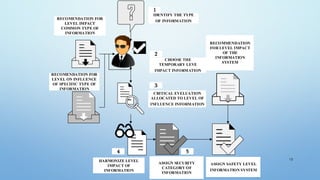
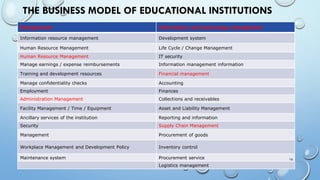
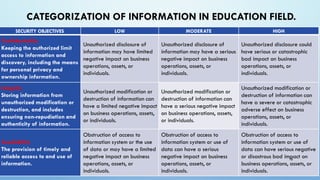
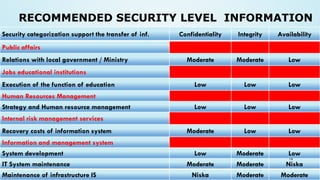
The document outlines a comprehensive methodology for classifying information within the education sector, focusing on defining security objectives related to confidentiality, integrity, and availability. It categorizes sensitive information into various types, including state, official, business, and professional secrets, while assessing the potential impact of information breaches at low, moderate, and high levels. It emphasizes the need for expert groups to establish protocols for managing confidential information, highlighting the importance of employee awareness and the adoption of regulations to enhance data protection and information security.