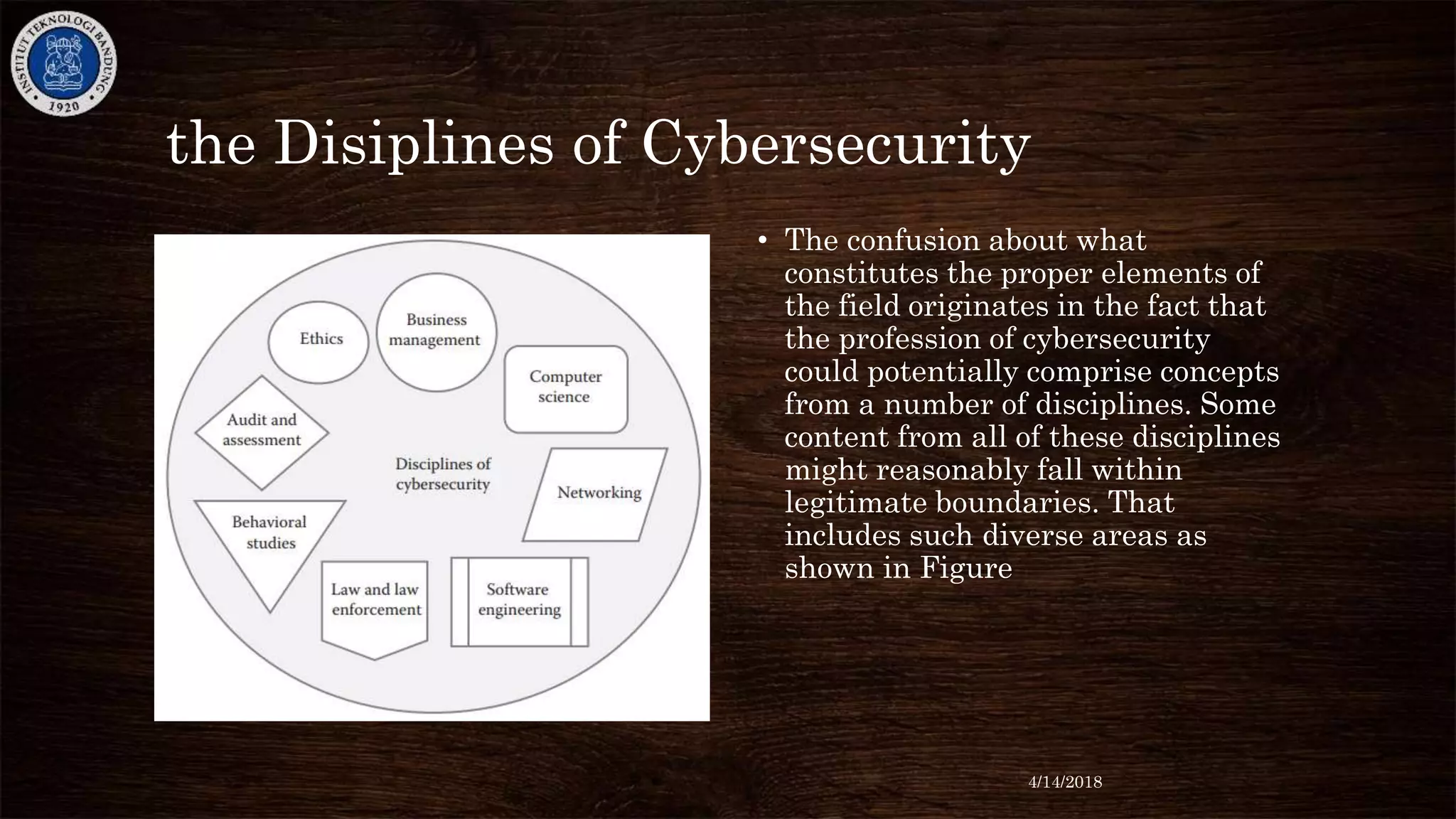
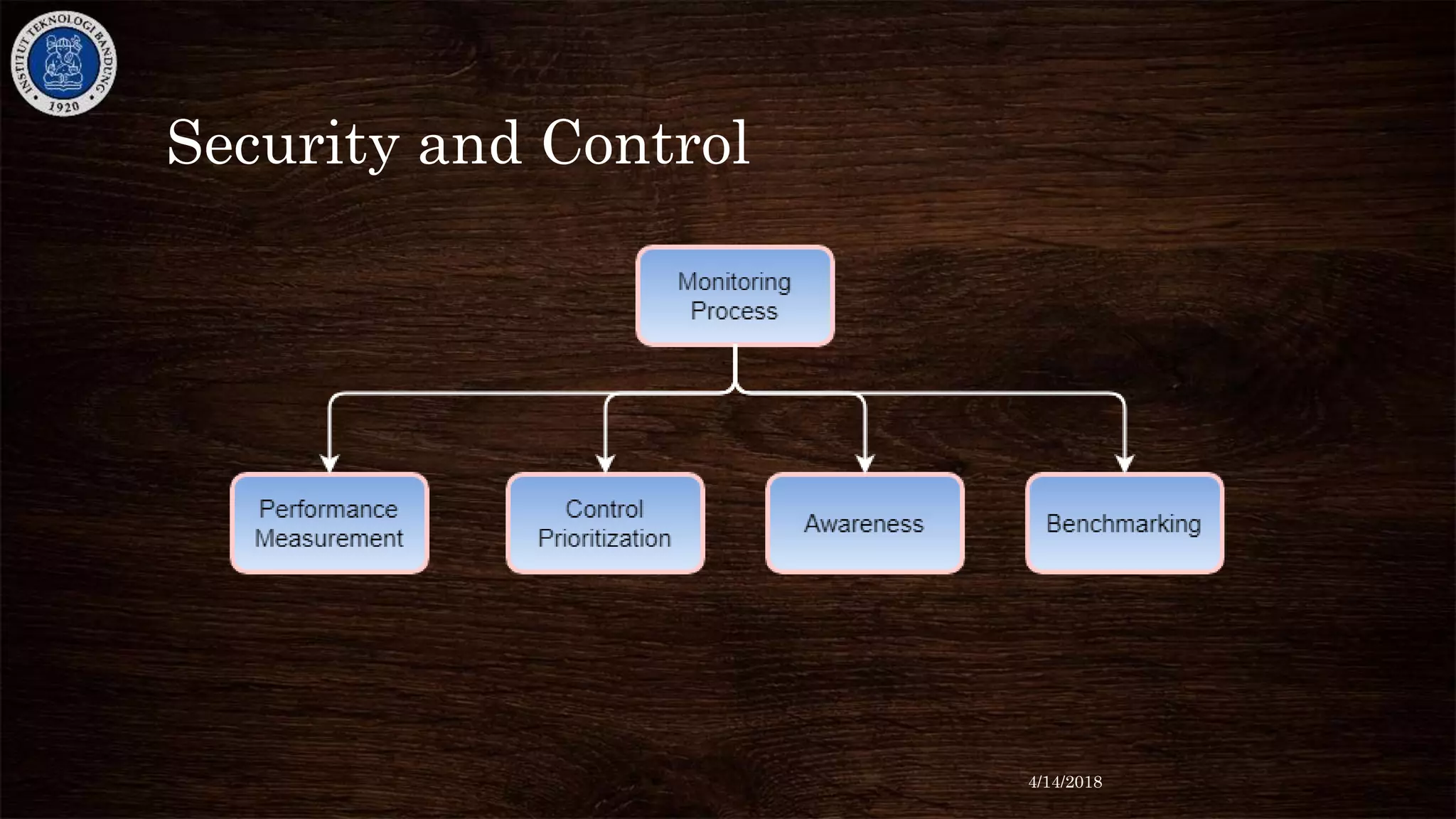
The document discusses cybersecurity risks and controls. It begins by defining cybersecurity and noting that 46% of the world's population is connected to the internet. It then discusses common threat vectors and the industries most targeted by espionage. The document emphasizes the importance of cybersecurity management and outlines standard guidance documents. It describes the key elements of effective cybersecurity as including policies, governance, personnel security, and controls related to assets, access, operations, networks, software and more. Finally, it discusses integrating security across an organization's infrastructure.


![What is Cybersecurity?
