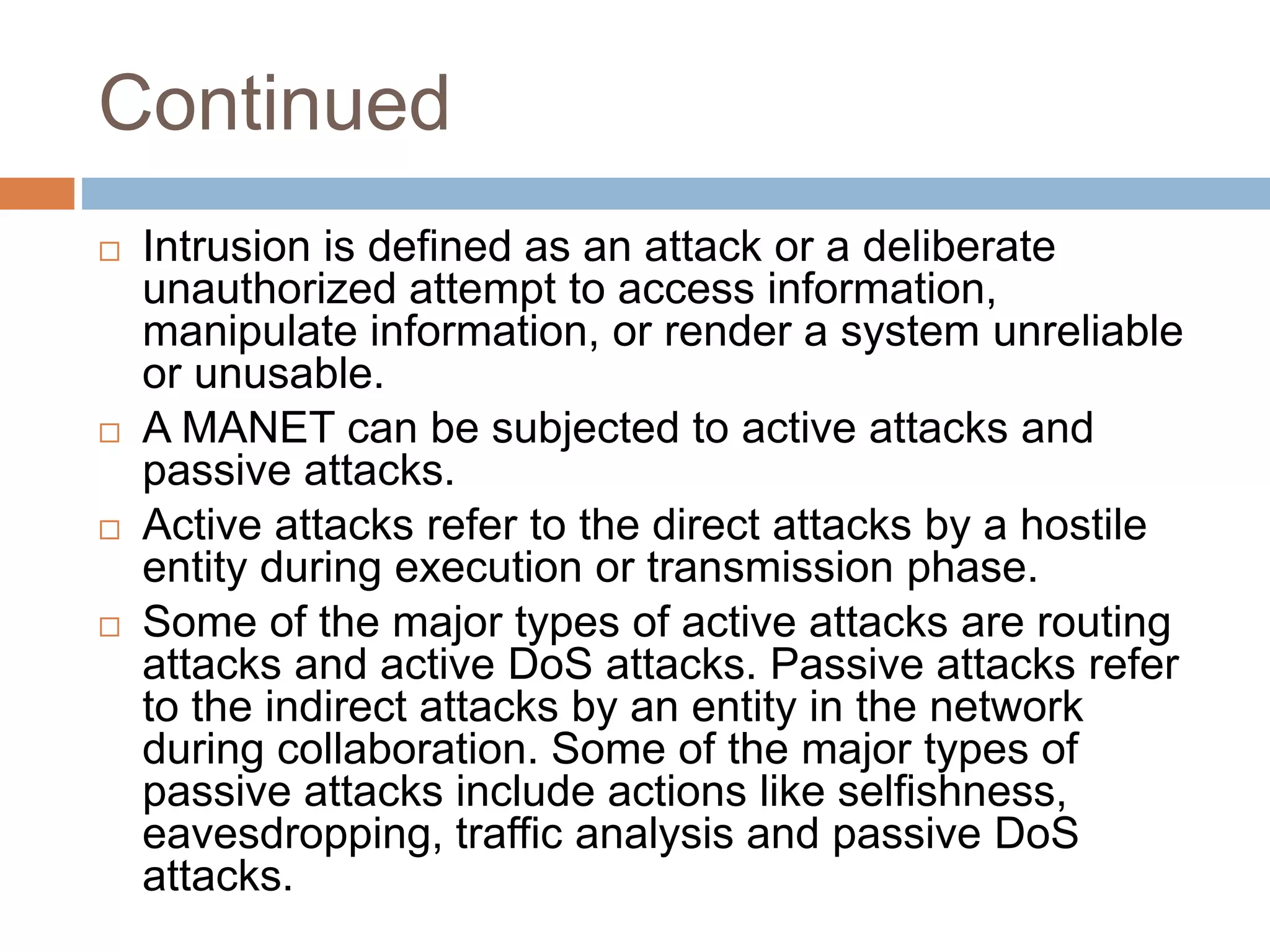
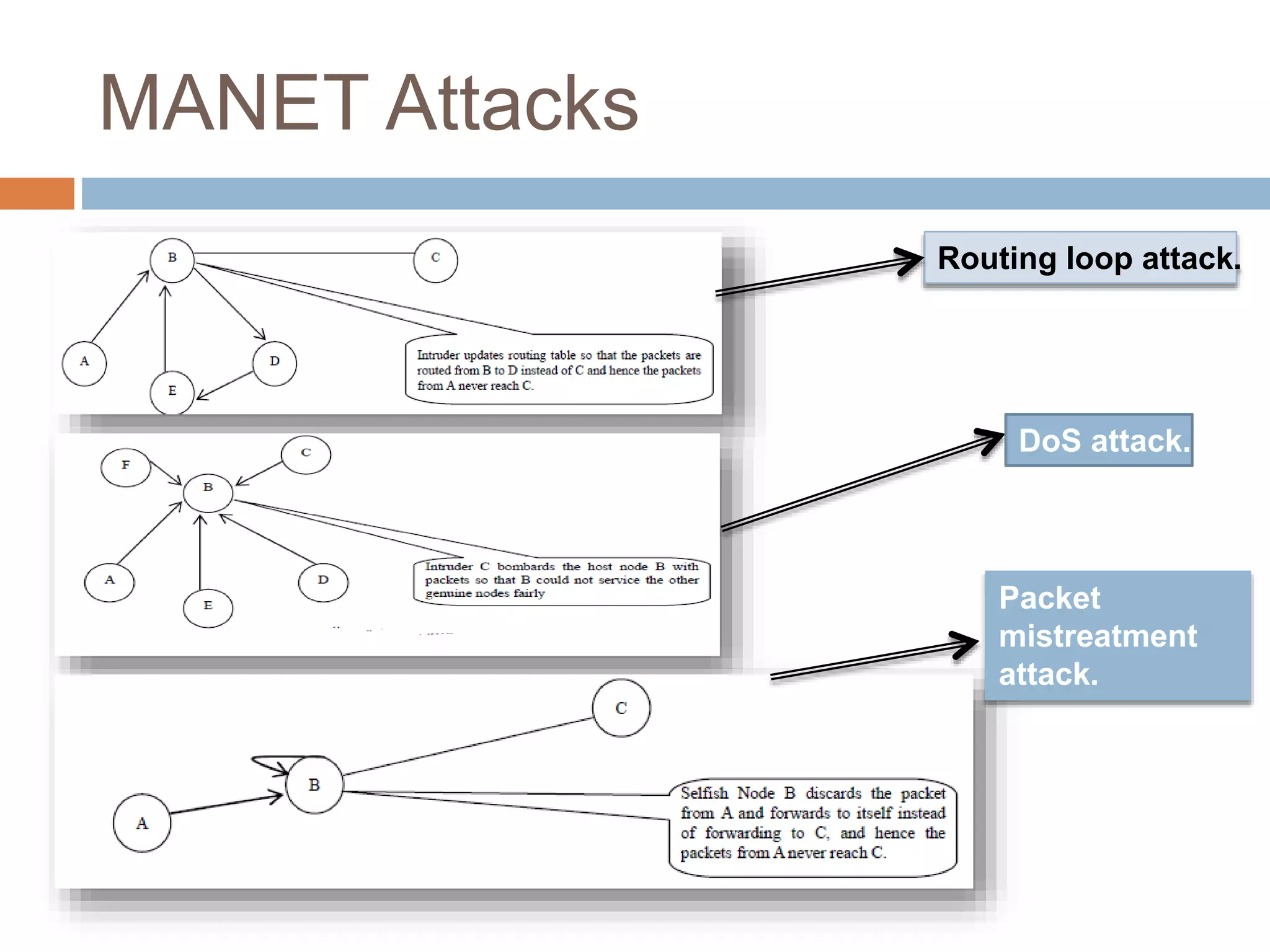
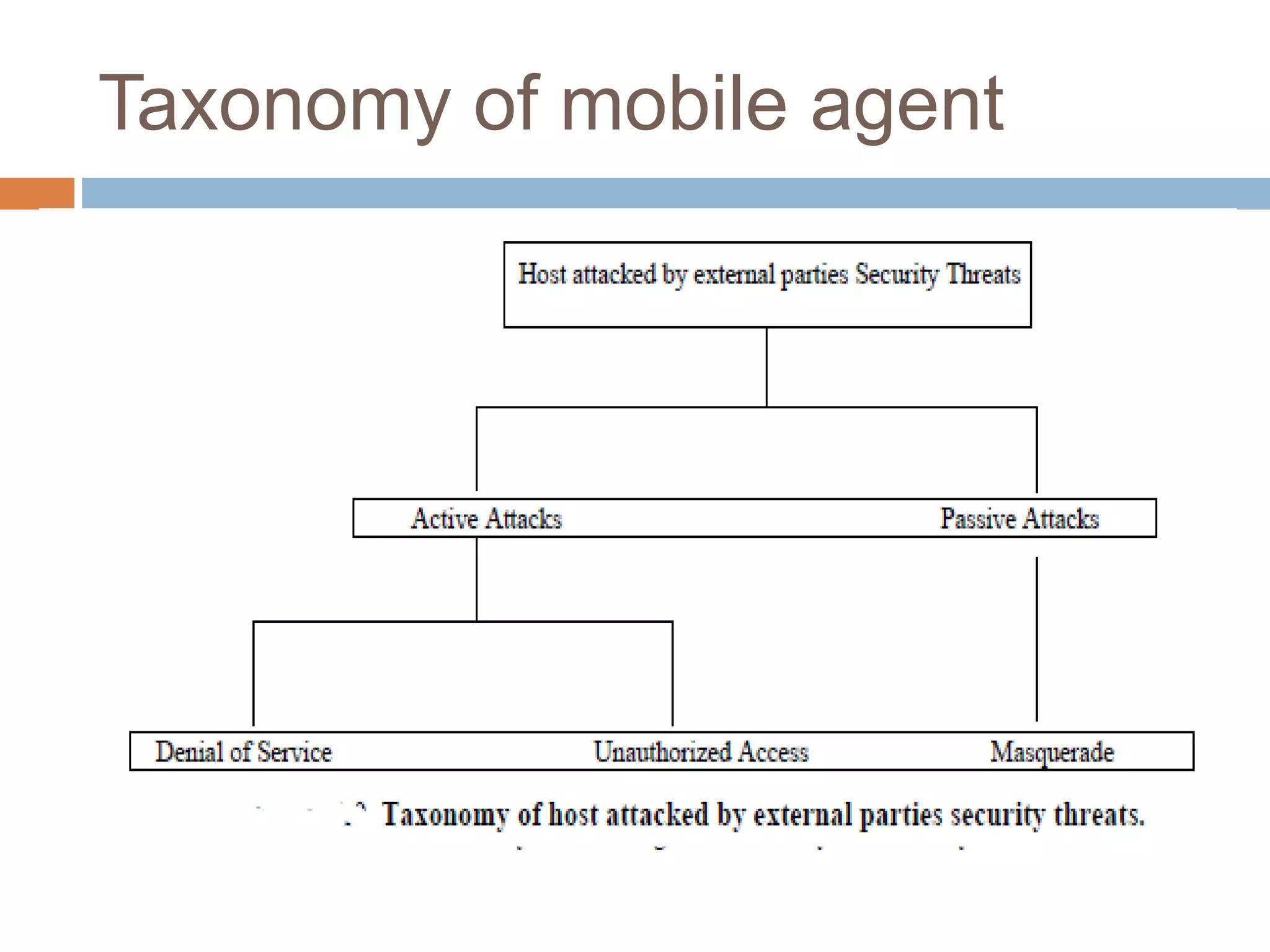
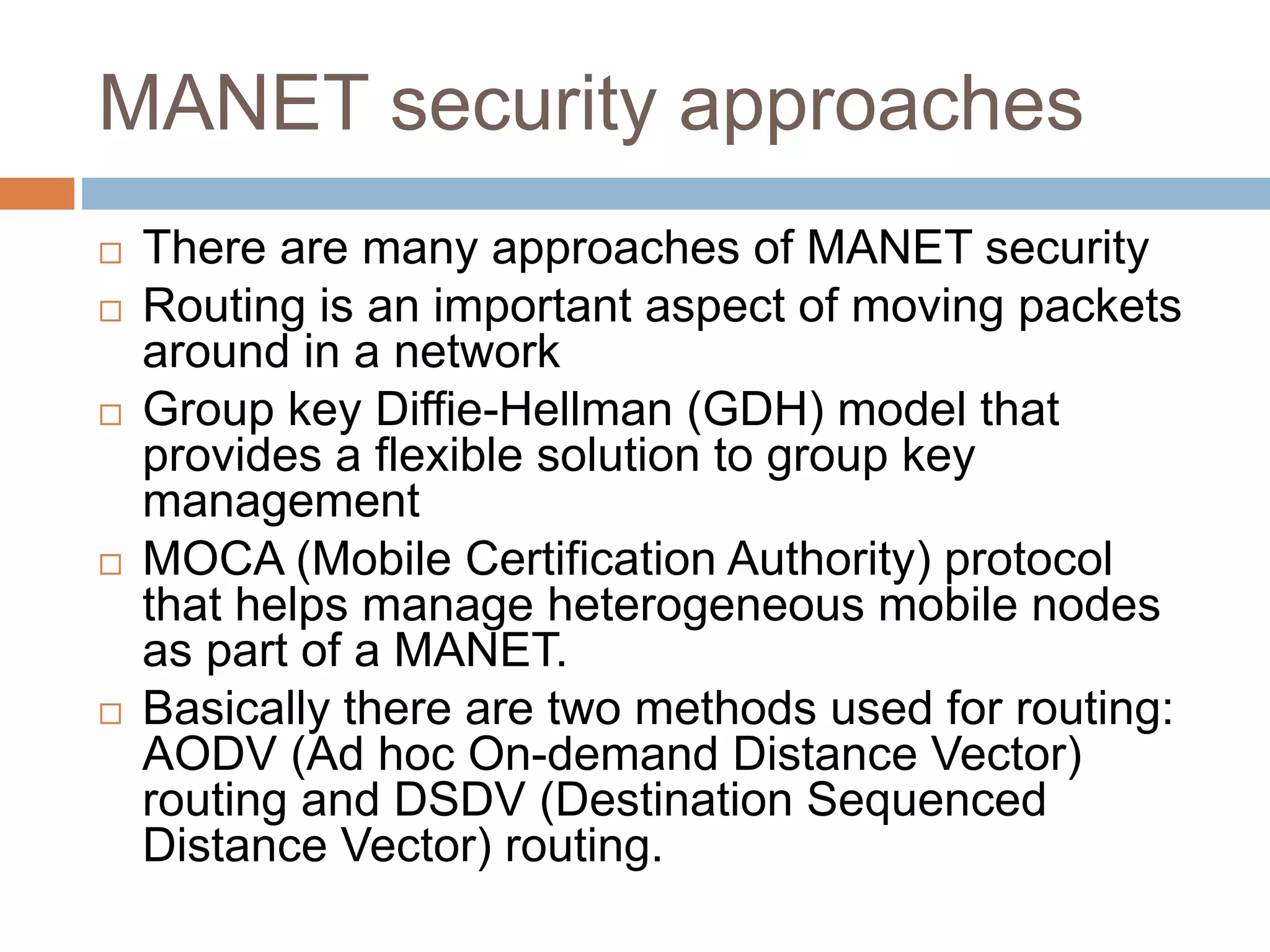
Mobile computing systems face security challenges due to their vulnerability. This document analyzes security schemes for mobile computing, classifying approaches for mobile ad hoc networks (MANETs) and mobile agents. For MANETs, threats include denial of service attacks and routing attacks. For mobile agents, protecting agents from hostile hosts is difficult. The taxonomy highlights contributions to address different attack types and approaches, identifying limitations and open issues to better secure mobile networks.