• The state of being protected
against the criminal or
unauthorized use of electronic
data, or the measures taken to
achieve this (Oxford English
Dictionary)
• 46% populasi dunia terhubung
ke jaringan internet [1]
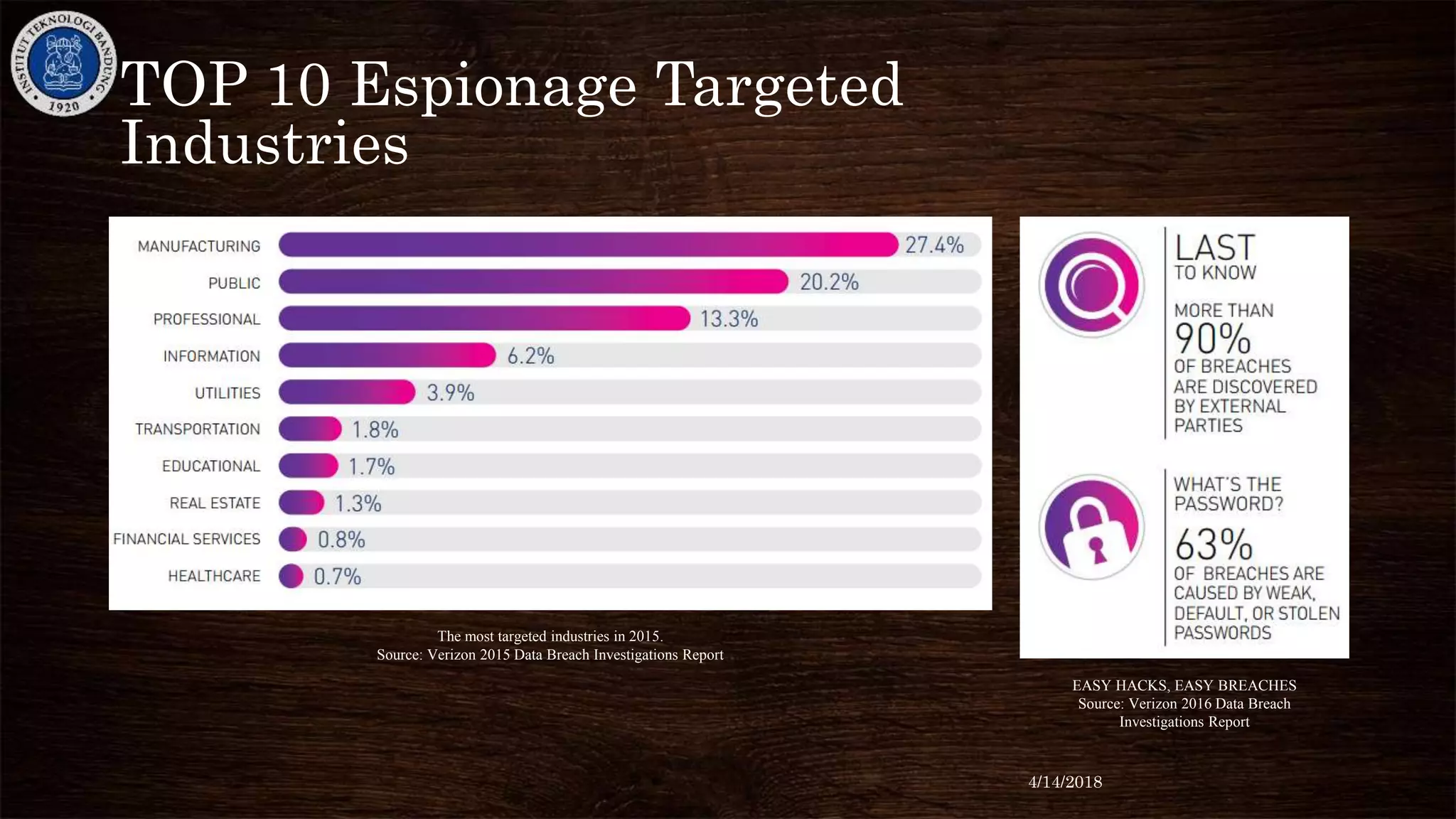
THREAT VECTORS BY INDUSTRY
The vectors by which industries are compromised.
Source: Verizon 2015 Data Breach Investigations Report
[1] Cybersecurity: Threats, Challenges, and Opportunities by ACS
4/14/2018](https://image.slidesharecdn.com/23216316rd-180421151010/75/Resume-The-Complete-Guide-to-Cybersecurity-Risks-and-Controls-3-2048.jpg)








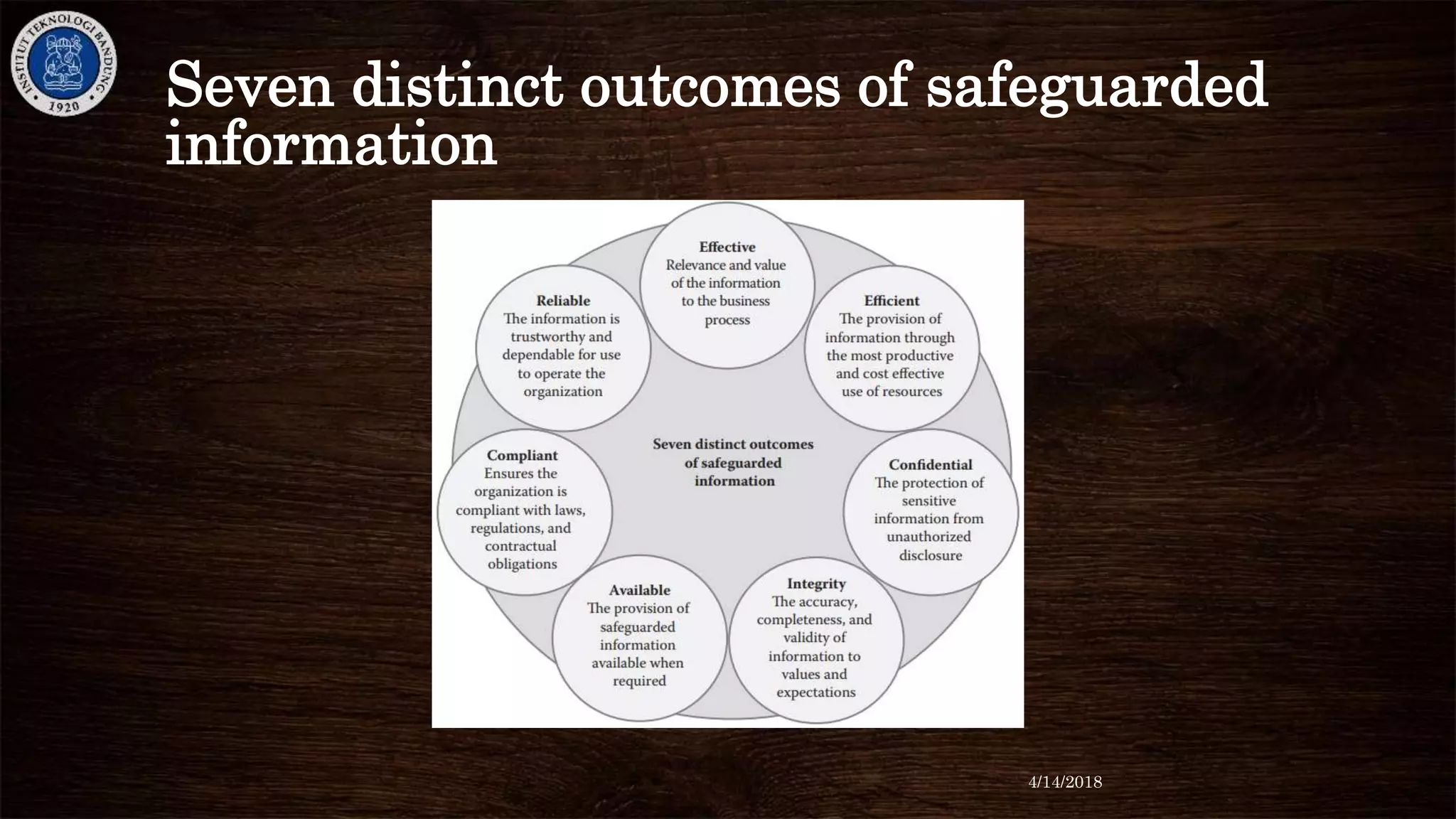
![• Effective information security governance should result in six
outcomes to include (Information Systems Audit and Control
Association [ISACA], 2012) the following:
– Strategic alignment
– Risk management
– Business process management/value delivery
– Resource management
– Performance management
– Integration
4/14/2018](https://image.slidesharecdn.com/23216316rd-180421151010/75/Resume-The-Complete-Guide-to-Cybersecurity-Risks-and-Controls-18-2048.jpg)